Release Notes: Fresh Connectors, SDK Update, and 2,200+ New Detection Rules
August was a busy month at ANY.RUN. We expanded our list of connectors with Microsoft Sentinel and OpenCTI, added Linux Debian (ARM) support to the SDK, and strengthened detection across hundreds of new malware families and techniques. With fresh signatures, rules, and product updates, your SOC can now investigate faster, detect more threats in real time, and keep defenses sharp against the latest campaigns.
Let’s dive into the details now.
Product Updates
New Connectors: Bringing Threat Intelligence into Your Existing Stack
We continue to expand ANY.RUN connectors so teams can work with familiar tools while boosting threat visibility. Our goal is simple: reduce setup friction and deliver fresh, high-fidelity IOCs directly into your workflows; no extra tools, no complex scripts, no wasted analyst time.
Microsoft Sentinel
ANY.RUN now delivers Threat Intelligence (TI) Feeds directly to Microsoft Sentinel via the built-in STIX/TAXII connector. That means:
- Effortless setup: Connect TI Feeds with your custom API key
- Enhanced automation: Sentinel’s playbooks automatically correlate IOCs with your logs, trigger alerts, and even block IPs.
- Cost efficiency: Maximize your existing Sentinel setup, cut false positives, and reduce breach risks with high-fidelity indicators.
- Rich context: Every IOC links back to a sandbox session with full TTPs for faster investigations and informed responses.
- Faster detection: Fresh IOCs stream into Sentinel in real time, accelerating threat identification before impact.
- Seamless interoperability: TI Feeds work natively within your Sentinel environment, so no workflows need to change.
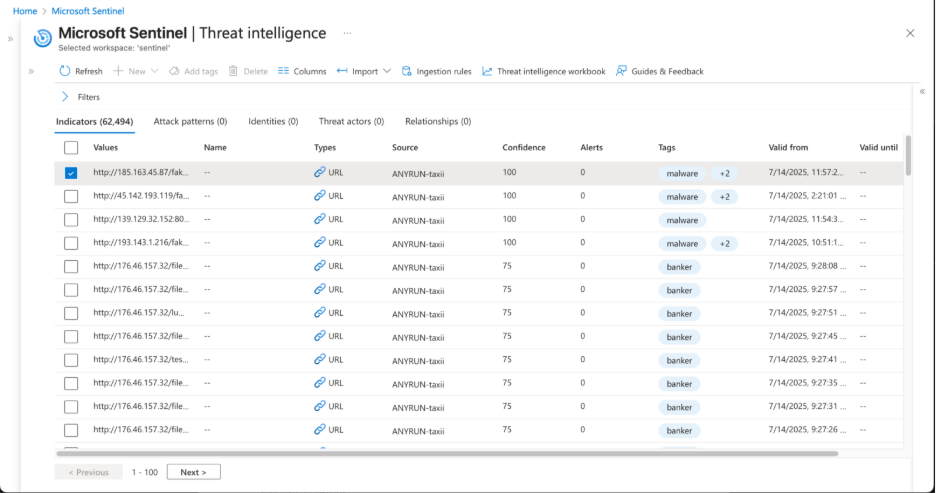
Investigations become faster and responses more precise with IOCs enriched by full sandbox context. Unlike static or delayed threat feeds, ANY.RUN’s TI Feeds are powered by real-time detonations of fresh malware samples observed across attacks on 15,000+ organizations worldwide. The data is updated continuously and pre-processed by analysts to ensure high fidelity and near-zero false positives, so your SOC can act on threats that truly matter.
OpenCTI
For SOC teams using Filigran’s OpenCTI, ANY.RUN now provides dedicated connectors that bring interactive analysis and fresh threat intelligence directly into your workflows. Instead of juggling multiple tools, analysts can analyze files, enrich observables, and track emerging threats inside the OpenCTI interface they already use.
