How to Grow SOC Team Expertise for Ultimate Triage & Response Speed
Building analyst expertise takes time, often too much…
Most new hires need over six months before they can handle complex incidents with confidence, leaving senior analysts to pick up the slack and slowing the entire SOC down.
Traditional training programs can’t keep pace with real attacks. Theories and simulations don’t prepare teams for fast, messy, real-world threats. To grow expertise faster, learning needs to happen in daily investigations, not in classrooms.
Let’s see how today’s top SOCs are building expertise faster and running 3x more efficiently.
Turning Operations into a Continuous Learning Environment
To build lasting expertise, SOC leaders need to design workflows that teach as they protect. This means giving analysts room to explore, experiment, and learn from real data, without slowing operations or risking security.
A few principles make it work:
- Expose analysts to diverse cases: Rotating tasks between triage, malware analysis, and threat hunting helps them understand the full incident lifecycle.
- Encourage safe experimentation: Allowing analysts to test hypotheses and trace attacker behavior builds critical thinking, not just reaction skills.
- Share knowledge across levels: Post-incident reviews, shared notes, and team retros create a culture where insights circulate freely, not just among seniors.
- Integrate learning metrics: Tracking how fast analysts identify patterns or make confident decisions is just as valuable as measuring mean time to detect.
When continuous safe learning becomes part of SOC design, expertise doesn’t depend on a few individuals, it scales across the entire team.
That’s where ANY.RUN’s Interactive Sandbox brings these principles to life. It provides a safe, collaborative space where analysts, regardless of experience level, can analyze real threats, test detection ideas, and learn directly from live behavior.
Explore phishing analysis example
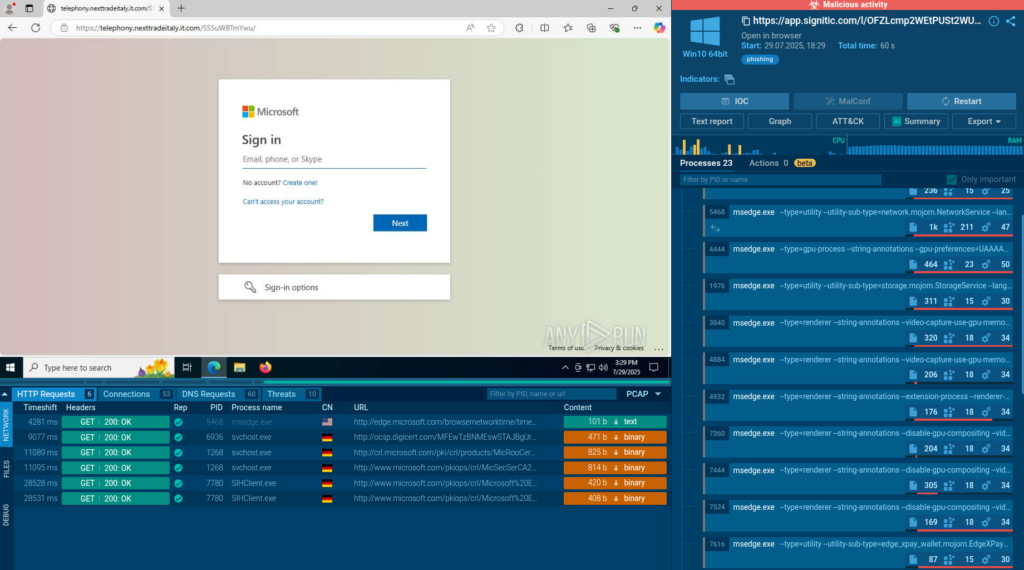
Instead of separating learning from daily operations, teams strengthen their skills through real investigations, turning each analysis into both a defensive action and a learning opportunity.
1. Fast Onboarding for Seamless Adoption
Getting new analysts up to speed is often one of the most time-consuming parts of SOC management. You can make it faster with the help of an intuitive, user-friendly interface that even junior specialists can start using right away.
