How to Spot Registry Abuse by Malware: Examples in ANY.RUN Sandbox
When malware infiltrates a system, it doesn’t always make noise. In fact, some of the most dangerous threats operate quietly embedding themselves deep within the system and ensuring they come back even after a reboot. One of the most common ways they achieve this is by abusing the Windows Registry.
In this article, we’ll walk through how registry abuse works, the signs to watch out for, and how security analysts can catch it using interactive sandboxes, such as ANY.RUN.
What Is Registry Abuse in Malware?
The Windows Registry is an important part of the operating system. It stores configuration settings that determine how Windows behaves, how software runs, and even how users interact with the system. From startup routines to driver settings and user preferences, the registry touches almost every part of the OS.
As it’s central, the registry is also a target for malware authors. By modifying registry keys and values, malware can silently manipulate system behavior to:
- Stay persistent by adding itself to autorun keys, it ensures execution every time the system boots.
- Hide from users disabling Task Manager, hiding file extensions, or suppressing warnings to avoid detection.
- Weaken security turning off Windows Defender or blocking updates to bypass protection.
- Control user behavior redirecting browser traffic, setting fake proxies, or hijacking default apps.
The Fastest Way to Spot Registry Abuse inside ANY.RUN Sandbox
Traditional security tools often miss subtle but critical signs of registry abuse, especially when malware hides behind scripts or legitimate-looking processes.
