Simplify Threat Analysis and Boost Detection Rate with Detonation Actions
Threat analysis is a complex task that demands full attention, especially during active incidents, when every second counts. ANY.RUN’s Interactive Sandbox is designed to ease that pressure with an intuitive interface and fast threat detection.
Our new feature, Detonation Actions, takes this further by highlighting detonation steps during analysis. When a specific action is needed to trigger the sample, like launching a file or clicking a link, it appears as a suggestion, so you know exactly what to do.
Detonation Actions work in both manual mode and with Automated Interactivity. Whether you’re investigating manually or running automated sessions, this guided mode reduces the time it takes to respond to threats and helps you catch the full scope of malicious behavior with minimal effort.
What Are Detonation Actions?
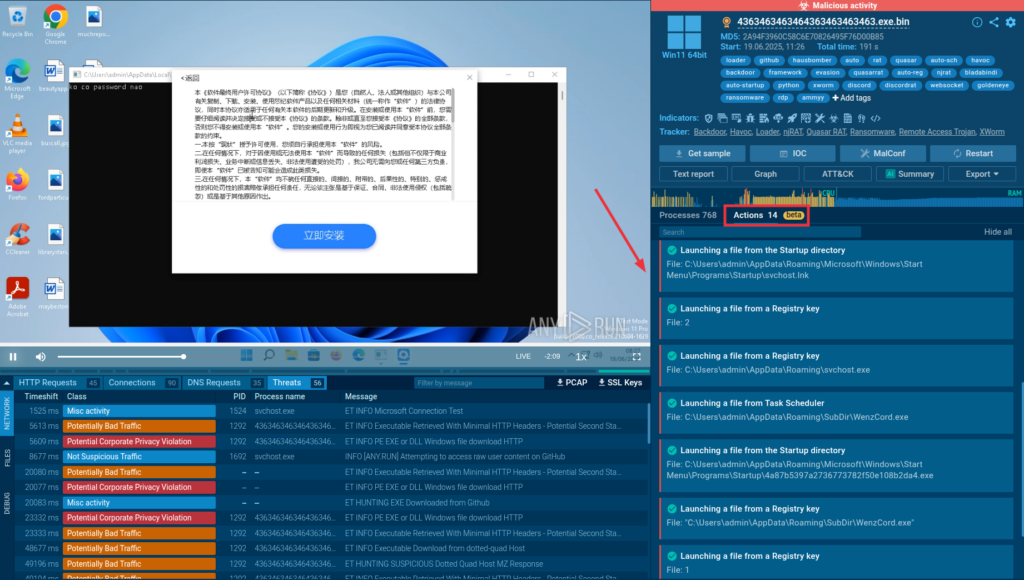
Detonation Actions are built-in hints in ANY.RUN’s Interactive Sandbox that guide users step-by-step through the threat analysis process. They are available in every sandbox session, for all users, and help make both manual and automated investigations clearer and more efficient.
Here’s how it works depending on your plan:
- Free Plan: You can see the suggested actions and follow them manually during your session.
- Paid Plans: Track and manage each action performed by Automated Interactivity, including via API, for a fully automated, hands-free analysis with full transparency and control.
