Streamline Your SOC: All-in-One Threat Detection with ANY.RUN
Running a SOC means living in a world of alerts. Every day, thousands of signals pour in; some urgent, many irrelevant. Analysts need to separate noise from real threats, investigate quickly, and keep the organization safe without letting cases pile up.
The challenge isn’t only about detecting threats but doing it fast enough to reduce escalations, avoid burnout, and keep operations efficient.
That’s where an all-in-one detection workflow changes everything. ANY.RUN brings together the tools analysts rely on most; live threat feeds, interactive sandboxing, and instant lookups, into a single, streamlined process. The result: faster answers, fewer escalations, and more confidence in every decision.
Why Fragmented Workflows Slow SOCs Down
It’s not the flood of alerts alone that puts SOCs under pressure but the fractured way they’re handled. One tool for threat feeds, another for detonation, a third for enrichment. Every time an analyst switches context, minutes are lost. Multiply that across hundreds of alerts, and the delays add up fast.
The bigger problem is what those delays cause: escalations that didn’t need to happen, senior staff tied up with routine checks, and threats that linger longer than they should. Instead of building momentum, investigations stall.
This is the hidden cost of disconnected tools. They don’t only slow analysts down but also create more work for everyone and open the door to mistakes.
From Chaos to Clarity: The Power of Unified Workflow
When detection runs as one continuous workflow, every step strengthens the next. Instead of losing time hopping between tools, analysts work with a steady flow:
- Noise gets filtered early: Live feeds rule out known threats, reducing case load by up to 20% and cutting unnecessary escalations by 30%.
- Investigations move faster: The sandbox reveals hidden behavior in real time, lowering MTTR by as much as 21 minutes per case.
- Decisions are backed by context: Lookups provide history from millions of past analyses contributed by 15,000+ organizations, giving analysts 24× more IOCs to work with and ensuring every case is backed by evidence.
| The result is measurable: |
|---|
| +62.7% more threats detected overall |
| 94% of surveyed users report faster triage |
| 63% year-over-year user growth, driven by analyst efficiency |
| 30% fewer alerts require escalation to senior analysts |
The outcome of this unified workflow is speed, clarity and confidence. Analysts know what to act on, what to ignore, and when a case can be closed without doubt.
Threat Feed: Cut Through the Noise
The first challenge in any SOC is deciding which alerts deserve attention. With live IOC streams collected from thousands of users worldwide, ANY.RUN’s TI Feeds works as your early filter. Analysts see instantly whether an IP, domain, or hash has already been confirmed as malicious and can rule out duplicates on the spot. That means less time wasted on “non-issues” and more focus on real threats that matter.
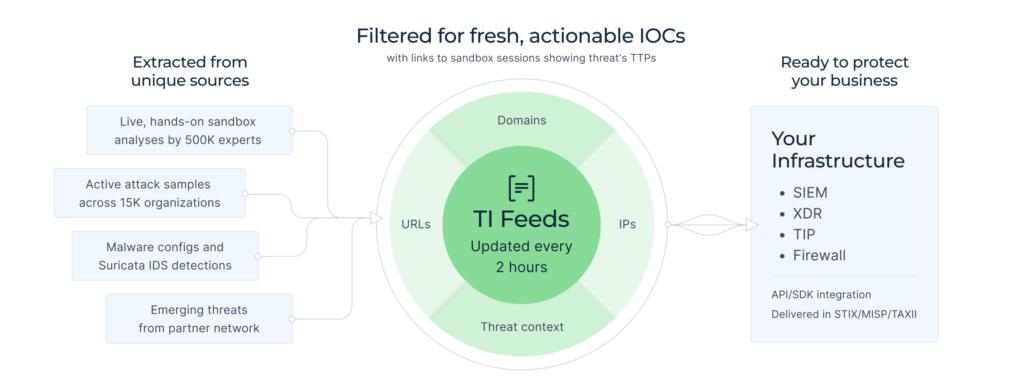
Every IOC in the feed is actionable and connected to sandbox analyses, giving analysts not just a red flag but the full context behind it. This means faster triage, more confident decisions, and the ability to trace threats back to their behavior in real-world samples.
The numbers speak for themselves: with Threat Feed and Lookup combined, analysts gain access to 24× more IOCs than from typical isolated sources. And because the feed captures real-world attacks, from targeted phishing campaigns to large-scale malware hitting banks and enterprises, your SOC works with threat data that reflects the real distribution of risks.
