Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders
As we highlighted in our article on building threat resilience in enterprises, one of the key challenges that stand before CISOs is ensuring proactive security. Reacting to incidents is no longer enough; you need to anticipate upcoming threats.
To achieve this, your team needs powerful solutions that meet your criteria and deliver fast results. Explore our step-by-step guide on integrating threat intelligence into your workflow with ANY.RUN’s TI Lookup and TI Feeds, solutions trusted by 15,000+ organizations across diverse industries.
Find a Source for Intel That Fits Your SOC
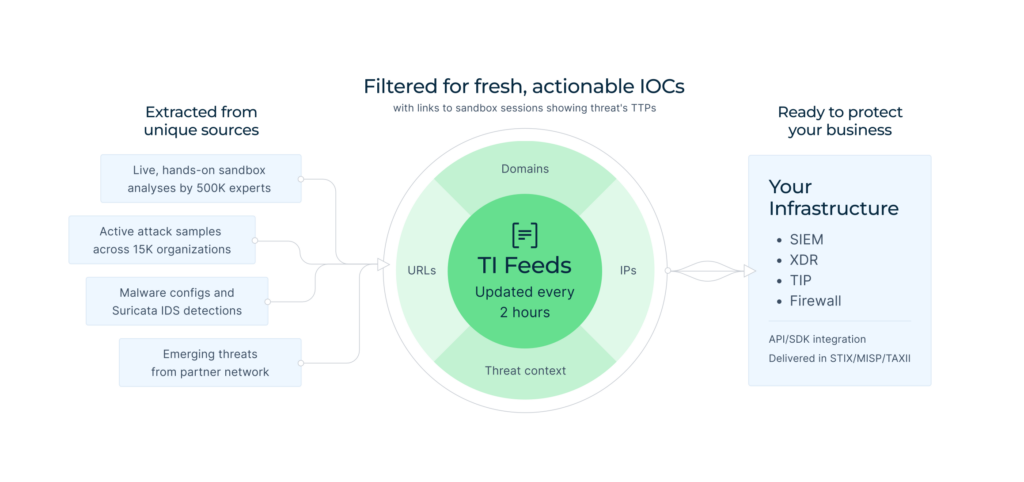
Threat intelligence is a crucial component of modern SOC operations. Implementing it increases threat detection rates, speeds up incident response, and strengthens overall defense against emerging threats.
When choosing a threat intel solution, prioritize reliability of data, rich context that comes with indicators, and constant updates that will keep you on top of things.
Being an enterprise-grade service, Threat Intelligence Feeds meets these standards. It delivers fast, fresh intelligence gained from threat investigations by 15,000 SOC teams. Each indicator, be that IP, domain, or URL, is linked to ANY.RUN’s Interactive Sandbox analysis of malware, enabling you to observe its impact, activities, and overall context in one click.
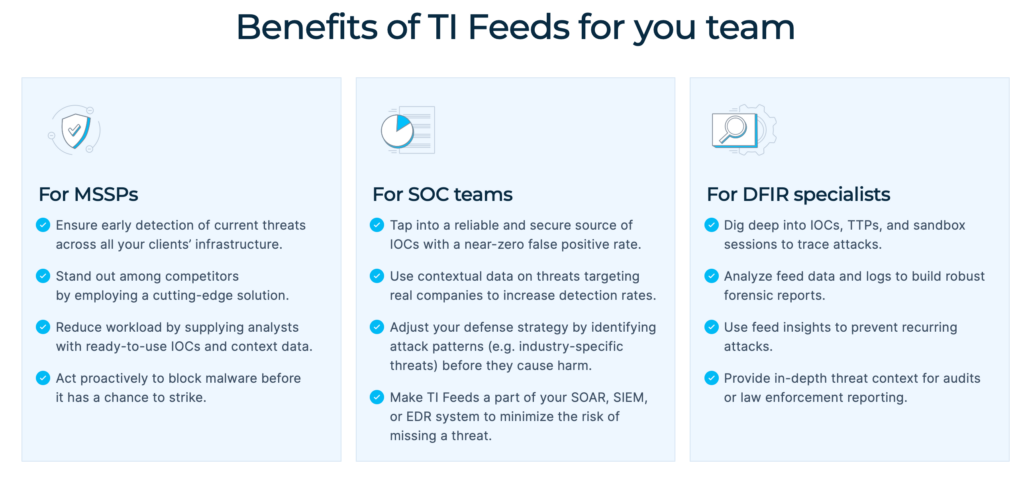
Enrich your SIEM, TIP, or XDR system with TI Feeds for:
- Expanded Coverage: ANY.RUN’s exclusive IOCs come from Memory Dumps, Suricata IDS, in-browser data, and internal threat categorization systems, increasing the chance of detection of the most evasive threats.