By running suspicious files or links inside ANY.RUN’s interactive sandbox, analysts can observe real-time registry changes as they happen, without waiting for static scans to catch up.
Why It’s So Effective:
- Instant visibility into registry modifications, autorun key changes, and process behaviors
- Behavior-based detection, not just signatures; perfect for catching new or obfuscated threats
- Clear labeling and process tree that highlight when a script or binary tampers with the registry
- Integrated threat intelligence tags (e.g., FormBook) to identify malware families quickly
- Interactive control, so you can simulate real user actions that trigger registry abuse (like opening a file or clicking a button)
Real-World Examples of Registry Abuse in Malware
Now, let’s look at how malware abuses the registry in practice and how ANY.RUN makes it easy to detect.
1. Persistence via Autorun Key Modification
This sample shows how the malware (BootstrapperNew.exe) abuses the registry to ensure it launches automatically every time the system boots; a classic persistence mechanism.
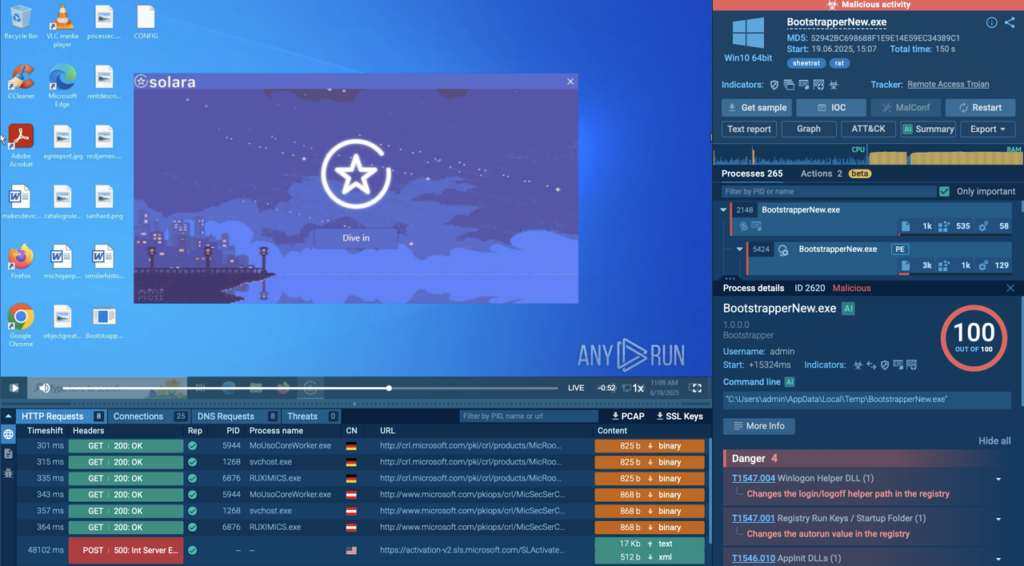
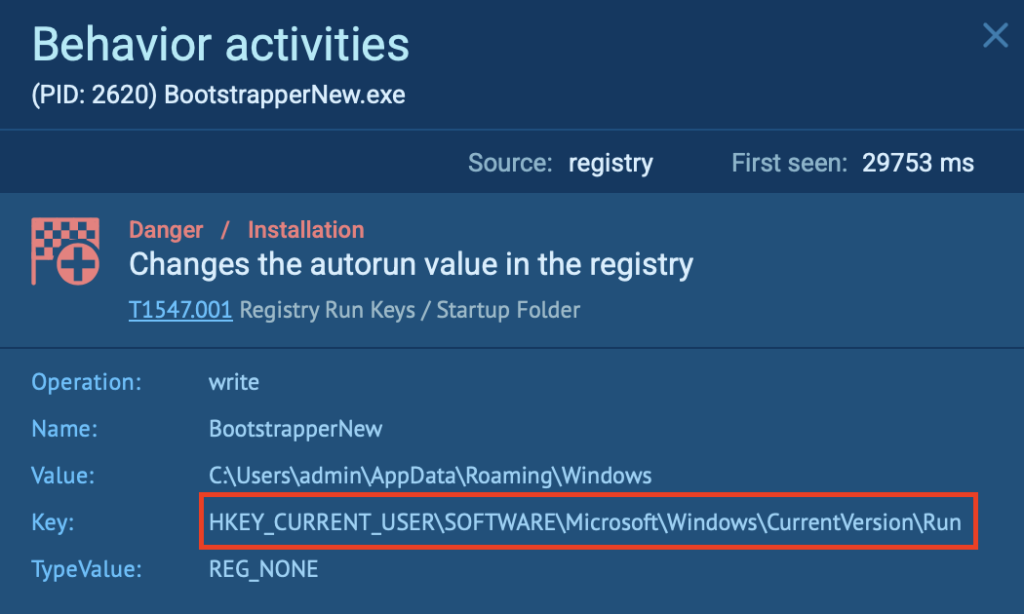
As shown in the analysis, the malware modifies the following registry key:
HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
It adds a new value:
- Name: BootstrapperNew
- Value: C:UsersadminAppDataRoamingWindowsBootstrapperNew.exe
- Operation: Write
- Type: REG_NONE
You can check all these details by checking the “BootstrapperNew.exe” process from the right part of the screen.
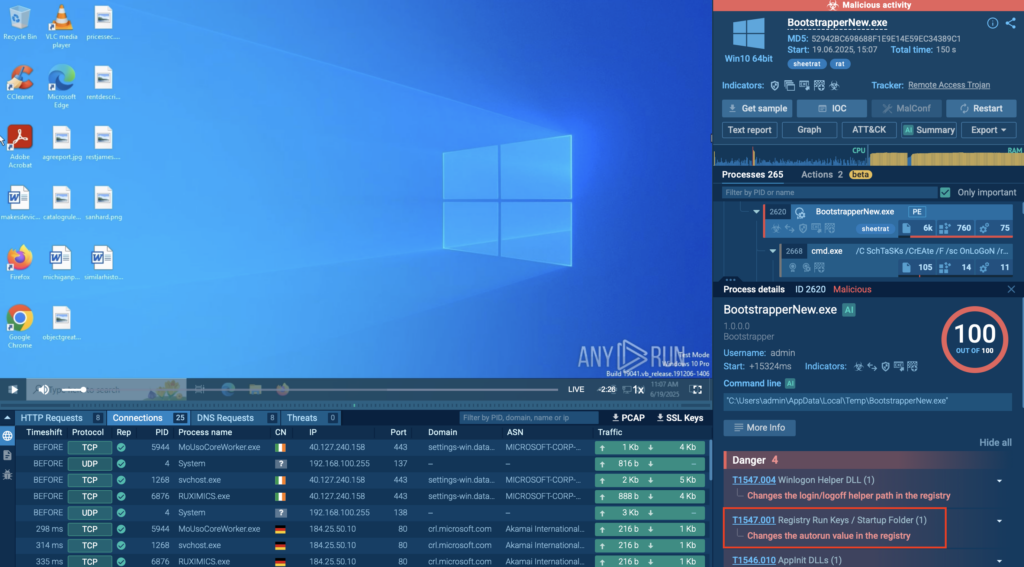
Click on the tactic to get all the details:
This modification triggers Windows to execute the malicious file at every user login, giving the attacker a reliable foothold on the system.
