Beating Supply Chain Attacks: DHL Impersonation Case Study
ANY.RUN’s services processes data on current threats daily, including attacks affecting supply chains. In this case study, we analyze examples of DHL brand abuse. The company is a leading global logistic operator, and attackers exploit its recognition to send phishing emails, potentially targeting its partners.
We will demonstrate how ANY.RUN’s solutions can be used to identify such threats, collect technical indicators, and enhance security. Here are the key findings.
Key Takeaways
- Supply chain attacks are on the rise: adversaries actively exploit third-party relationships.
- Real-world example: attackers impersonated DHL in phishing emails targeting partner organizations, like Meralco, using fake domains and deceptive attachments to collect credentials.
- HTML attachment bypasses filters: lesser-known file extensions are used.
- Credential theft via third-party form service: analysis with HTTPS MITM revealed a POST request containing plaintext credentials sent to a unique endpoint.
- Shared visual lures identified by image hash: the DHL-themed image in the phishing email was reverse-searched via its SHA256 hash, revealing five other phishing campaigns using the same lure.
- DHL-imitating domains and filenames as indicators: analysts identified 39 phishing domains (e.g., dhlshipment*, -dhl.) and over 300 malware samples with DHL-themed filenames (e.g., dhlreceipt*.pdf) — exposing common obfuscation patterns and phishing themes used to trick users.
Supply Chain Attack Growing Dynamics
A supply chain attack is a type of cyberattack where adversaries gain access to a target organization by compromising a less protected external participant in the interaction chain: a contractor, a supplier, a technology partner, or another link.
The data from Cyble reveals supply chain attacks steady growth. From October 2024 to May 2025, an average of more than 16 incidents per month has been recorded, a 25% increase from the previous eight-month period. A sharp spike in activity was observed in April and May 2025. This dynamic indicates growing attacker interest in this attack model and its increasingly widespread use in real campaigns.
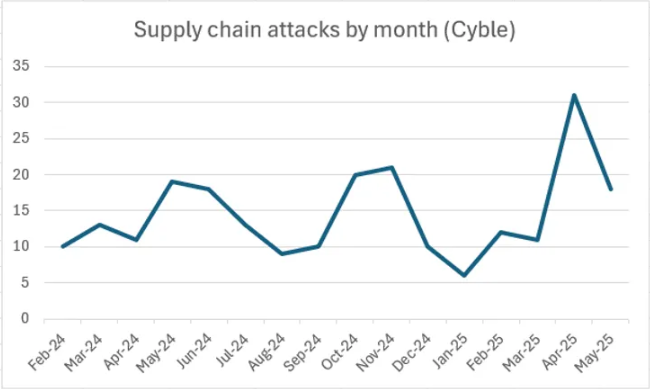
Real-world examples include the Scattered Spider group’s attack on Australian airline Qantas. The attackers penetrated through a third party (contact center), which is typical for such attacks.
DHL Brand Abuse in Phishing Campaigns
Suppose we are information security specialists at a company that collaborates with DHL and could be used by attackers as an intermediate link in the attack chain.
Our task is to detect timely phishing emails disguised as official correspondence from DHL. Such messages may target company employees, contractors, or other DHL partners.
To identify such activity, we use ANY.RUN’s YARA Search — we’ll create a rule that allows us to find .eml files mentioning DHL in the From, To, and Subject headers. This will help collect indicators, identify malicious attachments, and assess potential risks to our infrastructure.
