Release Notes: QRadar SOAR App, TI Lookup Free Access, and 2,900+ New Detection Rules
July brought powerful new updates to help your SOC catch threats faster, reduce manual effort, and make more confident decisions, right inside your existing workflows. From fresh integrations to better detection coverage, these changes are built to support your team every step of the way.
In this update:
- New IBM QRadar SOAR integration to automate investigations and speed up response
- Launch of a free TI Lookup plan, giving all users access to live attack data from 15K SOCs
- New Debian ARM VM for analyzing malware targeting IoT and embedded systems
- Expanded detection with 163 new behavior signatures, 13 YARA rules, and 2,772 Suricata rules
Keep reading to explore what’s new and how these updates can improve your daily workflows and threat visibility.
Product Updates
IBM QRadar SOAR Integration: Faster, Smarter Incident Response
We’ve officially launched the ANY.RUN app for IBM QRadar SOAR, helping SOC teams move faster, reduce manual effort, and make smarter decisions without leaving their existing workflows.
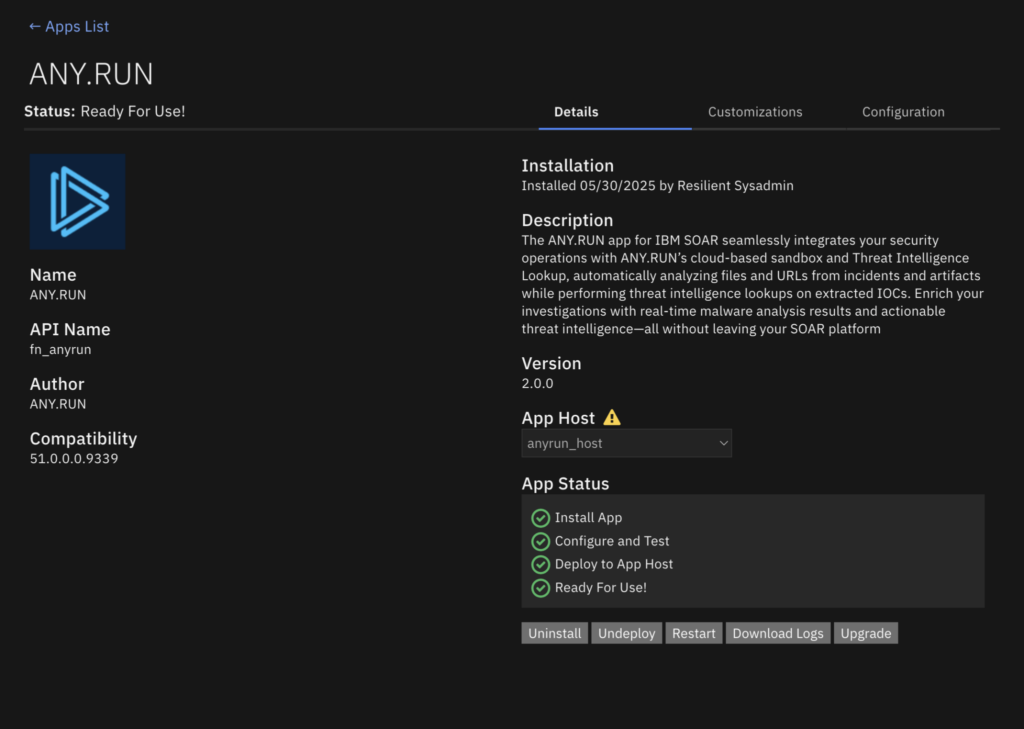
With this integration, analysts can detonate suspicious files and URLs in ANY.RUN’s interactive sandbox directly from QRadar SOAR, and get verdicts, behavioral logs, and IOCs pushed back into the incident automatically. This not only speeds up triage, but also cuts Mean Time to Respond (MTTR) and reduces the risk of missing stealthy threats.