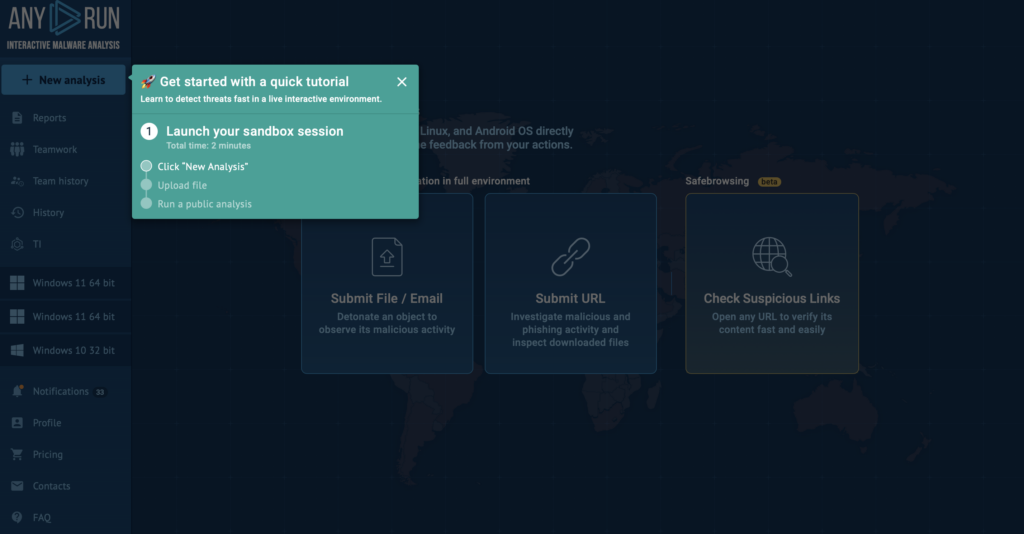
Besides, the built-in guides and quick tutorials available help new team members understand how to navigate the sandbox, launch analyses, and interpret results in just a few steps. Try it yourself by navigating to the Tutorials tab on the FAQ page.
After completing the short onboarding flow, analysts can begin investigating real samples safely, without the risk of compromising systems or making critical mistakes.
This hands-on, accessible approach saves weeks of training time and allows teams to start real analysis work much sooner.
2. Real-World Skill Development on the Job
Analysts learn best when they can interact with live attacks instead of static examples. With ANY.RUN, they can launch, observe, and engage with threats safely and without complex setup. This helps them not only perform their job tasks but also grow skills with every new analysis.
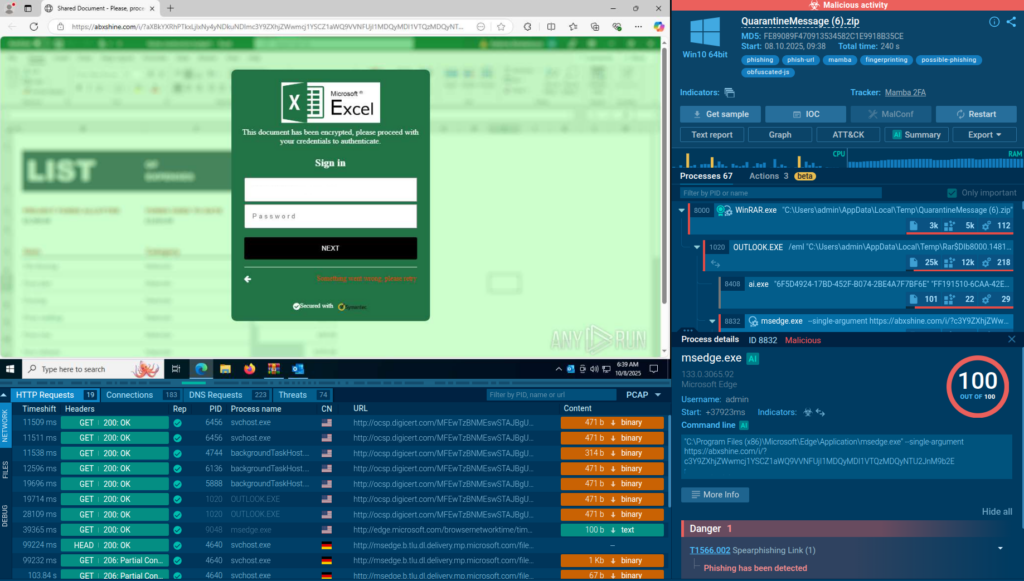
The solution’s interactivity helps analysts perform steps like solving CAPTCHAs or launching payloads from email attachments to better understand multi-stage attacks, trace malware’s activities, and uncover hidden techniques such as malicious links behind QR codes.
This direct, hands-on experience helps them recognize attack patterns faster, make confident decisions, and strengthen their investigative instincts, turning everyday analysis into a learning opportunity.
To simplify analysis, the sandbox also shows all the malicious activities in real time, which can help junior staff understand better how different attacks are carried out.