One Button to Start the Guided Mode
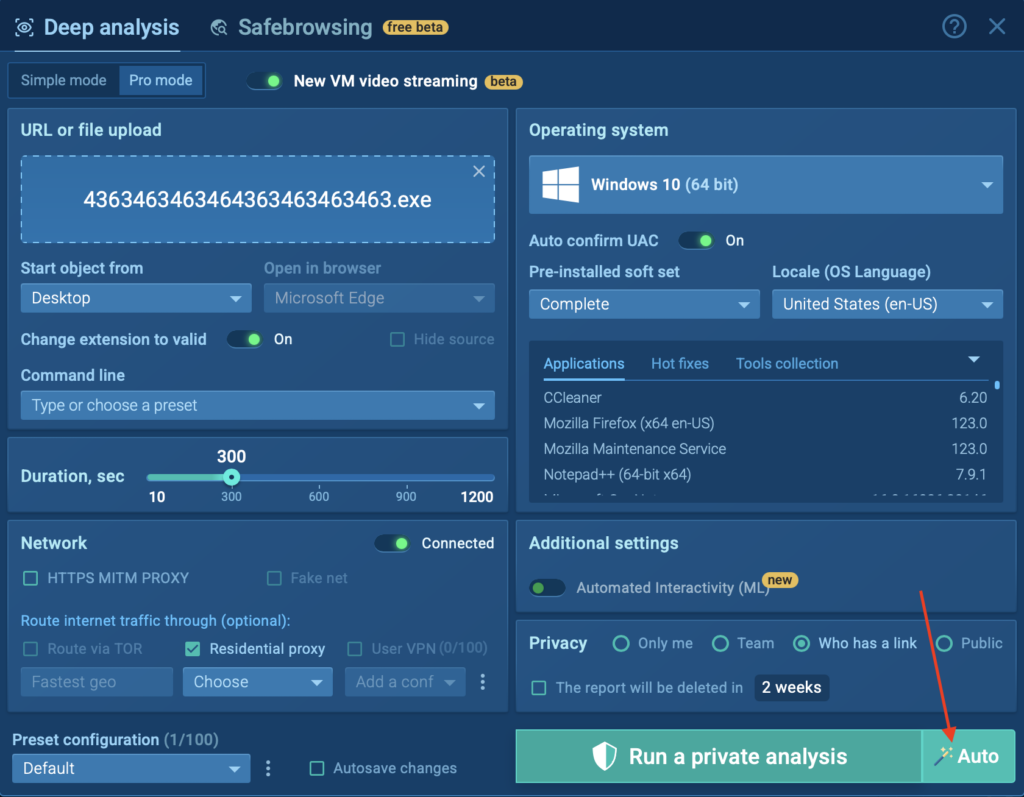
Before launching your analysis, you’ll now see a new “Auto” button during the VM setup phase. Clicking this button starts your session with Automated Interactivity enabled, which in turn activates the guided mode, powered by Detonation Actions.
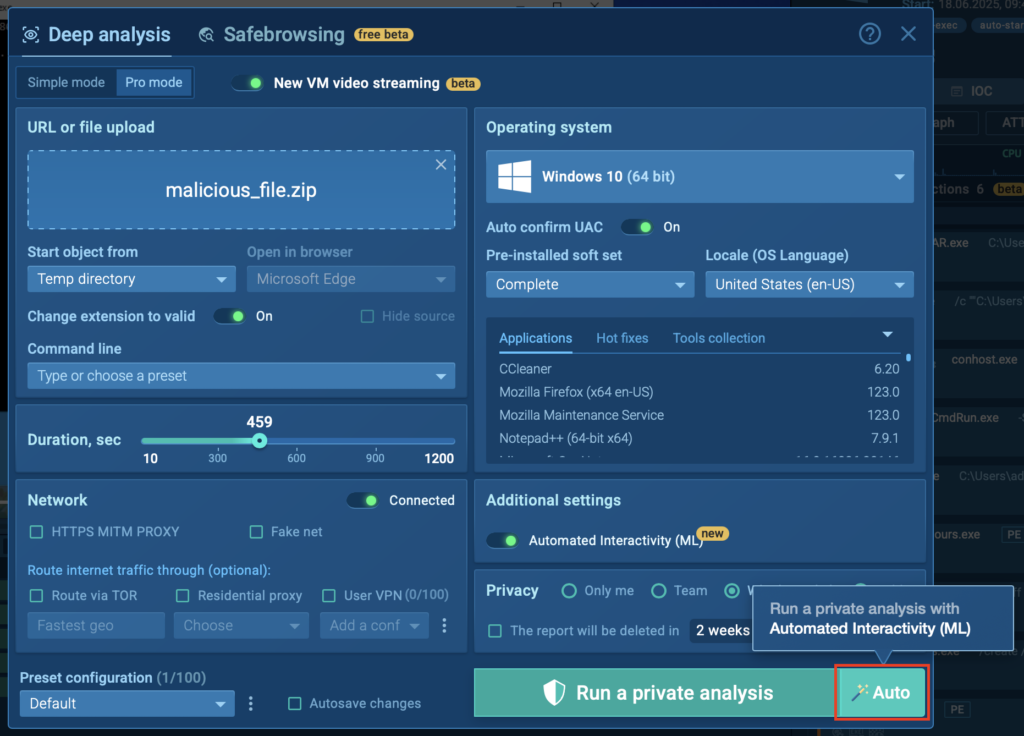
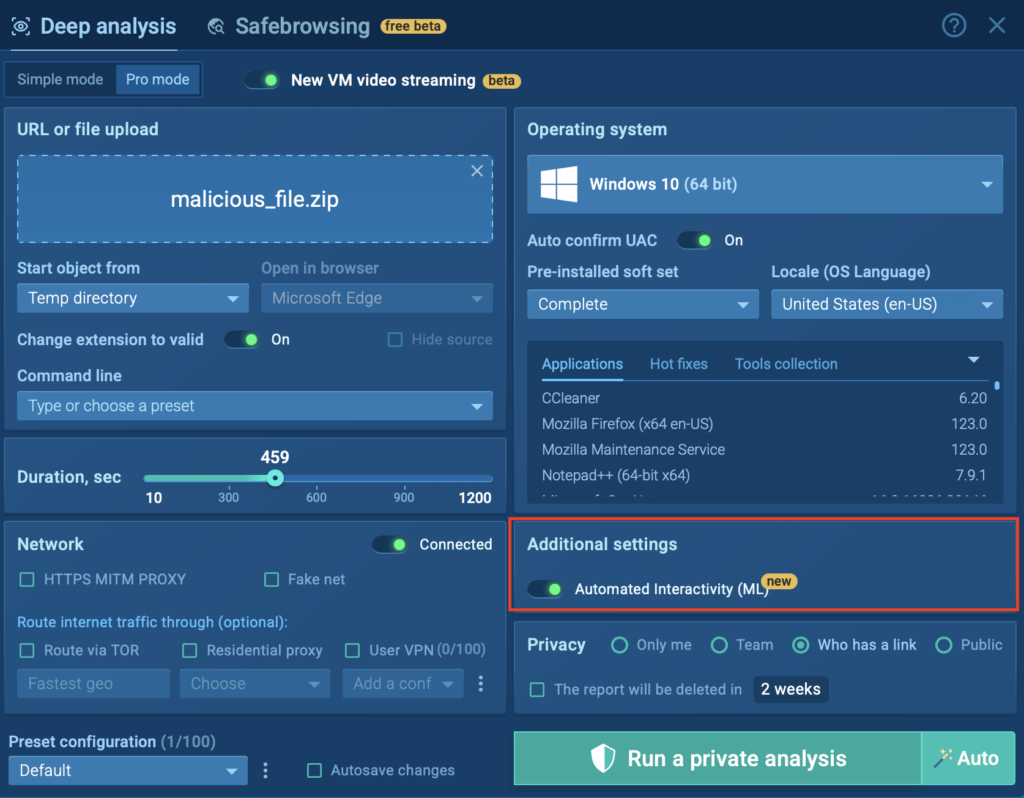
For your convenience, you can also enable the same feature manually by toggling “Automated Interactivity (ML)” in the “Additional settings” section above.
Once the session begins, you’ll notice Detonation Actions appear on the right side of the screen, next to the process tree. These hints show you exactly what steps have been or should be taken to trigger malicious behavior.
This gives you a clear picture of what was done, what triggered the threat, and how it unfolded, helping you detect malicious activity faster and respond more confidently.
In the manual mode, you can manually approve actions (by clicking the “Approve” button) or reject them (by clicking the “X” icon) for each suggested step.