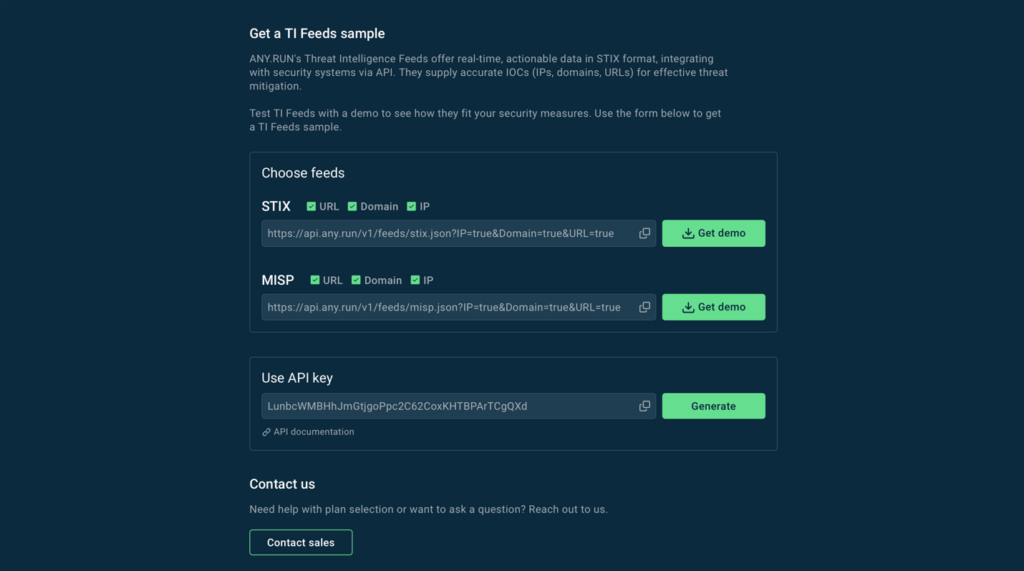
ANY.RUN’s Threat Intelligence Feeds come in multiple formats with simple integration options, making it easy to plug into your existing SIEM, TIP, or SOAR setup.
Interactive Sandbox: See the Whole Picture
When an alert passes the filter, it needs proof. This is where ANY.RUN’s interactive sandbox becomes the proving ground, turning suspicious files, scripts, and URLs into full investigations in real time. Instead of waiting for static reports or snapshots, analysts can detonate samples and watch the behavior unfold step by step, just like a real user would.
This approach uncovers what traditional sandboxes often miss:
- Hidden payloads that require clicks or triggers to activate.
- Staged downloads that reveal themselves only over time.
- Evasive tactics designed to bypass automated detection.
But visibility doesn’t depend solely on manual clicks. With automated interactivity, ANY.RUN simulates user actions to expose threats faster, reducing the need for analysts to intervene at every step. Junior analysts gain confidence because the system highlights behaviors for them, while senior staff can focus on advanced investigations instead of routine triage.
The user-friendly interface and AI assistance add another layer of efficiency. Complex behaviors are explained clearly, reports are well-structured, and the entire attack chain is mapped from start to finish.
For example, in the case of Lumma Stealer, ANY.RUN captured the full infection chain, from initial dropper to persistence mechanisms, all preserved in a detailed report ready for escalation, rule writing, or sharing.
View Lumma Stealer exposed in 30 seconds
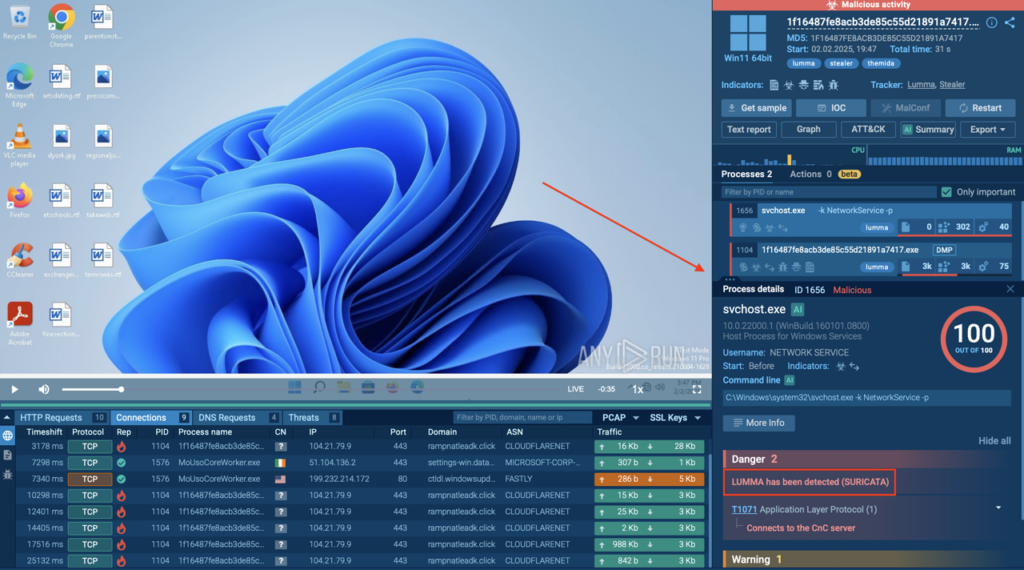
The outcome is a process where analysts of all skill levels can act faster, escalate less, and make decisions with confidence, while SOC leaders gain time back from their most experienced staff.
