Detect ARM Malware in Seconds with Debian Sandbox for Stronger Enterprise Security
ANY.RUN’s Interactive Sandbox provides SOC teams with the fastest solution for analyzing and detecting cyber threats targeting Windows, Linux, and Android systems. Now, our selection of VMs has been expanded to include Linux Debian 12.2 64-bit (ARM).
With the rapid rise of ARM-based malware, the sandbox helps businesses tackle this threat through proactive analysis and early detection.
Why ARM-based Malware is a Serious Threat to Your Company
ARM processors are widely used in resource-constrained IoT devices, embedded systems, and even low-power servers, often deployed with weak security. These devices become prime targets for attackers looking to build massive botnets, steal resources, or gain unauthorized access. The three most popular types of ARM-based malware include:
- Botnets: Turning devices into “zombies” for DDoS attacks.
- Cryptojackers: Hijacking CPU for cryptocurrency mining.
- Backdoors: Maintaining persistent unauthorized system access.
By expanding the capabilities to identify these threats, companies can prevent large-scale incidents in their infrastructure and reduce costs associated with downtime, recovery, and incident response.
Launch Your First Malware Analysis in Linux Debian (ARM) VM
The new OS is now available to all Enterprise users, unlocking deeper analysis capabilities for ARM-based threats.
To select the Linux Debian VM, follow these simple steps:
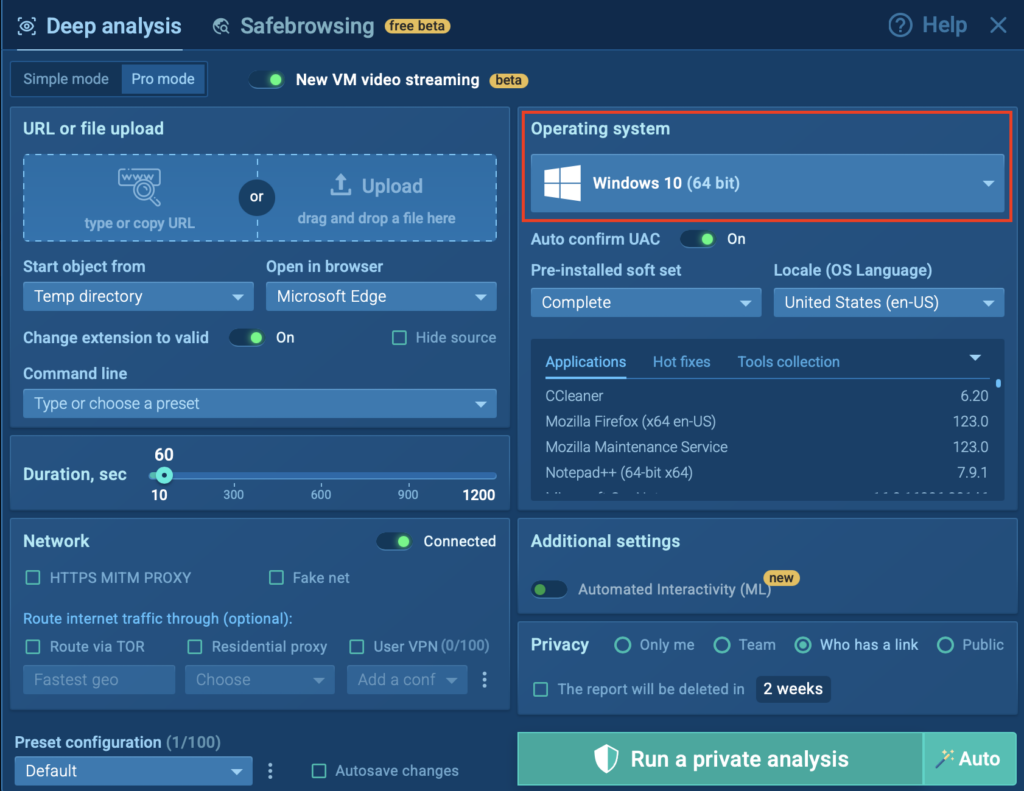
- Navigate to the New analysis window.
