How to survive digitalization | Kaspersky official blog
Digitalization of business – especially in the small and medium-sized segment – allows for quick upscaling, better customer service, and entry into new markets. On the downside, digitalization amplifies the damage caused by a cyberattack, and complicates the recovery process. Given that company resources are always limited, which attacks should be deflected first?
To answer this question, we studied the INTERPOL Africa Cyberthreat Assessment Report 2025. The document is useful because it collates police cybercrime statistics and data from information security companies – including Kaspersky – allowing us to compare the number and types of attacks with the actual damage they caused. This data can be used to build a company’s information security strategy.
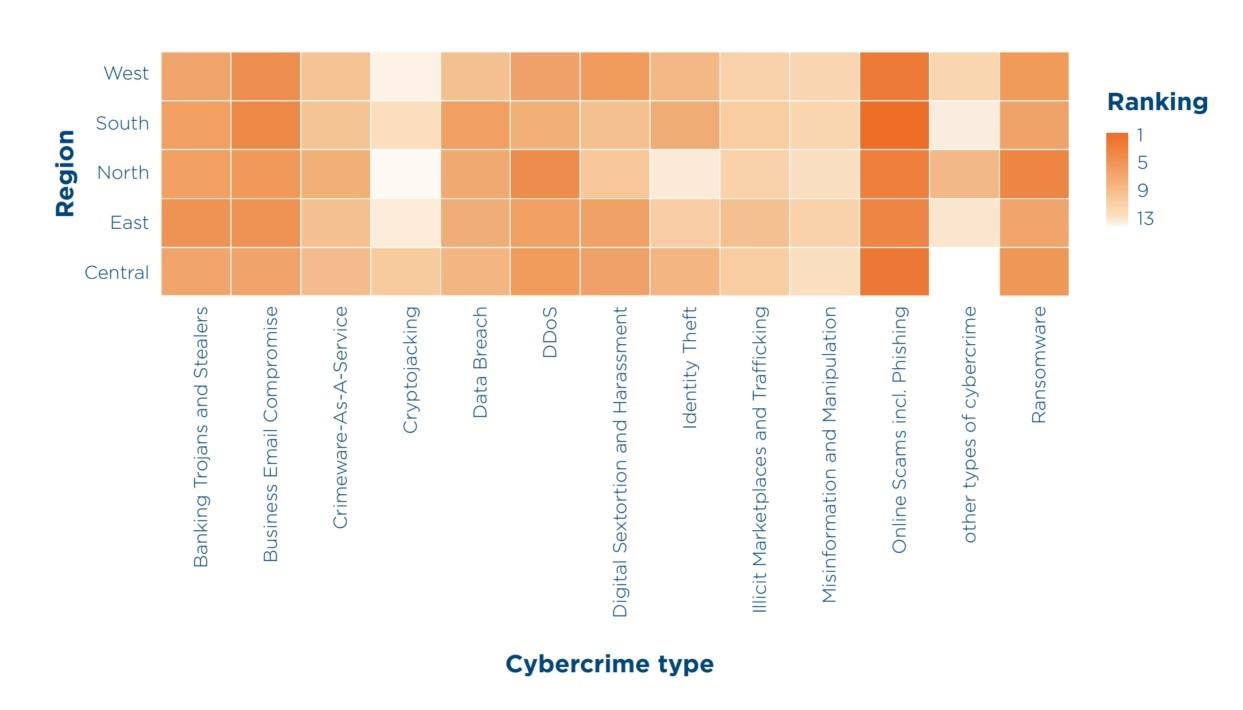
Average ranking of cybercrime types by reported financial impact across African subregions, based on INTERPOL member country data. Source
Targeted online fraud
Fraudulent operations were the clear leader in terms of damage caused across the continent. They’re gaining momentum in line with the rising popularity of mobile banking, digital commerce, and social media. In addition to mass phishing aimed at personal and payment data theft, targeted attacks are growing at a rapid rate. Scammers are grooming potential victims in messenger apps for months, building trust and guiding them into a money extortion scheme – for example, a fake cryptocurrency investment. Such schemes often exploit romantic relationships and are therefore called romance scams, but there are other variations. In Nigeria and Ivory Coast, for example, scammers were arrested for attacking small media platforms and advertising agencies. Posing as advertisers, they stole almost 1.5 million U.S. dollars from victims.
