Release Notes: Detonation Actions, Enhanced QR Extraction, and 1,400+ New Detection Rules
We’ve packed June with updates designed to make your day-to-day analysis faster, clearer, and easier than before. Whether you’re just getting started or deep into reverse engineering every day, these improvements are here to save you time and help you catch more threats.
In this update:
- Real-time Detonation Action hints that guide you through the steps needed to keep the analysis forward
- Enhanced QR code extraction, making it easier to detect phishing links hidden in documents, images, or dropped during runtime
- Expanded threat coverage, including 120 new behavior signatures, 12 YARA rules, and 1,320 Suricata rules across Windows, Linux, and Android
Scroll down to see what’s new and how these updates can help your team work faster, spot threats earlier, and get more from your ANY.RUN sessions.
Product Updates
Detonation Actions: Faster, Clearer Malware Analysis with Real-Time Guidance
In June, we focused on helping analysts work faster and with more clarity, especially during high-pressure investigations. That’s why we introduced Detonation Actions: real-time execution hints that keep your analysis moving forward without guesswork.
Now, when a sample requires interaction to detonate, like opening a file or following a link, Detonation Actions will show exactly what needs to be done.
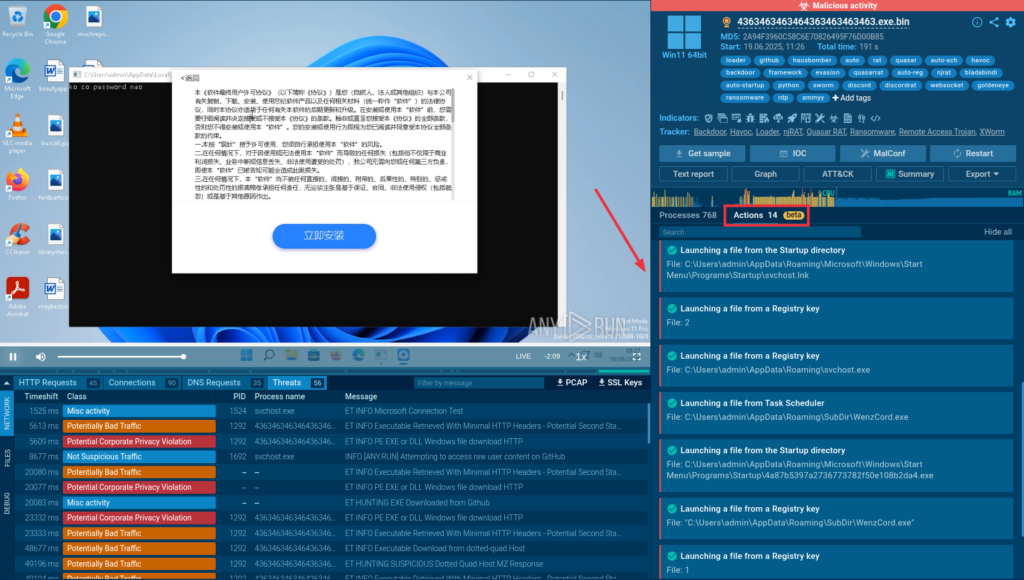
Whether you’re clicking through manually or relying on automation, you’ll see helpful hints to understand how the threat at hand unfolds.
- Manual Mode (Community plan):
You’ll see suggested actions during the session and can approve or reject them individually, helping you uncover hidden behavior faster.
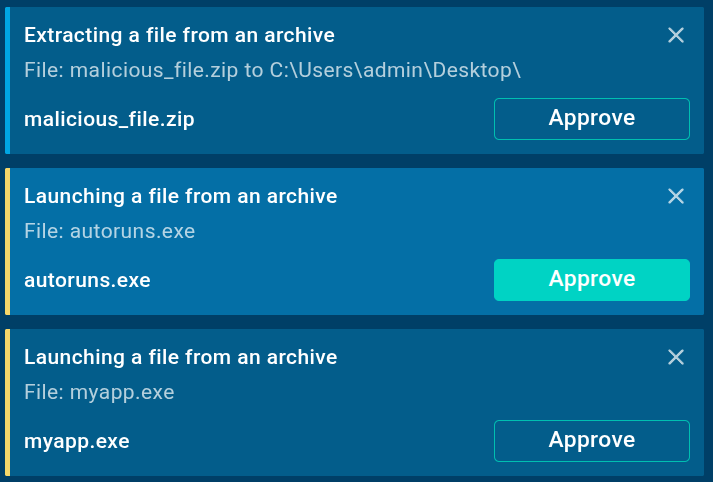
- Automated Interactivity (Paid plans):
Detonation Actions are automatically followed as part of a guided flow. Each step is logged and visible, so your team gets full transparency, even when analysis is fully hands-off.
You’ll find Detonation Actions inside the Actions tab, right next to the process tree. They work across all samples and help analysts of any skill level trigger and observe malware behavior with confidence.
- Speeds up threat analysis by guiding analysts through key detonation steps.