- Reduced Workload: The indicators are pre-processed to avoid false positives and ready to be used for malware analysis or incident investigation.
- Informed Response: Rich metadata provided for IOCs gives you the context for in-depth threat investigations and faster response.
Bridge the Gap Between Analysts and Threat Data
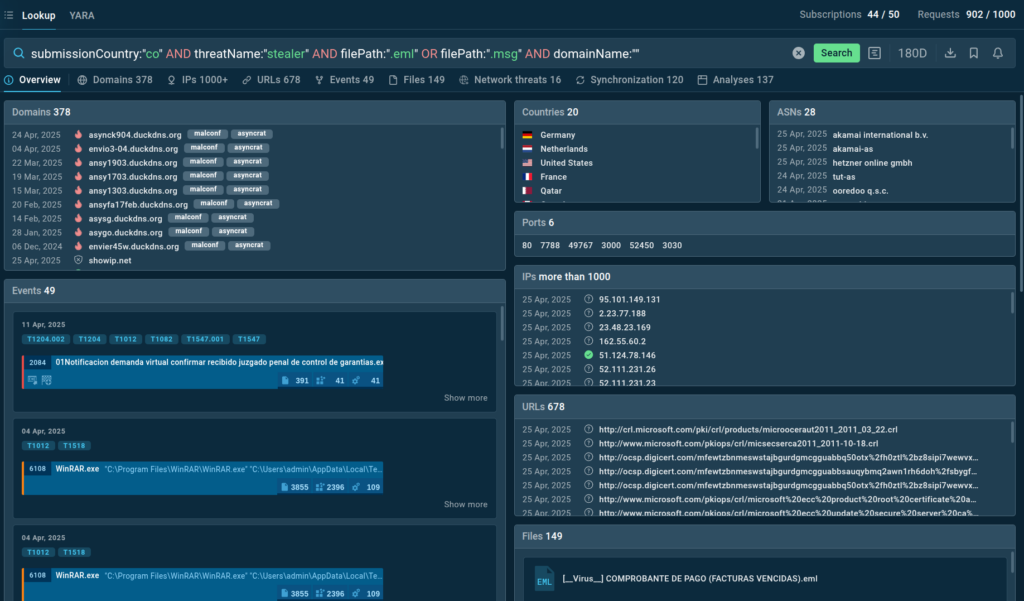
Steady monitoring and expanded threat coverage provided by solutions like TI Feeds are important for maintaining a robust defense system. The next challenge is finding a way to browse, identify, and enrich indicators quickly.
In other words, you need targeted, fast access to threat intelligence, for both proactive threat hunting and swift incident response. That’s just what Threat Intelligence Lookup provides. For analysts, it’s like a fishing rod with which they can catch exactly what they’re looking for in the sea of extensive data on threats: for example, quick verdicts on suspicious IPs or additional info on malicious indicators.
Equipping your team with TI Lookup means that your SOC will reach:
- Faster Triage and Data-Fueled Response: Check any indicator in seconds, identify malicious activity, and enriched it with more info.
- Higher Expertise Levels: Your team members can explore actual attacks, see how they unfold and what TTPs are in use, gaining insights into modern malware.
- Improved Proactive Defense: Use intel to develop new develop SIEM, IDS/IPS, or EDR rules for acting in advance.
Even the free version of TI Lookup makes it possible to achieve these results.
