Hijacking Discord invite links to install malware | Kaspersky official blog
Attackers are using expired and deleted Discord invite links to distribute two strains of malware: AsyncRAT for taking remote control of infected computers, and Skuld Stealer for stealing crypto wallet data. They do this by exploiting a vulnerability in Discord’s invite link system to stealthily redirect users from trusted sources to malicious servers.
The attack leverages the ClickFix technique, multi-stage loaders and deferred execution to bypass defenses and deliver malware undetected. This post examines in detail how attackers exploit the invite link system, what is ClickFix and why they use it, and, most importantly, how not to fall victim to this scheme.
How Discord invite links work
First, let’s look at how Discord invite links work and how they differ from each other. By doing so, we’ll gain an insight into how the attackers learned to exploit the link creation system in Discord.
Discord invite links are special URLs that users can use to join servers. They are created by administrators to simplify access to communities without having to add members manually. Invite links in Discord can take two alternative formats:
- https://discord.gg/{invite_code}
- https://discord.com/invite/{invite_code}
Having more than one format, with one that uses a “meme” domain, is not the best solution from a security viewpoint, as it sows confusion in the users’ minds. But that’s not all. Discord invite links also have three main types, which differ significantly from each other in terms of properties:
- Temporary invite links
- Permanent invite links
- Custom invite links (vanity URLs)
Links of the first type are what Discord creates by default. Moreover, in the Discord app, the server administrator has a choice of fixed invite expiration times: 30 minutes, 1 hour, 6 hours, 12 hours, 1 day or 7 days (the default option). For links created through the Discord API, a custom expiration time can be set — any value up to 7 days.
Codes for temporary invite links are randomly generated and usually contain 7 or 8 characters, including uppercase and lowercase letters, as well as numbers. Examples of a temporary link:
- https://discord.gg/a7X9pLd
- https://discord.gg/Fq5zW2cn
To create a permanent invite link, the server administrator must manually select Never in the Expire After field. Permanent invite codes consist of 10 random characters — uppercase and lowercase letters, and numbers, as before. Example of a permanent link:
- https://discord.gg/hT9aR2kLmB
Lastly, custom invite links (vanity links) are available only to Discord Level 3 servers. To reach this level, a server must get 14 boosts, which are paid upgrades that community members can buy to unlock special perks. That’s why popular communities with an active audience — servers of bloggers, streamers, gaming clans or public projects — usually attain Level 3.
Custom invite links allow administrators to set their own invite code, which must be unique among all servers. The code can contain lowercase letters, numbers and hyphens, and can be almost arbitrary in length — from 2 to 32 characters. A server can have only one custom link at any given time.
Such links are always permanent — they do not expire as long as the server maintains Level 3 perks. If the server loses this level, its vanity link becomes available for reuse by another server with the required level. Examples of a custom invite link:
- https://discord.gg/alanna-titterington
- https://discord.gg/best-discord-server-ever
- https://discord.gg/fq5zw2cn
From this last example, attentive readers may guess where we’re heading.
How scammers exploit the invite system
Now that we’ve looked at the different types of Discord invite links, let’s see how malicious actors weaponize the mechanism. Note that when a regular, non-custom invite link expires or is deleted, the administrator of a legitimate server cannot get the same code again, since all codes are generated randomly.
But when creating a custom invite link, the server owner can manually enter any available code, including one that matches the code of a previously expired or deleted link.
It is this quirk of the invite system that attackers exploit: they track legitimate expiring codes, then register them as custom links on their servers with Level 3 perks.
As a result, scammers can use:
- Any expired temporary invite links (even if the expired link has capital letters and the scammers’ custom URL replaces them with lowercase, the system automatically redirects the user to this vanity URL)
- Permanent invite links deleted from servers, if the code consisted solely of lowercase letters and numbers (no redirection here)
- Custom invite links, if the original server has lost Level 3 perks and its link is available for re-registration
What does this substitution lead to? Attackers get the ability to direct users who follow links previously posted on wholly legitimate resources (social networks, websites, blogs and forums of various communities) to their own malicious servers on Discord.
What’s more, the legal owners of these resources may not even realize that the old invite links now point to fake Discord servers set up to distribute malware. This means they can’t even warn users that a link is dangerous, or delete messages in which it appears.
