Major Cyber Attacks in October 2025: Phishing via Google Careers & ClickUp, Figma Abuse, LockBit 5.0, and TyKit
Phishing campaigns and ransomware families evolved rapidly this October, from fake Google Careers pages and ClickUp redirect chains to Figma-hosted credential theft and LockBit’s move into ESXi and Linux systems. ANY.RUN analysts also uncovered TyKit, a reusable phishing kit hiding JavaScript inside SVG files to steal Microsoft 365 credentials across multiple sectors.
Each of these threats shows how attackers are increasingly abusing legitimate cloud platforms, layering CAPTCHA checks and redirects to bypass detection. All cases were analyzed inside ANY.RUN’s Interactive Sandbox, revealing execution flows and behavioral indicators missed by static tools; insights SOC teams can turn into actionable detection logic.
Let’s break down how these attacks unfolded, who they targeted, and what security teams can learn to strengthen their defenses before the next wave hits.
1. Google Careers Phishing Campaign: Legitimate Platforms Used to Steal Corporate Credentials
ANY.RUN analysts uncovered a phishing campaign posing as Google Careers, where attackers combined a Salesforce redirect, Cloudflare Turnstile CAPTCHA, and a fake job application page to steal corporate credentials. The campaign primarily targets employees in technology, consulting, and enterprise service sectors, exploiting the trust people place in well-known brands and cloud services.
Unlike typical phishing kits, this campaign weaves together multiple legitimate platforms to make the flow appear authentic, slipping through filters and reputation-based security tools. Once credentials are entered on the fake Google Careers portal, they’re exfiltrated to the command-and-control (C2) server, such as satoshicommands[.]com, enabling further compromise of work accounts, client data, and internal collaboration tools.
For organizations, this attack creates a chain reaction: compromised mailboxes, lateral movement across SaaS ecosystems, and potential exposure of customer or partner data; all while evading detection from traditional tools that trust the Salesforce and Cloudflare domains in the redirect path.
See full execution chain exposed in 60 seconds
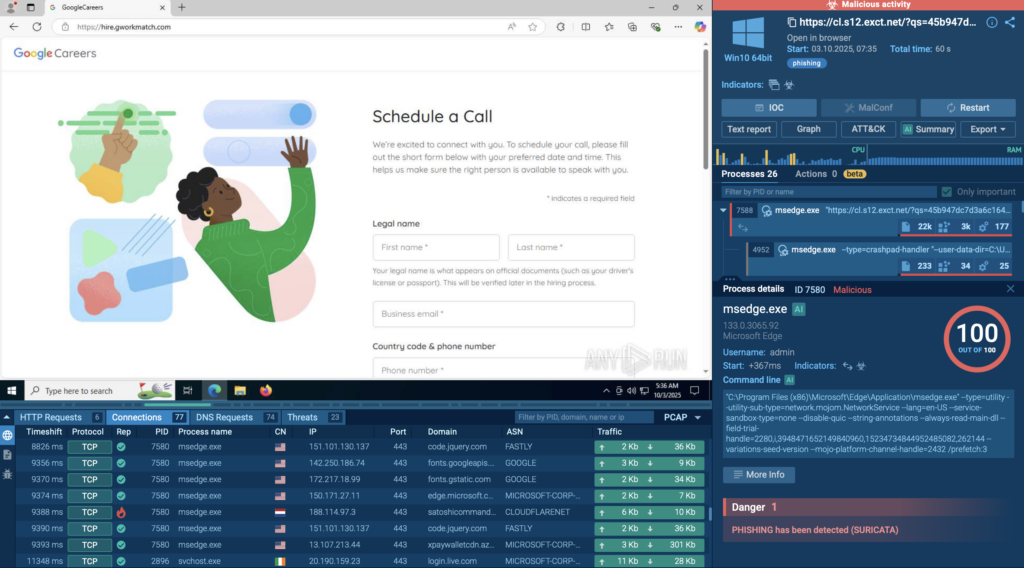
Adversaries in this campaign misuse legitimate platforms to host phishing flows that evade automated detection. The combination of trusted domains and multi-step redirection makes these attacks particularly hard to catch without behavioral visibility.