To conduct private analyses, gain three times more info on threats, and integrate TI Lookup into your system, choose Premium plan and:
- Hunt Threats with Precision: Create and explore custom YARA rules in ANY.RUN’s database to detect malware patterns.
- Reduce Risks of Breaches: Fast and accurate access to intelligence is a game-changer for alert triage and incident response, minimizing the likelihood of successful attacks.
- Deepen Investigations: Fine-tune your queries with 40+ parameters and browse not only IOCs, but also IOAs and IOBs.
- Track Malware Trends: See Threat Intelligence Reports written by expert analysts and stay informed on latest industry-wide attacks.
As result, every stage of SOC operations will become sharper, faster, and more strategic.
Make Threat Intelligence a Part of Your Infrastructure
For teams, it’s more effective to use flexible services available for integration, rather than standalone solutions. That’s how you create a coordinated, resource-efficient defense system.
ANY.RUN offers wide opportunities for integration, including API and SDK, as well compatibility with a majority of vendors, such as IBM QRadar, ThreatConnect, OpenCTI.
- Automate Threat Monitoring: Connecting TI solutions to your SIEM, TIP, or SOAR system results in accelerated, more efficient workflow.
- Expand Threat Coverage: For centralized protection, TI Feeds offer continuously updated stream of fresh intel available in STIX/TAXII and MISP.
- Improved Detection Rate: Turn to TI Lookup to increase your detection capabilities, correlate indicators from over 15,000 global attacks for early detection, and enrich your threat investigations.
- No Alert Overload: Reduce workload of Tier 2 and 3 specialists, empowering Tier 1 analytics to make informed decisions based on actionable and reliable threat intelligence.
Use Cases: Applying This Strategy In Real Life
Implementing threat intelligence into your security operations doesn’t mean increasing workload. It’s actually the opposite. Here are three real-world use cases explaining how quality TI solutions can address common SOC challenges.
Improving Speed and Confidence for Incident Response
The right solution can make a huge impact for your SOC team. It enables analysts to handle incidents faster and with more confidence, boosting overall efficiency.
For example, analysts can use TI Lookup for a quick check of an indicator. Enter this simple query like:
domainName:”smtp.godforeu.com”
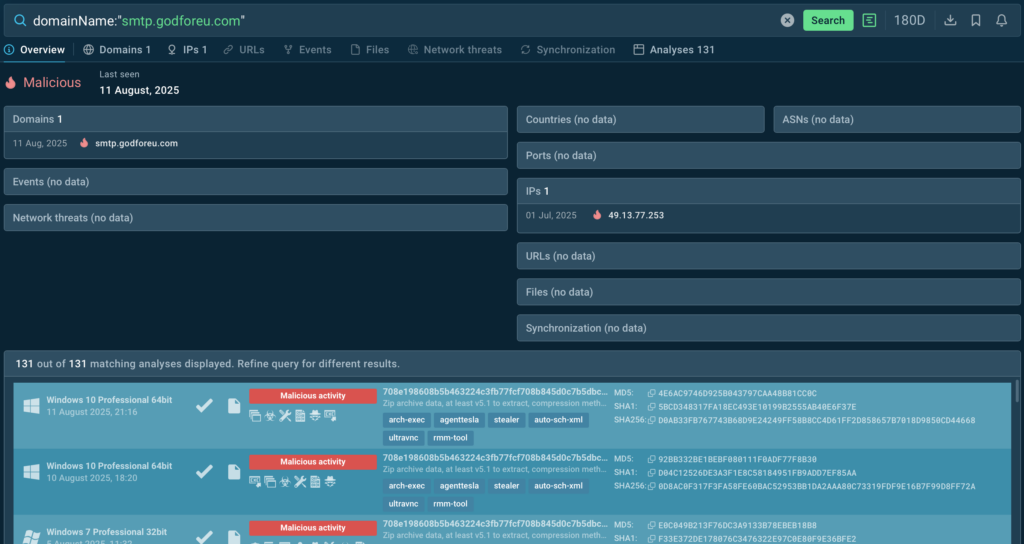
And within seconds, you’ll know that that this domain is malicious. Next step doesn’t take much either: click one of the linked analyses and you’ll see how exactly malware behaves and which processes it affects.