ANY.RUN also flags this behavior with the MITRE ATT&CK sub-technique T1547.001 (Registry Run Keys / Startup Folder), clearly highlighting the persistence mechanism used. The visual process tree further confirms the execution flow, registry operation, and background network activity.
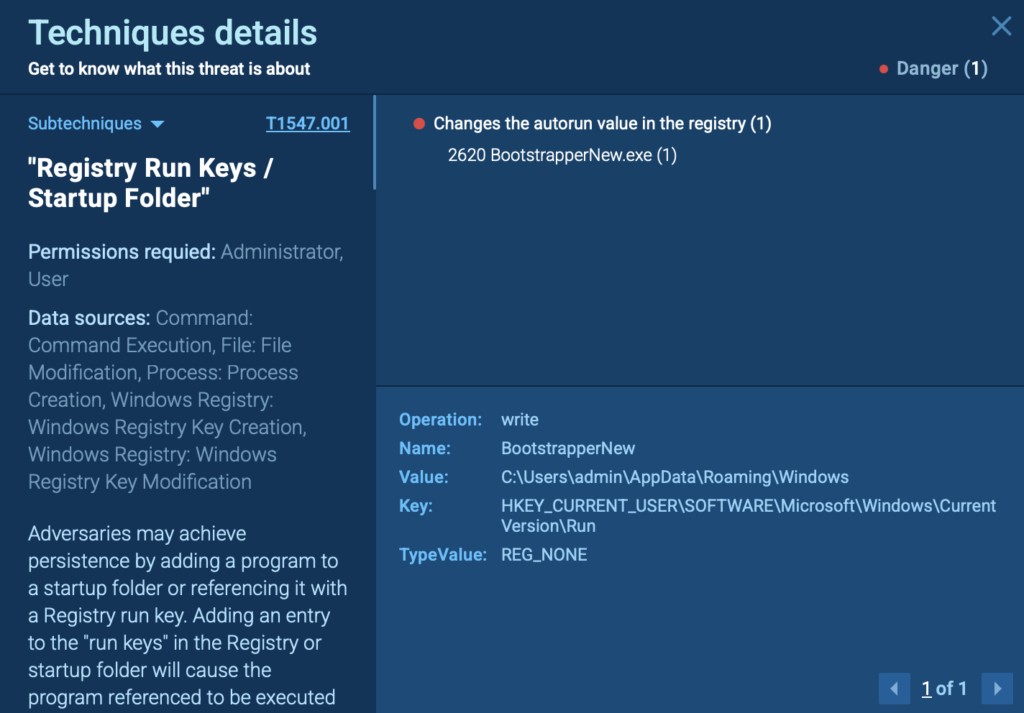
With static detection tools, this behavior might go unnoticed. But in ANY.RUN’s sandbox, the threat is immediately identified, tagged, and visually traceable in real time, from registry edit to scheduled task creation.
2. FormBook Stealer Using Registry for Stealth
In this example, the malware identified as FormBook manipulates the Windows Registry to aid in stealth and persistence.
