Free. Powerful. Actionable. Make Smarter Security Decisions with Live Attack Data
Streamlining your SOC workflows with fresh intelligence is now easier than ever: ANY.RUN introduces free access to Threat Intelligence Lookup.
With it, you can enrich your threat investigations with data on attacks targeting 15,000 companies all over the world. All you need to do to strengthen your defense against them is to register, browse our unique database, and gain actionable insights.
Threat Intelligence in ANY.RUN continues to evolve — not only by adding more features, but by making the right ones easier to use. We’ve simplified access to ANY.RUN Threat Intelligence with a free version of TI Lookup.
You now can explore Public Samples, TTPs, Suricata rules, and malware trends inside our Threat Intelligence product in a cleaner, faster way.
It’s about putting existing value in the right place, for the right audience. For analysts and teams starting with ANY.RUN in a Threat Intelligence context, this is a much better entry point.
It’s a step to help you do less — so you can focus on more.
Aleksey Lapshin, ANY.RUN CEO
TI Lookup—Essential Solution for SOC Teams
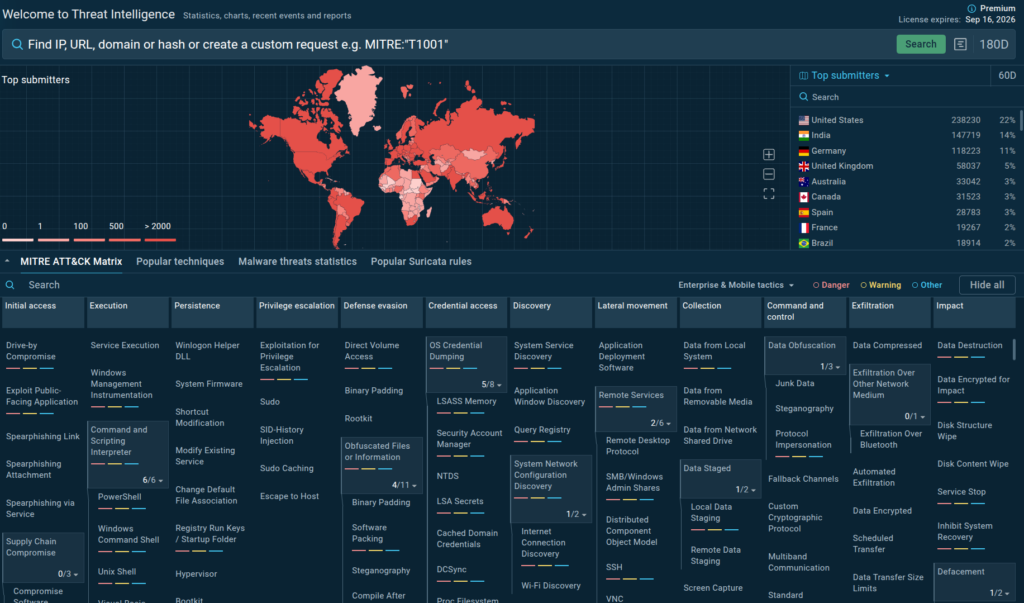
TI Lookup is ANY.RUN’s key solution for working with threat intelligence. It simplifies and accelerates different stages of malware investigations, from proactive monitoring to gaining insights for incident response. As a result, you get to ensure a better defense against cyber threats for your company.
In practice, this means that TI Lookup provides you with Indicators of Compromise (IOCs), Attack (IOAs), and Behavior (IOBs). It not only links each indicator to an attack or sample but also showcases its behavior inside the sandbox.
The source of indicators is unique: all data comes from millions of public malware analysis sessions done in ANY.RUN’s Interactive Sandbox. TI Lookup allows you to tap into it to gain invaluable insights into real threats targeting 15,000 companies in finance, manufacturing, transportation, government, and other industries right now.
Unlike other solutions relying on public reports or databases published days or weeks after an incident, TI Lookup provides fresh, actionable data available to you hours or even minutes after the attack happened.
And now you get to access the benefit of our service at no cost. See how even its free version with limited functionality can become a game-changer for your security operations.
Results You Can Achieve Using Free Plan

Essential features of TI Lookup are available at no cost. With the free plan, you can view up to 20 recent sandbox sessions per query, conduct unlimited searches using basic search fields (file hashes, URLs, domains, IPs, MITRE ATT&CK techniques, Suricata IDs, etc.) and an operator for combination search (AND).
