Top Email Security Risks for Businesses and How to Catch Them Before They Cause Damage
Even with all the new ways we stay in touch, Slack, Teams, DMs, email is still the backbone of business communication. That also makes it one of the easiest ways in for attackers.
A single message with the right subject line or attachment can lead to stolen logins, malware infections, or even full network access. It happens so fast that many employees don’t notice until it’s too late.
Let’s take a closer look at the most common security risks businesses face when it comes to email, and what you can do to avoid falling into those traps.
Why Email is Still a Big Risk for Businesses
For security teams, email is often the most unpredictable part of the attack surface. Firewalls, EDR, and filters help but one convincing message can still get through.
Here are a few reasons why email remains a top security concern:
- It’s too familiar: Employees open dozens (or hundreds) of emails a day. One click on a fake invoice or calendar invite is all it takes.
- Threats are getting smarter: Attackers use trusted services like SharePoint or QR codes. They design malware that doesn’t trigger alerts.
- Some attacks don’t need clicks: Zero-click exploits can launch as soon as the message is previewed.
- Traditional tools miss behavior: Filters and antivirus might scan attachments, but they don’t show what the file does once it’s opened.
To reduce risk, businesses need visibility into what’s happening behind the scenes; what gets triggered, what connects where, and what the real intent is.
Sandboxes like ANY.RUN makes that possible. It lets security teams safely detonate suspicious emails and watch every step of the attack before it reaches users or spreads across the network.
Check Out Real Email Attacks That Target Businesses Now
The following real-world cases, captured inside ANY.RUN’s sandbox, show how today’s most common email threats actually unfold. From malware-laced attachments to zero-click exploits, these examples reveal the tactics that put businesses at risk every day.
1. Malware Attachments: A Hidden Threat in Everyday Emails
Malware-laced attachments remain one of the most effective ways for attackers to break into corporate systems. According to Verizon’s 2024 Data Breach Report, more than 50% of successful email-based attacks involved malicious attachments, often disguised as invoices, contracts, or shipping documents. All it takes is one click from a distracted employee.
These files can open the door to data theft, ransomware, and full system compromise.
Here’s a real-world example that shows exactly how this happens, captured in an ANY.RUN sandbox session where the entire attack chain unfolds in front of you.
Real Case: A Dangerous PDF That Looks Legit
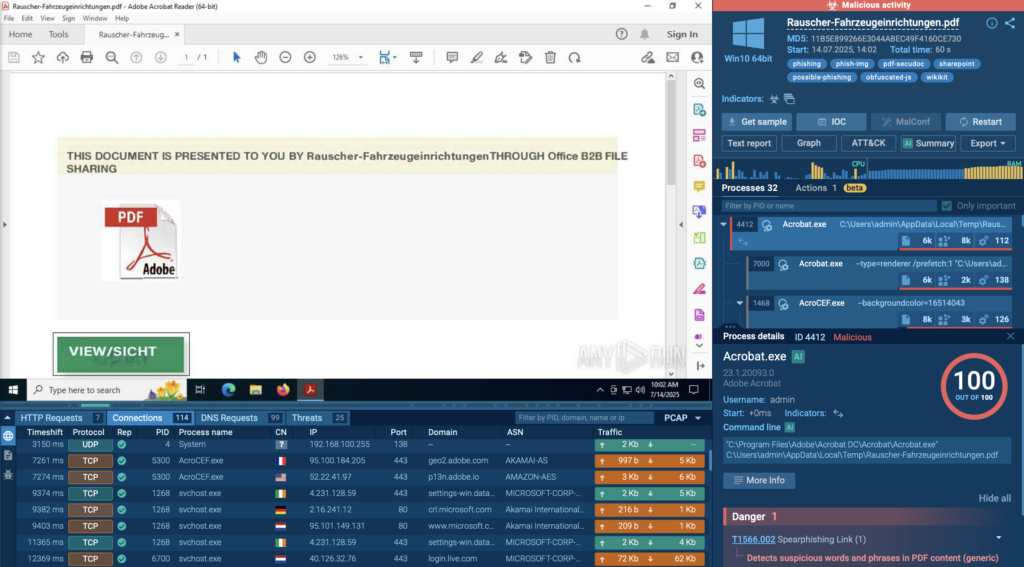
In this analysis, the file is named Rauscher-Fahrzeugeinrichtungen.pdf; harmless enough at first glance. But once opened, it immediately starts reaching out to a phishing page hosted on SharePoint. That’s your first red flag.