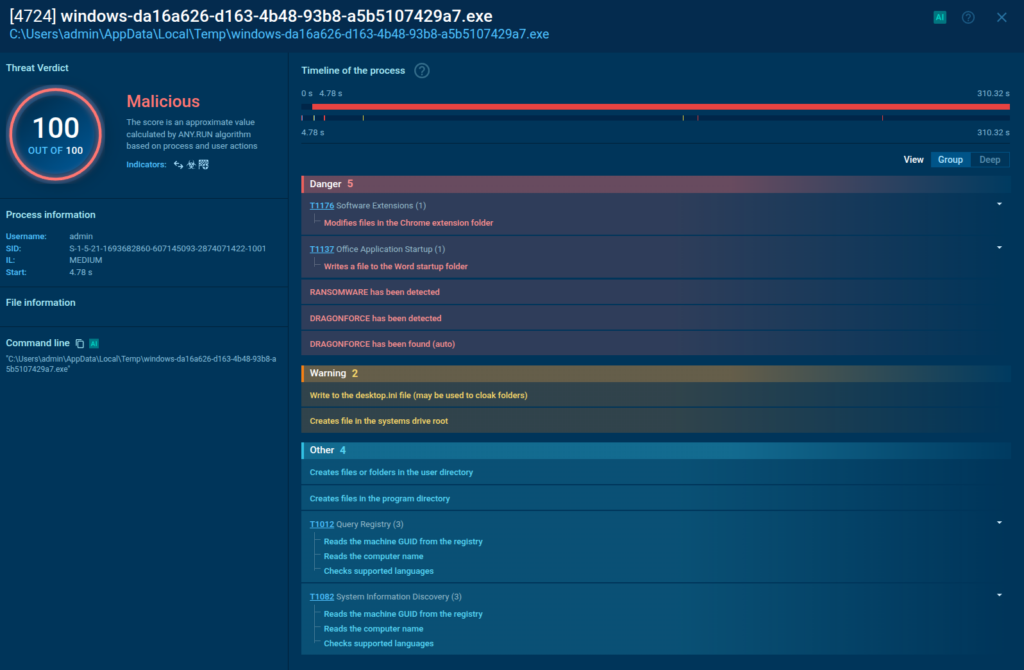
ANY.RUN flags all the important events like data exfiltration and command and control connections as they happen. It also maps these activities to the MITRE ATT&CK matrix, giving you the actionable insights you need to contain the threat.
As a result, analysts can observe the full scope of the attack and its impact in seconds.
3. AI-powered Insights for Faster, Easier Understanding of Threats
ANY.RUN’s sandbox also provides AI summaries to help analysts better understand malicious processes and improve decision-making under pressure.
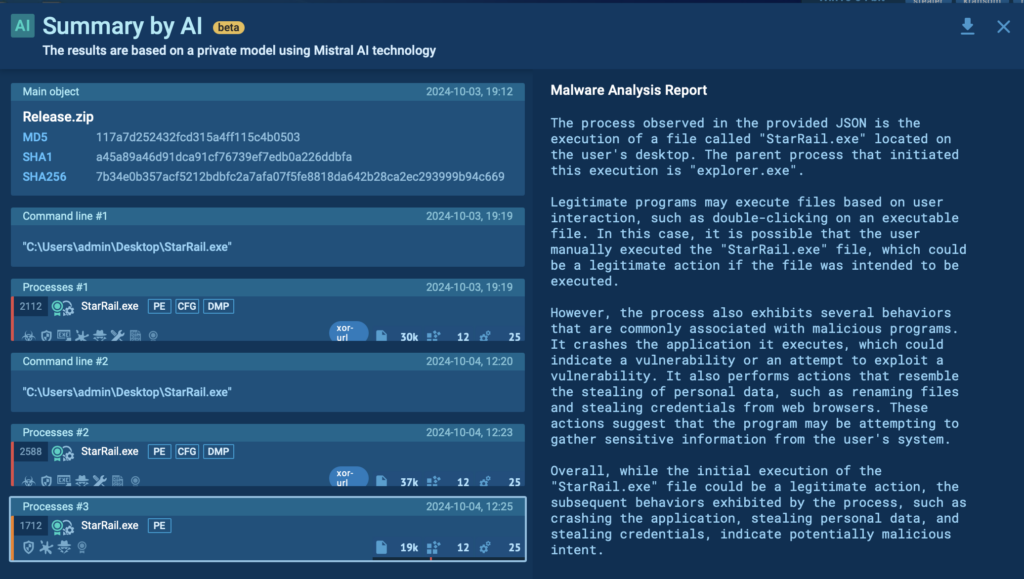
Real-time explanations of malware’s behavior enhance threat analysis skills and turns investigations into opportunities for professional growth. By embedding insights into routine analysis, the AI creates a dynamic learning environment. It bridges theory and practice and reduces the learning curve for complex concepts.
