Turn Alert Noise into Threat Insights without Leaving QRadar SOAR with ANY.RUN
IBM QRadar SOAR is a go-to platform for incident response. To make things faster and easier for SOCs to use this powerful tool with ANY.RUN’s services, we built an official app. Now you can seamlessly launch different playbooks directly inside SOAR to streamline threat analysis, speed up investigations, and reduce Mean Time to Respond (MTTR) in your SOC.
Here’s how your team can benefit from the new integration.
Streamline Your SOC Workflows
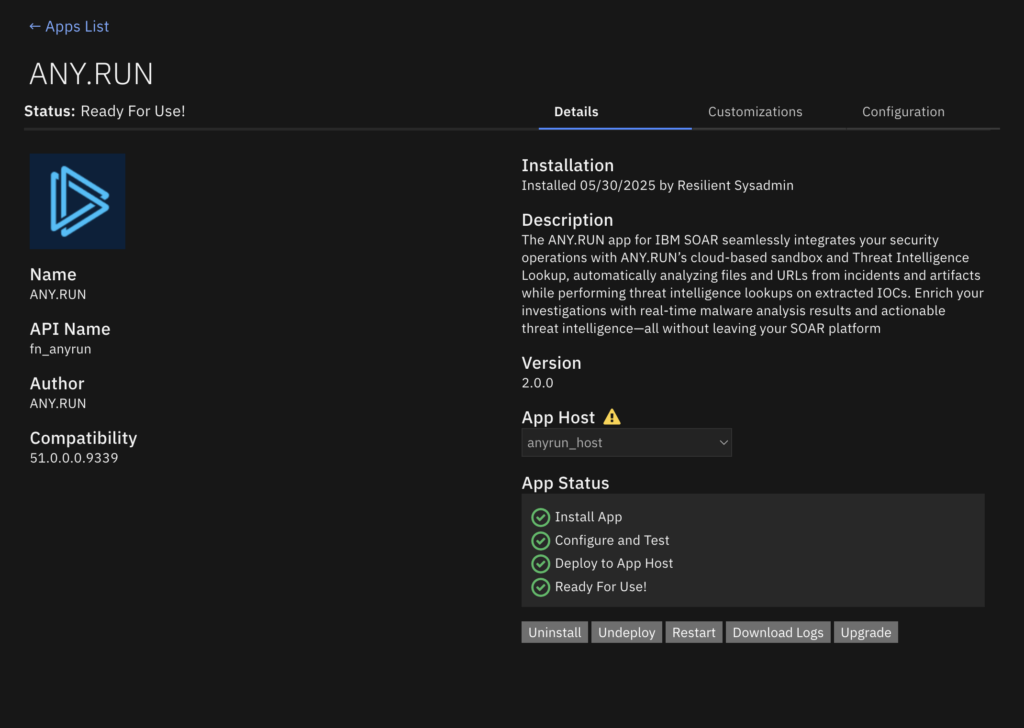
The app available on IBM Exchange allows SOC teams to start using ANY.RUN’s services in a more flexible and seamless way to detect threats and resolve incidents faster. The setup takes a few seconds as you only need an API key to connect your ANY.RUN account to QRadar SOAR, eliminating the need for custom development.
With this integration, you can get IOCs and verdicts from the sandbox and indicator context from TI Lookup to simplify triage and enrich incident data.
- Early Threat Detection: Real-time data from sandbox analyses and TI Lookup enable you to identify and respond to new attacks at their earliest stages.
- Automation of Routine Tasks: Prebuilt playbooks enable automatic or manual actions, saving time for Tier 1 and Tier 2 analysts.
- Reduced Response Times: Cuts incident analysis time by automating enrichment and analysis processes. Results feed directly into SOAR playbooks, enabling rapid isolation, blocking, or escalation based on your workflows.