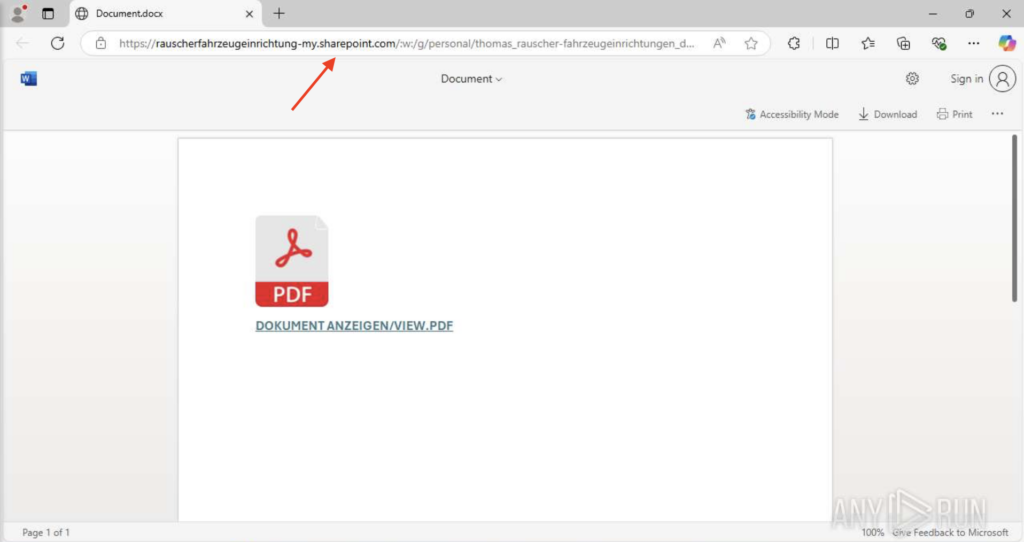
Why SharePoint? Because it’s a legitimate Microsoft domain, often trusted by corporate environments. Hosting a phishing link there increases the chance of bypassing security filters and convincing the user to trust it.
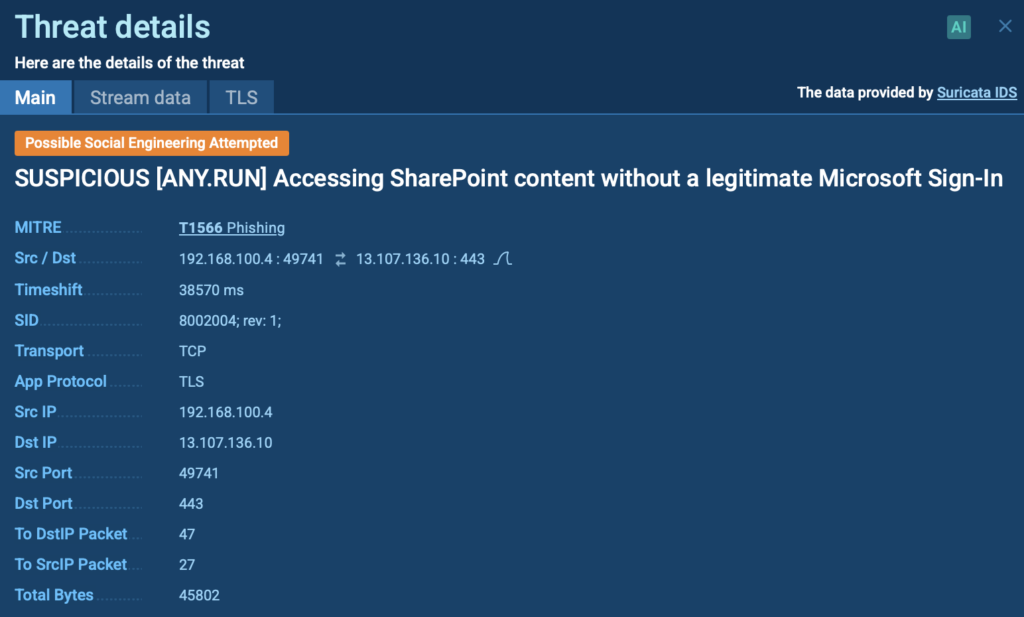
ANY.RUN flags this right away. In the Threats panel, we see it’s marked as “Social Engineering Attempted” and tied to MITRE Technique T1566 (Phishing).
Digging deeper, the PDF contains obfuscated JavaScript; a common trick used to hide malicious code from basic scanners. The user doesn’t see anything unusual, but Adobe Acrobat and Microsoft Edge are triggered, opening a fake Microsoft login page. These processes attempt to communicate with external servers and interact with the system in suspicious ways.