The fact that 93% of Africans use plain old WhatsApp rather than corporate communication tools for work significantly boosts the success rate of attacks on employees and company owners.
Ransomware incidents
Press headlines may give the impression that ransomware operators mainly target large organizations, but the statistics in the report debunk this theory – showing that both the number of attacks and the actual financial damage caused are significant across all business segments. What’s more, there’s a direct link between the level of digitalization and the number of attacks. So, if a company observes an overall increase in “digitized” business activity in its market segment, the threat level is sure to rise accordingly. In Africa, “affiliates” of the largest and most dangerous ransomware-as-a-service platforms – such as LockBit and Hunters International – are responsible for major incidents on a national scale.
Among the main ransomware incidents in Africa – hardly known about outside the continent – we highlight the following: the theft of $7 million from Nigerian fintech company Flutterwave; attacks on Cameroonian electricity supplier ENEO; a large-scale ransomware attack to exfiltrate data from Telecom Namibia; and the targeting of South Africa’s National Health Laboratory Service (NHLS), which led to canceled operations and the loss of millions of lab test results.
Banking Trojans and infostealers
Although the direct losses from banking Trojans and infostealers fell outside the top-three in terms of damage, it’s the “successes” of this criminal industry that have a direct impact on the number and severity of other attacks – primarily ransomware and business email compromise (BEC). After stealing what credentials they can from thousands of users with infostealers, attackers filter and group them by various criteria, then sell curated sets of accounts on the illicit market. This allows other criminals to buy passwords to infiltrate organizations of interest to them.
Business email compromise
For small and medium businesses mainly using public services like Gmail or Office 365, infection with an infostealer gives attackers full access to corporate correspondence and business operations. The attackers can then exploit this to trick customers and counterparties into paying for goods and services to a fraudulent account. BEC attacks have a firm hold at the top of the damage charts, and small businesses can fall victim to them in two ways. First, cybercriminals can extract money from larger clients or partners by impersonating the compromised small business. Second, it’s easier with a small business to persuade the owner or accountant to transfer money than it is with a large organization.
There are several large criminal syndicates based in Africa that are responsible for international BEC operations causing multi-billion-dollar damage. Their targets also include African organizations — primarily those in the financial and international trade sectors.
How to protect business from cyberthreats
To effectively counter digital threats, law enforcement agencies need to share data with commercial information security companies that harness telemetry to identify threat distribution hotspots. Recent successes of such partnerships include operations Serengeti (1000 arrests, 134 000 malicious online resources disabled), Red Card (300 arrests), and Secure (32 arrests, 20 000 malicious resources disabled). These operations, conducted under the auspices of INTERPOL, used cyberthreat intelligence received from partners – including Kaspersky.
But businesses can’t leave cybersecurity solely to the police; they need to implement simple but effective security measures of their own:
- Enable phishing-resistant multi-factor authentication (MFA) for all online accounts: Google, Microsoft, WhatsApp, etc.
- Install reliable anti-malware protection on all corporate and personal devices. For corporate devices, centralized security management is recommended – as implemented, for example, in Kaspersky Endpoint Detection and Response.
- Hold regular cybersecurity training – for example, using our Kaspersky Automated Security Awareness platform. This will reduce the risk of your company falling victim to BEC and phishing. All employees, including management, should participate in training regularly.
- Back up all company data on a regular basis and in such a way that the backups can’t be destroyed during an attack. This means backing up data either to media that are physically disconnected from the network, or to cloud storage where a policy prohibits data deletion.
Kaspersky official blog – Read More