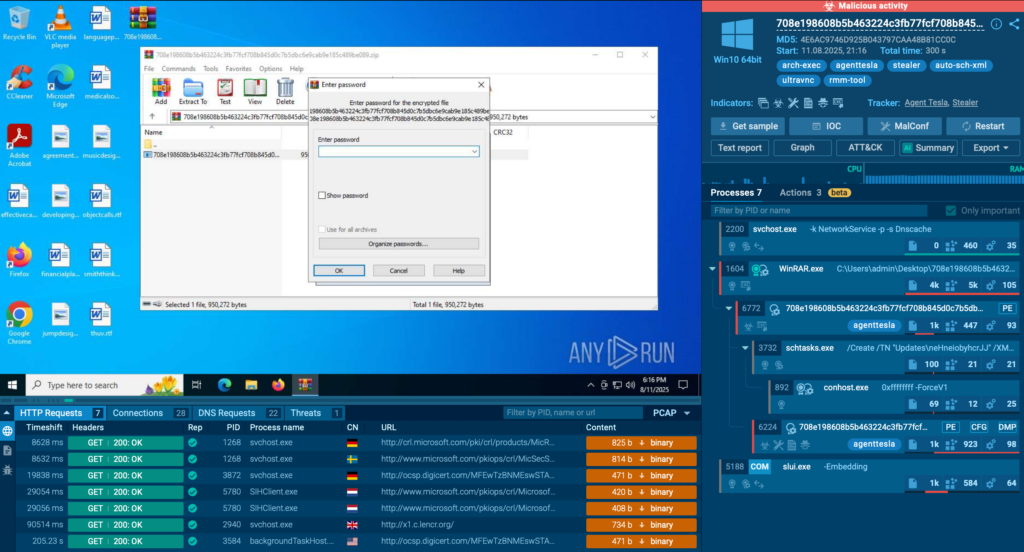
And finally, block this threat—and the incident is solved. That’s how you make informed decisions effortlessly and quickly: you just need to know where to find data.
Increase Detection Rate
Another use case for TI Lookup is reviewing alert backlog data, where evasive threats might be hidden. Instead of spending time on manual research, you quickly check any suspicious fragment, such as a command line:
And you’ll find out whether it was a false alarm. In this case, it wasn’t. The command line is actually related to steganography attacks spread by AsyncRAT:
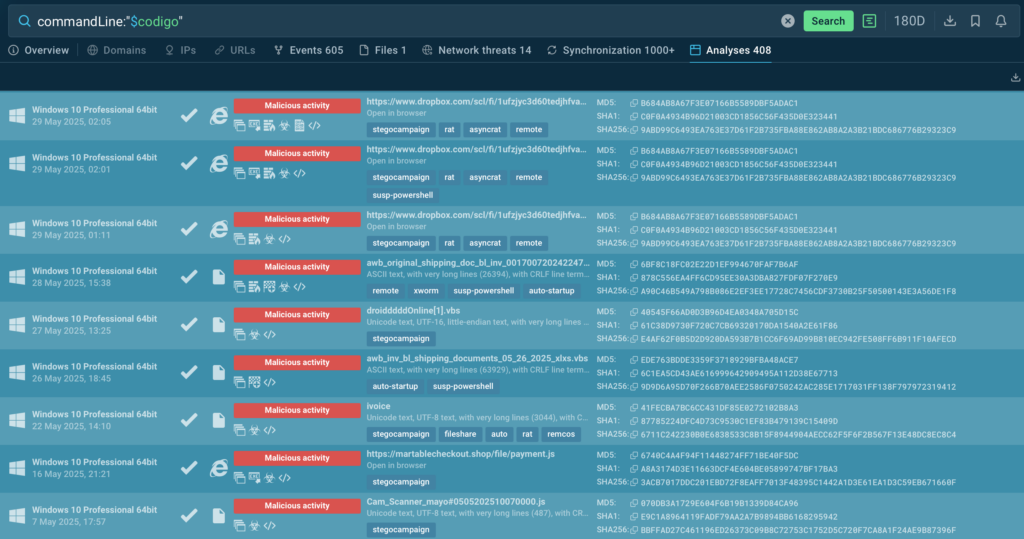
From here, go to sandbox analysis sessions to see how malware detonates, and collect data to take further informed action. As a result, an attack that could’ve remained in your systems for months is prevented.