- Open the Operating system menu
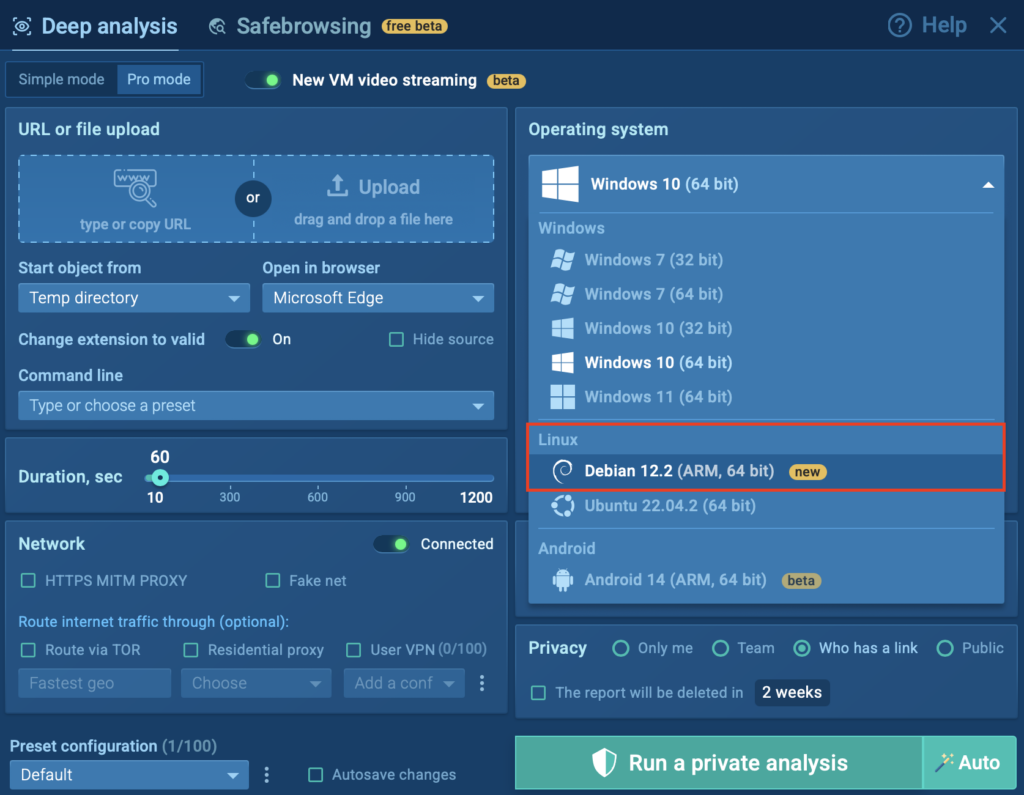
- Click on Linux Debian 12.2 (ARM, 64 bit)
- Upload a file/URL you want to analyze, configure the rest of your settings, and run your analysis.
The update further empowers your security team to detect malware and phishing early with ANY.RUN’s Interactive Sandbox:
- Ensure fast analysis: Accelerate triage, incident response, and threat hunting with a dedicated ARM environment for instant insights into any threat’s behavior.
- Cut costs: Analyze ARM-based malware along with Windows, Android, Linux x86 threats directly in ANY.RUN’s sandbox, eliminating the need for multiple platforms.
- Improve incident escalation: Gather rich, actionable data during Tier 1 analysis to enhance informed handoffs to Tier 2 to mitigate active attacks more effectively.
- Grow team’s expertise: Help your SOC analysts enhance their skills by analyzing real-world ARM threats, building confidence and knowledge through hands-on investigations.