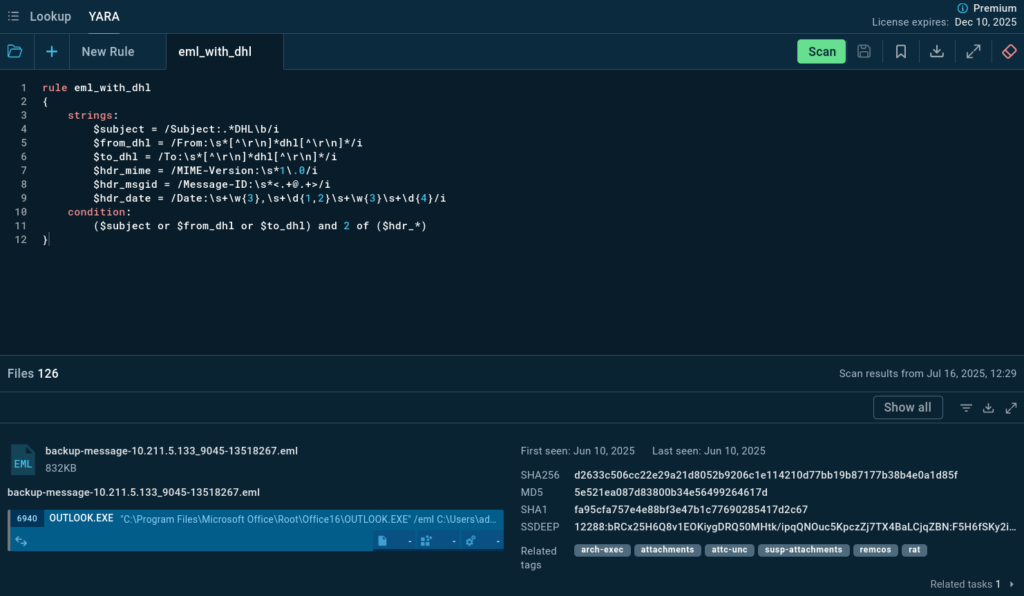
The search delivered over 110 files and associated analysis sessions (tasks) from the ANY.RUN’s Interactive Sandbox. This data allows us to:
- Identify malicious campaigns that exploit the DHL brand, including cases of possible compromise of official email accounts and infrastructure of the company or its contractors.
- Obtain technical indicators.
- Identify applied tactics, techniques, and procedures (TTPs).
- Classify the malware involved.
Not all found objects contain malicious payloads, but many are interesting from an analytical perspective, as examples of malicious brand abuse.
How to Detect DHL-themed Phishing in Your Infrastructure
To effectively detect and analyze DHL-themed phishing attempts within your infrastructure, consider the following practices:
Scan Your Endpoints with YARA Rule
Utilize a YARA rule to scan your email endpoints for any emails related to DHL. Here’s an example of a YARA rule you can use:
This rule helps identify emails that mention DHL in the subject line, sender, or recipient fields.
Analyze Suspicious Emails, Files, and URLs in ANY.RUN’s Interactive Sandbox
ANY.RUN’s Interactive Sandbox allows you to safely open and interact with suspicious files and URLs.
You can safely open emails and click through any attachments or links within a controlled environment. This helps in understanding the full attack chain from the initial phishing email to the execution of any malicious payloads.
Use TI Lookup to Gather Context on Alerts
Leverage ANY.RUN’s Threat Intelligence Lookup to quickly verify whether an artifact (URLs, file hashes, or even command line activities) involved in an alert within your company is associated with a specific attack.
Gather context on the alerts by identifying related campaigns and understanding the broader context of the attacks. This helps in recognizing common tactics, techniques, and procedures (TTPs) used by attackers, allowing for faster and more accurate responses to potential threats.
Case Study: Analyzing a Phishing Email targeting DHL counterparties
We shall analyze in ANY.RUN’s Sandbox one of the emails found by YARA scanning.