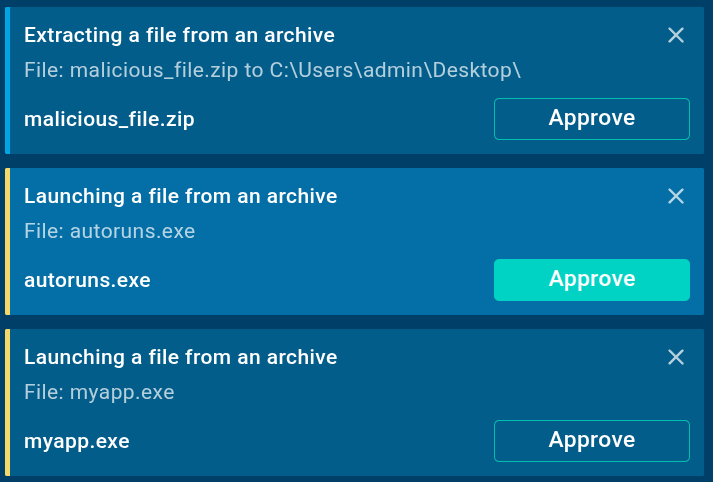
Automated Interactivity handles the actions for you; no manual approval needed.
Thanks to Detonation Actions, you get a guided analysis flow that improves detection and drastically cuts down your time to respond.
How Detonation Actions Help Analysts
Automated Interactivity
- Boosts detection rate by ensuring no critical actions are missed during analysis thanks to predefined, expert-crafted hints.
- Visualizes critical detonation steps, showing which actions were performed or recommended during the analysis.
- Frees up analyst time by automating routine tasks, so they can focus on more complex investigations while maintaining high detection quality.
Manual Analysis
- Helps uncover hidden threats by suggesting actions tailored to detonate specific malware types.
- Simplifies investigations with interactive hints like “Running this executable” or “Following this link.”
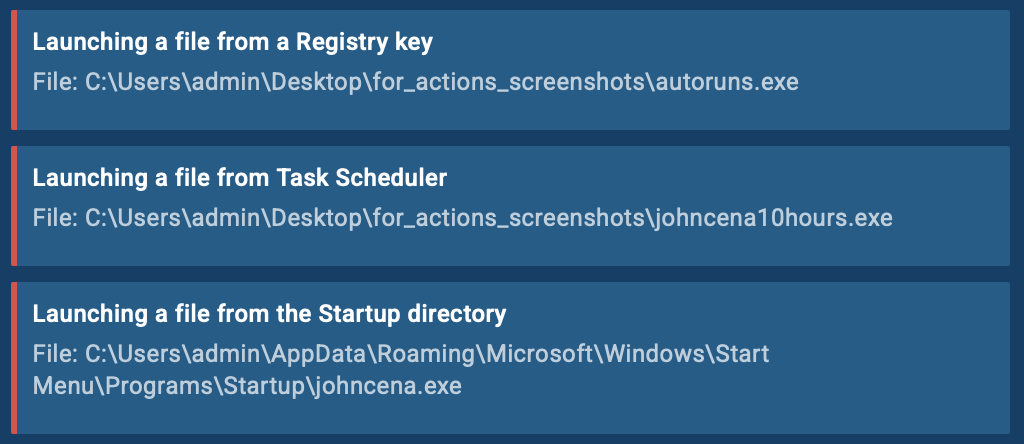
- Streamlines analysis of specific samples, for instance, by opening URLs in QR codes directly inside the analysis sessions.
- Improves accessibility by making manual analysis more intuitive for SOC analysts at any skill level.
- Speeds up decision-making through a clearer workflow and real-time actionable guidance.
See It in Action: Detonation Actions + Automated Interactivity in a Real Sample
Let’s walk through how Detonation Actions work in a real scenario using an .exe file and Automated Interactivity.
