CISO Blueprint: 5 Steps to Enterprise Cyber Threat Resilience
Why are SOC teams still struggling to keep up despite heavy investments in security tools? False positives pile up, evasive threats slip through, and critical alerts often get buried under noise. For CISOs, the challenge is giving teams the visibility and speed they need to respond before damage is done.
ANY.RUN helps close that gap. 95% of companies using the solution report faster investigations and shorter response times because their teams aren’t waiting on static reports or incomplete data. Instead, they get real-time insight into how threats behave, enabling faster decisions, fewer delays, and a measurable boost in SOC performance.
This CISO blueprint outlines five strategic steps to help your enterprise SOC reach new levels of resilience with proven results.
Proven Results from the Front Lines of the SOC
Security leaders are seeing real operational gains after integrating ANY.RUN into their workflows.
 Key ANY.RUN stats
Key ANY.RUN stats- 90% of companies report higher detection rates after adopting ANY.RUN
- SOC teams improve performance by up to 3x
- 74% of Fortune 100 companies rely on ANY.RUN in their security operations
- Trusted by 15,000+ organizations across finance, telecom, retail, government, and healthcare
Take Expertware, for example, a leading European IT consultancy. Facing growing pressure to shorten investigation timelines and scale without hiring, they adopted ANY.RUN’s sandbox. What used to take hours of manual work now happens in minutes thanks to real-time, interactive malware analysis.
What changed after implementing ANY.RUN’s sandbox?
- 50% reduction in malware investigation time
- Improved team collaboration, with shared reports and interactive analysis reducing handoff delays
- Deeper threat visibility, including multi-stage and fileless malware
- Faster client response, with clearer reports enabling quicker decision-making
ANY.RUN helped them eliminate the overhead of manual setups while improving threat clarity, leading to stronger security outcomes for both their team and their clients.
1. Deploy Real-Time Threat Analysis for Early Detection
When time is everything, waiting on static scans or post-execution reports just doesn’t cut it. To respond effectively, SOCs need a clear view of the threat as it happens.
ANY.RUN’s sandbox delivers that clarity through live detonation, giving your team an immediate look at the full scope of any malware or phishing attack. From execution flow to network connections and dropped payloads, everything is visible in real time.
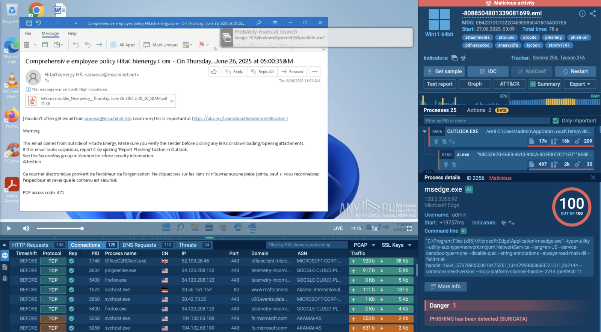
What sets ANY.RUN sandbox apart is interactivity. Analysts can engage with the sample mid-execution, clicking buttons, opening files, entering credentials, just like a real user. That means no waiting for analysis to complete and no relying on partial data. Threat behavior becomes obvious in seconds, allowing your team to move faster and with greater confidence.
2. Automate Triage to Reduce Analyst Workload and Alert Fatigue
Not all threats reveal themselves with a simple scan. Many phishing kits and malware samples are designed to evade detection unless specific user actions are taken, like solving a CAPTCHA, clicking a hidden button, or opening a malicious link embedded in a QR code.
View real case with QR code analysis
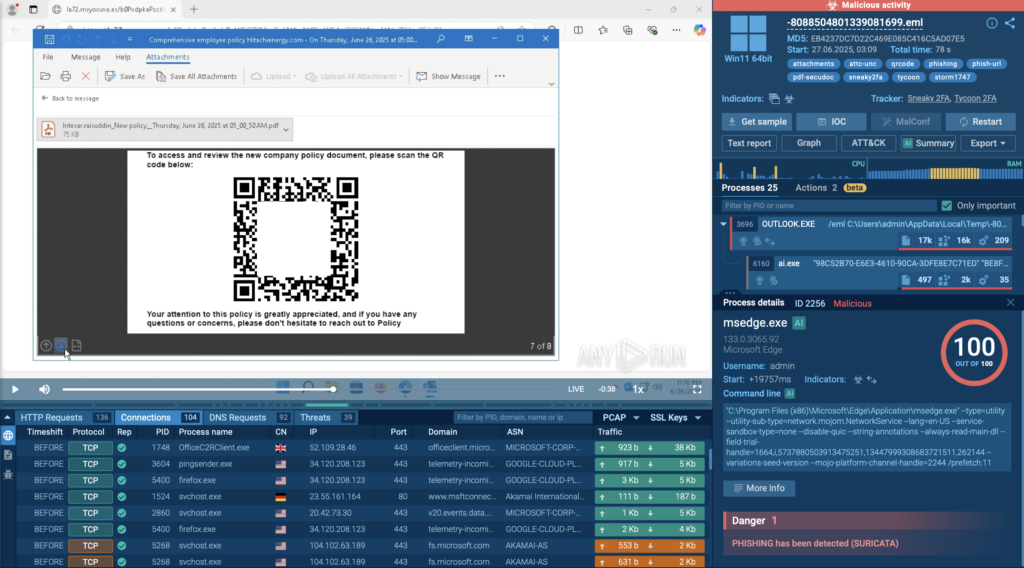
ANY.RUN tackles this head-on. With Automated Interactivity, available in the Enterprise plan, it simulates real user behavior, solving CAPTCHAs, navigating redirects, opening files and links hidden inside QR codes or archives. This allows the sandbox to detonate even evasive threats automatically, giving your team faster, more accurate results with less manual effort.