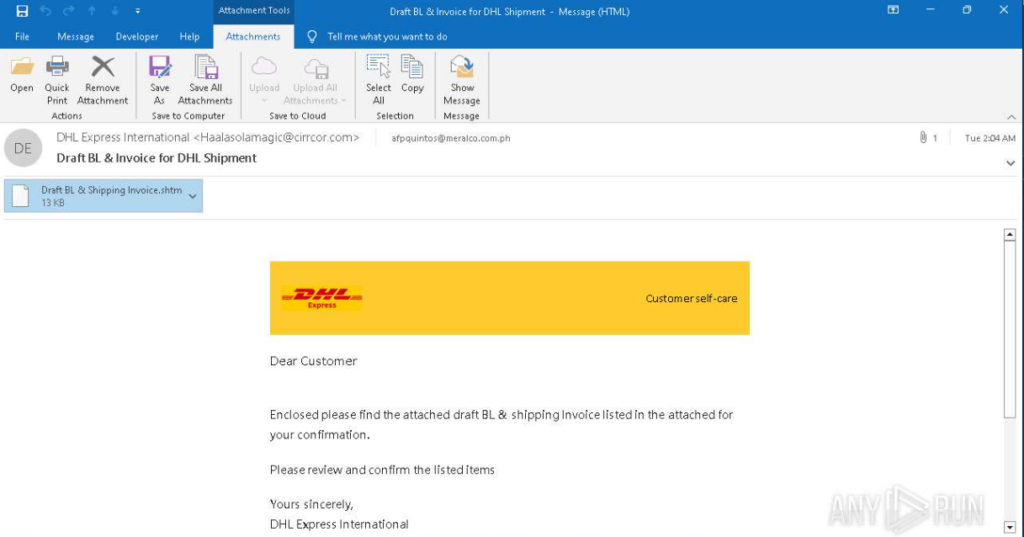
The email sender masquerades as DHL Express International. The “From” field displays the corresponding display name, but the actual sender address Haalasolamagic@cirrcor[.]com belongs to a third-party organization not affiliated with DHL.
The email is directed to an address in the meralco[.]com[.]ph domain, belonging to Meralco, the largest energy company in the Philippines. Previously, DHL objects were mentioned in Meralco’s planned power outage notifications, and in May 2025, Meralco’s subsidiary MSpectrum announced a joint project with DHL Supply Chain Philippines.
Based on this, we can assume that the cooperation between DHL and Meralco does exist, and the attackers’ use of such an addressee may not be coincidental.
The email looks like a part of an attempt at a supply chain attack. The email is not directed to DHL, but to an organization affiliated with it. The use of corporate identity and business context may be part of a scenario where attackers try to gain access to the main target through its partners or contractors — a typical technique in targeted campaigns.
IMPORTANT: Please report all instances of DHL impersonation to the company’s official Anti-Abuse Mailbox.
Email Content Analysis
The email body uses DHL’s corporate identity and phrasing typical for business correspondence. The recipient is asked to open an attachment — a file named “Draft BL & Shipping Invoice.shtm,” allegedly containing a preliminary invoice and waybill for confirmation. The .shtm (a variant of .html) extension is likely used for masking and bypassing email filters.
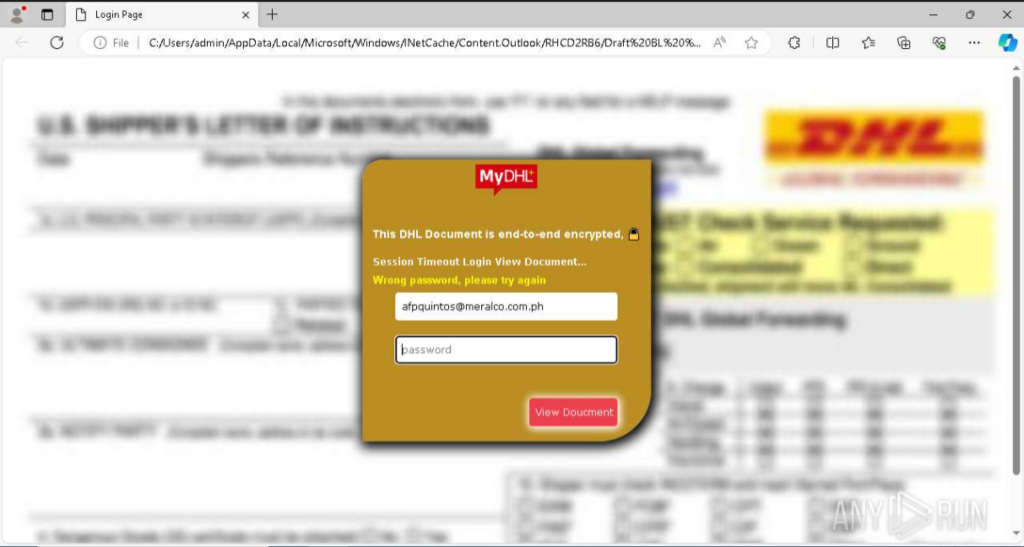
When the attached file is opened in a browser, a DHL-styled web page is displayed with a password submission form. The user is asked to authenticate to view an allegedly encrypted document supposedly sent from DHL. This is typical for phishing pages imitating official delivery services and used to collect credentials.