Right after execution, FormBook writes a new registry entry under:
- Key: HKEY_CURRENT_USERSOFTWARESoftina
- Name: MMM-Vkusnaa
- Value: 19.06.2025
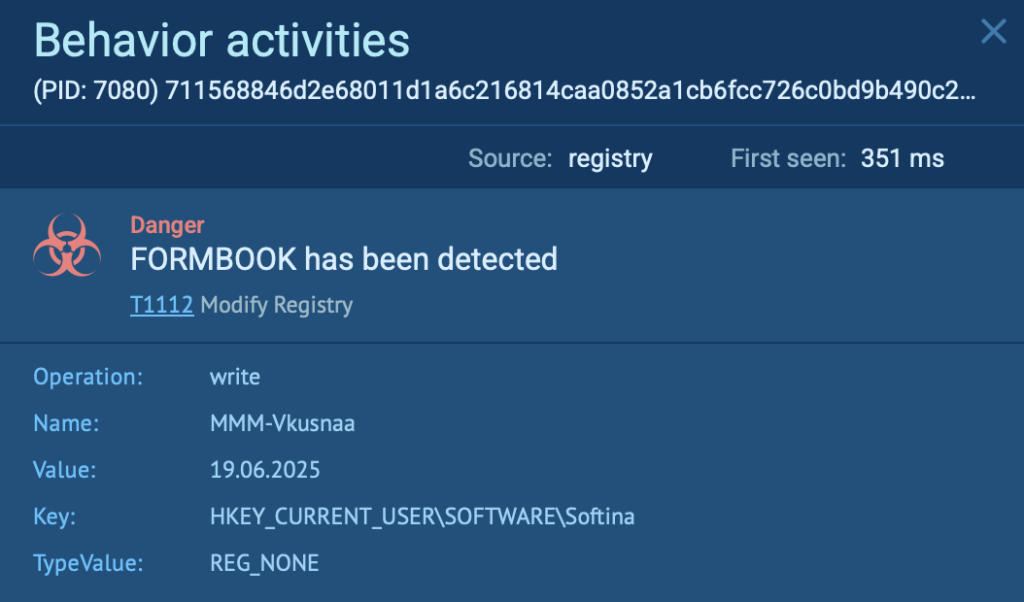
Custom registry values like this aren’t random. They’re typically placed in obscure subkeys (SOFTWARESoftina in this case) to avoid detection and logging by standard monitoring tools, but in ANY.RUN’s sandbox, it’s instantly visible and tied to MITRE technique T1112: Modify Registry.
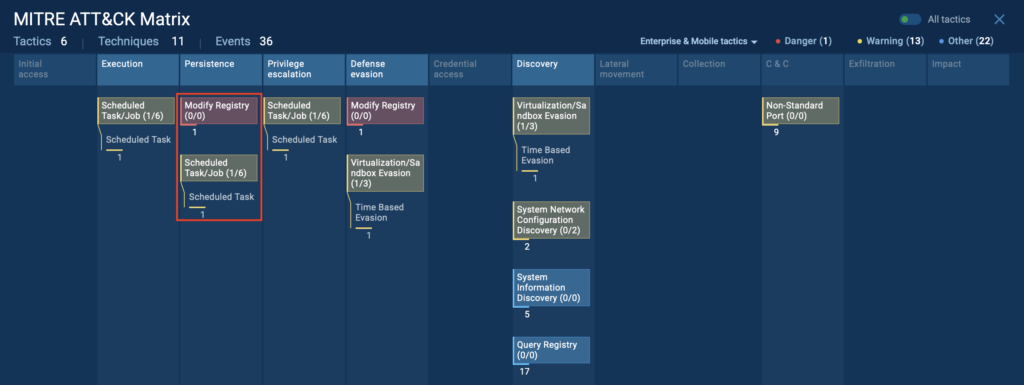
3. System Profiling Through Registry Access
Some malware doesn’t act immediately. Instead, it quietly profiles the environment to decide how (or whether) to execute. That’s exactly what we see in this sample, where the malware queries the registry to gather detailed system information.