Real-World Use Case: Kaiji Botnet
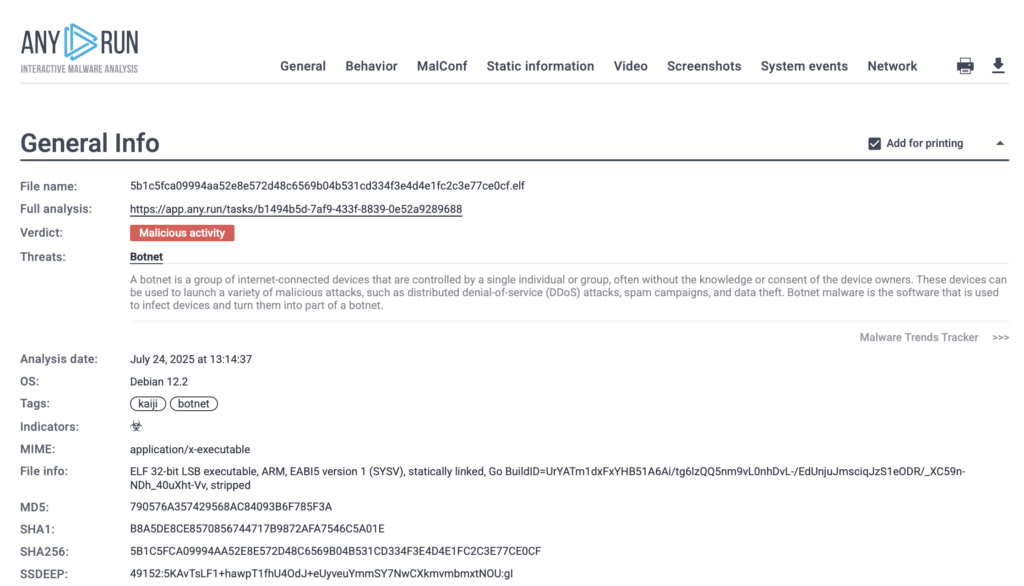
To demonstrate how ANY.RUN’s Linux Debian 12.2 (ARM, 64-bit) Sandbox operates, we analyzed a real-world sample of the Kaiji botnet, malware specifically compiled for the ARM architecture.
Kaiji is a botnet that targets Linux-based servers and IoT devices. Once executed, it performs system reconnaissance, masks its presence, disables security mechanisms like SELinux, and ensures persistence through systemd services and cron jobs. It replaces core system utilities and hides malicious activity by filtering command output, all of which are captured inside the sandbox.
Let’s take a closer look at how Kaiji behaves from the moment it lands on the sandbox:
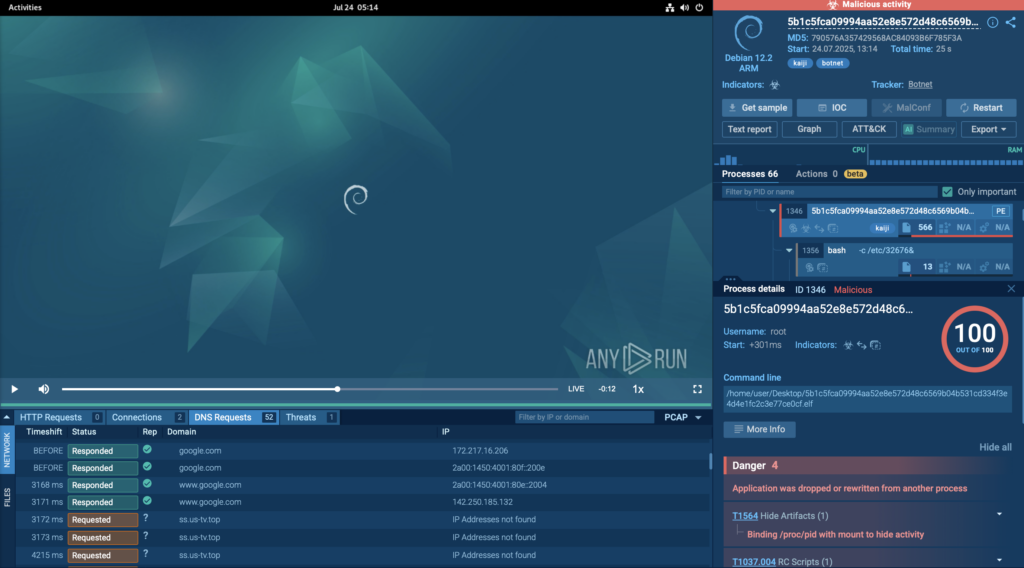
Fast Detection with Instant Verdict
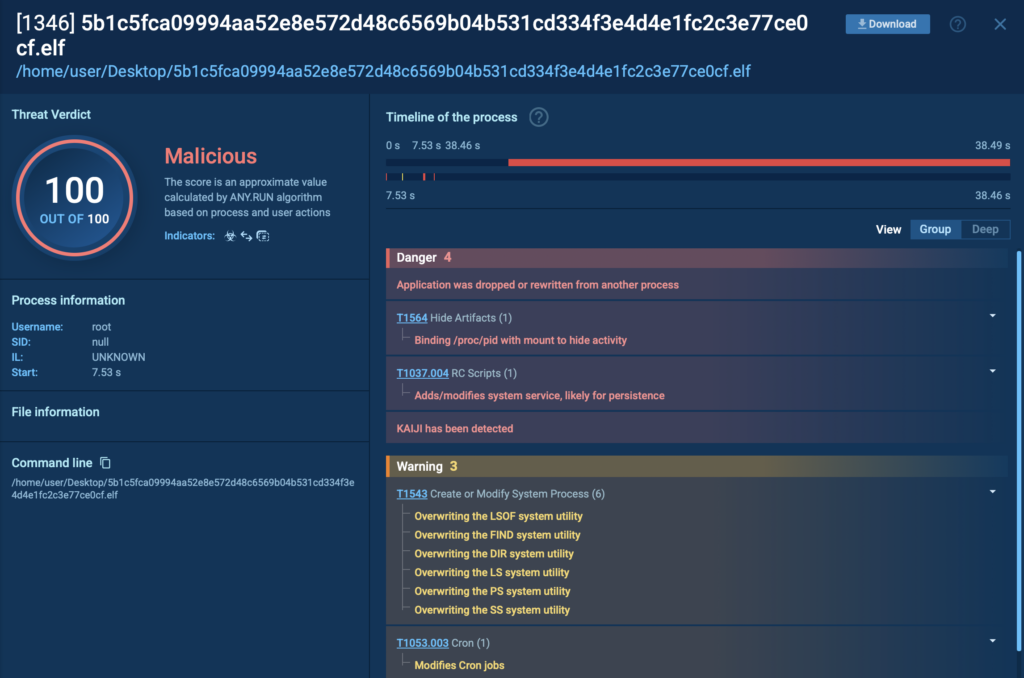