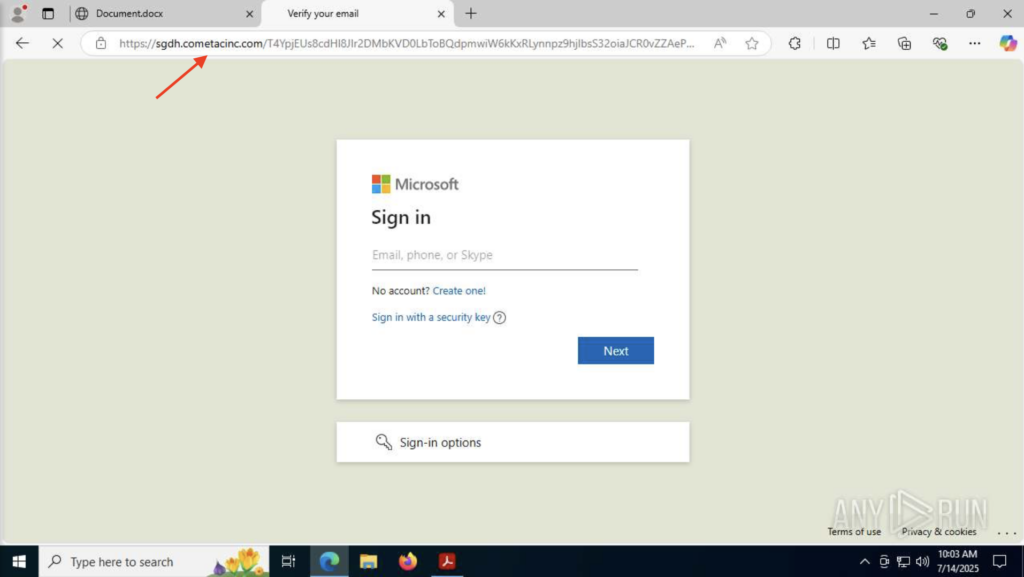
The goal of the attack here is to steal credentials using social engineering and invisible redirections. Everything about this PDF is designed to trick both the user and the security software.
Without a sandbox, this kind of attack is easy to miss. The file looks like a regular PDF, the hosting domain is trusted, and the user doesn’t see anything unusual until it’s too late.
But with ANY.RUN:
- Your team sees the entire attack flow in real time
- Threats are automatically labeled and enriched with context
- You can generate a full malware analysis report and act before damage spreads
2. Credential Theft: When One Click Gives Away Everything
Login credentials are gold for attackers. With the right email and a well-placed link, they can trick employees into handing over usernames and passwords, sometimes without even realizing it.
In fact, spearphishing links (MITRE T1566.002) remain one of the most popular ways to steal credentials, especially those tied to business accounts like Microsoft 365 or Gmail.
Here’s one case from the ANY.RUN sandbox that shows exactly how fast it can happen.
Real Case: Phishing with Tycoon 2FA
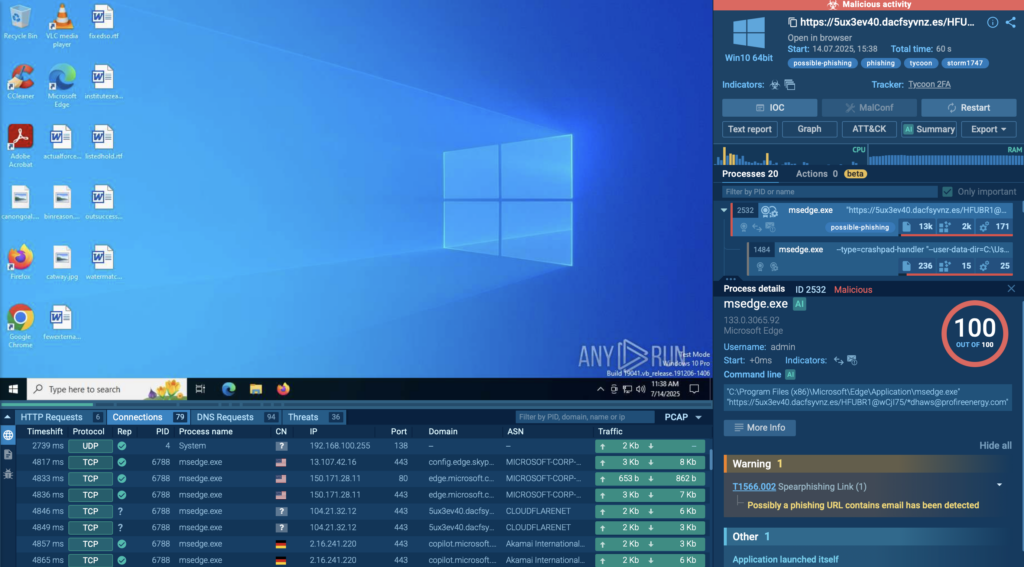
This phishing campaign used a platform called Tycoon 2FA; a tool designed to bypass multi-factor authentication on Microsoft and Google accounts. It all starts with a single malicious link sent via email.
Once the victim clicks the link, the system opens it in the browser, but that’s just the beginning. In the sandbox, we can see multiple Microsoft Edge processes launch one after another, which is already suspicious.