With free access to TI Lookup, you can gain a powerful solution to common challenges of SOC teams:
- Enrich threat investigations: Get extensive threat context by linking existing artifacts to actual attacks.
- Reduce response time (MTTR): Explore identified threats’ behavior, purpose, and targets through sandbox analyses for fast, informed security decisions.
- Strengthen proactive defense: Collect data on emerging threats to act before they cause harm.
- Grow expertise of your team: Let your SOC specialists explore real-world attacks and see examples of TTPs in actual malware via the interactive MITRE ATT&CK matrix.
- Develop SIEM, IDS/IPS, or EDR rules: Intelligence collected via TI Lookup can be used to improve proactive defense of your business.
All you need to do to get started is to sign up for ANY.RUN or sign in your account.
TI Lookup’s Free Plan: Real-World Use Cases
See how TI Lookup can give you a hand in solving common SOC challenges in a couple of examples. They involve threats active today and demonstrate how ANY.RUN’s solution will speed up and simplify their breakdown.
Fast Triage and Data-Fueled Response
If you receive an alert related to a suspicious domain, you can check it in TI Lookup to get the verdict in seconds. E.g., enter this simple query:
domainName:”smtp.godforeu.com”
And almost instantly you’ll see the verdict—it is indeed malicious.
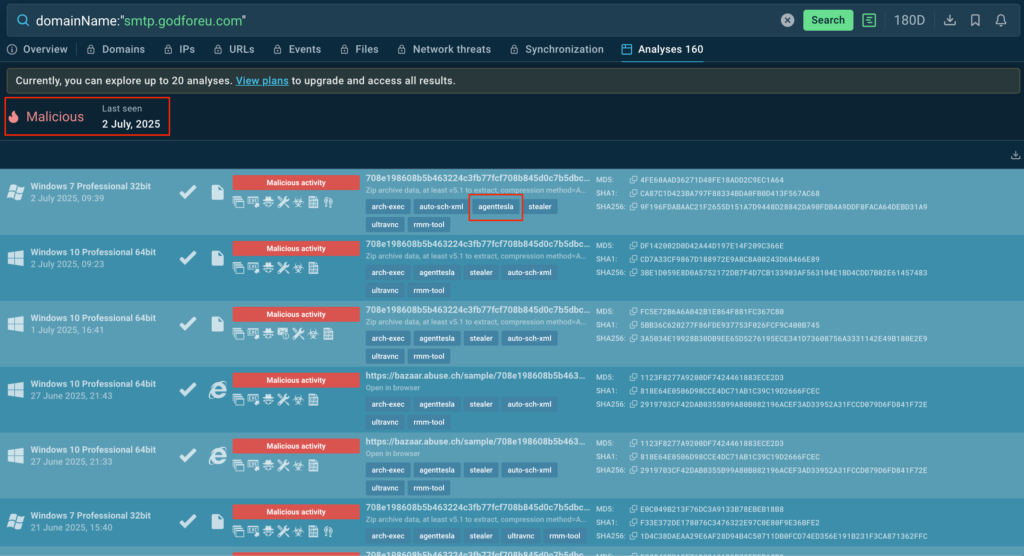
This info is enough to escalate the incident, but that’s not all TI Lookup is capable of. Take a look at the tags in analysis sessions that involve the domain in question. From them, you can also determine the name of the threat it’s related to—Agent Tesla.