You can also enrich key indicators using ANY.RUN’s Threat Intelligence Lookup, pulling in fresh, real-world threat context from live malware samples observed across 15,000+ organizations.
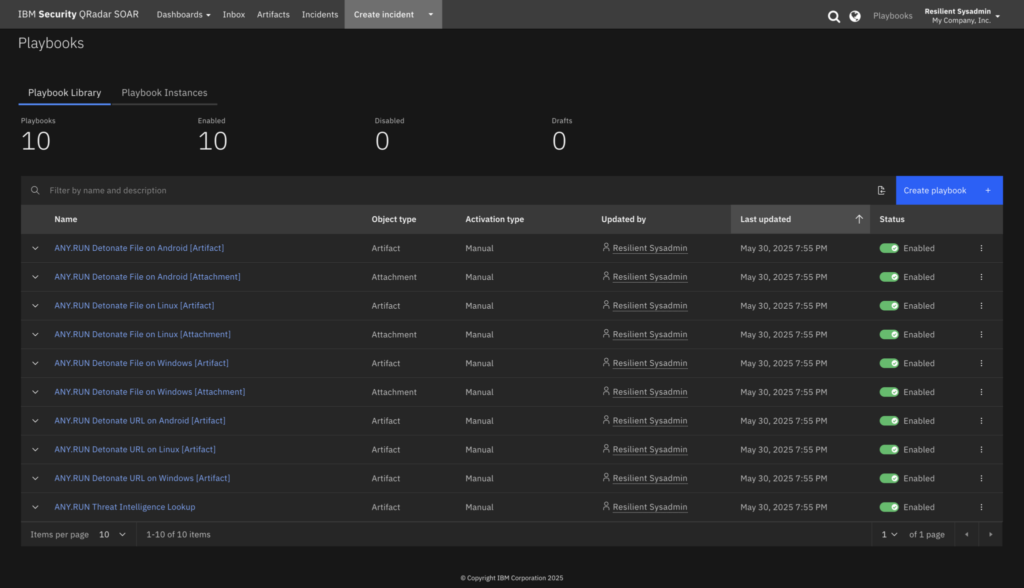
What Your Team Gains: Business and Operational Impact
The new IBM QRadar SOAR integration delivers real performance and value across your SOC. By combining automated sandbox detonation with live threat intelligence enrichment, ANY.RUN helps security teams reduce alert fatigue, move faster, and make better-informed decisions.
- Lower workload and faster response: Automation cuts down manual triage and enrichment, letting analysts focus on critical threats, not routine tasks.
- Improved efficiency across tiers: Tier 1 and Tier 2 analysts benefit from streamlined investigation and escalation, while senior staff gain the bandwidth to focus on strategy and tuning.
- Smarter decisions, better processes: Sandbox reports and TI Lookup insights feed directly into playbooks and detection rules, driving continuous improvement.
- Early visibility into stealthy threats: Real-time behavioral data exposes multi-stage and evasive attacks that traditional tools often miss.
- Stronger ROI from existing tools: The integration adds powerful behavioral context to your SOAR workflows, without requiring new infrastructure or steep learning curves.
How to Get Started
Getting started is easy, just install the ANY.RUN app from IBM App Exchange and connect your account using an API key. You can enable sandbox analysis, Threat Intelligence Lookup, or both, depending on your workflow.
Threat Intelligence Lookup Gets a Free Plan and More Power for Premium
This July, we made accessing high-quality threat intelligence easier than ever. ANY.RUN’s Threat Intelligence Lookup (TI Lookup) now includes a Free plan, giving every analyst and SOC team access to real-time, actionable data from millions of sandboxed malware sessions.
“Threat Intelligence in ANY.RUN continues to evolve — not only by adding more features, but by making the right ones easier to use.”