Network Activity Analysis
The network activity generated while interacting with this form contains a request to submit-form[.]com.
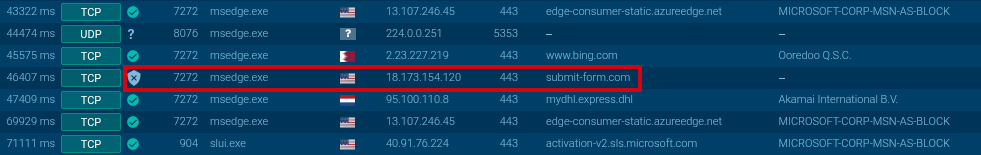
This service is used to collect data entered in HTML forms and allows redirecting it directly to a specified email address.
If we try to analyze the network request sent when entering data into the form, we’ll only see a connection through port 443. The connection is encrypted, and its content, including the entered password, is not available for viewing without applying MITM methods.
MITM Analysis
To get more information, we restart the analysis of this email in ANY.RUN’s Sandbox with the HTTPS-MITM-PROXY (MITM) function enabled to get access to the network packet contents.
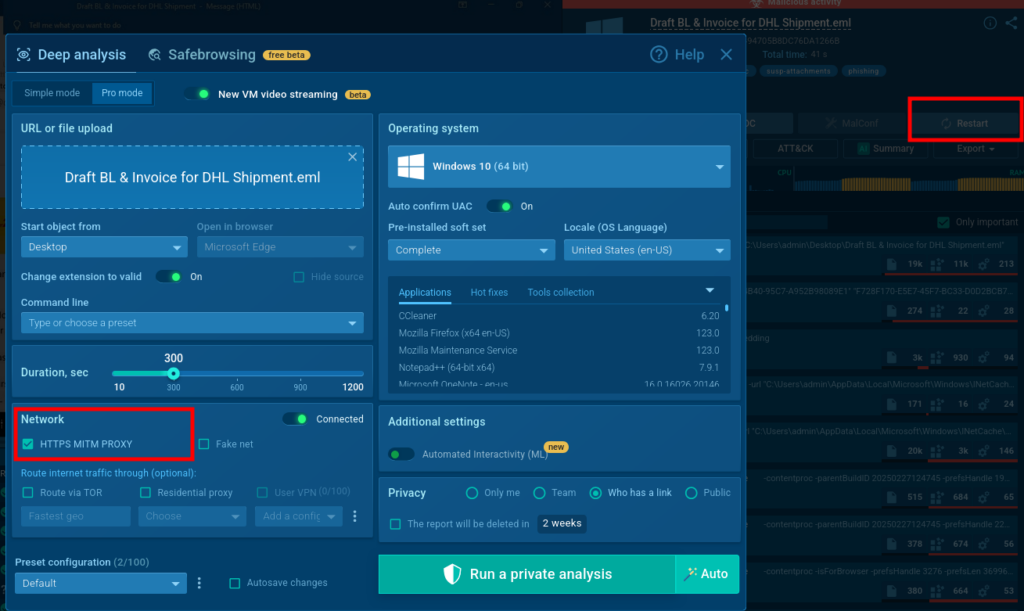
In the new analysis with MITM enabled, we open the attached .shtm file and enter a password in the form, for example “password999,” then click “View Document”.