And by clicking any of the sessions, you’ll be transferred to ANY.RUN sandbox for further investigation. You can observe how malware behaves and collect extra IOCs and TTPs. For example, follow this link to see the analysis of a threat sample from TI Lookup search results:
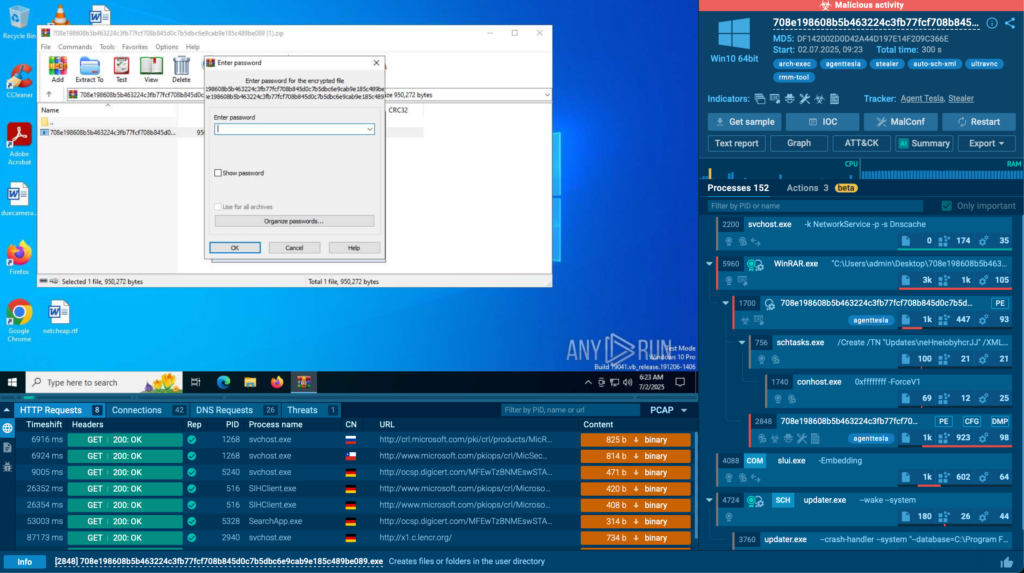
That’s how you get to enrich your threat research to follow through with an informed incident response.
Threat Hunting for Proactive Defense
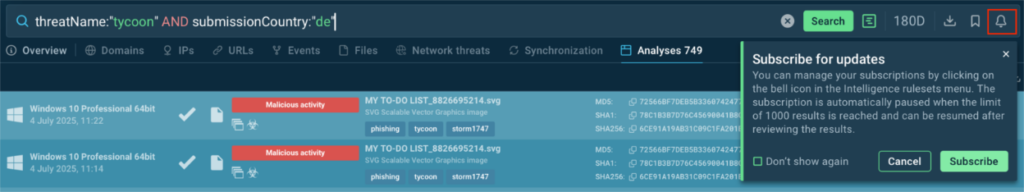
Another way to apply TI Lookup’s free functions is to use it for threat hunting. For instance, if you would like to research the phishing kit Tycoon2FA’s activity in a particular region, you can create a compound query like this:
threatName:”tycoon” AND submissionCountry:”de”
It combines the name of the threat we’re interested in with the id of a country—in this case, de – Germany. By entering this query, you’ll see the most recent analysis samples involving Tycoon2FA that were uploaded by users from there:
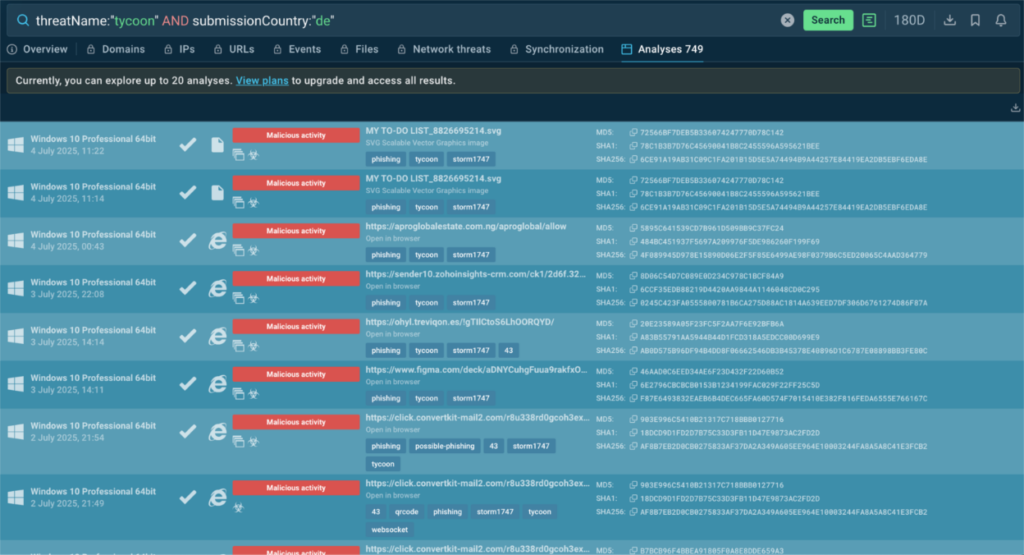
Now you get to collect IOCs and use this data to proactively defend your infrastructure.