Threat Lookup: Context at Your Fingertips
Even with full sandbox results, one question always remains: Has this threat been seen before? Knowing whether an IOC belongs to a fresh campaign or something already circulating across industries changes how analysts respond.
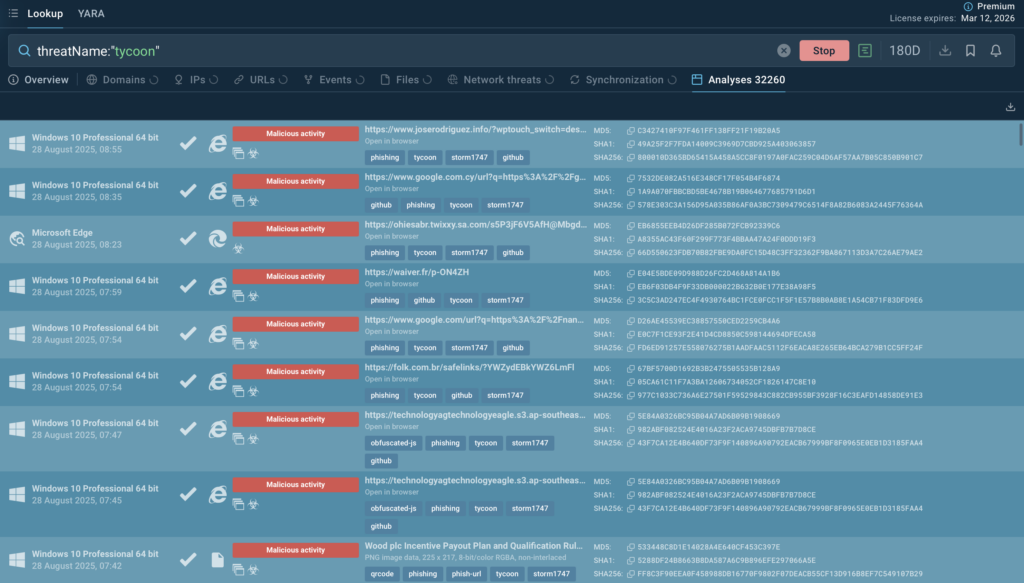
ANY.RUN’s Threat Lookup delivers that answer in seconds. With access to millions of past analyses contributed by more than 15,000 organizations worldwide, analysts can instantly check whether an IP, domain, or hash has been observed elsewhere. This turns isolated alerts into patterns, helping teams connect the dots and react with confidence.
- Early warning from others’ incidents: What hits one enterprise today could reach yours tomorrow. Lookup lets you learn from global telemetry before the threat arrives at your doorstep.
- Deeper reporting without heavy lifting: Instead of manually searching across multiple feeds and databases, analysts enrich findings with one query.
- Reduced unnecessary escalations: Confirmation from millions of past cases means analysts can validate faster and close tickets sooner.
The result is a smoother close to every investigation: sandbox analysis provides the behavior, Threat Lookup adds the history, and reports go out with stronger evidence. Analysts save time, senior experts get fewer escalations, and the SOC becomes more resilient with every case resolved.
Turn Detection Into One Continuous Workflow
The real power of ANY.RUN is in how the solutions work together, seamlessly feeding into one another to create a single, continuous process.
Instead of bouncing between disconnected tools, analysts move through one streamlined workflow: alerts are filtered at the start, suspicious activity is detonated, the entire attack chain is exposed in real time, and findings are instantly validated against global threat history.
The outcome is faster resolutions, fewer unnecessary escalations, and reports enriched with both behavioral detail and historical context; the kind of evidence leaders and clients can trust.
Sign up today to see how ANY.RUN’s all-in-one suite can turn your SOC into a faster, more confident detection machine.
The post Streamline Your SOC: All-in-One Threat Detection with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