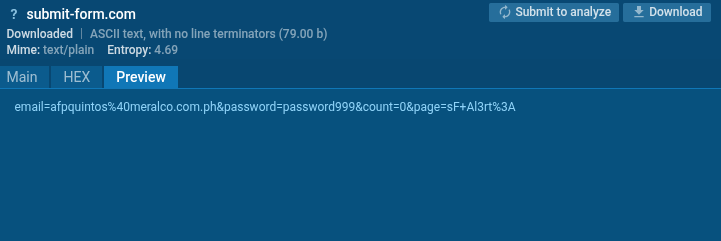
Going to the HTTP Requests tab, we find a POST request sent to https://submit-form[.]com/7zFSu099A.

The request contents confirm the transfer of entered data: the request body contains form field values, including the entered password. This proves that the attacker uses the third-party service submit-form[.]com to collect authentication data entered by the victim on the phishing page.
Submit-form dot com Usage Analysis
Using ANY.RUN Threat Intelligence Lookup to check the submit-form[.]com domain and related campaigns, we find more than 200 public analyses featuring the website. Most are marked as malicious: attackers actively use submit-form[.]com to intercept data entered on phishing pages, including passwords and email addresses.
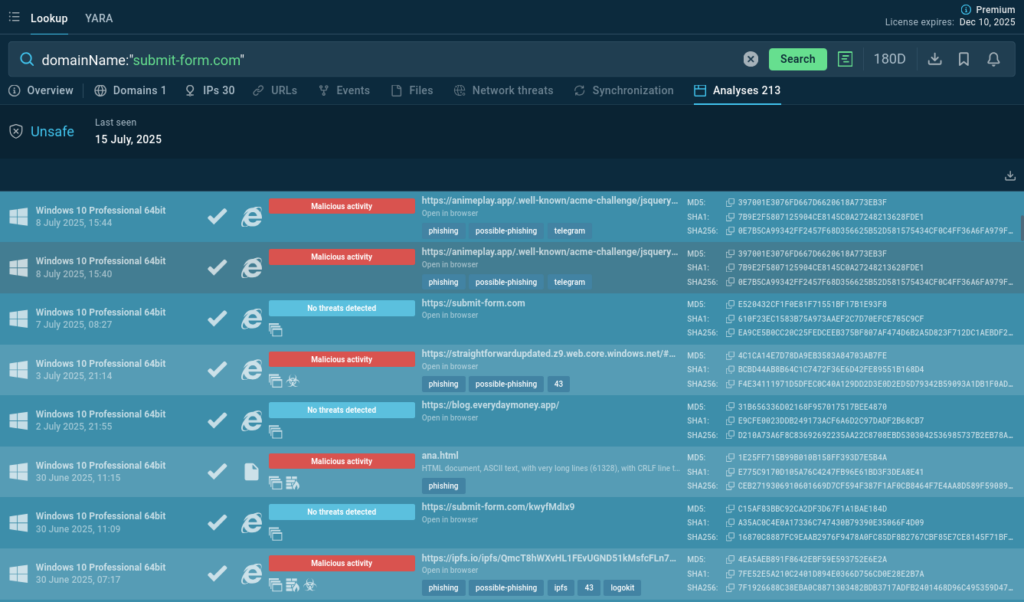
Now we can estimate the relevance and scale of such threats and make decisions about blocking/monitoring of this domain.
Image-Based Search for Similar Attacks
To find additional indicators of similar attacks, we have analyzed the image imitating DHL design used in the email above. Using this image, we can find other phishing campaigns using the same file, thus expanding our set of indicators and understanding of brand abuse scale.
We extract the image’s SHA256 hash from the static analysis and perform a search for the image through ANY.RUN’s TI Lookup.