With a Premium plan, you would also be able to subscribe to your query. This feature is called Search Updates and allows you to stay on the lookout for emerging threats that fit your previous search:
Maximize Benefits and Unlock Premium Features
The free version of TI Lookup grants you the functionality needed to achieve tangible results. To gain full access to its features and expand your ability to conduct investigations, opt for the Premium plan. With it, you can access three times more data, automate alert triage, and receive notifications on attacks as soon as they emerge.
| Free | Premium | |
|---|---|---|
| Requests | Unlimited number of basic requests | Advanced requests (100/500/5K/25K) |
| Search operators | AND | AND, OR, NOT |
| Search parameters | 11 | 44 |
| Links to analysis sessions | Up to 20 most recent | All available |
| Interface | Limited (only analyses) | Full (all threat data + analyses) |
| Integration | – | API and SDK (Python package) |
| YARA Search | – | + |
| Private search | – | + |
| TI Reports | – | + |
| Search Updates | – | + |
It’s designed for SOC teams from businesses and organizations, as it allows for private searches that can’t be seen by other users and other exclusive features:
- Speed up alert triage: Quickly correlate alerts against a vast database of the latest IOCs, IOBs, and IOAs.
- Automate workflow for real-time monitoring: Integrate TI Lookup with your security tools (e.g., SIEM, TIP, or SOAR systems).
- Threat hunt with precision: Create and browse custom YARA rules in ANY.RUN’s database to identify malware patterns with YARA Search.
- Investigate in detail: Fine-tune your search with over 40 search parameters, as well as extra operators.
- Stay proactive: Set up automated alerts for specific IOCs or threat patterns for continuous updates.
- Follow malware trends: With TI Reports by our expert analysts, you can raise awareness about the latest attacks targeting different industries.
Let’s see how TI Lookup’s interface looks like with all features unlocked. For that, we’ll use a query to look for the Lumma family threats. Additionally, we’ll browse for all domains related to it:
threatName:”lumma” AND domainName:””
Here are the results TI Lookup returns:
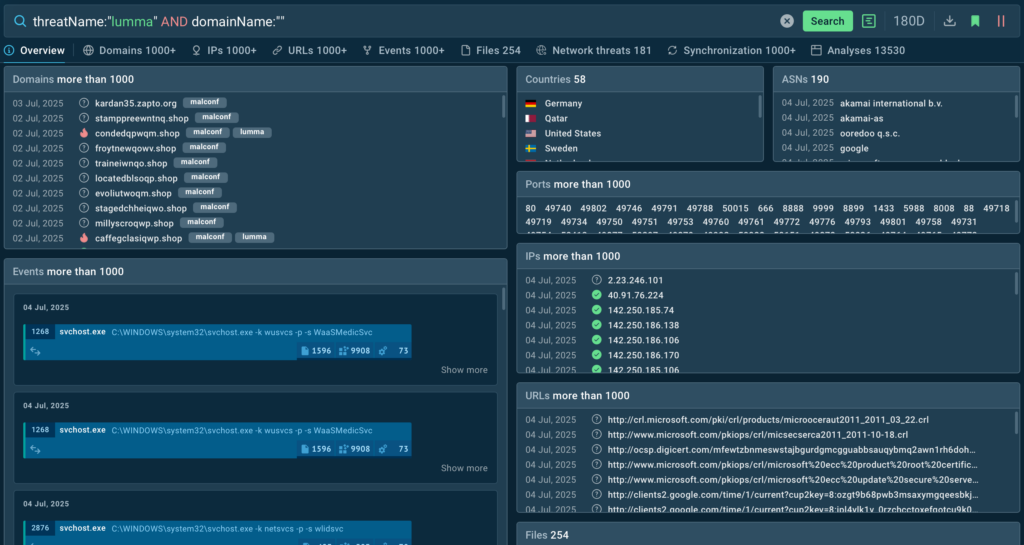
As you can see, the Premium plan grants you more data: it includes domains, countries, ports, IPs, and more. In this case, it’s especially important that we got to collect many malicious domains.
Conclusion
TI Lookup is a must-have tool if you want to maintain a simpler and faster way to conduct threat investigations. SOC teams can benefit from it immensely thanks to relevant, real-world data it provides. Accelerate your decision-making and take proactive action against malware with TI Lookup—available with Free and Premium plans.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Request trial of ANY.RUN’s services to see how they can boost your SOC workflows
The post Free. Powerful. Actionable. Make Smarter Security Decisions with Live Attack Data appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