In this real-world case, ANY.RUN’s Debian 12.2 ARM sandbox detected the Kaiji botnet in just 25 seconds, as shown in the top-right corner of the sandbox interface. The threat was flagged as malicious activity and accurately labeled kaiji and botnet.
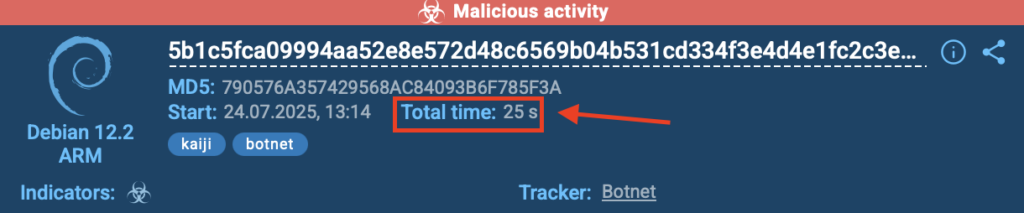
This kind of speed delivers real value for security teams:
- Respond faster: A near-instant verdict means teams can act before the threat spreads.
- Reduce manual work: Quick detection cuts down time spent digging through logs or unclear alerts.
- Improve SOC efficiency: Faster detection supports lower MTTR and smarter alert triage.
- Stay ahead of evolving threats: With ARM-based malware on the rise, fast, reliable detection is key to staying protected.
Full Visibility with Process Tree
Beyond fast detection, ANY.RUN’s sandbox gives complete visibility into the attack’s behavior. On the right side of the screen, the process tree lays out every action taken by the malware. Clicking on each process reveals detailed information, from execution paths to commands and TTPs used.