The outcome?
- Higher detection rates
- Faster triage
- Reduced alert fatigue
- More time to focus on high-impact threats
This type of automation also lowers the pressure on junior analysts, who can now complete complex investigations without relying on senior teammates to step in. With ANY.RUN handling the hard parts of triage, your team detects threats faster and stays focused on response, not troubleshooting.
3. Boost SOC Performance through Collaboration and a Unified Security Stack
Tools alone won’t fix slow investigations or fragmented response workflows; collaboration is just as critical.
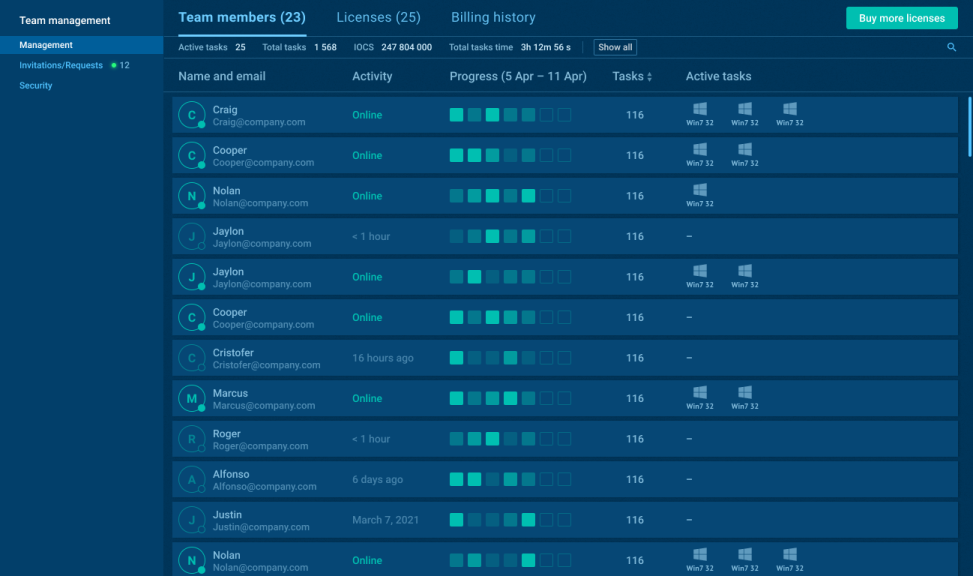
ANY.RUN is built to support this from the ground up. Designed for high-performing SOCs, its Teamwork feature gives analysts a shared workspace where roles are clearly defined, tasks are tracked in real time, and managers can supervise without disrupting the flow. Whether your team is in one office or spread across time zones, everyone stays aligned and productive.