One of the first actions taken is a read operation targeting:
- Key: HKEY_LOCAL_MACHINEHARDWAREDESCRIPTIONSystemCentralProcessor
- Name: ProcessorNameString
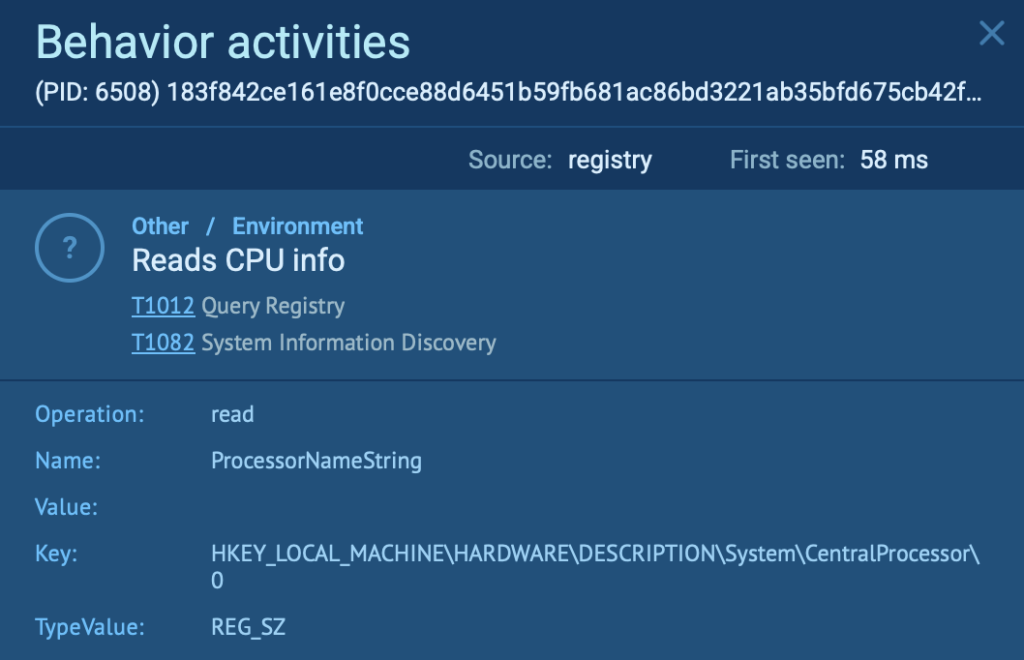
This query fetches CPU information, such as model name and vendor. While this might seem benign, it plays a crucial role in anti-analysis and evasion tactics.
Why malware reads CPU info:
- Environment validation: Malware may use CPU data to check if it’s running on a real machine or a virtual one (e.g., commonly used by sandboxes or researchers).
- Tailored payloads: Some threats adapt their behavior based on system specs, avoiding execution if they detect low-end CPUs or virtual environments.
- Fingerprinting the target: CPU info is often collected alongside other system data to create a unique victim profile.
But this is just the beginning. According to the MITRE ATT&CK technique T1012: Query Registry, this sample retrieves a wide range of values:
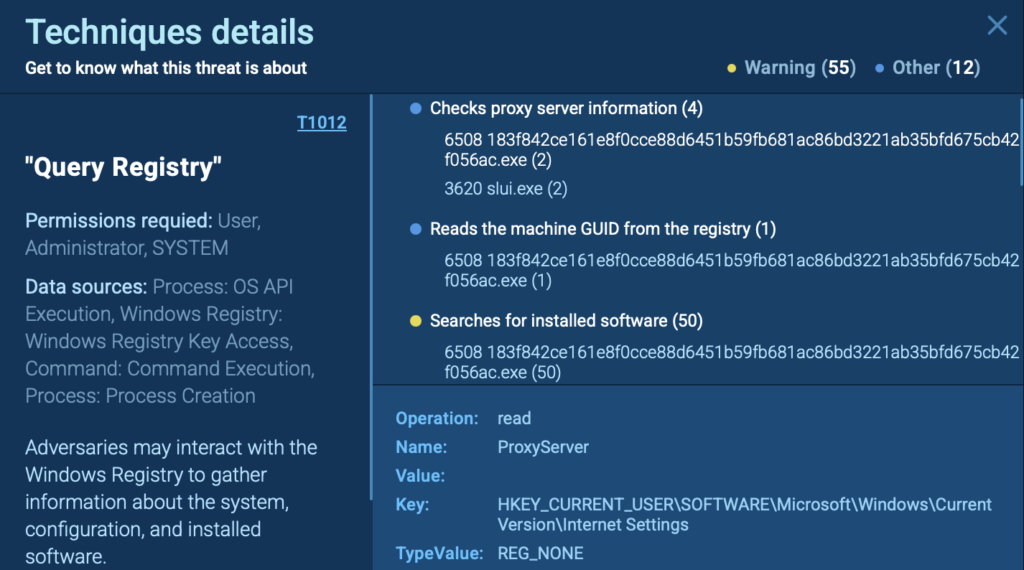
- Proxy configuration: Determines whether the system uses a proxy and may hijack it
- Machine GUID: A unique identifier, useful for tracking infected hosts
- Installed software (50 reads): Likely for reconnaissance or to check for security tools
- Internet Explorer security settings: May suggest preparation for exploit delivery via browser
- System language & locale: Used to avoid infecting machines in certain countries
- Computer name & Windows product ID: Adds more detail to the fingerprint
- Software policy settings: Used to detect restrictions or protections enabled by admins
This shows how malware can treat the registry as a rich source of system intelligence. Each value queried helps build a clearer picture of the host environment, guiding the next malicious action.