How ClickFix works in Discord-based attacks
Now let’s talk about what happens to users who follow hijacked invite links received from trusted sources. After joining the attackers’ Discord server, the user sees that all channels are unavailable to them except one, called verify.
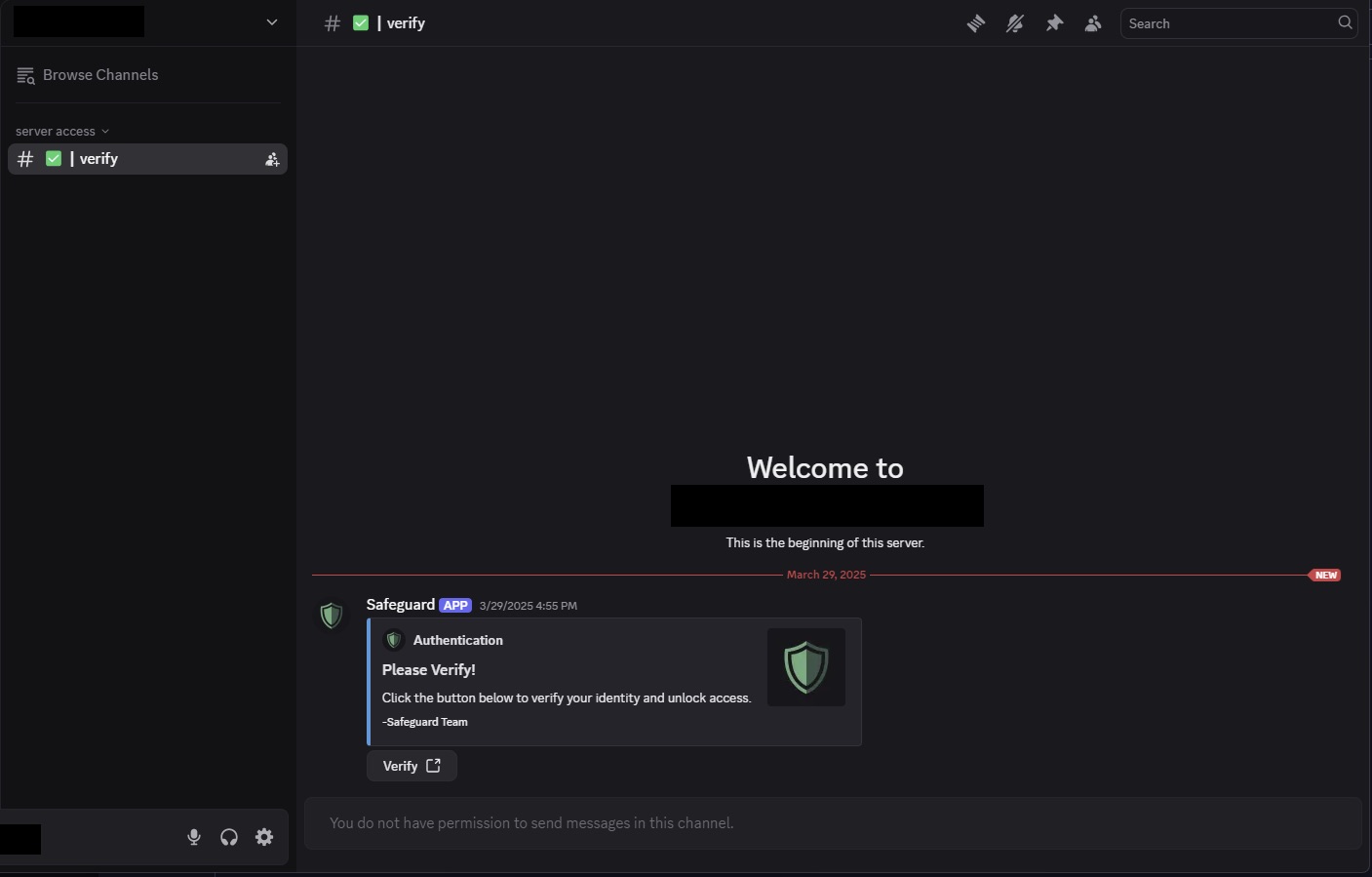
On the attackers’ Discord server, users who followed the hijacked link have access to only one channel, verify Source
This channel features a bot named Safeguard that offers full access to the server. To get this, the user must click the Verify button, which is followed by a prompt to authorize the bot.