Proactive Threat Analysis with Interactive Sandbox
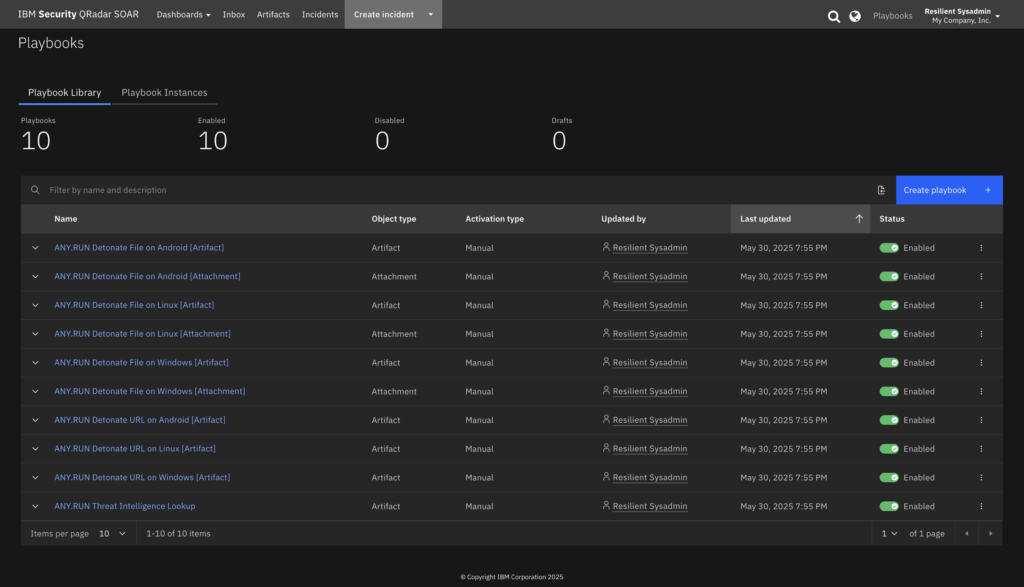
ANY.RUN’s Interactive Sandbox is a cloud-based service for analysis of suspicious files and URLs. It provides SOC teams with instant access to fully interactive Windows, Linux, and Android virtual machines, allowing you to engage with the system and the sample at hand and detonate every stage of the attack, from opening an email attachment to solving a CAPTCHA.
The sandbox logs and marks malicious network traffic, processes, registry and file modifications, providing instant visibility into the threat’s behavior. For each analysis, it generates a comprehensive report with a threat level verdict, IOCs, and TTPs.
With IBM QRadar SOAR integration, your SOC team can use the Automated Interactivity of the Sandbox to:
- Triage Files and URLs: Send suspicious files or URLs from IBM QRadar SOAR to ANY.RUN’s Sandbox for instant analysis, reducing manual effort.
- Gain Deep Behavioral Insights: Access detailed logs of malicious activities, including network traffic, processes, and file changes, for thorough threat understanding.
- Auto-Detonate Multi-Stage Attacks: Take advantage of Automated Interactivity for automated execution of user actions such as archive extraction, CAPTCHA solution, and payload launching to reach the final stage of the attack and ensure complete detection.
For the most accurate results, it’s recommended to avoid manual interference during the sandbox session. Let the analysis run to completion, so all behavior stages can be observed and properly logged.
Instant Incident Enrichment with TI Lookup
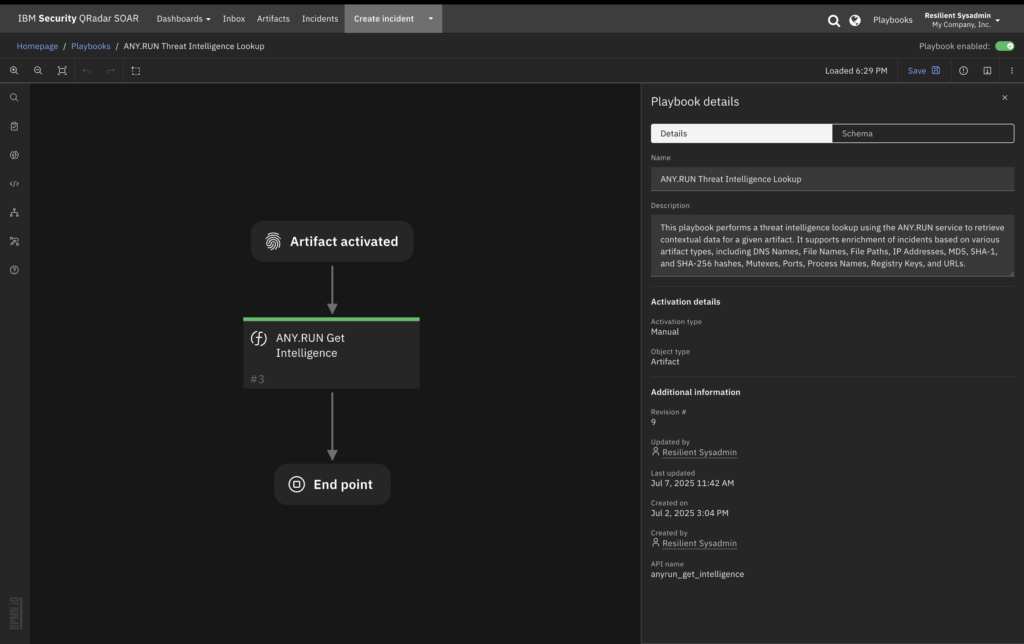
Threat Intelligence Lookup contains a database of fresh Indicators of Compromise (IOCs), Behavior (IOBs), and Action (IOAs) extracted from live sandbox analyses of active malware and phishing attacks across 15,000 organizations.
