Phoenix: Rowhammer that works on DDR5 | Kaspersky official blog
In September 2025, researchers at ETH Zurich (the Swiss Federal Institute of Technology) published a paper introducing Phoenix, a modification of the Rowhammer attack that works on DDR5 memory modules. The authors not only demonstrated the new attack’s effectiveness against 15 tested modules, but also proposed three practical use cases: reading and writing data from memory, stealing a private encryption key stored in memory, and bypassing Linux’s sudo utility protections to escalate privileges.
The Rowhammer attack: a brief history
To understand this rather complex study, we need to first briefly revisit the history of Rowhammer. The Rowhammer attack was first described in a 2014 research paper. Back then, researchers from both Carnegie Mellon University and Intel showed how repeatedly accessing rows of memory cells could cause adjacent memory cells to change value. These neighboring cells could contain critical data — the alteration of which could have serious consequences (such as privilege escalation).
This happens because each cell in a memory chip is essentially a capacitor: a simple component that can hold an electrical charge for only a short time. That’s why such memory is volatile: turn off the computer or server, and the data disappears. For the same reason the charge in cells must be frequently refreshed — even if no one is accessing that memory region.
Memory cells aren’t isolated; they’re organized in rows and columns, interconnected in ways that can cause interference. Accessing one row can affect a neighboring row; for example, refreshing one row can corrupt data in another. For years, this effect was only known to memory manufacturers — who tried their best to mitigate it in order to improve reliability. But as cells became smaller and therefore packed more tightly together, the “row hammering” effect became exploitable in real-world attacks.
After the Rowhammer attack was demonstrated, memory developers began to introduce defenses, resulting in Target Row Refresh (TRR) hardware technology. In theory, TRR is simple: it monitors aggressive access to rows and, if detected, forcibly refreshes adjacent rows. In practice, it wasn’t so effective. In 2021, researchers described the Blacksmith attack, which bypassed TRR by using more sophisticated memory-cell access patterns.
Developers adapted again — adding even more advanced defenses against Rowhammer-like attacks in DDR5 modules and increasing the enforced refresh rate. To further impede new attacks, manufacturers avoided disclosing which countermeasures were in place. This led many to believe that DDR5 had effectively solved the Rowhammer problem. However, just last year, researchers from the same ETH Zurich managed to successfully attack DDR5 modules — albeit under certain conditions: the memory had to be paired with AMD Zen 2 or Zen 3 CPUs, and, even then, some modules remained unaffected.
Features of the new attack
To develop Phoenix, the researchers reverse-engineered the TRR mechanism. They analyzed its behavior under various memory row access patterns and checked whether the protection triggered for adjacent rows. It turned out that TRR has become significantly more complex, and previously known access patterns no longer work — the protection now correctly flags those patterns as potentially dangerous and forcibly refreshes adjacent rows. As a result, the researchers discovered that after 128 TRR-tracked memory accesses, a “window of opportunity” of 64 accesses appears, during which defenses are weaker. It’s not that the protection system completely fails, but its responses are insufficient to prevent a value change in a targeted memory cell. The second window presents itself after accessing memory cells over the course of 2608 refresh intervals.
The researchers then studied these vulnerable points in detail to deliver a highly targeted strike on memory cells while knocking out the defenses. Put simply, the attack works like this: malicious code performs a series of dummy accesses that effectively lull the TRR mechanism into a false sense of security. Then the active phase of the attack occurs, which ultimately modifies the target cell value. As a result, the team confirmed that the attack reliably worked against all 15 tested DDR5 modules manufactured by SK Hynix, one of the market leaders.
Three real-world attack scenarios
A realistic attack must change a value in a precisely defined memory region — a difficult task. Firstly, an attacker needs detailed knowledge of the target software. They must bypass multiple conventional security controls, and missing the target by just one or two bits can result in a system crash instead of a successful hack.