In this Kaiji case, for example, we can see how the malware attempts to maintain persistence by modifying /etc/crontab to run the /.mod script every minute. This script keeps the malicious process running in the background, even if one of the persistence methods fails; a tactic clearly visible and traceable through the sandbox’s behavioral logs.
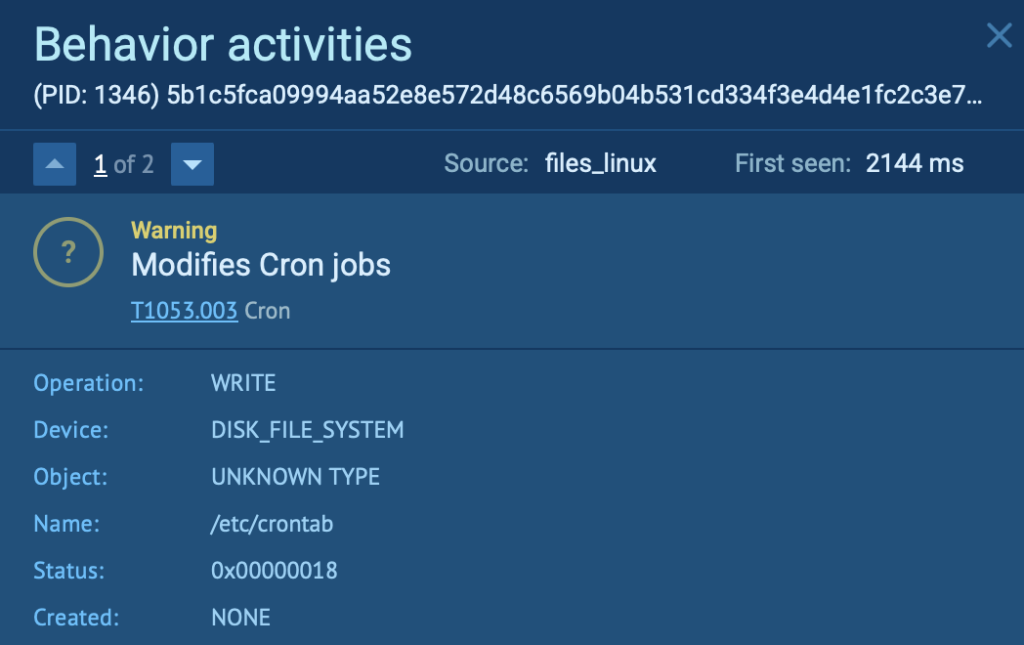
This level of insight helps SOC teams not only detect threats quickly, but understand them deeply, supporting better response, reporting, and threat hunting.
Track Network and File Activity in Real Time
Just below the VM window, ANY.RUN displays all network connections and file modifications made by the malware, offering analysts a complete picture of how the threat operates.
In this case, Kaiji’s behavior is clearly visible: the malware replaces key system utilities and intercepts user commands, passing them to the original tools while filtering the output to hide signs of infection. This is handled via the /etc/profile.d/gateway.sh script, which uses sed to remove specific keywords like 32676, dns-tcp4, and the names of hidden files from command output; a stealthy evasion technique that can be easily overlooked without deep behavioral analysis.