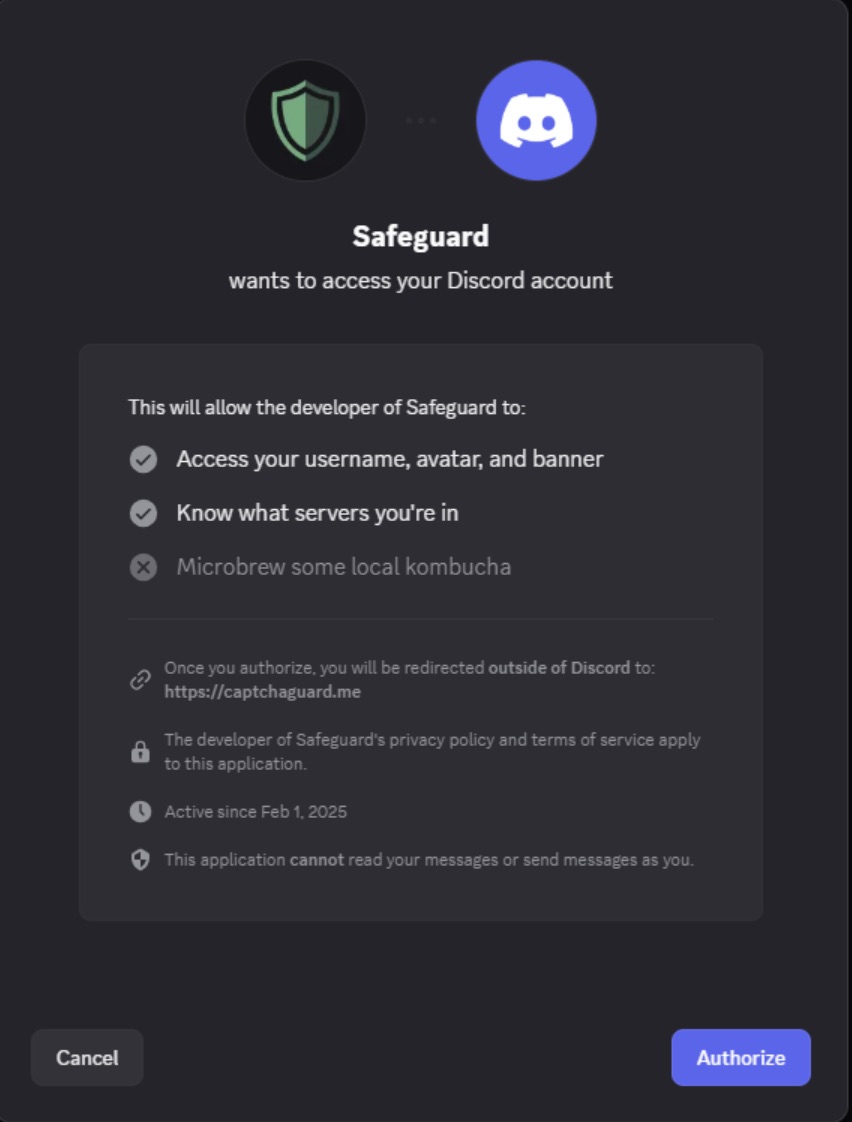
On clicking the Authorize button, the user is automatically redirected to the attackers’ external site, where the next and most important phase of the attack begins. Source
After authorization, the bot gains access to profile information (username, avatar, banner), and the user is redirected to an external site: https://captchaguard[.]me. Next, the user goes through a chain of redirects and ends up on a well-designed web page that mimics the Discord interface, with a Verify button in the center.