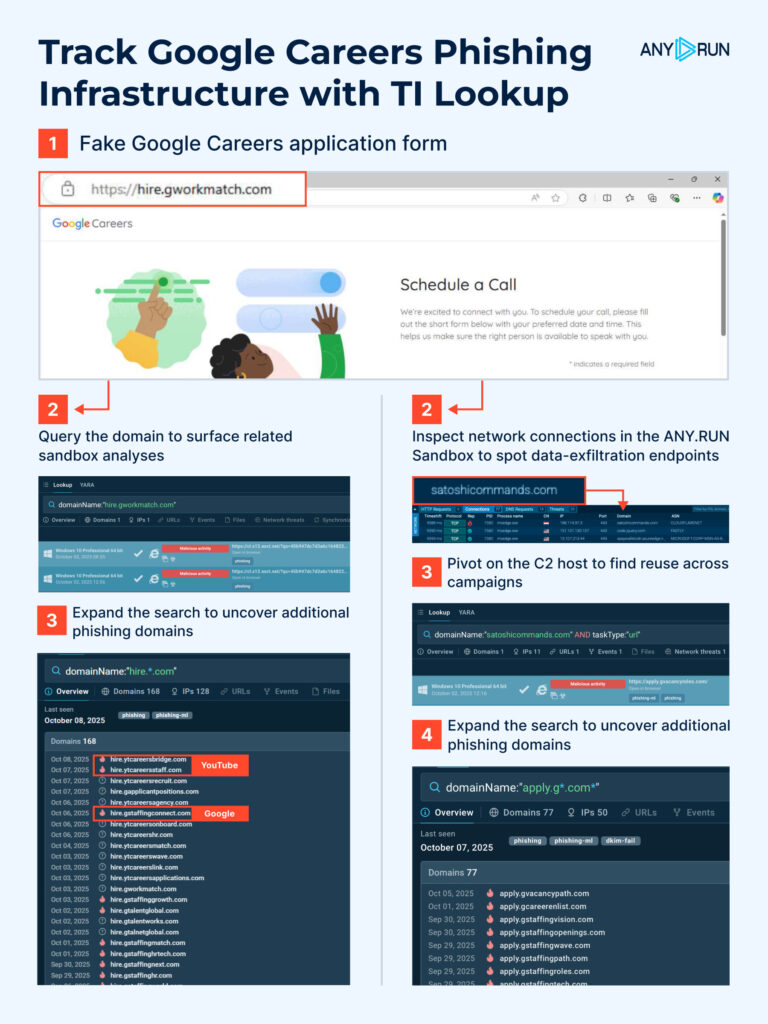
Below are ready-to-use Threat Intelligence Lookup queries to expand visibility, uncover infrastructure overlaps, and convert findings into detection rules, not just IOCs:
Google-like application domains: domainName:”apply.g*.com” OR domainName:”hire.g*.com”
Vercel deployment patterns: domainName:”puma-*.vercel.app” OR domainName:”hiring*.vercel.app”
YouTube TLD impersonation: domainName:”hire.yt”
C2 domain: domainName:”satoshicommands.com”
Gathered IOCs:
- 188[.]114[.]97[.]3
- 104[.]21[.]62[.]195
- hire[.]gworkmatch[.]com
- satoshicommands[.]com
2. Figma Abuse Leads to Microsoft-Themed Phishing Campaigns
ANY.RUN analysts identified a growing wave of phishing attacks abusing Figma, where public design prototypes are used to host and deliver Microsoft-themed credential theft campaigns. This trend highlights a serious blind spot in corporate defenses; the exploitation of trusted cloud platforms that security systems often whitelist by default.
Attackers are turning to Figma because it offers everything they need for a convincing delivery: it’s a widely trusted domain, allows anyone to publish and share prototypes publicly without authentication, and renders interactive content directly in the browser. That makes it perfect for embedding phishing elements, buttons, links, and visuals that look completely legitimate, while bypassing traditional email filters and URL reputation checks.
Across multiple samples analyzed last month, 49% of these attacks were linked to Storm-1747, followed by Mamba (25%), Gabagool (2%), and several smaller operators. Each uses Figma as the initial hosting vector, sending victims “document” invitations that appear genuine and trigger the phishing flow upon interaction.