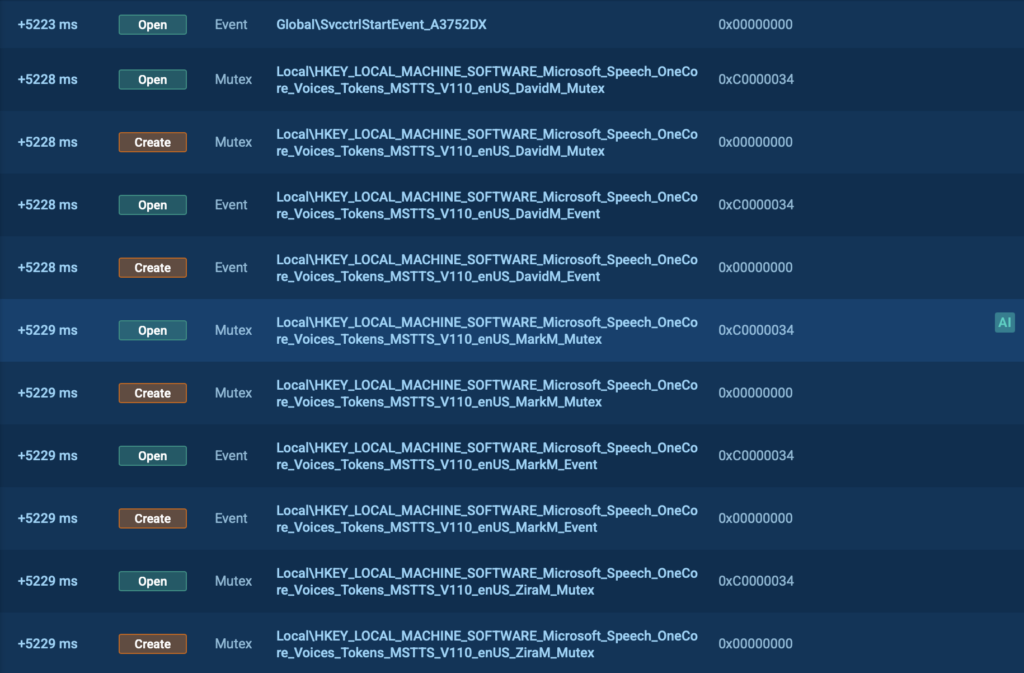
Then things get weirder. The sandbox also shows that these processes are modifying browser cache and user data folders, which normally wouldn’t happen during casual browsing.
The system also starts making changes in the registry, a place Windows uses to store settings. This often points to deeper system manipulation.
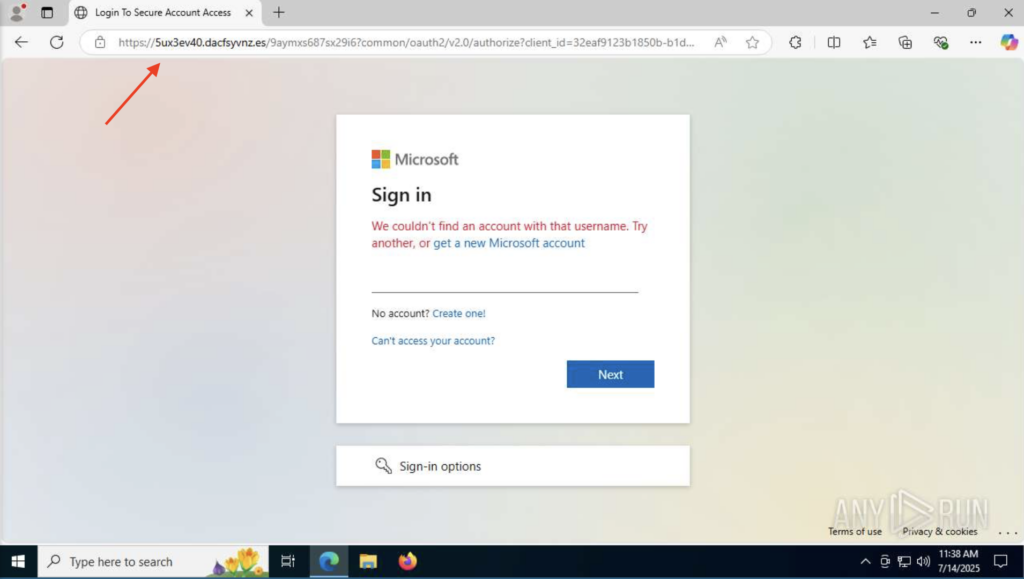
Eventually, the victim is redirected to a fake Microsoft login page. It looks completely legitimate, but it’s hosted on a malicious domain. If the victim enters their credentials here, the attacker gets immediate access.
The sandbox also catches a possible connection to the Tor network, which attackers often use to hide where the stolen data is being sent.
Phishing links like this don’t leave much trace but a sandbox catches what users and filters miss. With ANY.RUN, you see how the attack really works, so you can block it smarter, faster, and for good.
3. Zero-Day Exploits: When Hackers Use the Tools You Haven’t Patched For
Some attacks don’t rely on tricking users; they rely on software flaws that no one even knows about yet. These are zero-day exploits, and they’re dangerous because there’s no fix when they first appear.
One of the most recent examples is CVE-2024-43451, a Windows vulnerability that leaks a user’s NTLMv2 hash; a sensitive authentication value. All it takes is interacting with a specially crafted shortcut file. Just hovering, renaming, or deleting it can silently trigger a connection to a remote server controlled by the attacker.