4. Suspicious Registry Modification via REG.EXE
This sample involves a process (_virlock.exe) that uses reg.exe, a legitimate Windows utility, to modify the registry. This kind of activity isn’t inherently malicious, but in the context of malware execution, it often signals stealthy post-infection behavior.
Shortly after execution, the malware launches a command: reg add HKCUSoftwareMicrosoftWindowsCurrentVersionExplorerAdvanced /v HideFileExt /t REG_DWORD /d 1
This command modifies the registry to hide file extensions for known file types, a well-documented trick used by malware to disguise malicious executables (e.g., invoice.pdf.exe appears as invoice.pdf).
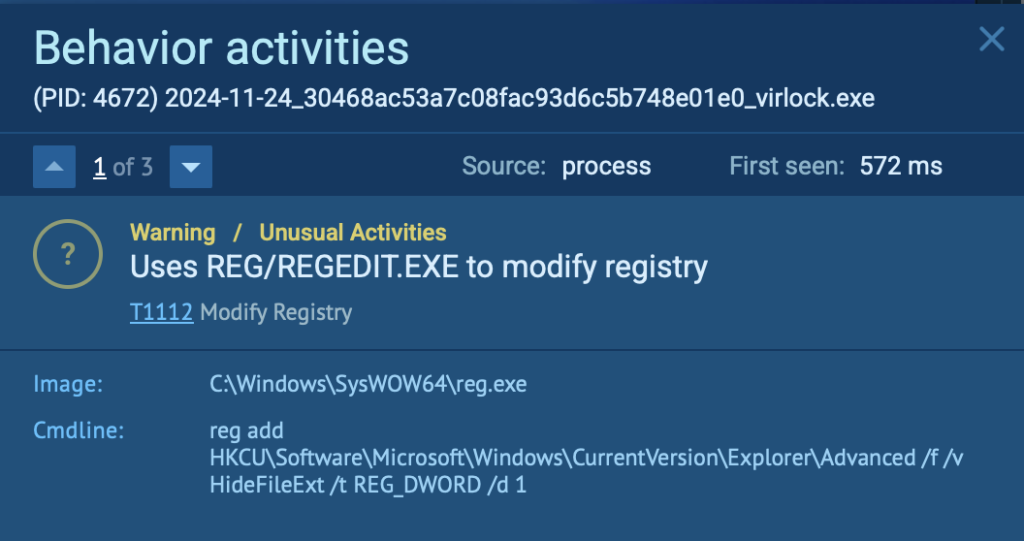
Why it’s suspicious:
- This change is frequently used in social engineering attacks, where victims are tricked into running malware that looks like a harmless document.
- The behavior is executed via reg.exe, which is a living-off-the-land binary (LOLBIN); a legitimate tool abused by attackers to avoid detection.
- ANY.RUN flags this activity under T1112: Modify Registry, and classifies it as a Warning / Unusual Activity.