Check real case: Figma abuse leading to fake Microsoft login page
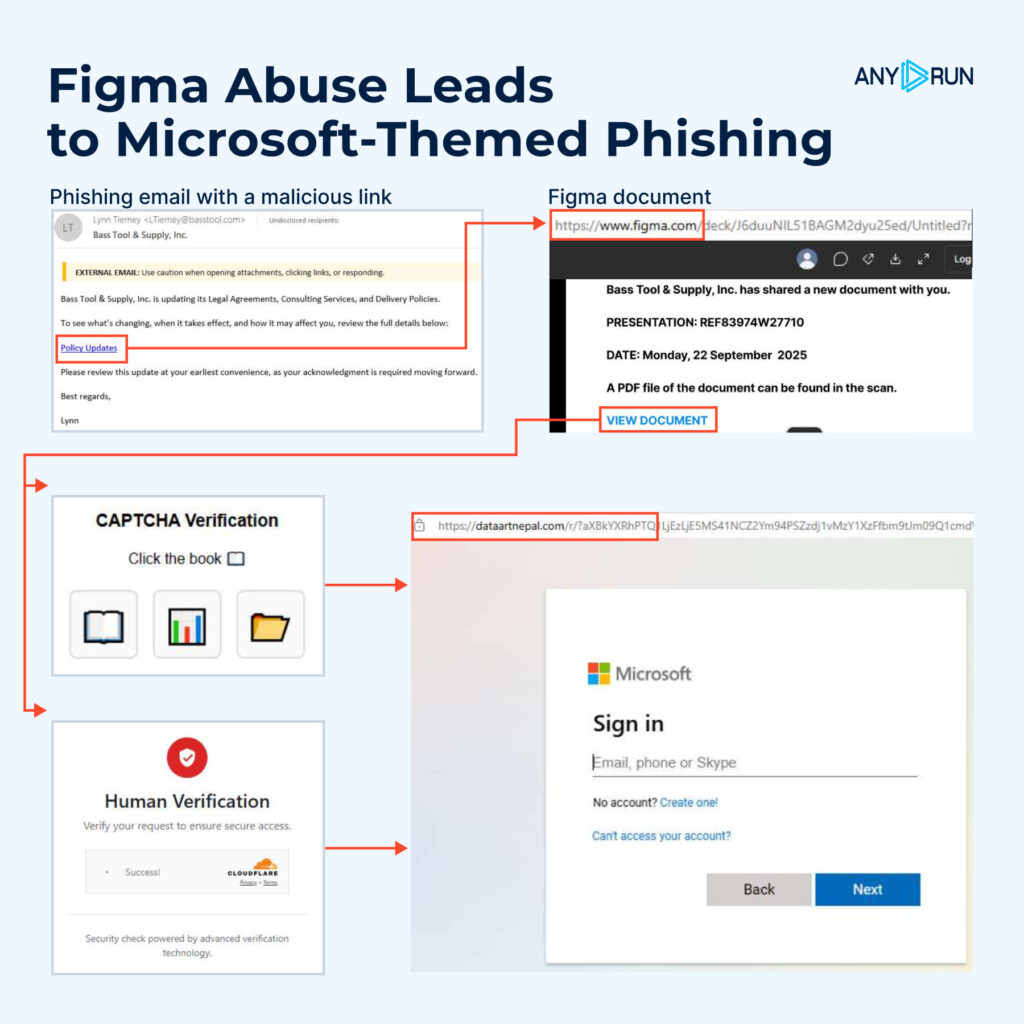
- Phishing email invites the victim to view a “shared document.”
- Figma prototype hosts a fake collaboration page within the figma.com domain.
- Embedded link triggers a fake CAPTCHA or Cloudflare Turnstile widget.
- Redirection leads to a Microsoft-themed login page that collects credentials.
Inside ANY.RUN’s Interactive Sandbox, analysts can safely detonate these links, visualize the full redirection flow, and expose the hidden credential capture mechanism; something static filters miss entirely. This interactive approach gives SOC teams real behavioral context for tuning detections and reduces investigation time when facing similar cloud-hosted phishing chains.
To uncover additional campaigns abusing Figma and connected infrastructure, use the following TI Lookup query:
domainName:”figma.com” AND threatName:”phishing”
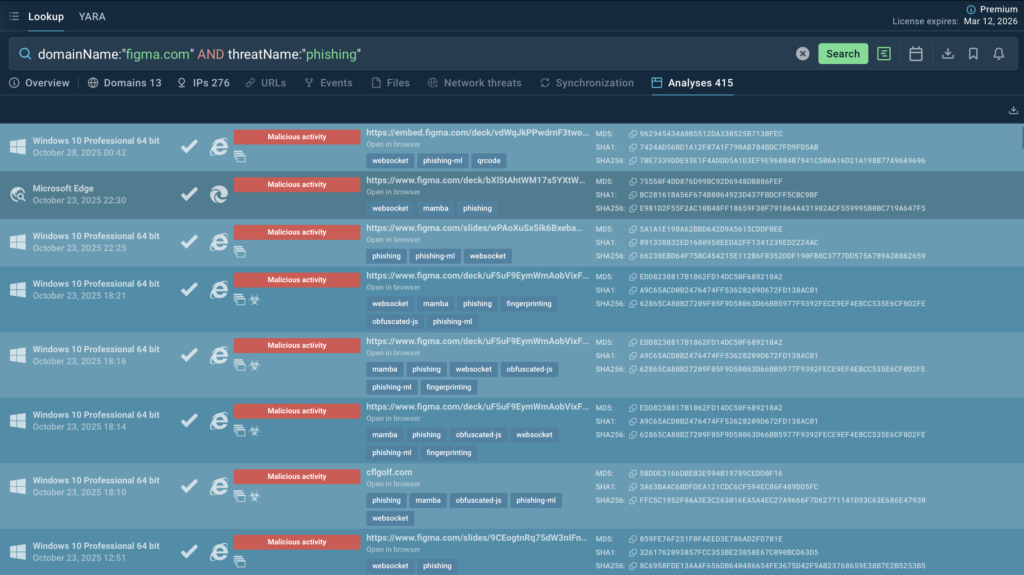
This search surfaces recent submissions that share behavioral traits, letting SOC teams expand visibility and transform isolated IOCs into behavioral detection rules.
Gathered IOCs:
- 9a4c7dcf25e9590654694063bc4958d58bcbe57e5e95d9469189db6873c4bb2c
- Dataartnepal[.]com
3. LockBit 5.0: New Variant Targets ESXi and Linux, Putting Critical Infrastructure at Risk
Researchers spotted a major update from the LockBit group on its sixth anniversary: LockBit 5.0. Unlike earlier releases, this version targets not only Windows but also Linux and VMware ESXi, meaning attackers are now going after core infrastructure. A single successful intrusion can take down many virtual machines at once and knock whole systems offline.