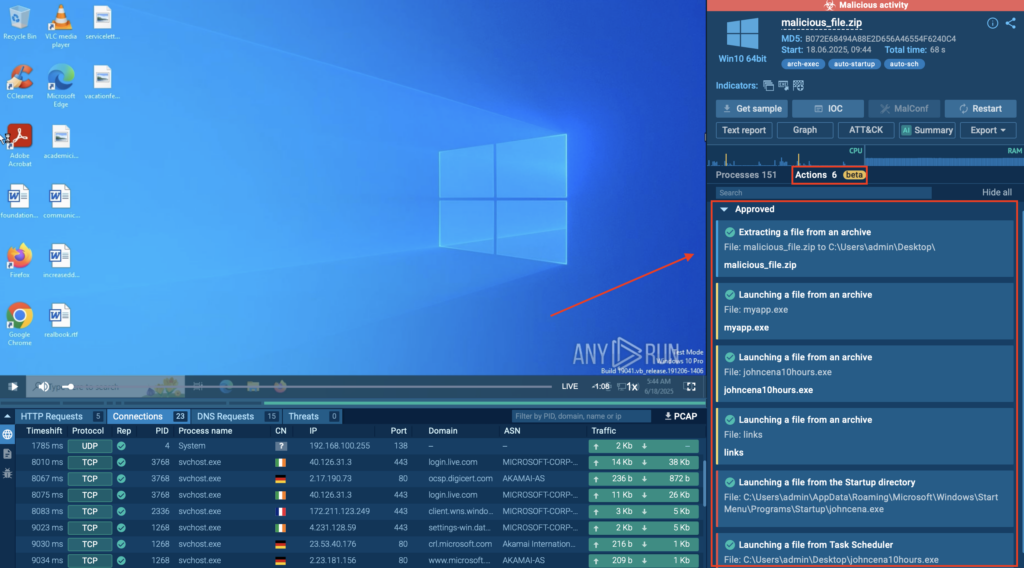
To start, we upload the .exe file and simply click the “Auto” button during the VM setup phase. This launches the sandbox session immediately with Automated Interactivity and Detonation Actions.
As the session begins, we can see Detonation Actions popping up quickly in the right corner of the screen. These actions, such as “Launching a file from Task Scheduler” or “Extracting a file from an archive”, are automatically executed, moving the analysis forward without any manual intervention.
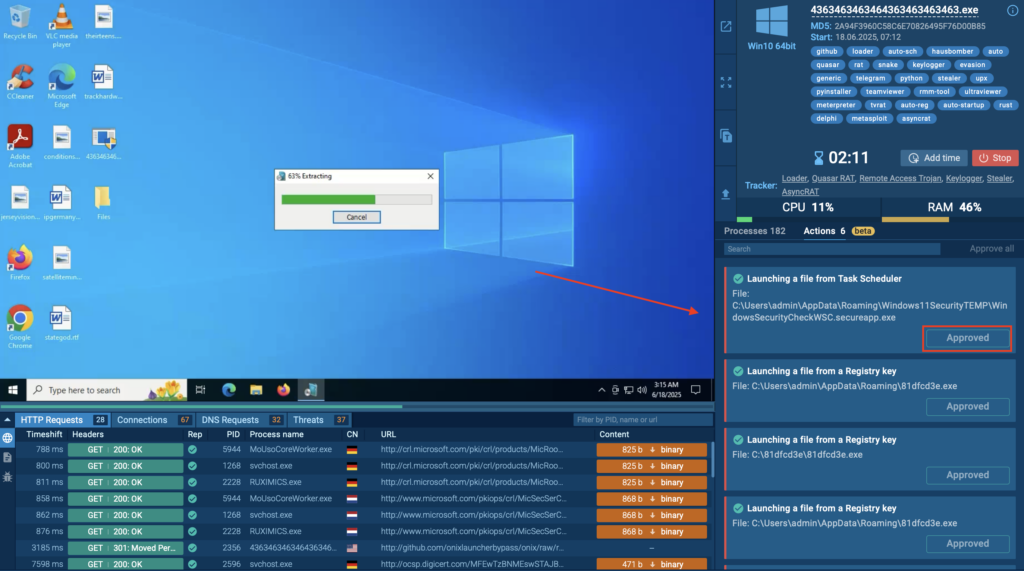
At the same time, the Processes section started populating with detailed insights, showing each spawned process along with associated tactics, techniques, and indicators.