It lets you search across various types of indicators, from IPs and domains to mutexes and registry keys. Since all data comes from real-time detonation of threats, TI Lookup always offers fresh indicators, available within hours and even minutes after the attack happened.
With IBM QRadar SOAR integration, your SOC team can use TI Lookup to:
- Enrich Incidents Automatically: Pull detailed threat intelligence for key indicator types, including DNS Name, File Name, File Path, IP Address, MD5, SHA-1, SHA-256, Mutex, Port, Process Name, Registry Key, and URL, directly into SOAR incidents.
- Add Behavioral Threat Context: Enhance indicators with behavioral insights from live sandbox analyses, providing deeper context for threat understanding.
- Speed Up Threat Assessment: Use fresh, high-quality data from 15,000 organizations to quickly evaluate and prioritize potential threats.
What Your Team Gains: Business and Operational Benefits
The IBM QRadar SOAR integration with ANY.RUN delivers measurable performance gains across your SOC, improving key metrics like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), while enhancing decision-making at every level.
- Cost and Time Savings: Lower analyst workload by automating repetitive tasks, allowing focus on critical threats.
- Increased SOC Efficiency: Streamline triage, investigation, and escalation for Tier 1 and Tier 2 analysts with built-in automation and enriched data, reducing alert fatigue and manual steps.
- Enhanced Decision-Making and Process Improvement: Use detailed Sandbox reports and enriched data to create more effective rules, update response playbooks, and train detection models.
- Proactive Threat Management: Detect emerging threats earlier with fresh, behavior-based data from real-time malware analysis. TI Lookup and Sandbox insights help you uncover stealthy or multi-stage attacks that traditional tools may miss.
- Stronger ROI from Existing Tools: Maximize the value of your SOAR investment by extending its capabilities with behavioral analysis and contextual enrichment, no additional infrastructure required.
How to Get Started
Getting started with the ANY.RUN app in IBM QRadar SOAR takes just a few steps:
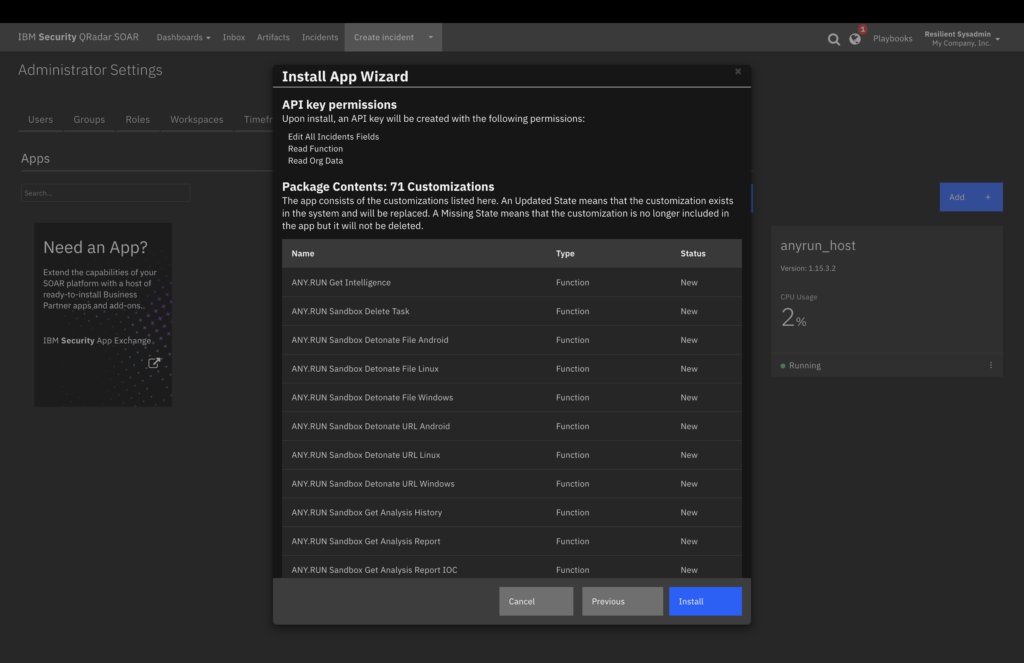
1. Install the App from IBM App Exchange
Simply find the official ANY.RUN app and install it in your SOAR environment; no coding or custom development needed.