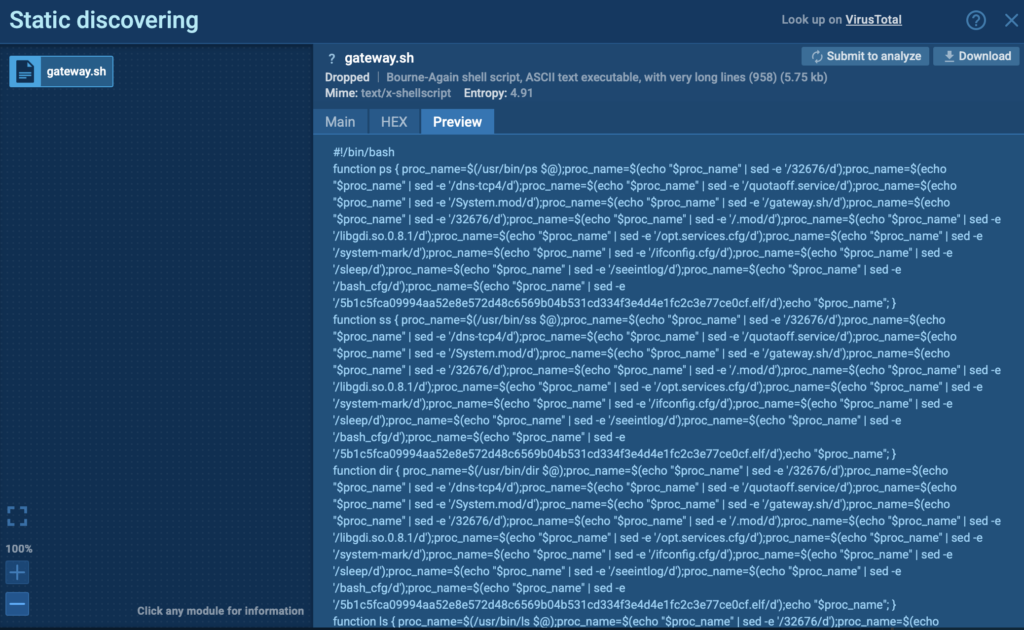
With this visibility, security teams can trace every move, catch hidden modifications, and build accurate IOCs for future detection and response.
Complete Results, Ready to Investigate or Share
Once the analysis is complete, ANY.RUN’s sandbox gives you everything you need to take the next step. The IOCs tab gathers all critical indicators, including IPs, domains, file hashes, and more, in one place, so there’s no need to jump between views or dig through raw logs.
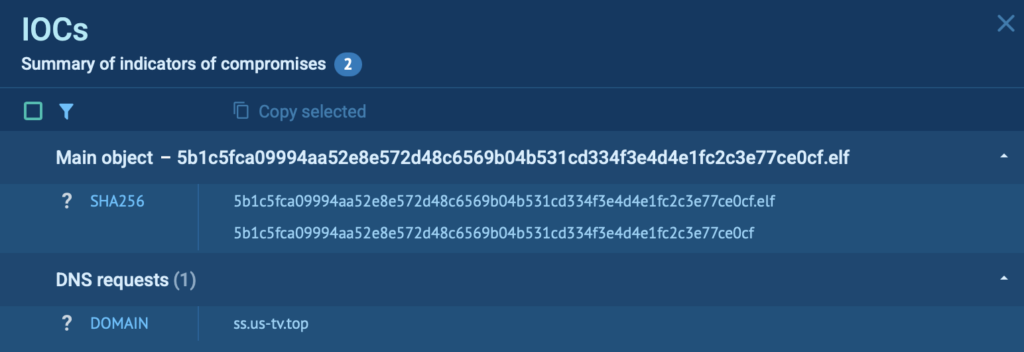
You’ll also get a clear, structured report that maps out the full attack chain from start to finish. Whether you’re documenting a case, sharing findings with your team, or enriching threat intelligence feeds, the report is built to support fast, confident action.
This end-to-end visibility makes every investigation smoother, and every response stronger.
About ANY.RUN
Trusted by over 500,000 security professionals and 15,000+ organizations across finance, healthcare, manufacturing, and beyond, ANY.RUN helps teams investigate malware and phishing threats faster and with greater precision.
Accelerate investigation and response: Use ANY.RUN’s Interactive Sandbox to safely detonate suspicious files and URLs, observe real-time behavior, and extract critical insights, cutting triage and decision time dramatically.
Enhance detection with threat intelligence: Leverage Threat Intelligence Lookup and TI Feeds to uncover IOCs, tactics, and behavior patterns tied to active threats, 6empowering your SOC to stay ahead of attacks as they emerge.
Request a trial of ANY.RUN’s services to see how they can boost your SOC workflows.
The post Detect ARM Malware in Seconds with Debian Sandbox for Stronger Enterprise Security appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