The Swiss researchers set out to prove that Phoenix could be used to cause real-world damage. They evaluated three attack scenarios. The first (PTE) involved accessing the page table to create conditions for arbitrary reading/writing of RAM data. The second (RSA) aimed to steal an RSA-2048 private encryption key from memory. The third (sudo) involved bypassing the protections of the standard Linux sudo utility with the aim of privilege escalation. The study’s final results are shown in this table:
[phoenix-rowhammer-attack-results.jpg]
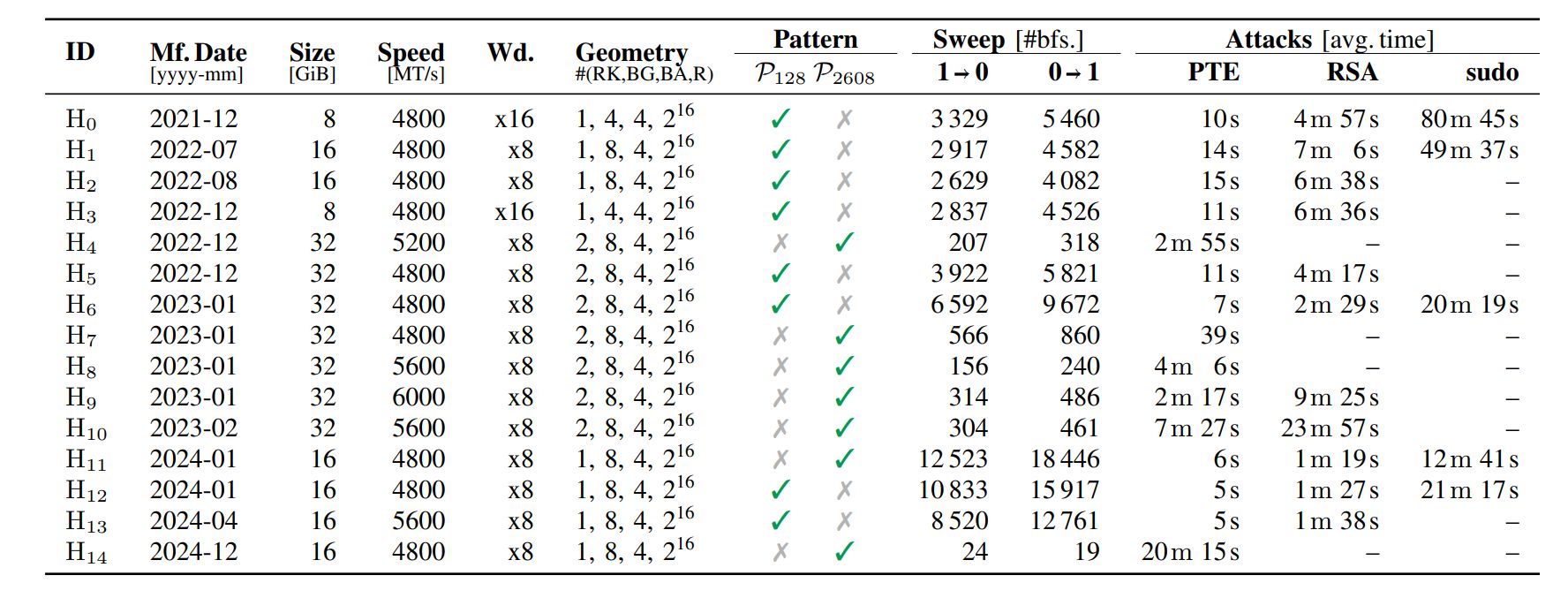
Phoenix attack effectiveness. Source
For some modules, the first attack variant (128 refresh intervals) was effective, while for others only the second (2608 intervals) method worked. In some experiments the RSA key theft and sudo exploits didn’t succeed. However, a method for arbitrary memory read/write was found for all modules, and the exploitation time was relatively short for this class of attacks — from about five seconds up to seven minutes. That’s enough to demonstrate that Rowhammer attacks pose a real risk, albeit in a highly constrained set of scenarios.
Relevance and countermeasures
The Phoenix attack shows that Rowhammer-style attacks can be carried out against DDR5 modules just as effectively as on DDR4 and DDR3. Though modules from a just single vendor were tested and the researchers uncovered a fairly simple weakness in that vendor’s TRR algorithm that will most likely be easy to fix, this is a significant step forward in the security research of memory modules.
The authors proposed several countermeasures against Rowhammer-type attacks. First, reducing the enforced refresh interval across all cells can significantly impede the attack. This may increase power consumption and chip temperature, but it’s a straightforward solution. Second, memory with an error correction code (ECC) can be used. This complicates Rowhammer attacks, although — somewhat paradoxically — it doesn’t make them completely impossible.
Beyond these obvious measures, the authors mention two more. The first is the Fine Granularity Refresh protection method, which is already being implemented. Built into the processor’s memory controller, it modifies memory-cell refresh behavior in order to resist Rowhammer attacks. As for the second, the researchers urge memory-module and chip developers to stop relying on proprietary security measures (“security through obscurity”). Instead, they recommend adopting an approach common in cryptography — where security algorithms are publicly available and subject to independent testing.
Kaspersky official blog – Read More

