How extensions from Open VSX were used to steal cryptocurrency
Our researchers have uncovered several malicious fake extensions targeting Solidity developers in the Open VSX marketplace. At least one company has fallen victim to the attackers distributing these extensions — losing approximately US$500 000 in crypto assets.
Threats associated with malware distribution in open-source repositories have been known about for a long time. Despite this, users of AI-powered code editors like Cursor AI and Windsurf are forced to use the open-source extension marketplace Open VSX, as they have no other source for the extensions these platforms need.
However, extensions on Open VSX do not undergo the same rigorous checks as those on the Visual Studio Marketplace. This loophole allows attackers to distribute malicious software disguised as legitimate solutions. In this post, we dive into the details of the malicious Open VSX extensions investigated by our experts, and explain how to prevent similar incidents within your organization.
Risks for users of Open VSX extensions
In June 2025, a blockchain developer who had just lost approximately US$500 000 in crypto assets to attackers reached out to our experts and requested an incident investigation. While examining a disk image from the compromised system, our researchers noticed a suspicious component of an extension named Solidity Language for the Cursor AI development environment. The component was executing a PowerShell script — a sure sign of malicious activity.
The extension was installed from the Open VSX marketplace, where it had tens of thousands of downloads (presumably inflated by bot activity). The description claimed to optimize development of smart contract code written in the Solidity language. However, analysis of the extension revealed it had no useful functionality whatsoever. The developers who installed it mistook the lack of advertised features for a bug, didn’t immediately investigate, and just continued their work.
The browser extension wasn’t actually faulty; it was fake. Once installed, it contacted a command-and-control server to download and run a malicious script. This script then installed ScreenConnect — a remote access application — on the victim’s computer.
The attackers used ScreenConnect to upload additional malicious payloads. In the incident our experts investigated, these tools specifically allowed the attackers to steal passphrases for the developer’s crypto wallets and then syphon off cryptocurrency. A detailed technical description of the attack, along with indicators of compromise, is available in a Securelist blog post.
Manipulating search: how attackers promote malicious extensions
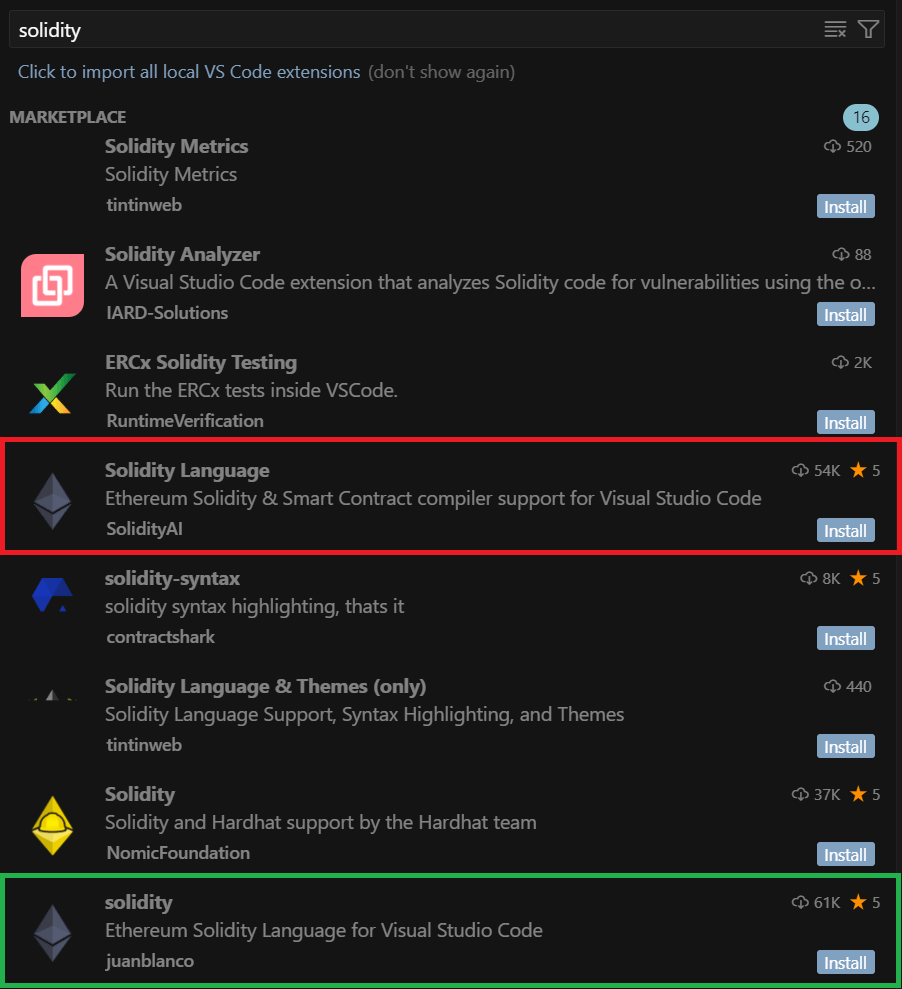
A look into the Open VSX marketplace revealed a concerning trend: a fake extension, deceptively named “Solidity Language”, ranked fourth in search results, while the legitimate extension, simply called solidity, appeared all the way down at eighth. It’s no surprise then that the developer downloaded the counterfeit instead of the genuine article.
This ranking is quite surprising, especially considering that at the time of the search, the legitimate extension had more downloads: 61 000 compared to the fake’s 54 000.
The key lies in Open VSX’s ranking algorithm. It doesn’t solely rely on download counts to determine relevance; it also considers other factors like verification status, ratings, and recency. This is exactly how the attackers managed to outrank the genuine extension in search results: the fake one had a more recent update date.
The fake plugin was removed from the Open VSX marketplace on July 2, 2025, right after the cryptocurrency heist. However, the very next day, we found another malicious package with the same name as the original extension, “solidity”, and the same harmful functionality as Solidity Language.
Additionally, our researchers used an open-source component-monitoring tool to discover yet another malicious package in Open VSX. Several details link this package to the same cybercriminals.
Why do developers have to rely on the Open VSX marketplace?
The Visual Studio Marketplace, Microsoft’s official store, has long been the primary industry source for extensions. It includes automatic scanning for malicious code, sandboxed execution of extensions for behavioral analysis, monitoring for anomalies in extension usage, and a number of other features to help identify harmful extensions. However, its licensing agreement dictates that only solutions for use with Visual Studio products can be published in the Visual Studio Marketplace.
Consequently, users of increasingly popular AI-powered code editors like Cursor AI and Windsurf must install extensions from an alternative store: Open VSX. The problem is that this platform has less stringent extension vetting, which makes it easier to distribute malicious packages compared to Microsoft’s official marketplace.
To be fair, attackers sometimes manage to publish malicious extensions even in the more secure Visual Studio Marketplace. For instance, this spring, experts found three malicious extensions there with an infection scheme very similar to the one described in this post, also targeting Solidity developers.
How to stay safe?
No matter where you’re installing extensions from, we recommend the following:
- Be careful when searching marketplaces.
- Always take note of who the developer of an extension is.
- Check the code and behavior of extensions you install.
- Use an XDR solution to monitor any suspicious activity inside the corporate network.
Kaspersky official blog – Read More