— Aleksey Lapshin, CEO at ANY.RUN
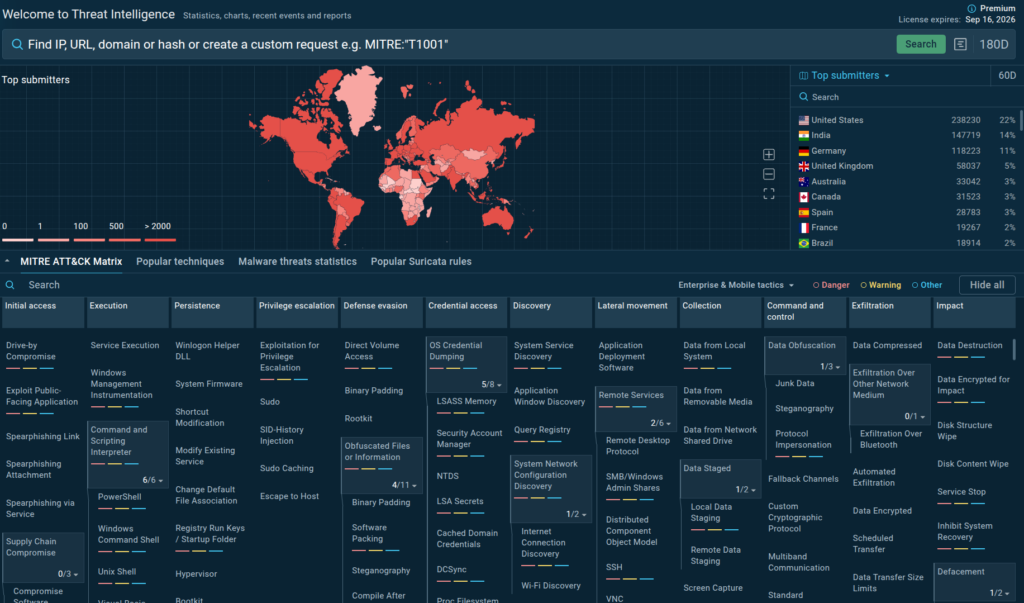
We’ve simplified access to ANY.RUN’s threat intelligence ecosystem with a cleaner, faster entry point. With the Free plan, you can now explore Public Samples, TTPs, Suricata rules, and malware trends without cost or complexity.
Users can perform unlimited searches using core indicators like file hashes, URLs, domains, IPs, Suricata IDs, and MITRE ATT&CK techniques, and combine them using the AND operator for refined threat queries.
What You Can Achieve with TI Lookup Free
The essential features in the free tier help SOC teams address real-world challenges:
- Enrich threat investigations: Gain extensive context by linking existing artifacts to real-world attacks observed in the wild.
- Reduce response time (MTTR): Analyze threat behavior, objectives, and targets directly from sandbox sessions to support fast, informed decisions.
- Strengthen proactive defense: Gather intel on emerging threats early, before they escalate, using real-time data.
- Grow your team’s expertise: Help SOC analysts learn from real-world malware by exploring TTPs through the interactive MITRE ATT&CK matrix.
- Develop SIEM, IDS/IPS, or EDR rules: Use collected intelligence to fine-tune detection rules and boost your organization’s overall defense.
You can view up to 20 recent sandbox sessions per query, giving you insight into how threats evolve and behave across multiple industries and regions.
All you need to do to get started is sign up or log into your ANY.RUN account, and you’re in.
Go Beyond the Basics with TI Lookup Premium
The Free plan gives your team a powerful starting point, but with TI Lookup Premium, you gain the scale, depth, and automation needed for enterprise-grade investigations. Premium unlocks three times more threat data, advanced search capabilities, and access to exclusive features like private search, YARA rule matching, alert subscriptions, and API integration.
| Free | Premium | |
|---|---|---|
| Requests | Unlimited number of basic requests | Advanced requests (100/500/5K/25K) |
| Search operators | AND | AND, OR, NOT |
| Search parameters | 11 | 44 |
| Links to analysis sessions | Up to 20 most recent | All available |
| Interface | Limited (only analyses) | Full (all threat data + analyses) |
| Integration | – | API and SDK (Python package) |
| YARA Search | – | + |
| Private search | – | + |
| TI Reports | – | + |
| Search Updates | – | + |
Whether you’re triaging alerts, threat hunting, or building detection rules, Premium gives you full control over your threat intelligence workflows, so your SOC stays ahead of threats, not just reacts to them.