Once the hash is captured, it can be reused to impersonate the user in a classic pass-the-hash attack, giving intruders a way to move through the network with elevated access.
Real Case: Phishing with Zero Interaction
In this sandbox session, attackers exploit the CVE-2024-43451 vulnerability to launch a malicious HTML file from an .eml email attachment. The user doesn’t need to click a link or run anything manually; just opening the email is enough to trigger the chain.
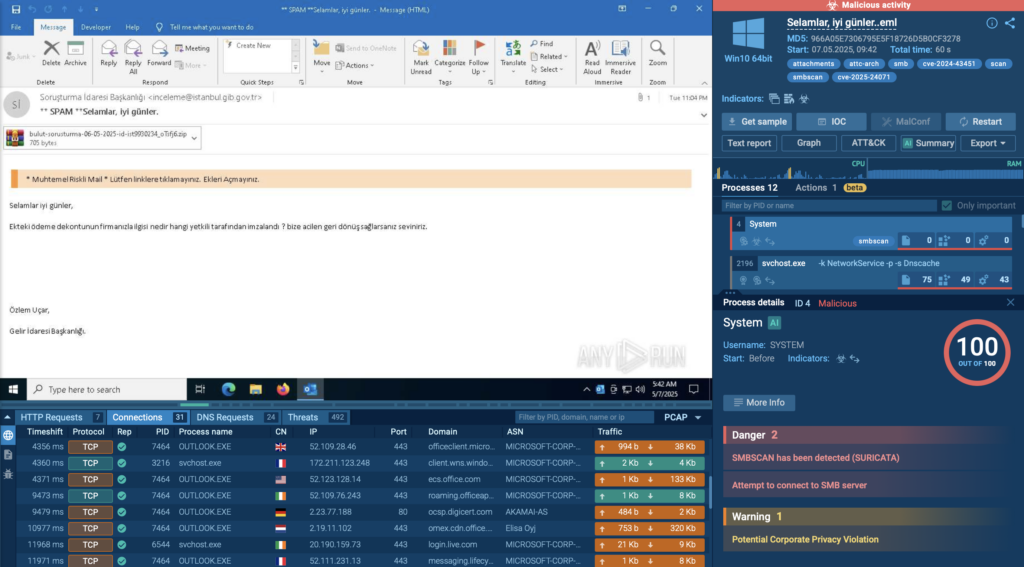
Microsoft Edge launches instantly and redirects the user to a phishing site, without any additional interaction. This is a textbook example of a zero-interaction phishing attack, where the victim is compromised simply by viewing the message
Inside the sandbox, we also see that the malicious file triggers WinRAR.exe, which in turn executes hidden commands tied to the CVE-2024-43451 vulnerability.
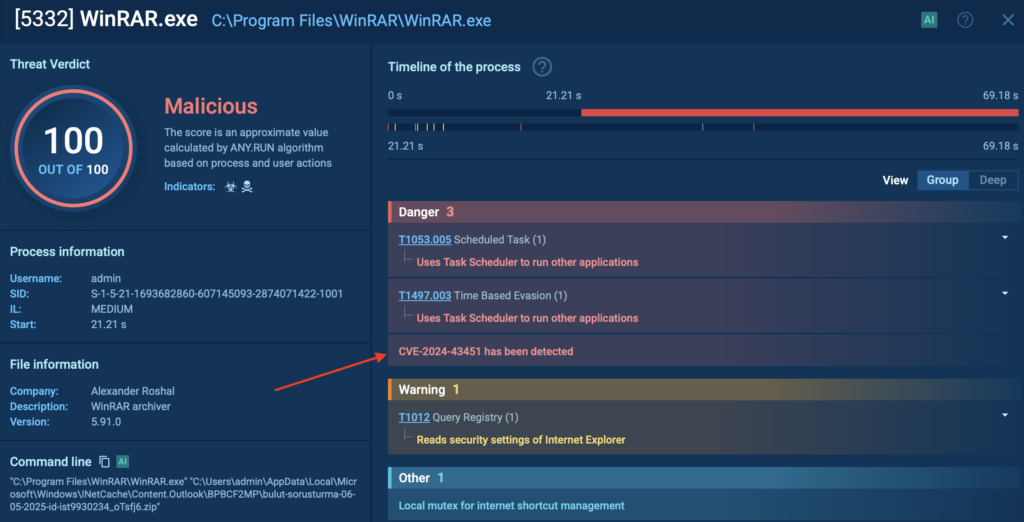
But that’s not all. The exploit leads to a silent SMB connection; a network communication that sends the victim’s NTLMv2 hash to an external server. This hash can later be used in pass-the-hash attacks, letting intruders move through a network as if they were the victim.