- Clear task ownership to prevent duplication and confusion
- Role-based access and oversight for team leads
- Scalable structure that grows with your team
- Built-in activity tracking to monitor productivity
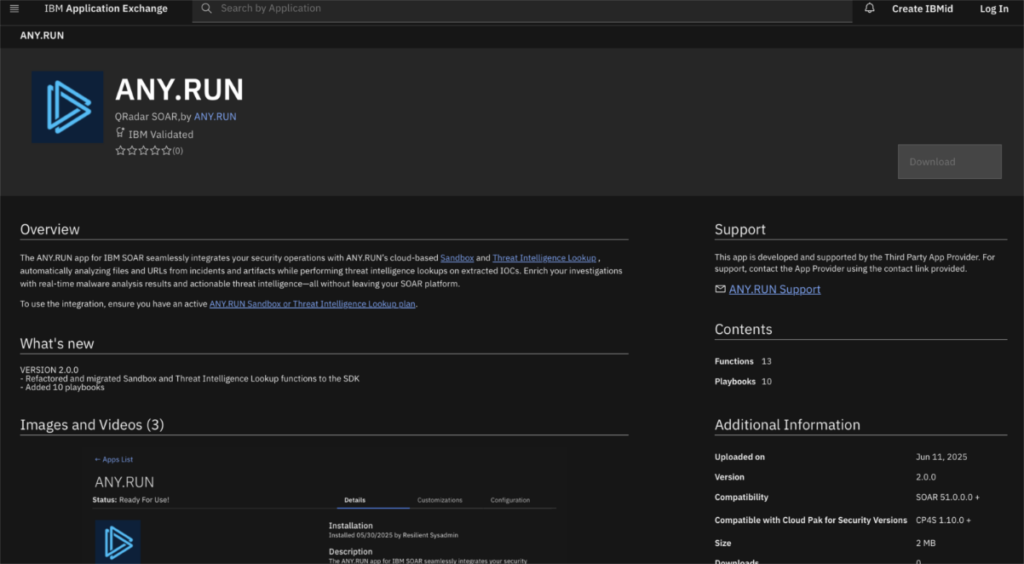
And it doesn’t stop there. ANY.RUN integrates seamlessly with your existing SOAR, XDR, or SIEM platforms, allowing teams to analyze suspicious files straight from alerts, enrich incidents with fresh IOCs, and manage security workflows without leaving their familiar interfaces.

One of the latest integrations is with IBM QRadar SOAR, a widely used platform for incident response. With ANY.RUN’s official app, teams can:
- Launch sandbox analyses directly from SOAR playbooks
- Enrich cases with real-time IOCs and behavioral insights
- Automate repetitive steps to reduce Mean Time to Respond (MTTR)
Setup takes just minutes; plug in your API key, and your team is ready to go.
Together, this connected and collaborative approach leads to faster decisions, higher output, and a stronger, more efficient SOC.
4. Ensure Privacy and Compliance to Prevent Data Leaks
Threat detection means little if it compromises sensitive data in the process. For CISOs, building a resilient security program also means ensuring that investigations don’t create new risks, like exposing internal files, violating client confidentiality, or falling out of compliance.
ANY.RUN addresses this risk with robust privacy controls designed for enterprise SOCs. Teams can conduct investigations in a fully private sandbox, ensuring that no data is accidentally exposed or shared outside the organization. Role-based visibility settings let team leads define who sees what, while granular access controls prevent analysts from unintentionally publishing sensitive tasks.
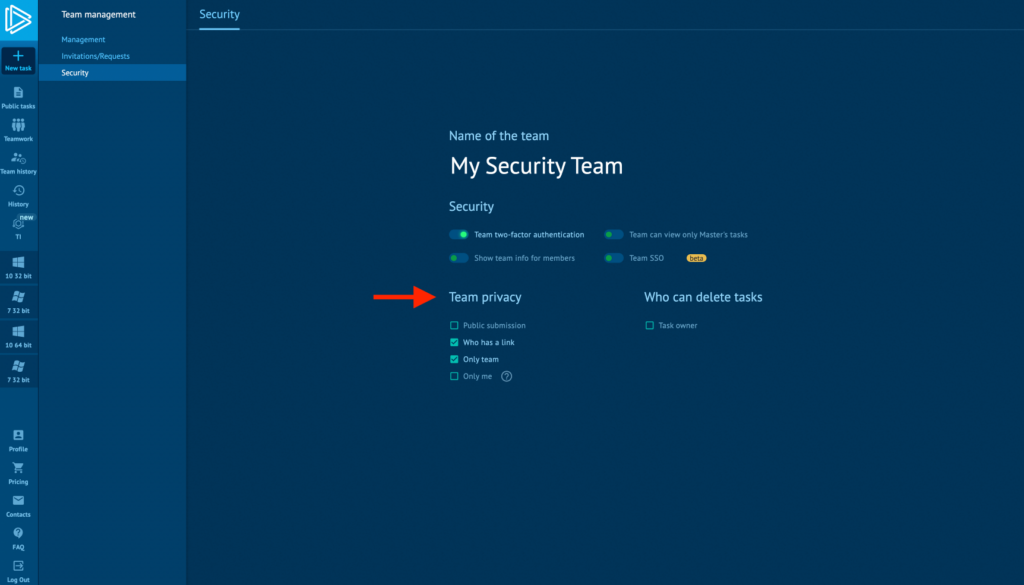
You also get flexible private analysis options that scale with your team:
- Unlimited private analyses per user
- Or unlimited users with per-analysis pricing
This means your investigations stay confidential without compromising collaboration or growth.