Reach out to us for trial access to TI Lookup Premium for your SOC team.
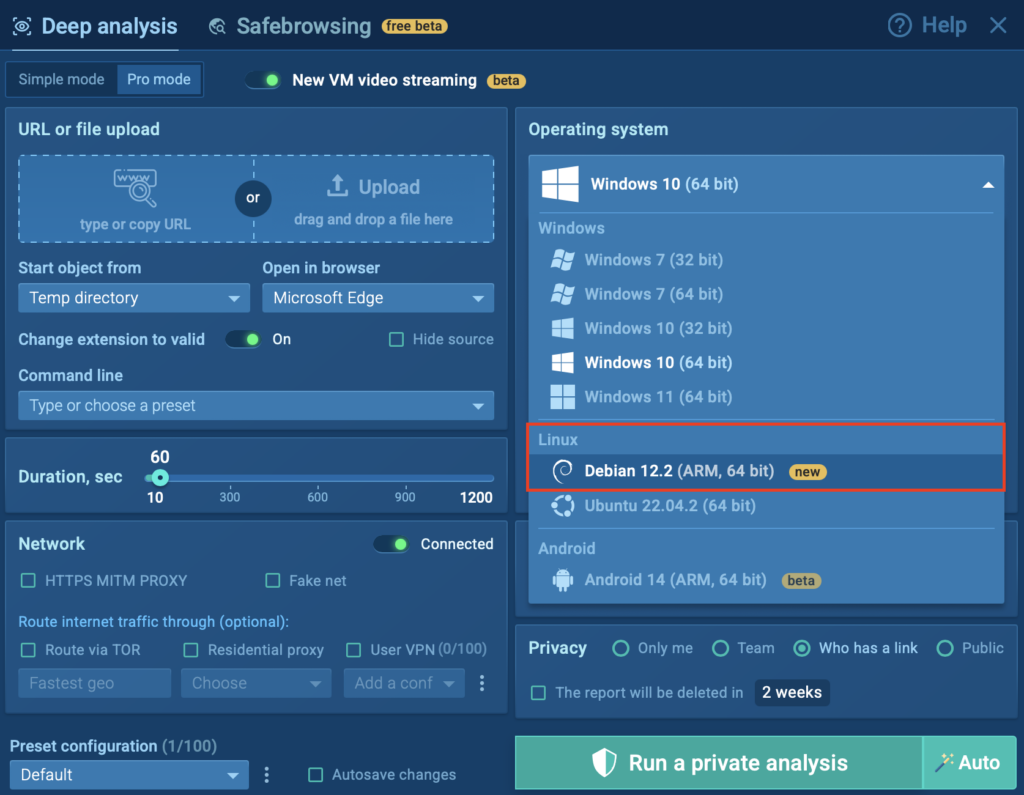
Debian Sandbox for ARM Malware Detection and Analysis
To help SOC teams stay ahead of evolving threats, ANY.RUN now supports Linux Debian 12.2 64-bit (ARM) in our Interactive Sandbox. This new environment enables deep analysis of malware targeting ARM-based systems, commonly found in IoT devices, embedded infrastructure, and lightweight servers.
ARM-based malware is becoming a serious concern across industries. These attacks often target underprotected systems to establish botnets, steal resources, or maintain unauthorized access, making early detection critical.
With the new Debian (ARM) VM, analysts can:
- Engage directly with ARM-based malware in a live, isolated environment to trigger and observe hidden behaviors
- Uncover advanced tactics like persistence, evasion, and privilege escalation with process-level visibility
- Trace execution paths in real time, from dropped files to command-line activity
- Correlate behaviors with known TTPs using integrated MITRE ATT&CK mapping for threat classification
The new ARM VM is available to Enterprise users. Simply open a new analysis and select Linux Debian 12.2 (ARM, 64-bit) from the OS list to get started.