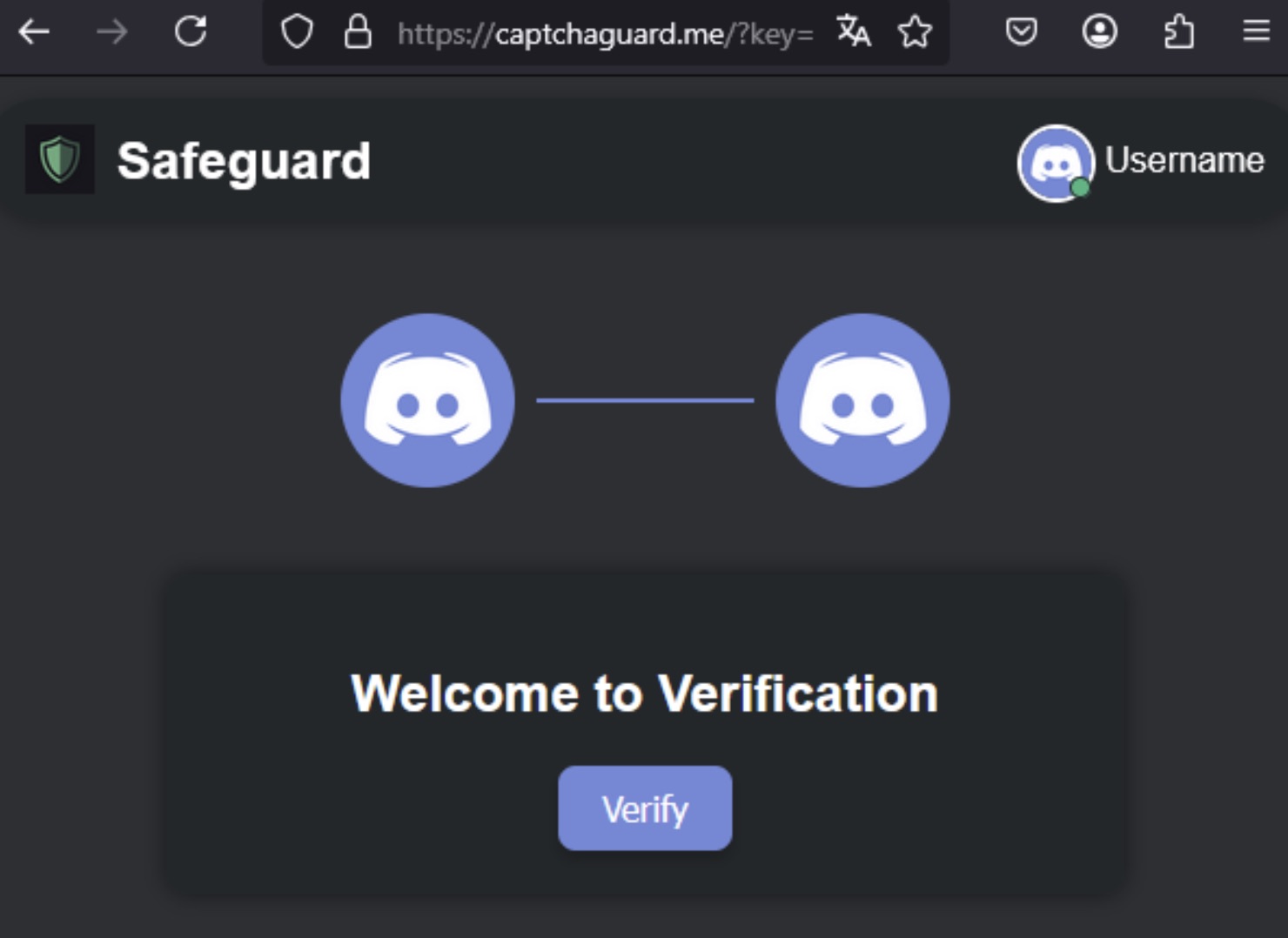
Redirection takes the user to a fake page styled to look like the Discord interface. Clicking the Verify button activates malicious JavaScript code that copies a PowerShell command to the clipboard Source
Clicking the Verify button activates JavaScript code that copies a malicious PowerShell command to the clipboard. The user is then given precise instructions on how to “pass the check”: open the Run window (Win + R), paste the clipboarded text (Ctrl + C), and click Enter.