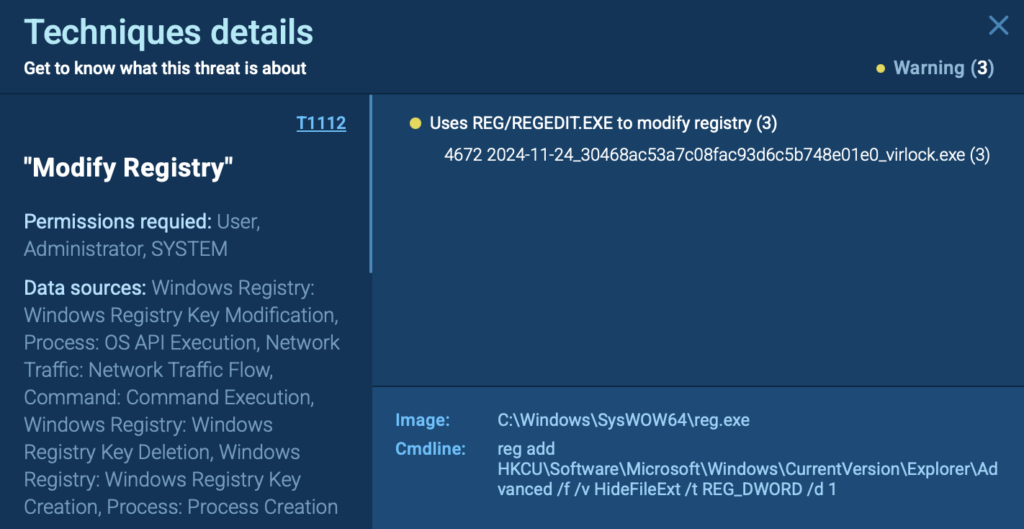
This case is a good reminder that not all registry abuse is about persistence. Some changes are purely meant to deceive the user, reduce visibility, or mask malicious actions.
With ANY.RUN’s behavioral analysis, this tactic becomes immediately visible, showing which registry key was changed, how, when, and by what process, including full command-line context.
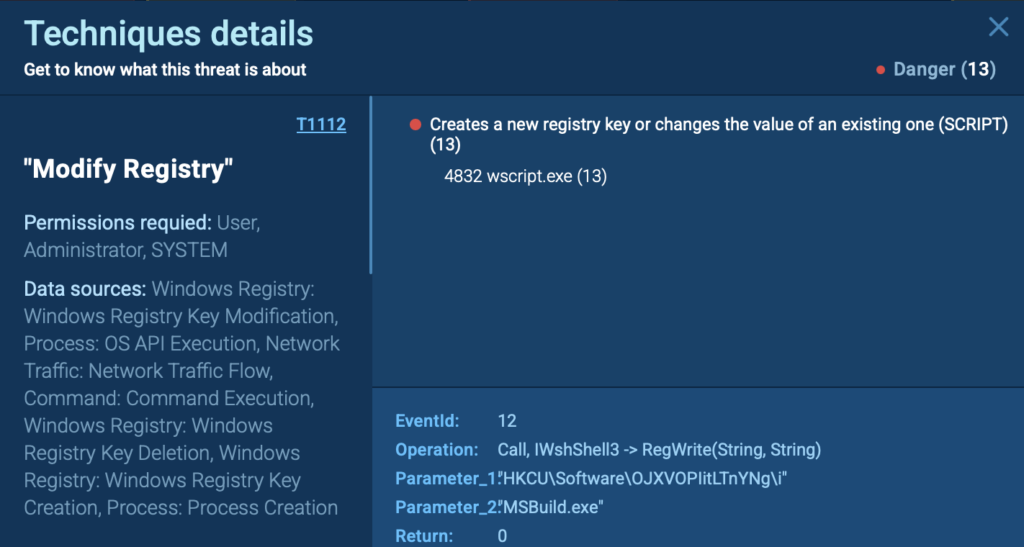
5. Script-Based Registry Modification
In this sample, we see a Windows Script Host process (wscript.exe) modifying the registry, not through a typical executable, but via script-based interaction. This kind of behavior is harder to detect, especially if you’re relying on traditional static analysis.