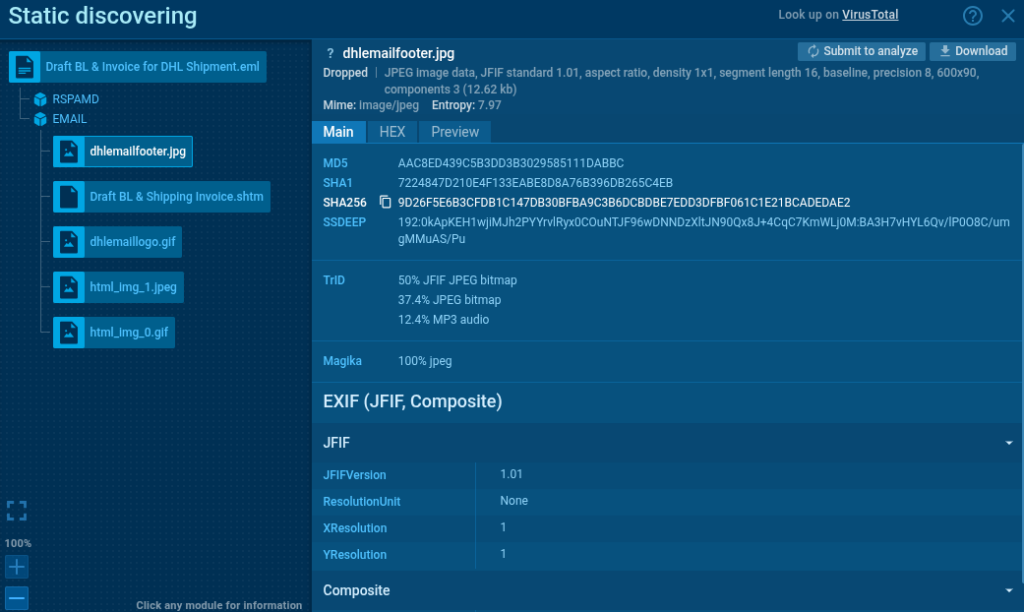
The search returns 5 analyses featuring identical images. They were used in campaigns targeting various addresses that may belong to potential contractors, clients, or company employees.
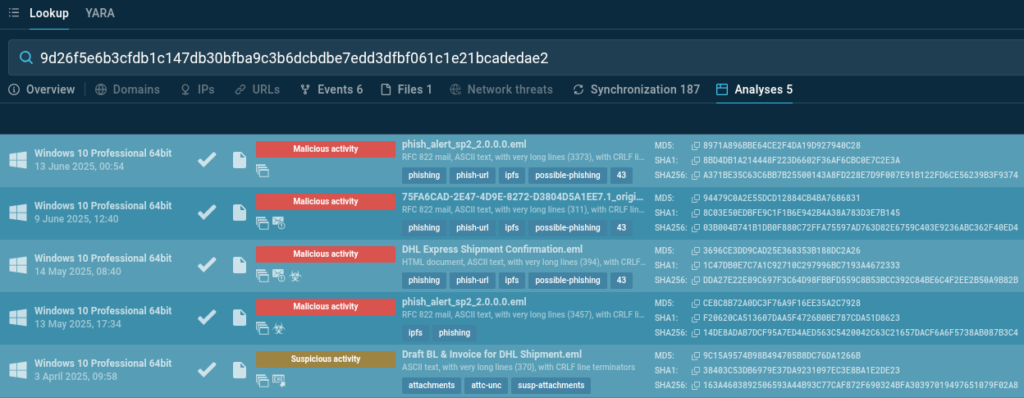
These analyses allow us to study additional social engineering techniques and various phishing strategies and to collect threat indicators: email subjects, sender IP addresses, malicious domains.
Identifying Malicious Domains Imitating DHL
Now we search for domains that imitate official DHL resources to understand what phishing domains might be used to masquerade as partner organizations. This helps us understand:
- What tactics and methods attackers use.
- How such resources are designed (appearance, structure, content copying).
- What payload they may distribute.