LockBit 5.0 introduces stronger obfuscation, flexible configuration files, and enhanced anti-analysis techniques, making it significantly harder to detect and dissect. The campaign primarily targets enterprise networks, managed service providers, and government systems across Europe, North America, and Asia, where virtualized environments form the backbone of daily operations.
A single LockBit 5.0 intrusion can shut down dozens of servers simultaneously, halting production systems, paralyzing data centers, and causing prolonged outages with severe financial and reputational consequences.
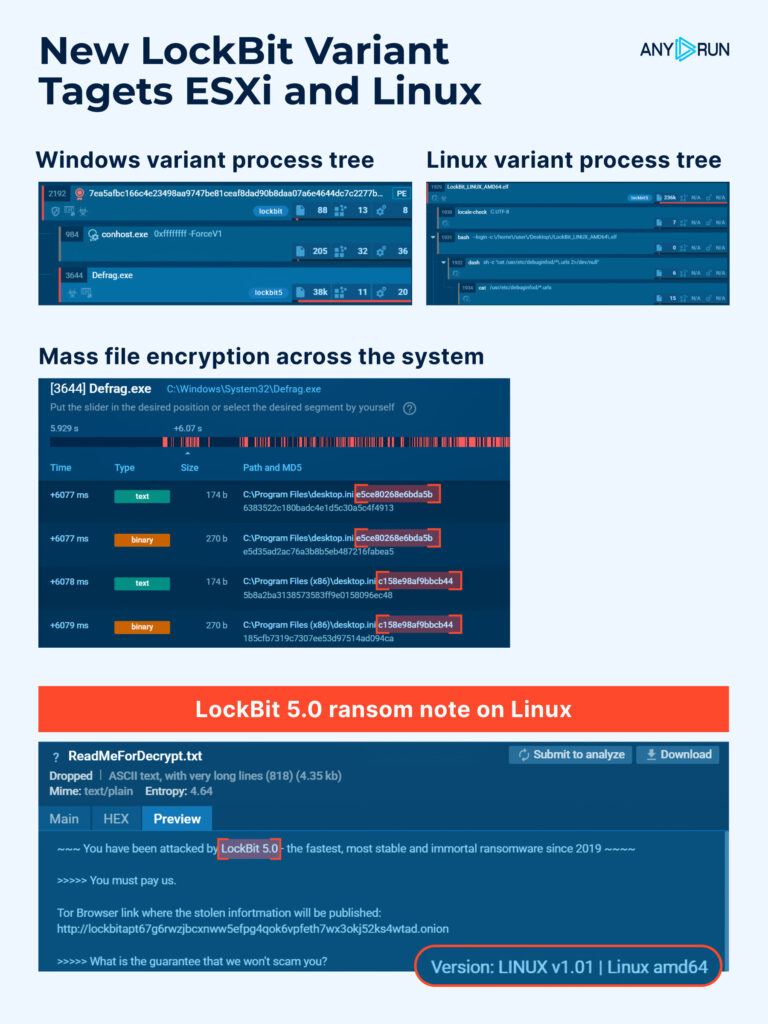
Technical Overview of LockBit 5.0 Variants
- VMware ESXi
View real-world analysis of VMware ESXi variant
The most critical of the three builds. A dedicated encryptor for hypervisors capable of disabling multiple virtual machines at once. Its CLI closely mirrors the Windows version but adds datastore and VM config targeting, enabling it to halt operations across entire host environments in seconds.
- Windows
View real-world analysis of Windows variant
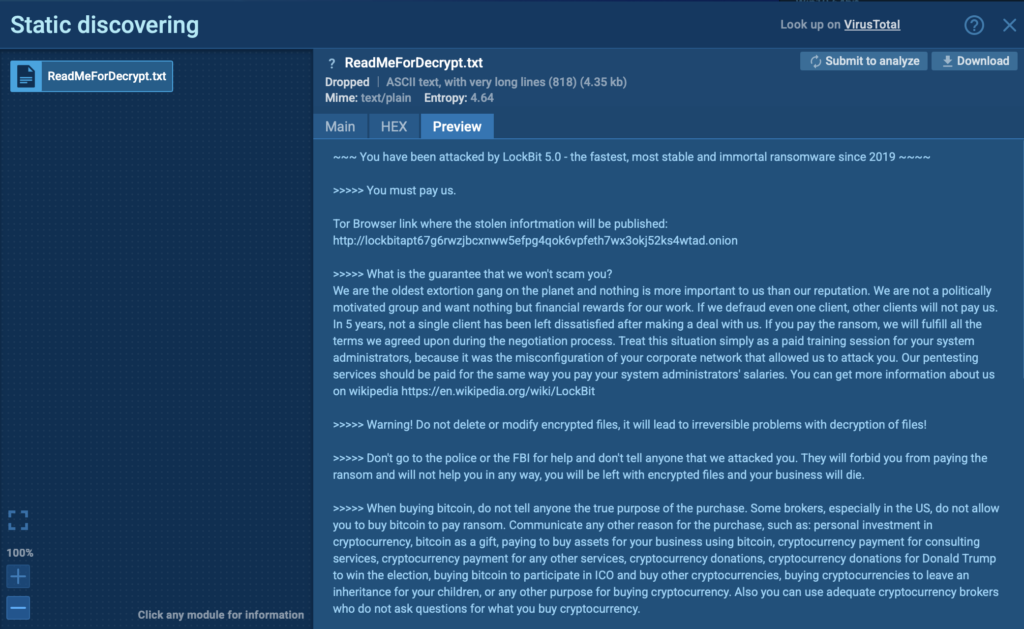
The mainline variant runs with DLL reflection, supports both GUI and console modes, encrypts local and network drives, and performs cleanup actions like deleting shadow copies, stopping critical services, and clearing event logs. It drops a ransom note linking to LockBit’s live negotiation portal.