Thanks to ANY.RUN’s Script Tracer, we can observe the exact call and parameters used:
- Key: HKCUSoftwareOJXVOPIitLTnYNgdonnsegment2
- Value: (Hex-encoded string payload)
- Process: wscript.exe
- Operation: RegWrite via WshShell3
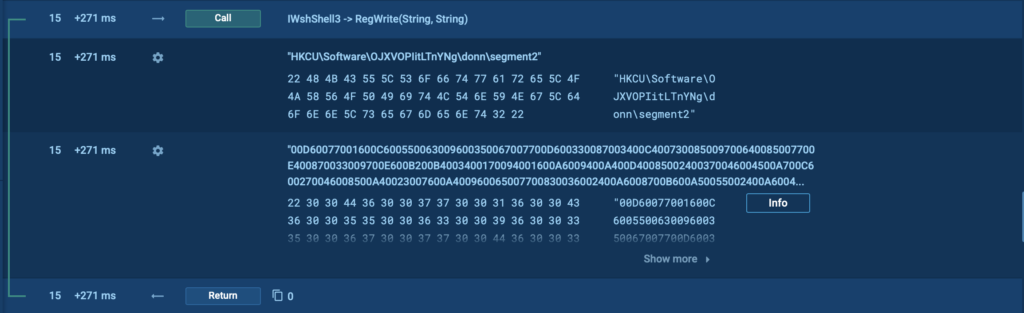
This script creates a new key and writes what appears to be an obfuscated or encoded payload into the registry; a technique commonly used to:
- Store secondary payloads or shellcode
- Evade file-based detection mechanisms
- Delay execution until a later stage (fileless persistence)
The registry key name (OJXVOPIitLTnYNg) is randomly generated and meaningless, a common trait of obfuscated malware activity.
We can see how the script writes a long block of hexadecimal content, which may later be decoded and executed, without ever dropping a traditional file on disk.
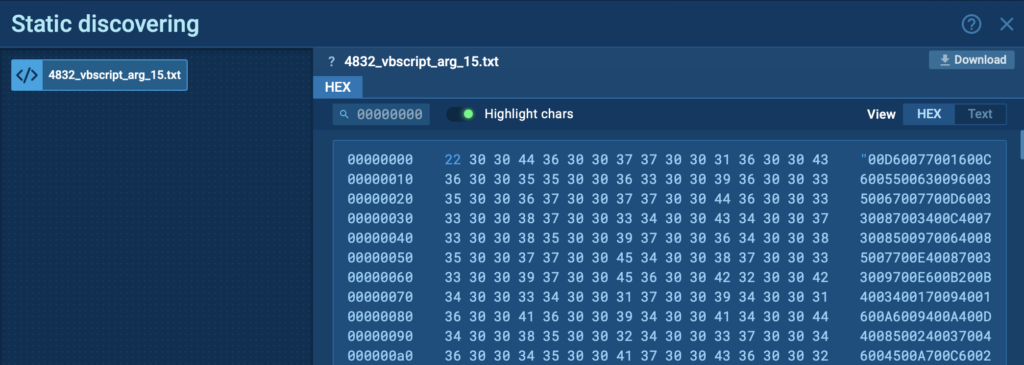
These modifications fall under MITRE ATT&CK technique T1112: Modify Registry, and ANY.RUN labels this behavior as Dangerous (13 instances).
Without behavioral analysis, this kind of registry manipulation would be nearly invisible, but with Script Tracer, security analysts can follow every step the script takes, down to the exact method calls and values.
Spotting Registry Abuse is Easy with ANY.RUN
Registry modifications are a common and powerful tactic used by malware to stay hidden, persist through reboots, and weaken your defenses. But with the right tools, these threats become much easier to spot, investigate, and respond to.
ANY.RUN’s interactive sandbox doesn’t just show you what malware is doing, it visually breaks down every behavior, from registry edits to process injection and data exfiltration, in real time.
- Faster threat detection
Catch malicious registry changes and system tampering before damage is done; no need to wait for traditional tools to catch up.
- Improved incident response
With clear visual evidence and behavior chains, your team can respond to threats with greater accuracy and speed.
- Reduced investigation time
Analysts can immediately see what’s been changed, what triggered the behavior, and which malware family is involved.
- Stronger defenses across the board
By identifying how threats abuse the registry, you can harden your endpoints, update rules, and block similar attacks in the future.
- Better collaboration and reporting
Export detailed analysis reports, share IOCs with teams, and make smarter security decisions faster.
See how ANY.RUN’s interactive sandbox reveals the behavior behind modern threats in real time, and with full context.
Access all capabilities of ANY.RUN’s Interactive Sandbox with a 14-day trial
The post How to Spot Registry Abuse by Malware: Examples in ANY.RUN Sandbox appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