A simple query in ANY.RUN’s TI Lookup allows us to find phishing domains imitating DHL, focusing on typical patterns used in the logistics industry, including campaigns masquerading as delivery notifications, documents, or cargo movements.
domainName:”–dhl.” or domainName:”dhlshipment*” OR domainName:”dhldocument*”
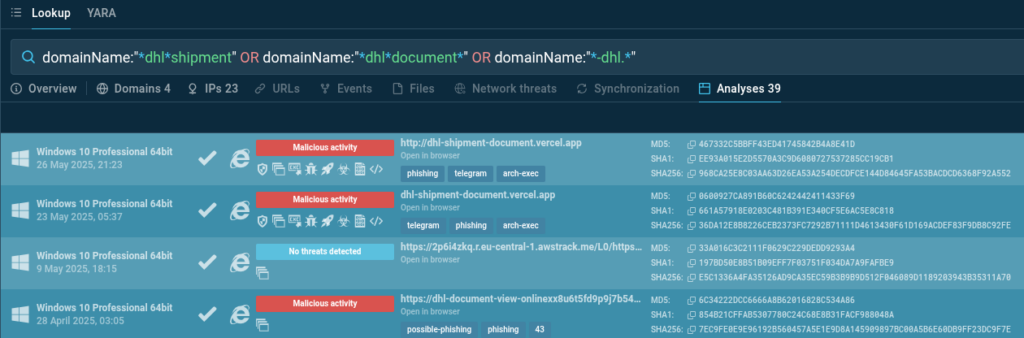
The query results provide access to 39 public analyses containing the specified patterns. This data can be used to enrich IOC collection and improve phishing detection and filtering by security systems.
Analyzing Files Imitating Legitimate DHL Attachments
Additionally, we can search for the names of files uploaded to ANY.RUN that contain mentions of the partner company. This analysis helps to:
- Identify popular malware distribution schemes abusing DHL.
- Determine which malware families are employed.
- Collect related indicators — file names, hashes, attachments.
- Obtain data on vulnerabilities used by attackers.
Here is a TI Lookup query exposing files imitating legitimate DHL attachments:
filePath:”dhlreceipt*” or filePath:”dhlshipment*” or filePath:”dhldelivery*”
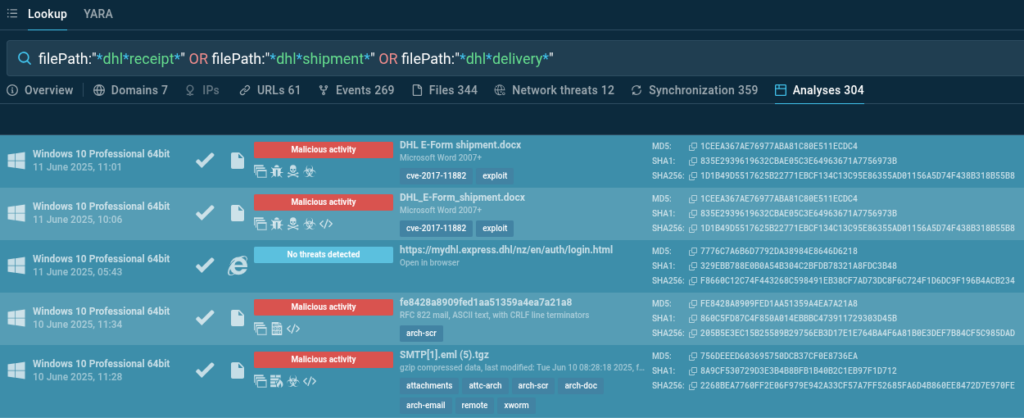
We have found over 300 analyses containing the requested patterns in file names. Not all of them are malicious, but a significant portion is worth analyzing for updating filters, detection rules, and raising awareness about DHL masquerading techniques in recent attacks.
Conclusion
In this case study, we demonstrated how ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup can be used to identify threats related to potential supply chain attacks. Using DHL as an example, we analyzed activity targeting its partners and contractors — from phishing emails to impersonating domains.
Such activity may be part of preparation for supply chain attacks. The presented methods allow timely identification of such risks and adaptation of approaches to the specifics of a particular organization.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Request a trial of ANY.RUN’s services to see how they can boost your SOC workflows.
The post Beating Supply Chain Attacks: DHL Impersonation Case Study appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