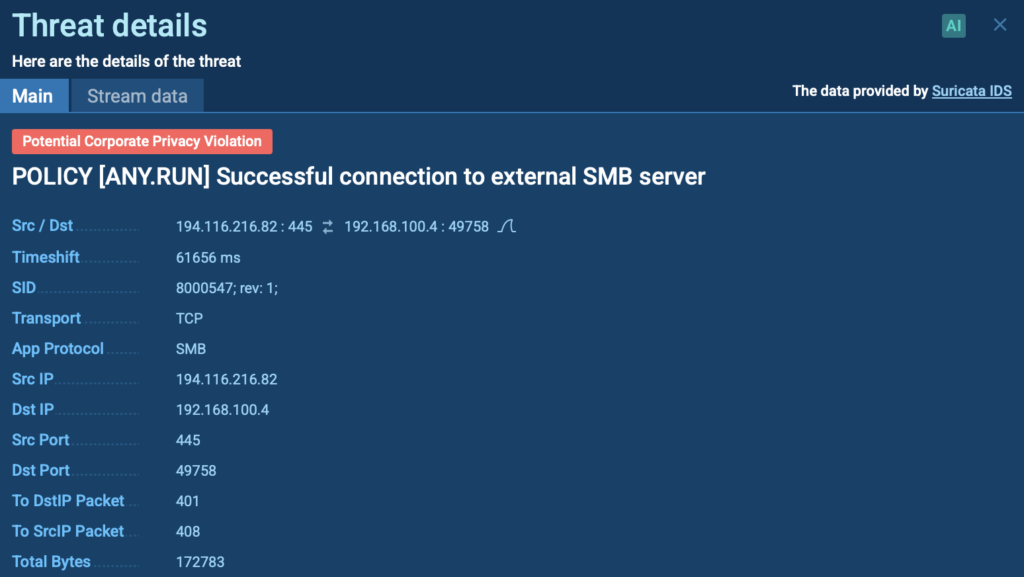
This kind of attack is especially dangerous because it doesn’t rely on clicks or user mistakes. It looks like a normal email but behind the scenes, it opens the door to credential theft and internal access.
With ANY.RUN, the entire chain was exposed in under one minute. That kind of speed gives your security team a real advantage, cutting detection time, reducing investigation effort, and preventing costly breaches before they unfold.

4. Quishing: When a QR Code Becomes the Attack
QR codes have become part of everyday life; menus, logins, verifications. And attackers know it. That’s what makes Quishing (QR phishing) so effective.
Instead of sending a suspicious link, attackers embed a QR code into an email, document, or image. When scanned, it sends the user to a fake website, often mimicking Microsoft 365, voicemail systems, or banking portals, where credentials can be stolen or malware downloaded.
As the code is scanned on a phone, it often bypasses email filters and endpoint protection entirely. Since mobile devices are typically outside the company’s full security stack, they make an easy target.
Real Case: Fake Voicemail Lures via QR Code
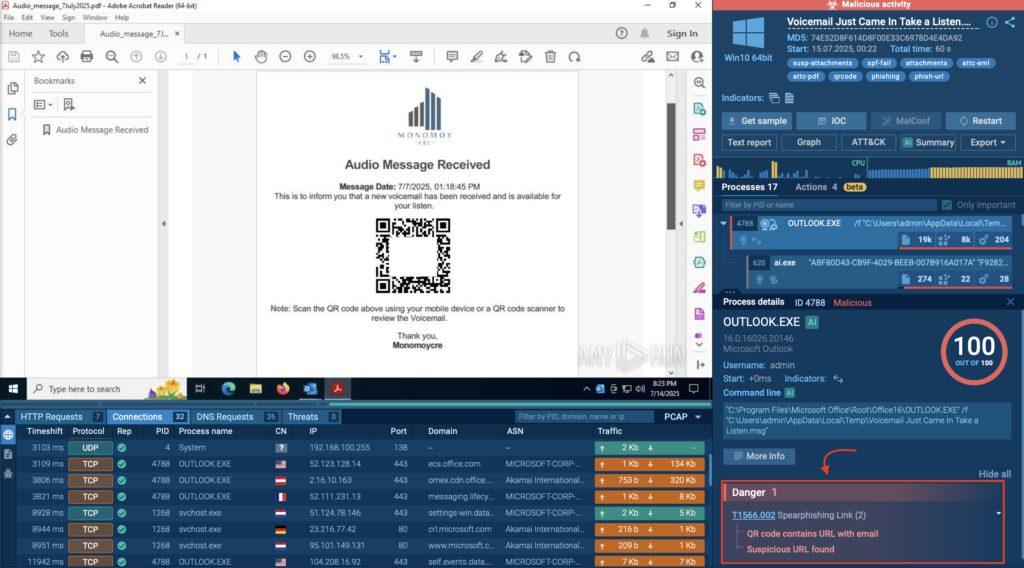
In this ANY.RUN sandbox session, the attack comes in the form of an email telling the user they have a voicemail waiting, asking them to scan a QR code to listen.