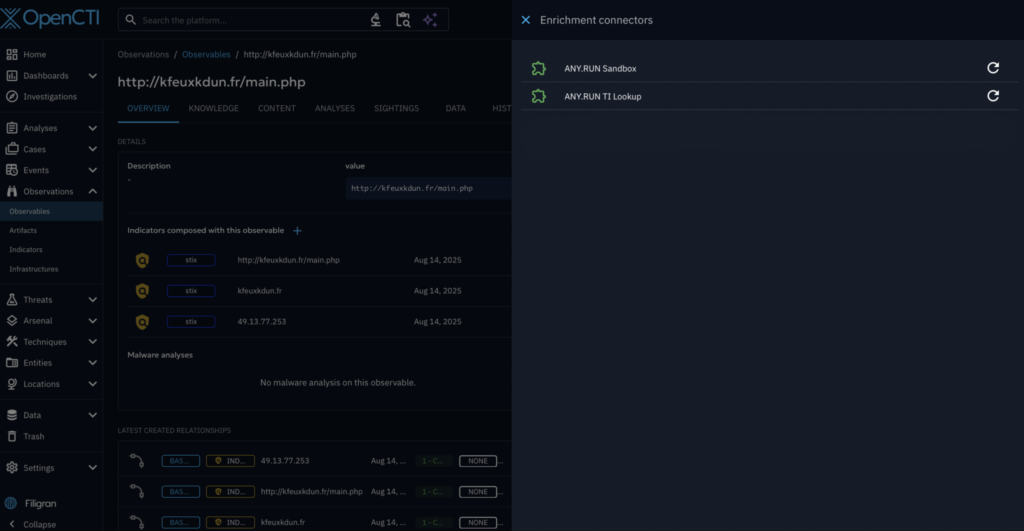
- Interactive Sandbox: Automate analysis of suspicious files and URLs to quickly understand their threat level, TTPs, and collect IOCs.
- Threat Intelligence Lookup: Enrich observables with threat context based on fresh live attack data.
- Threat Intelligence Feeds: Stay updated on the active threats with filtered, actionable network IOCs from the latest malware samples.
You can connect any combination of these connectors based on their specific needs and licenses.
View documentation on GitHub →
SDK Update: Linux Debian (ARM) Support
We’ve expanded our software development kit (SDK) to include Linux Debian 12.2 (ARM, 64-bit) in the Linux connector. This addition ensures that analysts can now automate malware analysis for ARM-based threats alongside Windows, Linux x86, and Android, all from the same SDK.
With this update, your team can:
- Submit ARM samples for automated analysis and retrieve detailed reports.
- Collect IOCs, IOBs, and IOAs from Debian (ARM) environments in real time.
- Integrate ARM analysis seamlessly into SIEM, SOAR, or XDR workflows without extra tools.
ARM-based malware is rapidly expanding across IoT, embedded systems, and cloud servers. By adding Debian ARM support, the SDK gives SOCs earlier visibility into these threats and helps reduce costs by keeping all environments under one automated process.
Explore ANY.RUN’s SDK on GitHub
Threat Coverage Update
In August, our team continued to expand detection capabilities to help SOCs stay ahead of evolving threats:
- 104 new signatures were added to strengthen detection across malware families and techniques.
- 14 new YARA rules went live in production, boosting accuracy and enabling deeper hunting capabilities.
- 2,124 new Suricata rules were deployed, ensuring better coverage for network-based attacks.
These updates mean analysts get faster, more confident verdicts in the sandbox and can enrich SIEM, SOAR, and IDS workflows with fresh, actionable IOCs.
New Behavior Signatures
In August, we introduced a new set of behavior signatures to help SOC teams detect obfuscation, persistence, and stealthy delivery techniques earlier in the attack chain. These detections are triggered by real actions, not static indicators, giving analysts deeper visibility and faster context during investigations.
This month’s coverage includes new families and techniques across stealers, lockers, loaders, and RATs:
YARA Rule Updates
In August, we released 14 new YARA rules into production to help analysts detect threats faster, improve hunting accuracy, and cover a wider range of malware families and evasion tactics. Key additions include:
- YANO – Stealer detection
- BABEL – Obfuscation coverage
- DNGuard – Packer/obfuscator detection
New Suricata Rules
We also added 2,124 targeted Suricata rules to help SOC teams catch data exfiltration and phishing campaigns more reliably. Highlights include:
- Salty2FA exfiltration activity (sid:85002719): Detects emerged phishkit’s pattern of retrieving stolen credentials
- Salty2FA TLD domain chain (sid:85002796): Tracks Salty2FA infrastructure by usage of domain names in .*.com & .ru TLD-zones in specific order
- Rhadamanthys stage-payload HTTP request (sid:85002618): Identifies stealer activity by specific web request for additional payload
Other Updates
- Updated extractor – improved parsing for modern samples
- Updated Lumma rule – enhanced detection for new campaign variants (sample)
About ANY.RUN
ANY.RUN supports over 15,000 organizations across banking, manufacturing, telecom, healthcare, retail, and tech, helping them build faster, smarter, and more resilient cybersecurity operations.
Our cloud-based Interactive Sandbox enables teams to safely analyze threats targeting Windows, Linux, and Android systems in under 40 seconds; no complex infrastructure required. Paired with TI Lookup, YARA Search, and Threat Feeds, ANY.RUN empowers security teams to accelerate investigations, reduce risk, and boost SOC efficiency.
The post Release Notes: Fresh Connectors, SDK Update, and 2,200+ New Detection Rules appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