4. Community Knowledge Base of Current Threats
Important insights often stay locked in personal notes or isolated investigations. ANY.RUN helps turn that scattered knowledge into a structured, shareable resource.
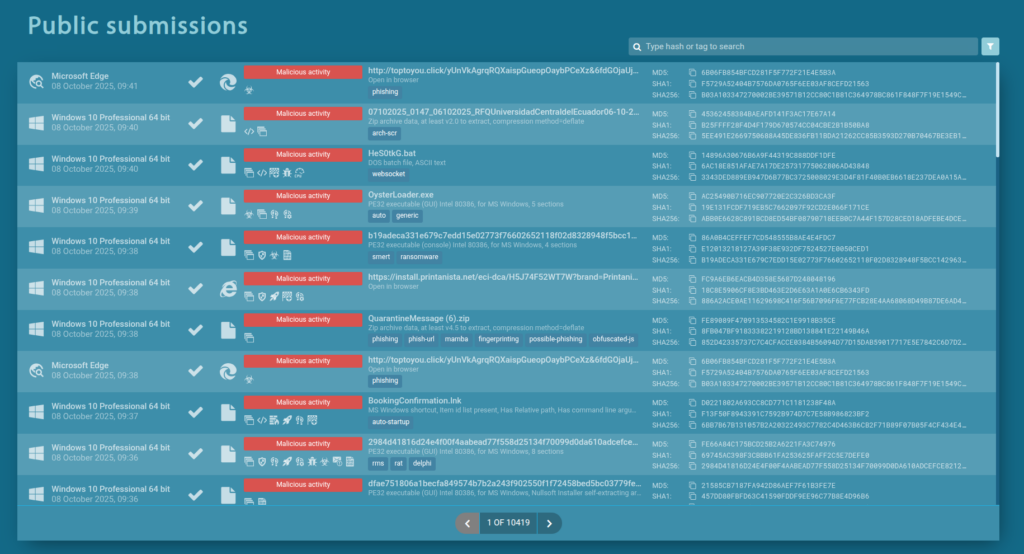
Analysts can access thousands of public analysis sessions performed daily by professionals worldwide, learn from real cases, and apply those insights to their own work.
Each public session is saved and can be studied to observe IOCs, behaviors, and MITRE ATT&CK mappings for the latest threats around the world, creating ready-to-use references for future investigations and onboarding.
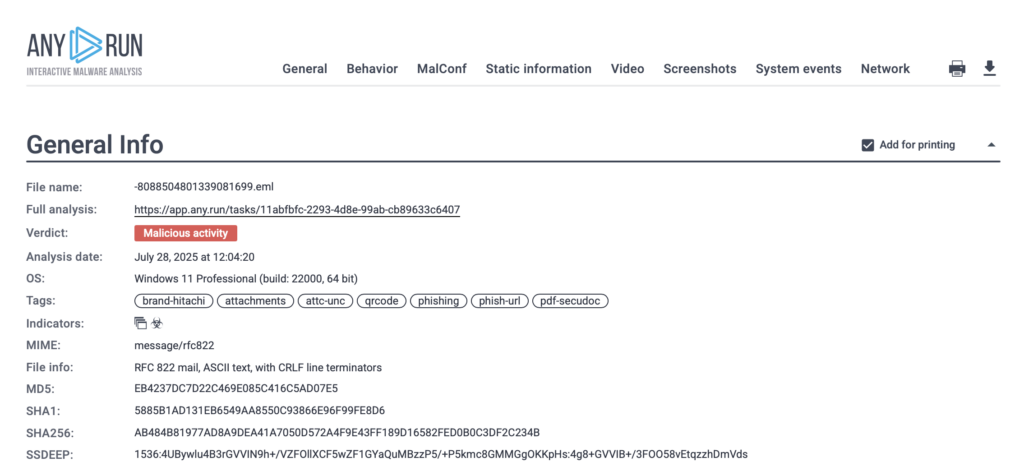
Analysts can dive into this live library of real-world attacks to further their expertise. What one analyst discovers today becomes a learning resource for many others tomorrow.