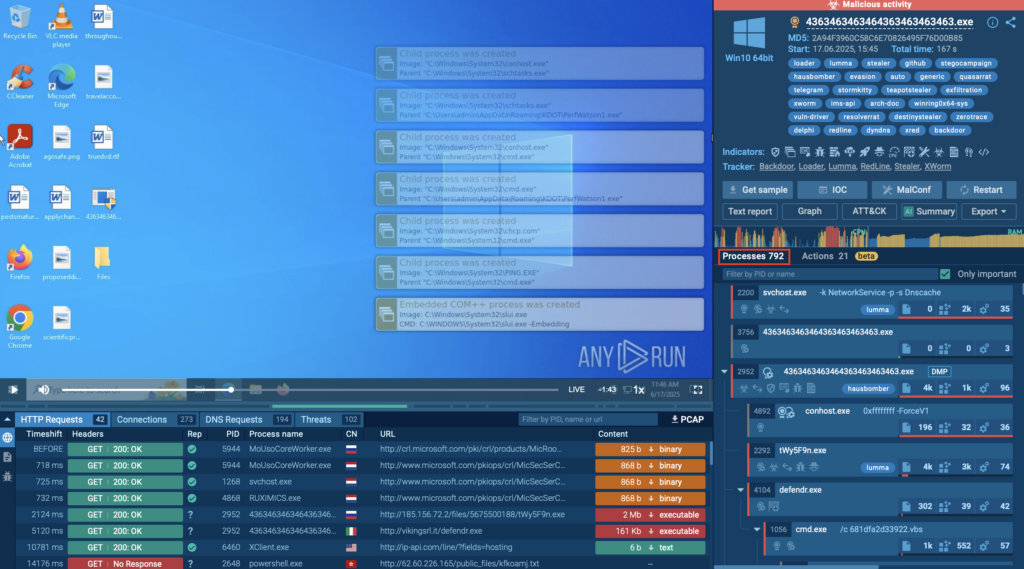
This combination, automated execution + guided visibility, gives analysts a powerful advantage: a complete behavioral picture of the malware, without delays or missed steps. It’s fast, structured, and built for clarity.
How SOCs and Businesses Benefit from It
The introduction of Detonation Actions brings clear, measurable value to security teams and businesses by improving both the speed and quality of threat analysis.
- Simplifies and accelerates threat analysis
Makes threat analysis easier and faster for SOC teams at any level, saving time, reducing manual effort, and boosting overall productivity.
- Improves data handover between SOC Tiers
Enhances the quality of data transfer from Tier 1 to Tier 2 analysts through detailed, action-based reports, ensuring critical insights are passed along clearly and efficiently.
- Enables faster incident response
Streamlines triage by automating key steps in the response process, reducing time to detect and respond to threats, and minimizing potential impact.
- Boosts employee training and onboarding
Helps junior analysts learn faster thanks to clear, guided hints, shortening the learning curve and allowing them to contribute to investigations sooner.
- Supports smarter decision-making
Empowers team members with more context and clearer behavioral evidence, helping them make faster, more confident decisions during investigations.
- Integrates easily into automation workflows
Works seamlessly with automated triage and incident response setups, maintaining high detection rates while reducing manual overhead.
Ready to Try It Yourself?
Detonation Actions are built to make your job easier, whether you’re triaging a live threat or onboarding a new team member. You get expert guidance, faster detection, and a clearer view of what malware is really doing.
Start your next investigation with ANY.RUN’s guided mode and see how much smoother analysis can be.
Launch your ANY.RUN sandbox session now
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our Interactive Sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, Threat Intelligence Lookup and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request trial of ANY.RUN’s services to test them in your organization →
The post Simplify Threat Analysis and Boost Detection Rate with Detonation Actions appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