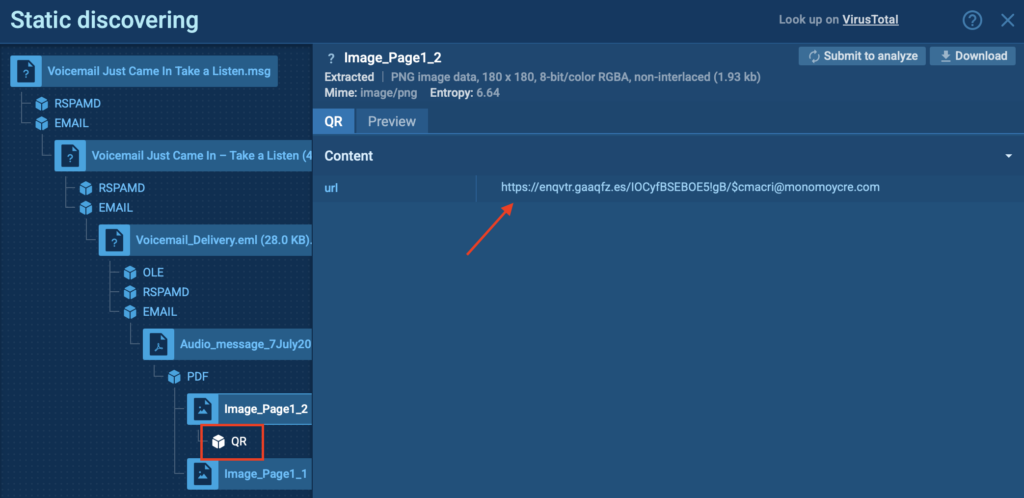
Thanks to the sandbox’s automated interactivity, analysts don’t need to manually extract or decode anything. The QR code is scanned automatically, and the URL is uncovered; all in just a few seconds.
That means faster insights, less analyst effort, and a clearer view of where the attack leads, even when the delivery method tries to avoid traditional defenses. For businesses, it’s a smarter way to catch threats that bypass filters and target mobile users directly.
5. CVE-2017-11882: Exploiting a Known Vulnerability in Microsoft Office
CVE-2017-11882 is a remote code execution (RCE) vulnerability in a legacy component of Microsoft Office; the Equation Editor (eqnedt32.exe). This flaw is caused by a stack buffer overflow, which occurs due to improper handling of objects in memory. When exploited, it allows attackers to execute arbitrary code on the victim’s system.
All it takes is for the user to open a specially crafted Office document, typically in .RTF or .DOC format.
Real Case: Triggering the Exploit via Malicious Email
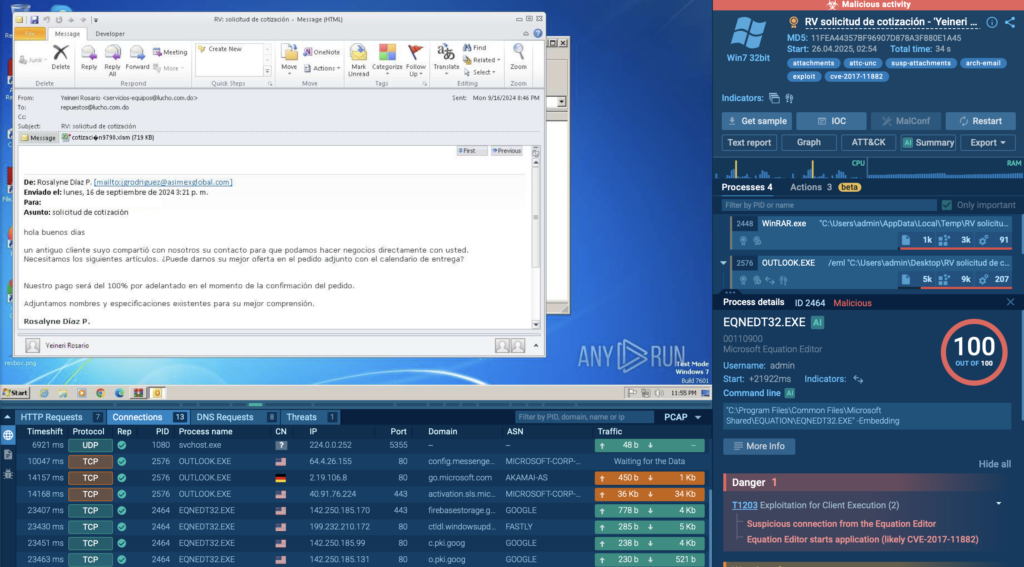
In this sandbox session, the malicious payload is delivered via an email containing a .eml attachment. This attachment includes an Office document that exploits CVE-2017-11882 through the Equation Editor.
ANY.RUN identified the exploit within seconds of the document opening, flagging the vulnerable process and its suspicious behavior right away. By catching CVE-2017-11882 so early, teams can reduce mean time to detect (MTTD), avoid time-consuming manual investigation, and respond before the threat spreads.