- Improves SOC handover with action-based insights for smoother investigations.
- Accelerates incident response by automating detonation and surfacing behavior fast.
- Simplifies onboarding by helping junior analysts learn through guided workflows.
- Enables smarter decisions with clearer behavioral context during investigations.
- Supports automation by integrating with existing workflows and API-based pipelines.
You can activate Detonation Actions by clicking the new Auto button when launching your VM or toggle Automated Interactivity (ML) manually in Advanced Settings.
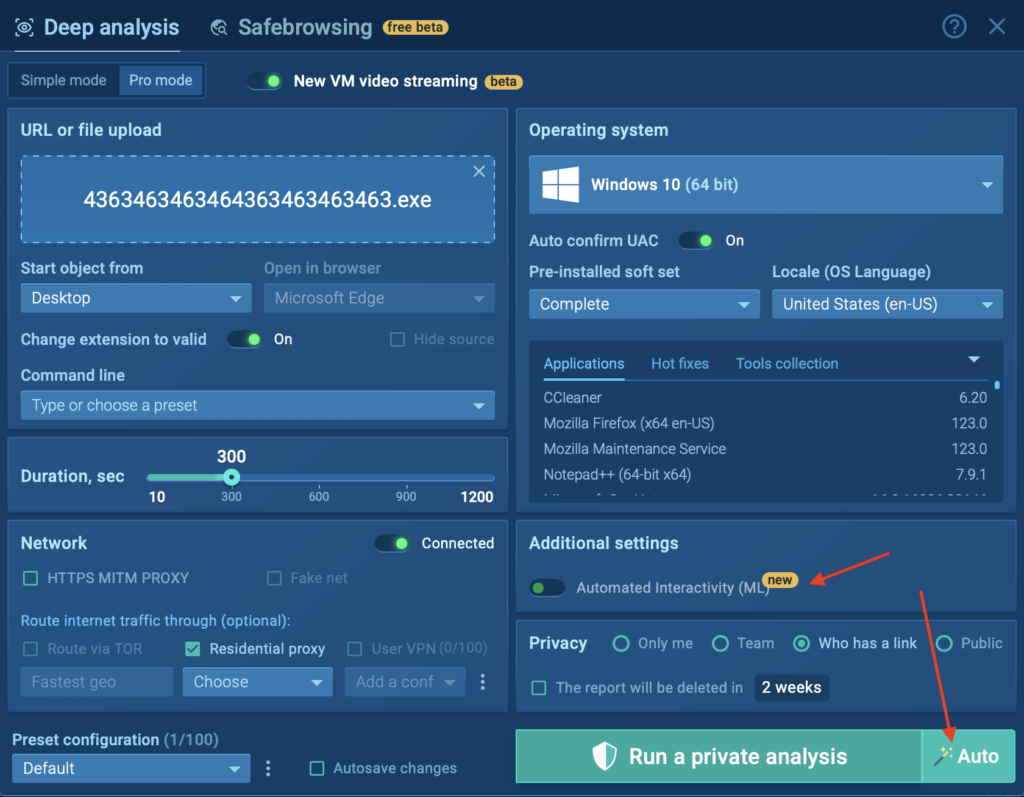
Enhanced QR Code Auto-Extraction for Broader Use Cases
We’ve improved how the sandbox detects and extracts QR codes, making it easier to investigate threats hidden in documents, images, and archives.
Now, QR code detection works more reliably across a wider range of file types and delivery methods. Whether it’s a malicious link embedded in a PDF or a code inside an SVG file, the sandbox will automatically pick it up and display the decoded URL in the QR tab under Static Discovering.
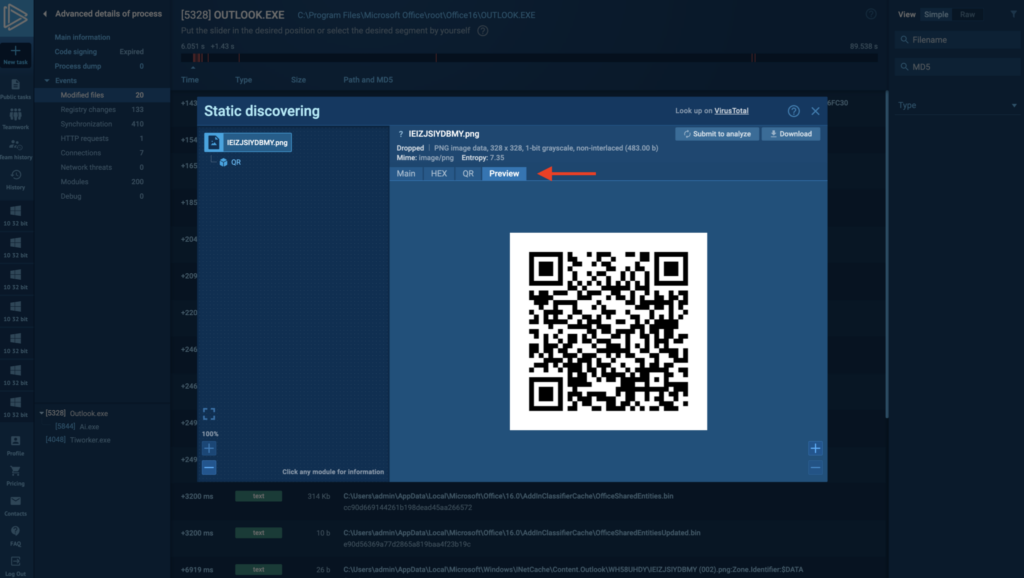
QR-based phishing is still on the rise. This improvement makes it even easier to detect and investigate QR code threats before a user ever scans them.