Ensure Proactive Defense to Prevent Breaches
A key aspect of proactive defense is staying alert and continuously monitoring the threat landscape. One you know what’s going on in your industry or other sectors, you should keep an eye on malware in question, track how it evolves and what new data on it appears.
For that, use Query Updates feature in TI Lookup. Click the bell icon when doing a search to subscribe to your query. For example, if you need to access domains related to Lumma specifically, use this line:
threatName:”lumma” AND domainName:””
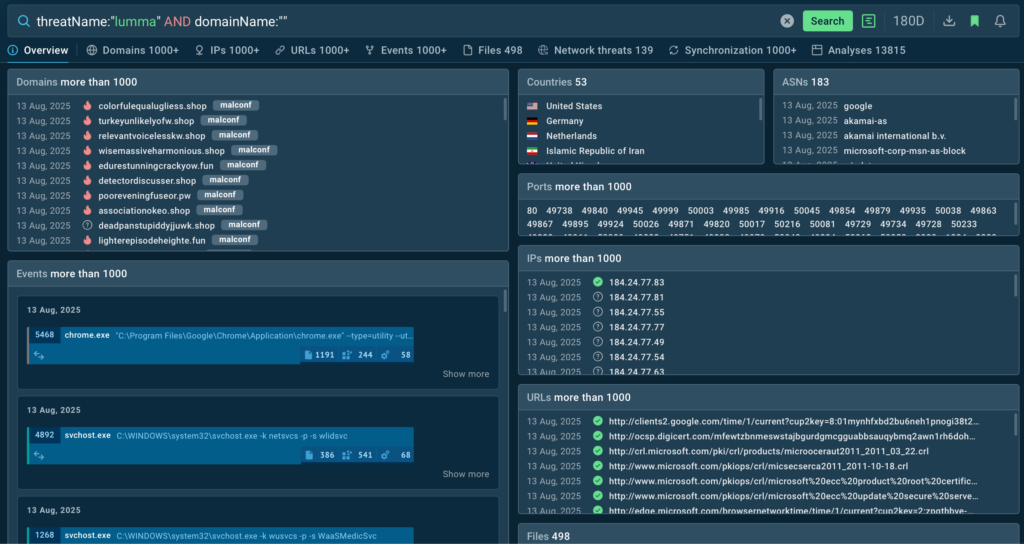
Activate Query Updates:
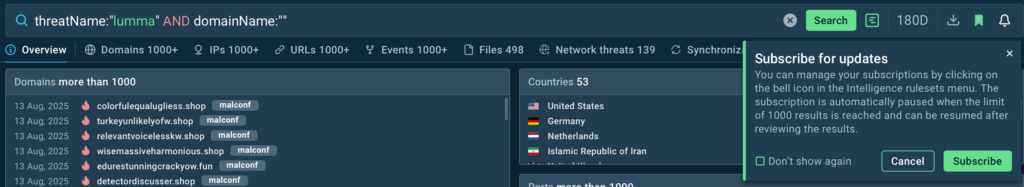
And from now on, you’ll be notified on all new instances for proactive blocking of evolving threats.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN to streamline malware investigations worldwide.
Speed up triage and response by detonating suspicious files in ANY.RUN’s Interactive Sandbox, observing malicious behavior in real time, and gathering insights for faster, more confident security decisions. Paired with Threat Intelligence Lookup and Threat Intelligence Feeds, it provides actionable data on cyberattacks to improve detection and deepen your understanding of evolving threats.
Explore more ANY.RUN’s capabilities during 14-day trial
The post Bridging the Threat Intelligence Gap in Your SOC: A Guide for Security Leaders appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More