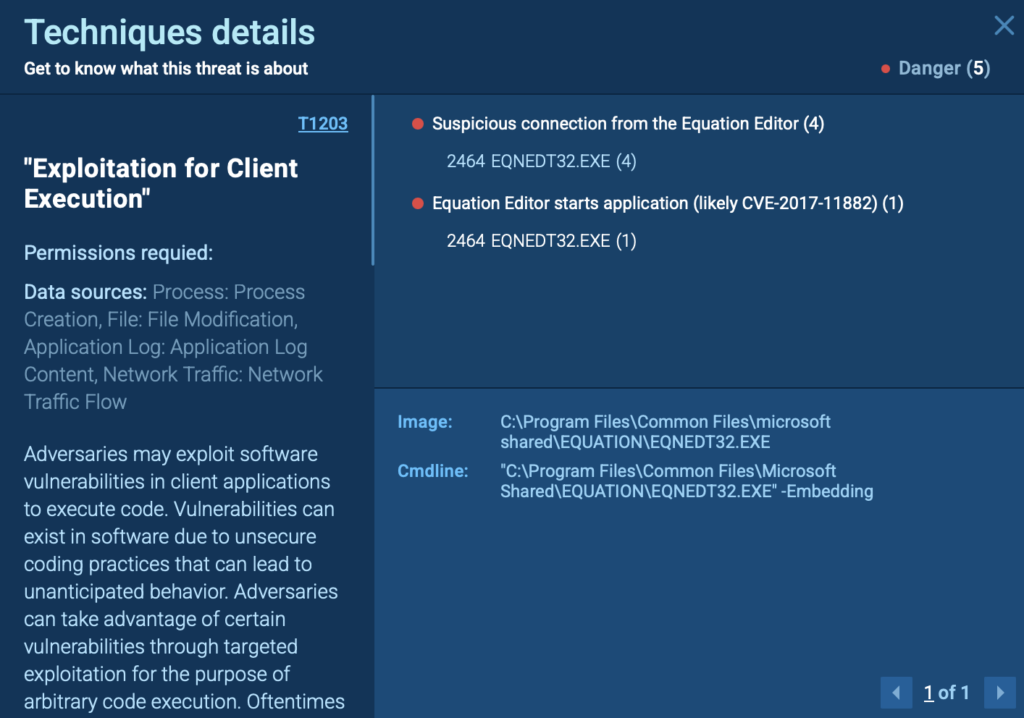
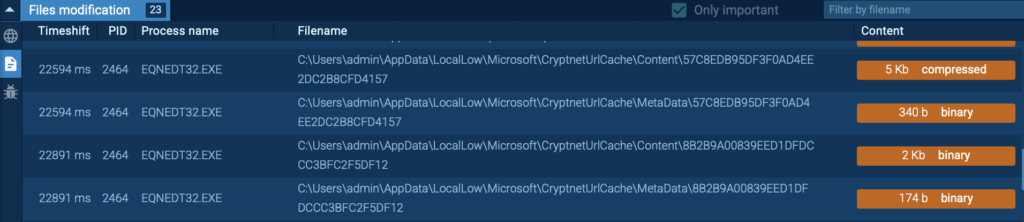
As soon as the victim opens the file, the EQNEDT32.EXE process is triggered, kicking off a series of malicious actions:
- Reading system parameters and configurations
- Accessing stored certificates and proxy settings
- Creating and dropping new files
- Establishing connections to external servers
Strengthen Your Email Security Before the Next Threat Hits
The above-mentioned attacks are happening right now, in inboxes just like yours. Some rely on tricking users. Others don’t need user interaction at all. And in many cases, traditional defenses simply don’t catch them in time.
This is exactly where ANY.RUN’s sandbox comes in handy. With real-time sandbox analysis, your team can uncover how threats behave, understand their full impact, and stop them before they spread.
Here’s what you gain when ANY.RUN becomes part of your email security workflow:
- Faster detection of threats and reduced Mean Time to Detect (MTTD)
- Full visibility into what files and links actually do without any guesswork
- Immediate access to IOCs for SIEM enrichment and faster response
- Less manual effort for analysts, thanks to automated interactivity
- Lower risk of breaches, data loss, and business disruption
- Shareable, detailed reports for internal teams, clients, or compliance needs
Try ANY.RUN now and take back control of your email security.
About ANY.RUN
ANY.RUN is relied on by more than 500,000 cybersecurity professionals and 15,000+ organizations across finance, healthcare, manufacturing, and other critical industries. Our platform helps security teams investigate threats faster and with more clarity.
Speed up incident response with our Interactive Sandbox: analyze suspicious files in real time, observe behavior as it unfolds, and make faster, more informed decisions.
Strengthen detection with Threat Intelligence Lookup and TI Feeds: give your team the context they need to stay ahead of today’s most advanced threats.
Want to see it in action? Start your 14-day trial of ANY.RUN today →
The post Top Email Security Risks for Businesses and How to Catch Them Before They Cause Damage appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