- Linux
View real-world analysis of Linux variant
A lightweight console-based encryptor that replicates Windows behavior with added mount point filters, disk wiping, anti-analysis routines, and region-based execution restrictions to evade detection and avoid unwanted publicity in certain locales.
Inside ANY.RUN’s Interactive Sandbox, analysts can trace how the new encryptors behave across each operating system, from memory injection and service termination to encryption logic and ransom note delivery, helping SOC teams identify new TTPs early and enrich detection logic with behavioral indicators, not just static IOCs.
Use the following Threat Intelligence Lookup queries to identify LockBit 5.0 activity and enrich your SOC’s detection coverage with live sandbox data:
ESXi Lockbit 5.0: commandLine:”vmware -v”
Linux Lockbit 5.0: filePath:”^/home/user/.local/share/evolution/tasks/ReadMeForDecrypt.txt$”
Windows Lockbit 5.0: filePath:”^C:\ReadMeForDecrypt.txt$”
These queries help analysts pivot from OS-specific artifacts to global attack patterns, connecting infrastructure and payload updates across submissions.
What Security Teams Should Do Now:
- Boost visibility: Combine endpoint and network telemetry with behavior-based monitoring. Use ANY.RUN’s sandbox and TI Lookup to detect evolving LockBit builds earlier, enrich IOC sets, and reduce MTTR by up to 21 minutes.
- Harden access: Enforce MFA for vCenter and admin accounts, restrict direct Internet access to ESXi hosts, and route all management connections through a secure VPN.
- Ensure resilience: Maintain offline backups, test recovery workflows regularly, and rehearse ransomware playbooks to minimize downtime in case of a breach.
4. ClickUp Hosts Used as Phishing Redirectors
ANY.RUN analysts found attackers abusing ClickUp to host redirect pages and hide phishing flows. In many cases ClickUp is the visible domain the victim clicks, then the chain moves through other trusted services (like Microsoft’s microdomains and Azure Blob Storage) before landing on a credential-harvesting page.
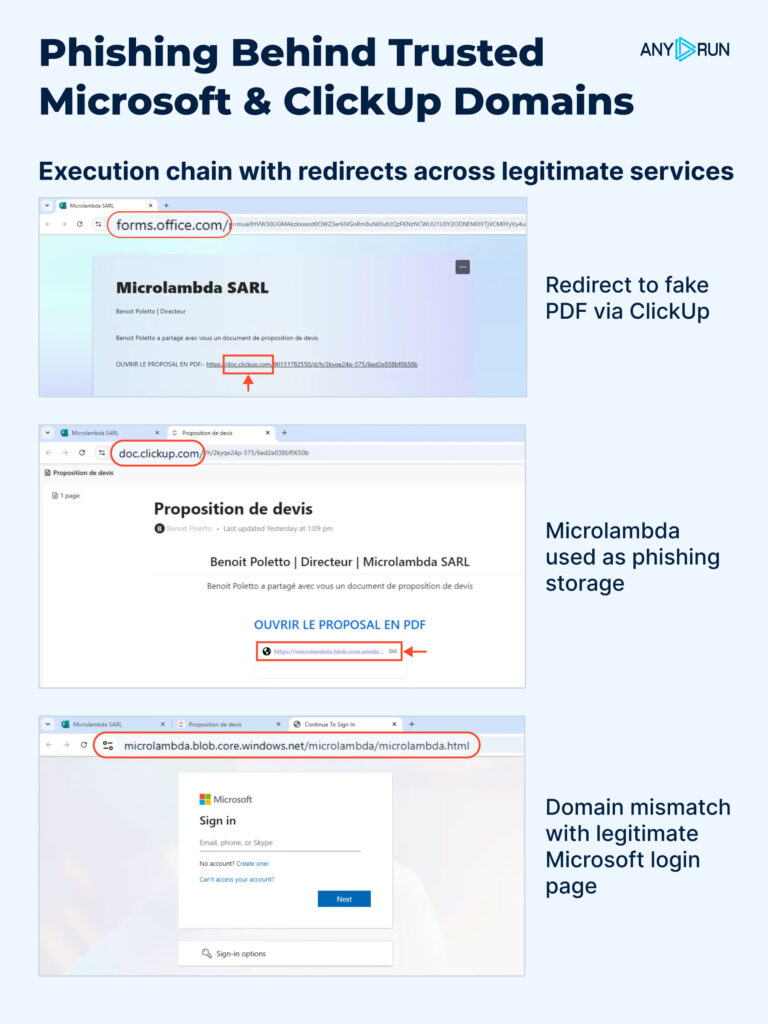
Attackers use ClickUp because public docs and prototypes are quick to create, look legitimate in inboxes, and come from a domain most organizations don’t block. Besides ClickUp, they also exploit microdot-style Microsoft endpoints and Azure Blob Storage to host the final phishing page, making the whole flow look like normal collaboration traffic.
