ANY.RUN & MS Defender: Enrich Alerts Faster, Stop Attacks Early
Lack of context makes it hard for Security Operations Centers (SOC) to tell actual threats from false positives. ANY.RUN’s connectors for Microsoft Defender bridge this gap by automating interactive sandbox analysis and providing real-time threat intelligence for correlation.
As a result, security teams achieve faster incident resolution, reduced alert fatigue, and proactive threat detection all without disrupting existing workflows. Here’s how.
ANY.RUN & Microsoft Defender Connectors
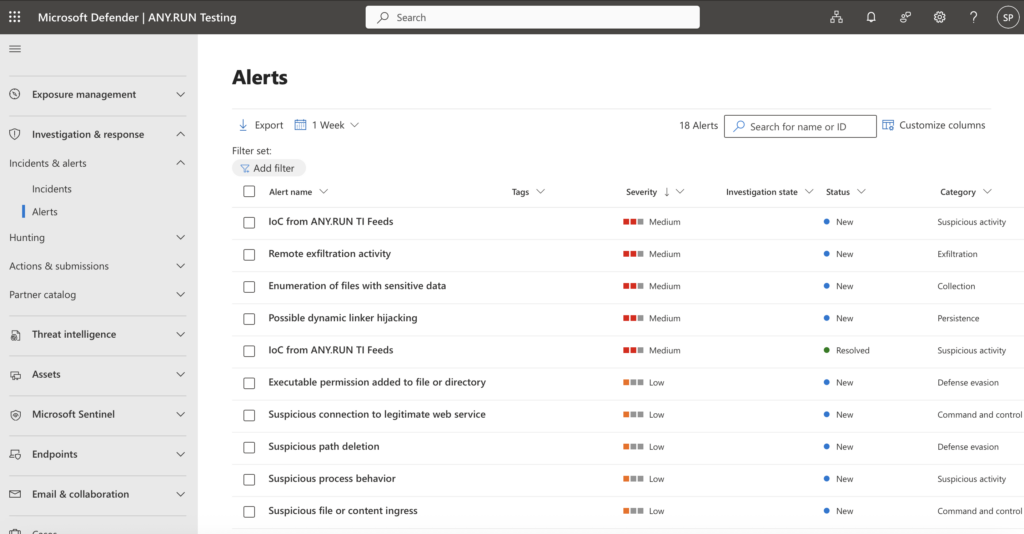
SOCs using Microsoft Defender can seamlessly connect ANY.RUN’s solutions into their existing workflows, boosting their ability to combat advanced threats seamlessly and without disrupting existing processes.
The ANY.RUN connectors include:
- Interactive Sandbox connector: Automates the analysis of suspicious files and URLs, delivering detailed behavioral insights and IOCs directly within Microsoft Defender.
- Threat Intelligence Feeds connector: Provides real-time, actionable indicators of compromise (IOCs) to enable proactive threat detection.
These connectors empower SOC teams to triage alerts efficiently, detect elusive malware, and respond to incidents faster, all while reducing operational overhead.
- Enhanced threat detection: Real-time IOCs and behavioral analysis uncover evasive and targeted attacks that signature-based systems may miss.
- Reduced Mean Time to Respond (MTTR): Automation of sandbox analysis and threat intelligence correlation cuts incident resolution time by tens of percent, enabling faster response to critical threats.
- Decreased analyst workload: By automating routine tasks like file analysis and alert enrichment, analysts can focus on high-priority incidents, reducing burnout and improving productivity.
- Improved MSSP competitiveness: Automated workflows help MSSPs meet SLAs, deliver higher-value services, and stand out in a competitive market.
- Cost efficiency: Seamless interoperability with Microsoft Defender eliminates the need for costly infrastructure changes, maximizing ROI on existing tools.
Interactive Sandbox in Microsoft Defender
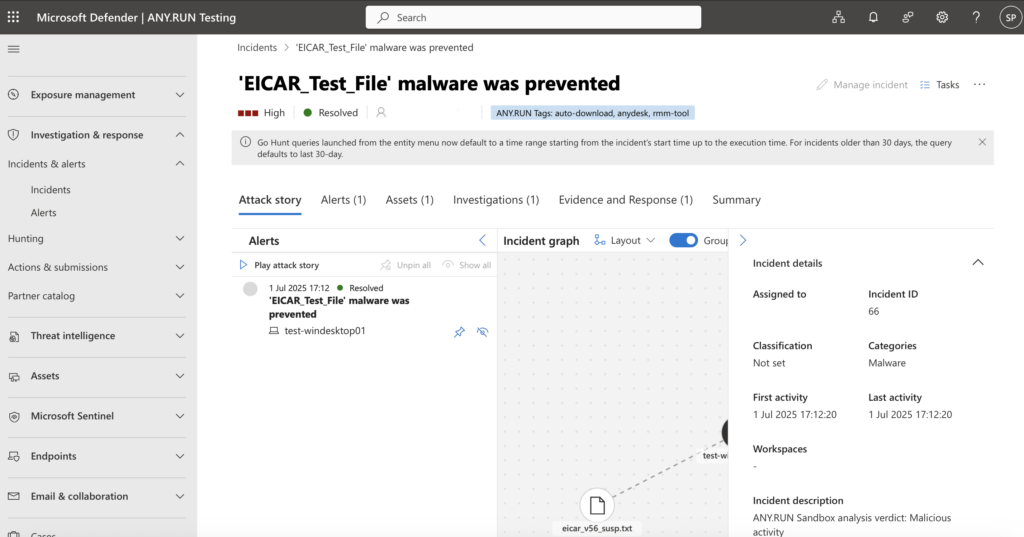
ANY.RUN’s Interactive Sandbox is a cloud-based solution offering SOC teams immediate, real-time access to Windows, Linux, and Android virtual environments for analyzing suspicious files and URLs.