To further tighten access and simplify security management, ANY.RUN supports Single Sign-On (SSO). Analysts can log in using existing organizational credentials, improving both security and ease of use. Onboarding, offboarding, and daily access become seamless, reducing risk and helping you stay compliant with internal policies and external standards.
5. Move From Reactive to Proactive Security
Staying ahead of modern threats demands proactive insight into what’s coming next. But for many CISOs, building that foresight into daily workflows is still a challenge. With queues overflowing and teams focused on triage, opportunities to uncover patterns, enrich investigations, and harden defenses often slip through the cracks.
That’s where ANY.RUN’s Threat Intelligence Lookup (TI Lookup) delivers a clear advantage.
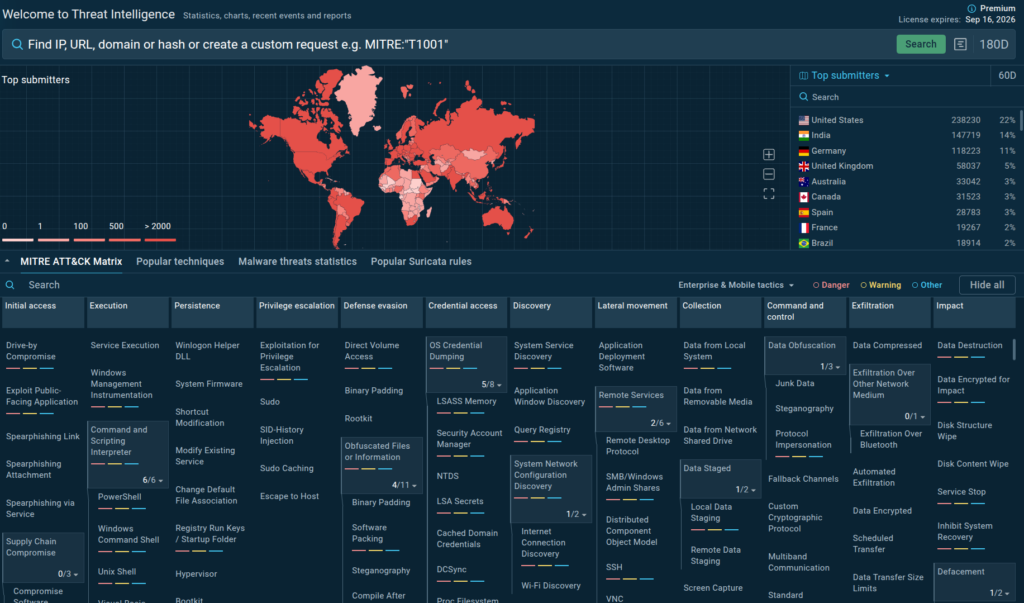
TI Lookup gives your SOC team instant access to threat data sourced from millions of malware detonation sessions, with real-world samples, IOCs, IOBs, IOAs, and TTPs updated within hours of an attack, not days or weeks later. It’s built to accelerate investigation, support informed decisions, and drive proactive defense across your infrastructure.
With free access, your team can:
- Enrich alerts with context from recent sandbox sessions
- Link artifacts to real-world malware campaigns targeting over 15,000 companies globally
- Reduce MTTR by quickly identifying behaviors, payloads, and known threat families
- Explore malware trends, TTPs, and MITRE mappings directly from the interactive sandbox
- Gather intelligence to improve SIEM, IDS/IPS, or EDR rule creation
Build a Smarter, More Resilient SOC Starting Now
Resilience is built with visibility, automation, and collaboration that work together across your entire SOC. From accelerating detection to reducing manual workload, ANY.RUN gives security teams the tools they need to respond faster, dig deeper, and stay ahead of evolving threats.
Whether you’re modernizing your stack or scaling operations, a live, interactive sandbox can be the force multiplier your team needs.
Ready to see how it fits into your environment?
Contact us for integration and start strengthening your threat response with speed and precision.
About ANY.RUN
ANY.RUN is built to help security teams detect threats faster and respond with greater confidence. Our interactive sandbox platform delivers real-time malware analysis and threat intelligence, giving analysts the clarity they need when it matters most.
With support for Windows, Linux, and Android environments, our cloud-based sandbox enables deep behavioral analysis without the need for complex setup. Paired with Threat Intelligence Lookup and Feeds, ANY.RUN provides rich context, actionable IOCs, and automation-ready outputs, all with zero infrastructure burden.
The post CISO Blueprint: 5 Steps to Enterprise Cyber Threat Resilience appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