What this update brings to your SOC:
- Faster analysis: Accelerate triage, incident response, and threat hunting with a dedicated ARM environment that delivers instant behavioral insights.
- Reduced platform costs: Analyze ARM-based threats alongside Windows, Android, and Linux samples, all within the same sandbox platform.
- Smarter incident escalation: Collect rich, actionable data during Tier 1 analysis to support better handoffs to Tier 2 teams.
- Stronger analyst expertise: Empower your team to investigate real-world ARM malware, improving skillsets through hands-on, safe analysis.
Threat Coverage Update
In July, our team expanded detection capabilities significantly to help SOCs stay ahead of evolving threats:
- 163 new signatures were added to strengthen detection across malware families and techniques.
- 13 new YARA rules went live in production, boosting accuracy and enabling deeper hunting capabilities.
- 2,772 new Suricata rules were deployed, ensuring better coverage for network-based attacks.
These updates mean analysts get faster, more confident verdicts in the sandbox and can enrich SIEM, SOAR, and IDS workflows with fresh, actionable IOCs.
New Behavior Signatures
In July, we added a new set of behavior signatures to help SOC teams detect stealthy, obfuscated, and persistent techniques earlier in the attack chain. These signatures are triggered by actions, not static indicators, giving your analysts deeper visibility and faster context during investigations.
Malware Families
Obfuscation & Evasion Techniques
Persistence Techniques
Recon & Credential Access
File/Registry/OS Abuse
Payload Delivery
Other
- BART: Loader activity observed in stealthy malware campaigns
- susp-lnk: Flags suspicious .lnk shortcut behavior often used for initial access
- susp-clipboard: Detects suspicious clipboard manipulation commonly used in credential theft or staged payload delivery
YARA Rule Updates
In July, we released 13 new YARA rules into production to help analysts detect threats faster, improve hunting accuracy, and cover a wider range of malware families and evasion tactics.
Some key additions:
- BLACKMATTER: Detects ransomware operations linked to critical infrastructure attacks.
- LOCKBIT4: Tracks the latest variant of this widely distributed ransomware family.
- NirCmd has been detected: Flags abuse of NirCmd, a legitimate utility often used for stealthy execution.
- nightspire:Identifies this stealthy stealer observed in recent targeted campaigns.
- sinobi: Detects an infostealer family using Telegram for data exfiltration.
- cryptolocker: Covers one of the earliest forms of ransomware still resurfacing in modified campaigns.
New Suricata Rules
We’ve also added 2772 targeted Suricata rules to help SOC teams catch stealthy data exfiltration attempts and phishing campaigns more reliably. Here are a few hihglights:
- Telegram data exfiltration (sid:85002387): Detects attempt to exfiltrate stolen data via Telegram Bot API
- Fake government domain pattern (sid:85002265): Identifies potentially fraudulent domains mimicking legitimate government services
- Microsoft authorization phishing (sid:85002349): Tracks phishing attacks by observing legitimate MS Auth URL on unknown/fake domain
These new rules enhance detection for modern phishing and exfiltration tactics and are automatically applied in your ANY.RUN sessions.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across banking, manufacturing, telecom, healthcare, retail, and tech, helping them build faster, smarter, and more resilient cybersecurity operations.
Our cloud-based Interactive Sandbox enables teams to safely analyze threats targeting Windows, Linux, and Android systems in under 40 seconds; no complex infrastructure required. Paired with TI Lookup, YARA Search, and Threat Feeds, ANY.RUN empowers security teams to accelerate investigations, reduce risk, and boost SOC efficiency.
Start your 14-day trial and take full control of threat analysis
The post Release Notes: QRadar SOAR App, TI Lookup Free Access, and 2,900+ New Detection Rules appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