5. Collaborative Growth
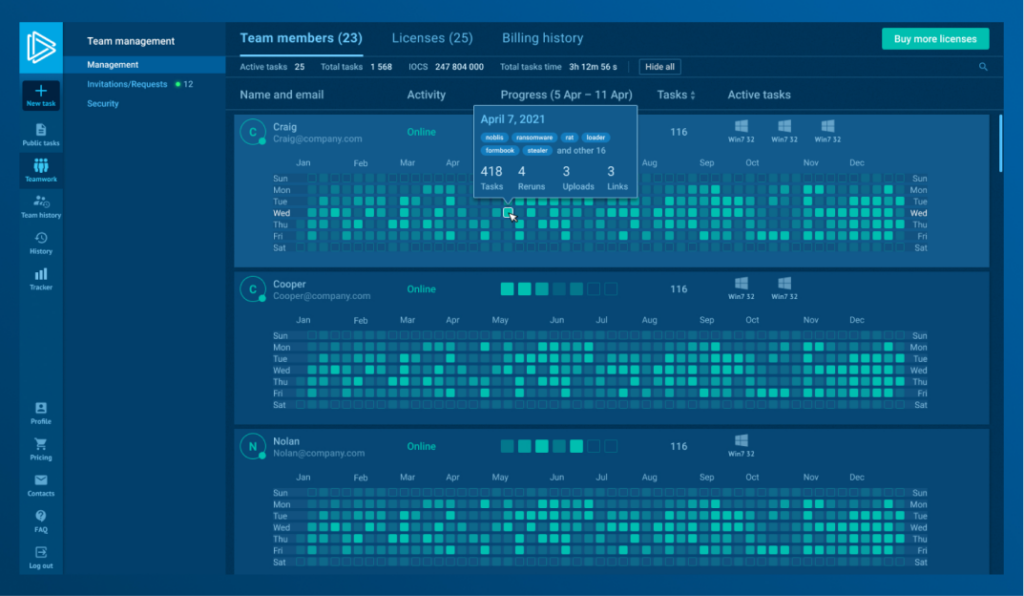
Expertise grows faster when analysts learn together. ANY.RUN’s teamwork features allow analysts to share sessions, add comments, and review investigations side by side. Junior specialists learn directly from senior peers in real cases, while leaders can track progress and assign tasks that match each analyst’s skill level.
How Practical, Hands-On Learning Transforms SOC Performance
When analysts learn through real investigations, observing, testing, and reacting to live threats, the results reach far beyond individual growth. SOCs that apply this approach with ANY.RUN’s Interactive Sandbox build stronger teams, faster workflows, and measurable returns on every training hour.
Here’s what organizations are achieving in practice:
- Faster onboarding: New analysts reach operational readiness in weeks, not months, easing pressure on senior staff.
- Up to 94% faster investigations: Real-time interaction and automation reveal malicious activity almost instantly.
- 3× higher SOC efficiency: Less manual work, more focus on validation, correlation, and proactive defense.
- Up to 20% lower Tier 1 workload: Streamlined processes reduce alert volume and repetitive tasks, freeing junior analysts for higher-value work.
- 30% fewer Tier 1 → Tier 2 escalations: Intuitive tools and better visibility empower Tier 1 analysts to resolve more incidents independently.
- Eliminated hardware setup costs: Cloud-based infrastructure removes the need for local environments and maintenance expenses.
- Lower training costs: On-the-job learning replaces expensive external programs and downtime.
- Higher engagement and retention: Analysts grow through real challenges, stay motivated, and continuously refine their skills.
This hands-on approach turns each analysis into both a defense and a growth opportunity. With ANY.RUN, organizations develop in-house expertise that compounds over time, creating SOCs that not only respond faster but continuously get better with every threat they face.
Start building a high-performing SOC with ANY.RUN Enterprise Security Solutions today!
About ANY.RUN
ANY.RUN is built to help security teams detect threats faster and respond with greater confidence. Our Interactive Sandbox delivers real-time malware analysis and threat intelligence, giving analysts the clarity they need when it matters most.
With support for Windows, Linux, and Android environments, our cloud-based sandbox enables deep behavioral analysis without the need for complex setup. Paired with Threat Intelligence Lookup and TI Feeds, ANY.RUN provides rich context, actionable IOCs, and automation-ready outputs, all with zero infrastructure burden.
The post How to Grow SOC Team Expertise for Ultimate Triage & Response Speed appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