With the ANY.RUN Sandbox connector in Microsoft Defender, users can:
- Submit files and URLs for analysis across Windows, Ubuntu, or Android operating systems.
- Retrieve detailed report details and IOCs in JSON or HTML formats.
- Download file submission samples and analysis network traffic dumps for deeper incident response insights.
The process is fully automated by default. The built-in playbook detects files or URLs in alerts/incidents and launches the analysis. Obtained IOCs are stored in the internal Threat Intelligence portal within Microsoft Defender.
How Interactive Sandbox Boosts Microsoft Defender Workflows
- Higher detection rate: Automated Interactivity ensures even evasive attacks are fully detonated and identified.
- Faster incident resolution: Quick sandbox analysis insights accelerate response to critical threats.
- Reduced alert fatigue: Focus only on severe incidents, while the sandbox provides verdicts for effective prioritization.
Threat Intelligence Feeds in Microsoft Defender
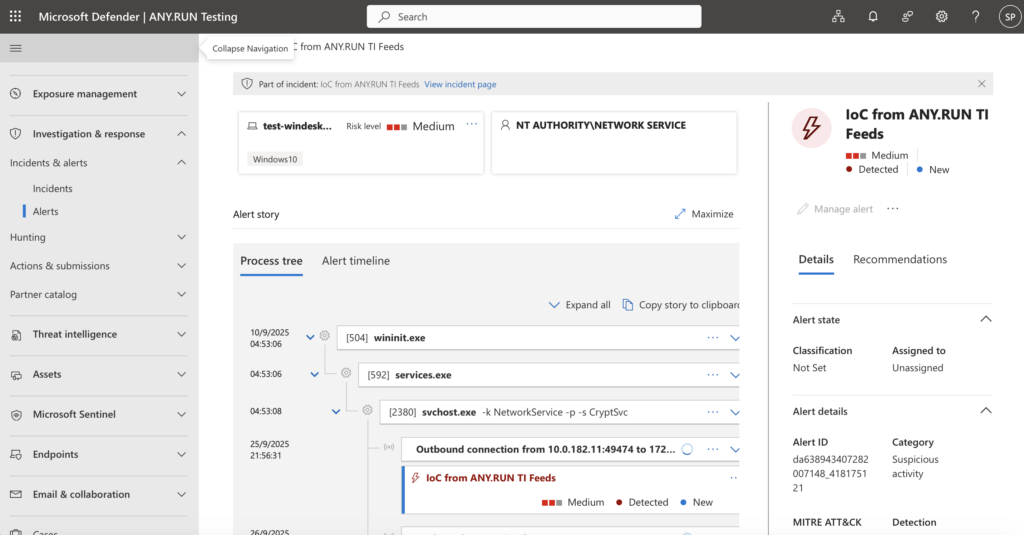
ANY.RUN’s Threat Intelligence Feeds empower SOCs and MSSPs to strengthen security with high-fidelity, actionable IOCs from real-time sandbox analysis. Indicators are continuously updated from sandbox investigations across 15,000+ organizations, delivering a curated stream of malicious IPs, domains, and URLs to detect ongoing attacks.
With the ANY.RUN Threat Intelligence Feeds connector in Microsoft Defender, users can:
- Correlate feed data with incoming alerts to identify high-risk threats.
- Use indicators to create new detection rules for proactive threat mitigation.
- Automate threat hunting and response workflows using Microsoft Defender playbooks.
Data such as IP addresses, URLs, and domains are automatically pulled into the system for analysis, playbook creation, and correlation.
The connector generates alerts if indicators from the feeds are detected in the client’s infrastructure, matching the feed entry’s status (medium, high).
How Threat Intelligence Feeds Boost Microsoft Defender Workflows
- Expanded threat coverage: Real-time IOCs from 15,000+ organizations boost SOC’s ability to detect current threats, reducing the number of possible security gaps.
- Enhanced threat prioritization: Correlating alerts with IOCs helps SOC teams identify critical risks.
- Proactive attack prevention: Fresh intelligence enables early threat detection to avoid any damage to the business.
About ANY.RUN
Trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and other critical industries, ANY.RUN helps security teams investigate threats faster and with greater accuracy.
Our Interactive Sandbox accelerates incident response by allowing you to analyze suspicious files in real time, watch behavior as it unfolds, and make confident, well-informed decisions.
Our Threat Intelligence Lookup and Threat Intelligence Feeds strengthen detection by providing the context your team needs to anticipate and stop today’s most advanced attacks.
Ready to see the difference?
Start your 14-day trial of ANY.RUN today →
The post ANY.RUN & MS Defender: Enrich Alerts Faster, Stop Attacks Early appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