2. Connect Using Your ANY.RUN API Key
In the integration settings, add your API key to connect your ANY.RUN account. You can choose to activate:
- TI Lookup only for real-time IOC enrichment
- Sandbox only for dynamic file and URL analysis
- Both modules together for full access to enrichment and behavioral analysis
Both modules are available to paid ANY.RUN users and can be used independently or in combination, depending on your license.
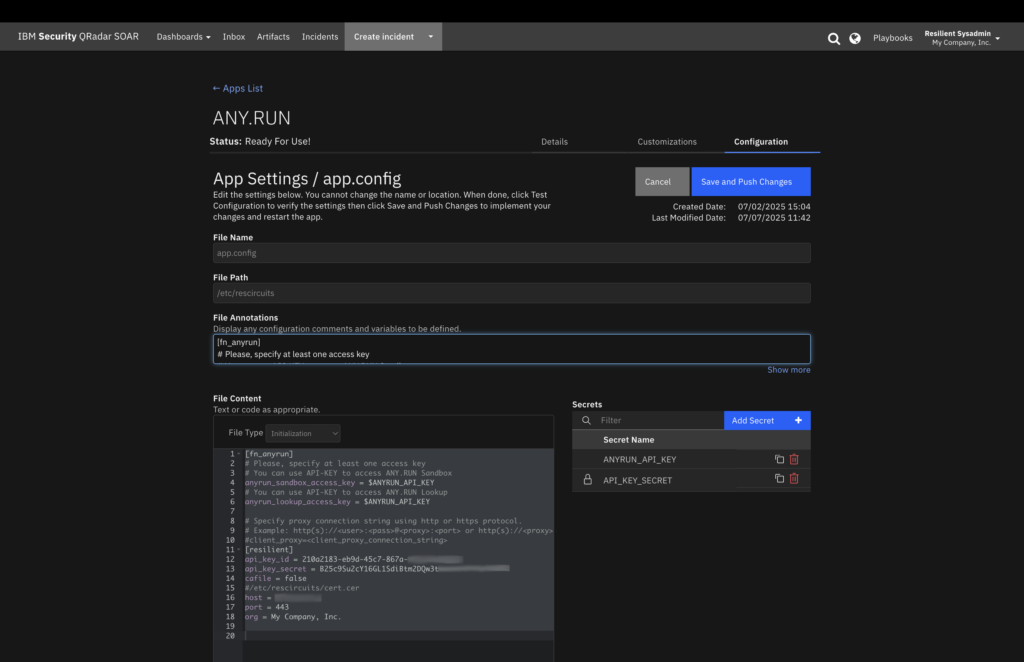
3. Use or Customize the Playbooks
Use the pre-configured playbooks that come with the integration or customize them to fit your SOC workflows.
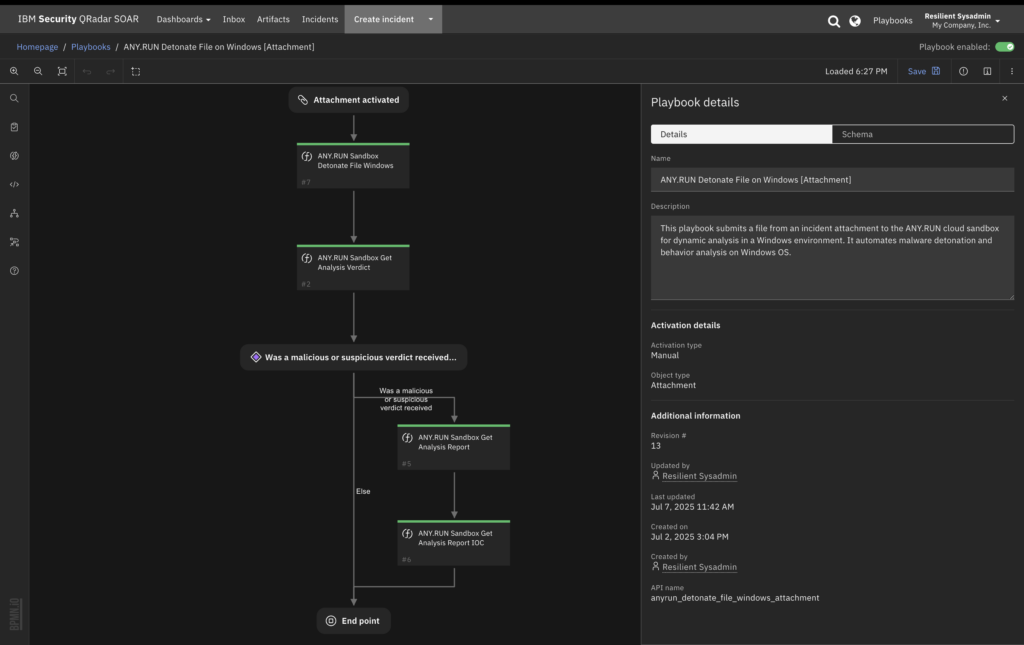
4. Automate Enrichment and Analysis in Your Incidents
Once configured, you can begin automating threat investigation steps directly within IBM QRadar SOAR:
- Pull data from TI Lookup by sending artifacts (IPs, hashes, domains, etc.) and retrieving JSON-based enrichment with real-time threat intelligence
- Send files and URLs to Sandbox and receive key indicators, behavioral tags, verdicts, and detailed reports (PDF/JSON), all injected back into the incident