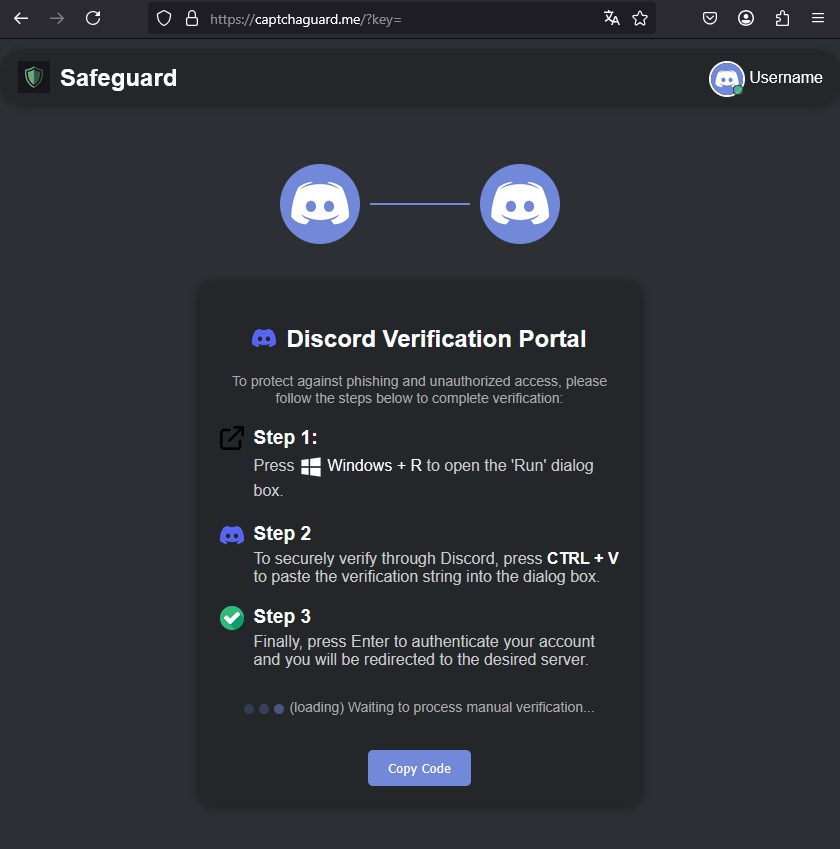
Next comes the ClickFix technique: the user is instructed to paste and run the malicious command copied to the clipboard in the previous step. Source
The site does not ask the user to download or run any files manually, thereby removing the typical warning signs. Instead, users essentially infect themselves by running a malicious PowerShell command that the site slips onto the clipboard. All these steps are part of an infection tactic called ClickFix, which we’ve already covered in depth on our blog.
AsyncRAT and Skuld Stealer malware
The user-activated PowerShell script is the first step in the multi-stage delivery of the malicious payload. The attackers’ next goal is to install two malicious programs on the victim’s device — let’s take a closer look at each of them.
First, the attackers download a modified version of AsyncRAT to gain remote control over the infected system. This tool provides a wide range of capabilities: executing commands and scripts, intercepting keystrokes, viewing the screen, managing files, and accessing the remote desktop and camera.
Next, the cybercriminals install Skuld Stealer on the victim’s device. This crypto stealer harvests system information, siphons off Discord login credentials and authentication tokens saved in the browser, and, crucially, steals seed phrases and passwords for Exodus and Atomic crypto wallets by injecting malicious code directly into their interface.
Skuld sends all collected data via a Discord webhook — a one-way HTTP channel that allows applications to automatically send messages to Discord channels. This provides a secure way for stealing information directly in Discord without the need for a sophisticated management infrastructure.
As a result, all data — from passwords and authentication tokens to crypto wallet seed phrases — is automatically published in a private channel set up in advance on the attackers’ Discord server. Armed with the seed phrases, the attackers can recover all the private keys of the hijacked wallets and gain full control over all cryptocurrency assets of their victims.
How to avoid falling victim?
Unfortunately, Discord’s invite system lacks transparency and clarity. And this makes it extremely difficult, especially for newbies, to spot the trick before clicking a hijacked link and during the redirection process.
Nevertheless, there are some security measures that, if done properly, should fend off the worst outcome — a malware-infected computer and financial losses:
- Never paste code into the Run window if you don’t know exactly what it does. Doing this is extremely dangerous, and normal sites will never give such an instruction.
- Configure Discord privacy and security by following our detailed guide. This will not guard against hijacked invite links, but will minimize other risks associated with Discord.
- Use a reliable security solution that gives advance warning of danger and prevents the download of malware. It’s best to install it on all devices, but especially on ones where you use crypto wallets and other financial software.
Malicious actors often target Discord to steal cryptocurrency, game accounts and assets, and generally cause misery for users. Check out our posts for more examples of Discord scams:
Kaspersky official blog – Read More