Check a real-world case that exposes the full attack chain in ~1 minute
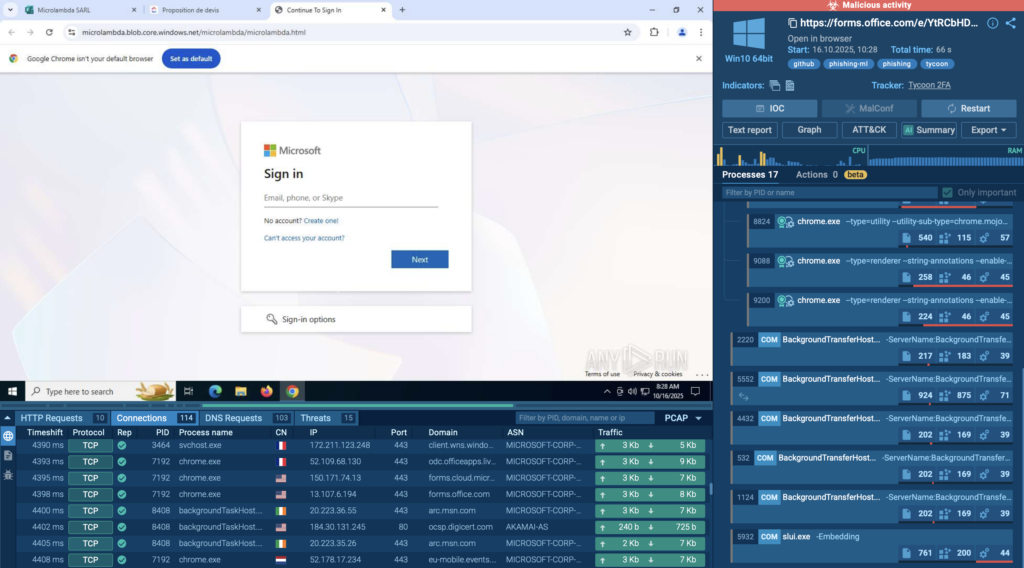
- Phishing email: Invites victim to view a shared ClickUp “document.”
- ClickUp redirect page: Host or shortener on doc[.]clickup[.]com forwards the user.
- Microsoft microdomain hop: A forms or doc endpoint (e.g., forms.office.com or other msft microdomains) is used to add legitimacy.
- Azure Blob Storage: Final hosting for the fake Microsoft login page.
- Credential exfiltration: Captured credentials POST to attacker-controlled collector.
Because every domain in the chain belongs to a legitimate provider, these campaigns are hard to detect. Filters and whitelists that trust SaaS vendors often let the traffic pass, and users are less likely to be suspicious when the URL looks familiar.
Inside ANY.RUN’s Interactive Sandbox, analysts can observe how each redirect unfolds across real Microsoft and ClickUp domains, see the credential-harvesting page render inside Azure Blob Storage, and extract live indicators for immediate defense updates. This visibility helps SOC teams shorten investigation time and enrich detection logic with behavioral context, not just URLs.