Threat Coverage Updates
This month, we expanded threat detection across all supported platforms, Windows, Linux, and Android, with major additions to our rule base and signature library.
- 120 new behavior-based detection signatures
- 12 new YARA rules
- 1320 new Suricata rules
These updates improve detection accuracy, shorten triage time, and give analysts better visibility into evasive threats. From commodity malware to nation-state actors, the latest rules reflect real-world samples seen in the wild and analyzed inside ANY.RUN.
New Behavior Signatures
We added 120 behavior signatures targeting stealers, ransomware, RATs, loaders, and evasive techniques, many of which were observed in active campaigns.
Some highlights:
- PurpleFox – A rootkit-enabled malware that abuses SMB vulnerabilities for lateral movement
- Bert Loader – Dropper with obfuscated payload delivery tactics
- Bondy Loader – Frequently used to stage ransomware and remote control tools
- XData Ransomware – Resurfaces with updated infection logic and encryption flow
- LD_PRELOAD Hijacking – A Linux-based persistence technique now tracked as standalone behavior
- Winlocker – Known for fake law enforcement messages and aggressive blocking behavior
- Ransomblox – Displays error pop-ups while communicating with its C2 during encryption
- Conti-style variant – Exhibits callbacks to infrastructure overlapping with known Conti and DragonForce setups
- Dacic ransomware – Recently observed in campaigns with custom servers and DNS-based C2
- Cyberkiller – Attempts stealthy exfiltration before launching destructive behavior
Platform-Specific Threats
New behavior detections were also added for threats targeting specific operating systems:
Windows:
- Kiwistealer – Stealer that extracts browser data, passwords, and system information
- KimJongRAT – Remote access trojan that abuses trusted binaries and uses a GUI-based control panel
- Byakugan – Leverages signed binaries to inject into processes and maintain stealth
Linux:
- DSLogdRAT – Lightweight Linux backdoor with keylogging, reverse shell access, and simple evasion logic
Android:
- Antidot – Spyware disguised as a system utility app, capable of remote monitoring
- Zanubis – Banking trojan that abuses accessibility services to intercept credentials
- Godfather – Targets financial apps and intercepts MFA codes to bypass login security
YARA Rule Updates
We released 12 new and updated YARA rules this month to support faster static detection and classification of threats across all platforms. These rules help flag malicious files before execution and enhance attribution in multi-stage attacks.
Some of the key additions include:
- Katz – Credential-dumping tool used in post-exploitation phases
- Ryuk – Ransomware version attributed to the hacker group WIZARD SPIDER
- WirelessKeyView – Tool that extracts stored Wi-Fi credentials from Windows systems
- Mail PassView – Password-recovery tool that reveals the passwords and other account details for email clients
- SmartSniff – Network sniffer commonly abused in data exfiltration scenarios
- LClipper – Clipper malware that hijacks clipboard data to redirect crypto transactions
- Phantom – Stealer with anti-analysis techniques, commonly used in phishing kits
Suricata Rule Updates
To improve detection of phishing threats at the network layer, we added 1,320 new Suricata rules in June. These rules help security teams identify malicious domains, redirection chains, and phishing infrastructure early in the attack flow.
Here are some of the highlights:
- Lndeed domain typosquatting pattern (sid:85000784): Identifies indeed.com – themed phishing attempts
- Document-themed phishing (sid:85000452): Detects phishing domains utilizing social engineering methods (“See / review / share” + “document”)
- EvilProxy domain chain (sid:85000494): Tracks EvilProxy phishing kit activity by sequence of queried domains
New Detection Techniques
We added behavior-based detection for a tactic used by malware to bypass standard execution monitoring:
- Command execution via FileFix technique – This method involves abusing renamed or repurposed legitimate executables (e.g., “FileFix.exe”) to stealthily launch payloads. It’s commonly used in commodity loaders to blend in with normal activity.
This new detection helps analysts flag unusual execution chains earlier in the process tree and trace hidden payload delivery paths more efficiently.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with TI Lookup, YARA Search, and Feeds, we equip businesses to speed up investigations, reduce security risks, and improve team’s efficiency.
Integrate ANY.RUN’s Threat Intelligence suite in your organization →
The post Release Notes: Detonation Actions, Enhanced QR Extraction, and 1,400+ New Detection Rules appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