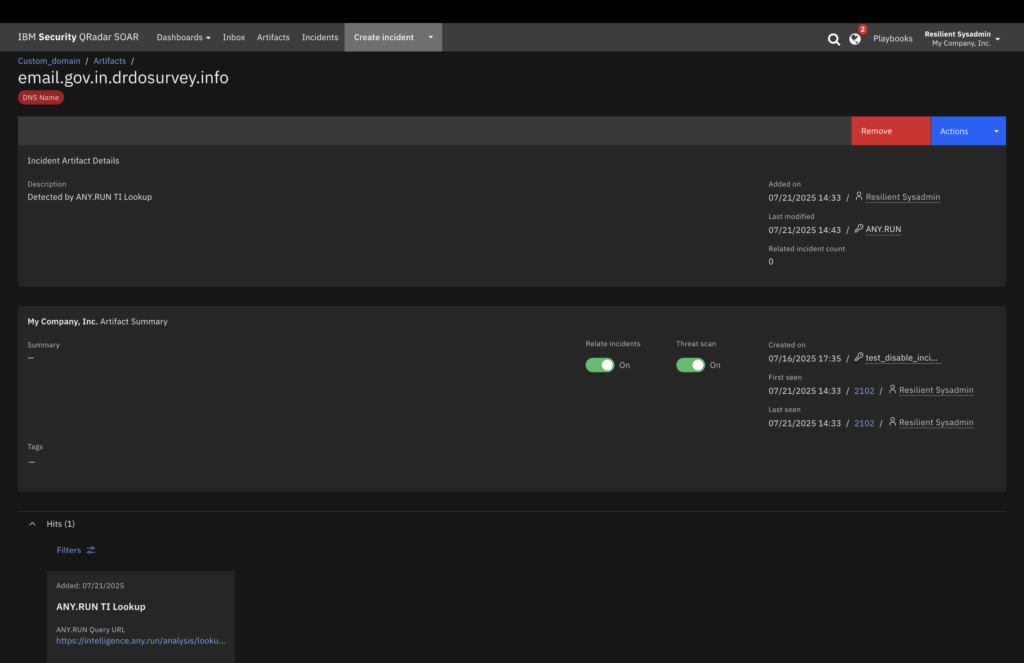
This lets your analysts make faster decisions, automate triage, and reduce response time without manual switching between tools.
Integrate ANY.RUN with Other Solutions and Vendors
ANY.RUN supports multiple integrations with popular security products. Check out the list to see how you can streamline workflows in your SOC.
About ANY.RUN
ANY.RUN is trusted by over 500,000 cybersecurity professionals and 15,000+ organizations in finance, healthcare, manufacturing, and beyond. Our services help security teams investigate threats faster and with greater confidence.
Accelerate response times with our Interactive Sandbox: Analyze suspicious files in real time, uncover malicious behavior, and support quick decision-making.
Enhance detection capabilities using Threat Intelligence Lookup and TI Feeds: Give your team the context they need to stay ahead of evolving cyber threats.
Reach out to us for a 14-day trial of ANY.RUN’s service now →
The post Turn Alert Noise into Threat Insights without Leaving QRadar SOAR with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