Ready-to-Use Threat Intelligence Lookup Queries
Use the following TI Lookup queries to uncover related infrastructure and track recurring phishing activity across trusted cloud providers:
Azure Blob Storage: domainName:”*.blob.core.windows.net$” AND threatName:”phishing
Microsoft Forms: domainName:”forms.office.com$” AND threatName:”phishing
ClickUp: domainName:”clickup.com$” AND threatName:”phishing”
Gathered IOCs:
- https[:]//forms[.]office[.]com/e/YtRCbHDk14
- microlambda[.]blob[.]core[.]windows[.]net
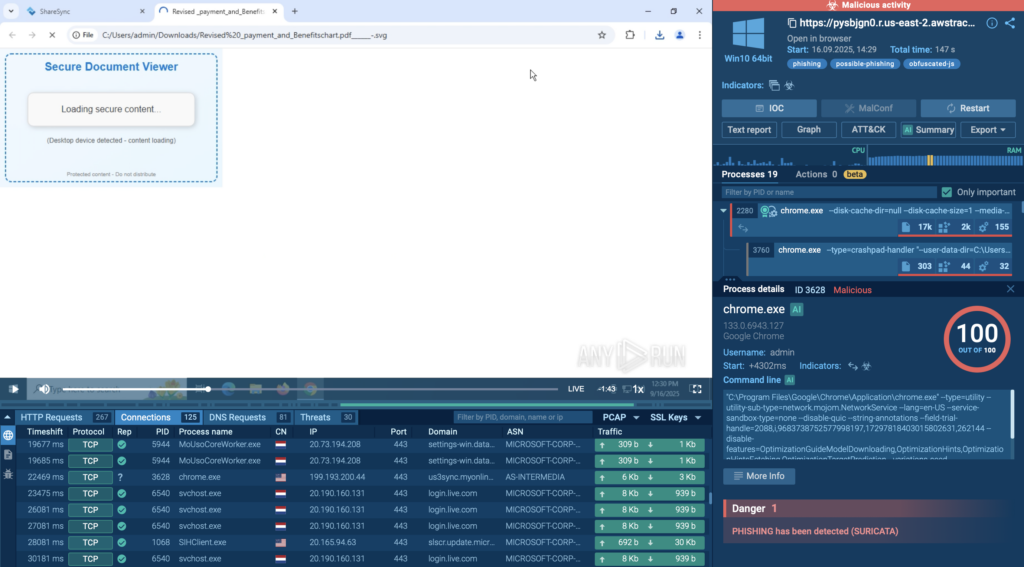
5. TyKit: New Phishkit Stealing Hundreds of Microsoft Accounts in Orgs
Detailed breakdown of TyKit attack
ANY.RUN analysts identified Tykit, a reusable phishing kit that hides JavaScript inside SVG files to push victims through a multi-stage flow and steal Microsoft 365 logins.
First seen in May 2025 with activity peaking in September–October 2025, it hits organizations across the US, Canada, LATAM, EMEA, SE Asia, and the Middle East, with notable impact on finance, government, telecom, IT, real estate, construction, professional services, education, and more.
Tykit blends redirects, basic anti-debugging, and staged C2 checks to outlast simple filters. A successful phish can lead to account takeover, data theft from mailboxes and cloud drives, lateral movement, and MFA bypass via AitM logic.
View analysis session with TyKit
How the attack unfolds:
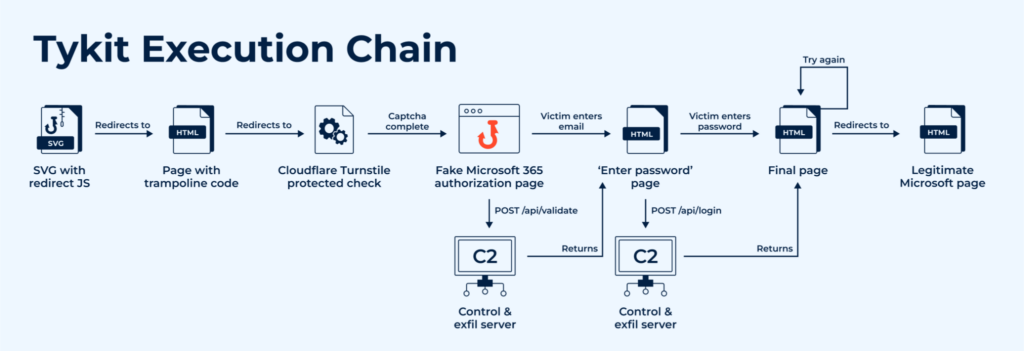
- SVG delivery → Obfuscated JS rebuilds payload and triggers redirect (eval, atob, charCodeAt patterns).
- Trampoline + CAPTCHA → Cloudflare Turnstile; blocks DevTools/context menu.
- Fake M365 sign-in → Background POST /api/validate to C2; server returns next HTML stage.
- Exfiltration → POST /api/login sends {key, redierct [sic], token, server, email, password}.
- Optional log hook → POST /x.php when server replies with status:”info”.
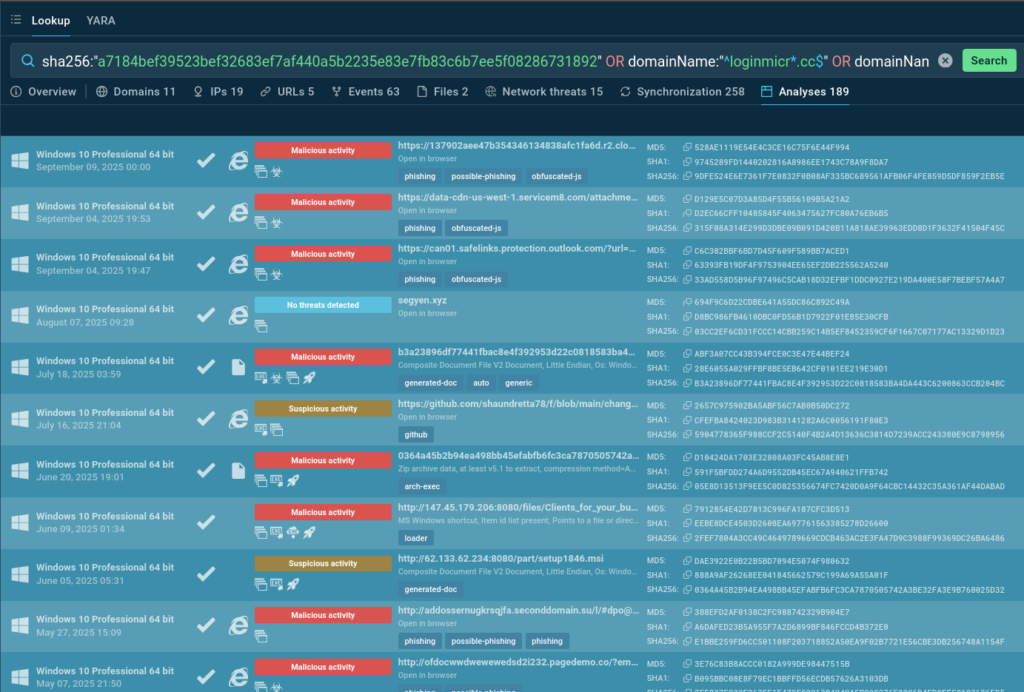
To collect all IOCs and perform a detailed case analysis, see the following TI Lookup query:
SVG/C2 pattern: domainName:”^segy.*”
Combined query: sha256:”a7184bef39523bef32683ef7af440a5b2235e83e7fb83c6b7ee5f08286731892″ OR domainName:”^loginmicr*.cc$” OR domainName:”^segy*”
How to Prevent Tykit Attacks
- Inspect SVGs: Treat SVGs as potential attack vectors; detonate them in a sandbox to reveal hidden scripts and redirects.
- Enable phishing-resistant MFA: Use FIDO2 or certificate-based methods and disable legacy authentication.
- Monitor key indicators: Watch for domains like segy*, loginmicr(o|0)s.*.cc, and POSTs to /api/validate or /api/login.
- Automate detection: Alert on Base64 /?s= parameters and integrate Threat Intelligence Feeds for fresh IOCs.
- Train and respond fast. Teach users that even image files can trigger phishing. If compromised, revoke sessions and reset credentials.
Using ANY.RUN’s Interactive Sandbox during incident response accelerates this process: analysts can safely replay the infection chain, confirm what data was exfiltrated, and extract accurate IOCs within minutes. This shortens MTTR and helps strengthen detections for the next wave of similar campaigns.
Gathered IOCs:
SHA256 (SVGs):
- ECD3C834148D12AF878FD1DECD27BBBE2B532B5B48787BAD1BDE7497F98C2CC8
- A7184BEF39523BEF32683EF7AF440A5B2235E83E7FB83C6B7EE5F08286731892
Domains & patterns:
- segy[.]zip, segy[.]xyz, segy[.]cc, segy[.]shop, segy2[.]cc
- ^loginmicr(o|0)s.*?.([a-z]+)?d+.cc$
URLs & requests:
- GET /?s=<b64_victim_email>
- POST /api/validate
- POST /api/login
- POST /x.php
Empower Your SOC with Live Visibility and Actionable Intelligence
From phishing kits and stealers to ransomware and zero-day exploits, today’s attacks evolve faster than static defenses can keep up. Investigating them manually can take hours, while attackers move in minutes. ANY.RUN helps SOC teams close that gap with real-time, interactive analysis.
Here’s how teams stay ahead:
- Expose the full attack chain instantly: Detonate suspicious files, links, or scripts in real time and see every process, redirect, and payload as it happens.
- Accelerate investigations: Live network mapping, script deobfuscation, and automatic IOC extraction cut analysis time from hours to minutes.
- Reduce MTTR by over 21 minutes per case: Clear visibility into system behavior and exfiltration flows enables faster triage and confident containment.
- Enrich detection logic automatically: Pivot from a single domain or hash in Threat Intelligence Lookup to hundreds of related submissions, revealing shared infrastructure and TTP patterns.
- Feed fresh intelligence into your stack: Integrate ANY.RUN’s Threat Intelligence Feeds with your SIEM, SOAR, or XDR for continuous updates and context-rich alerts.
For SOCs, MSSPs, and threat researchers, ANY.RUN delivers the speed, depth, and live visibility needed to turn reactive defense into proactive threat hunting and stay ahead of every new campaign.
Explore ANY.RUN’s capabilities during 14-day trial→
About ANY.RUN
ANY.RUN supports more than 15,000 organizations worldwide, including leaders in finance, healthcare, telecom, retail, and tech, helping them strengthen security operations and respond to threats with greater confidence.
Designed for speed and visibility, the solution blends interactive malware analysis with live threat intelligence, giving SOC teams instant insight into attack behavior and the context needed to act faster.
By integrating ANY.RUN’s Threat Intelligence suite into your existing workflows, you can accelerate investigations, minimize breach impact, and build lasting resilience against evolving threats.
The post Major Cyber Attacks in October 2025: Phishing via Google Careers & ClickUp, Figma Abuse, LockBit 5.0, and TyKit appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
