Why Businesses Are at Risk of Android Malware Attacks and How to Detect Them Early
It usually starts with something small: an app download, a strange text message, a tap on the wrong link. But when that device is also connected to company email, Slack, or cloud storage, it’s no longer just a personal problem.
Android malware has become a serious risk for businesses. Attackers know mobile devices are often the easiest way into a company’s internal systems, and they’re getting better at using that to their advantage.
Let’s take a closer look at why businesses are exposed, the kinds of risks these attacks create, and why it’s worth addressing them before they hit you first.
When Phones Become Attack Vectors against Businesses
Here are some of the most common and dangerous ways Android malware can put your business at risk:
1. Employee Devices with Work Access Get Infected
Personal phones are often used to check work emails, join internal chats, or access shared drives. If an employee installs a malicious app or clicks a phishing link, malware can sneak in and quietly start stealing data without triggering corporate security alerts.
2. Compromised MFA and Authenticator Apps
Many employees use their phones for two-factor authentication. If malware gains access to these apps, it can intercept or extract one-time codes, letting attackers bypass logins that were supposed to be protected.
3. Phishing Through Messaging Apps
Attackers are getting smarter about how they deliver malware. A casual-looking message via SMS, WhatsApp, or Telegram can include a link that installs malware or tricks someone into giving away credentials.
4. Sideloaded Apps from Untrusted Sources
While Google Play has basic protections, sideloaded apps don’t. If an employee downloads something from a third-party site, it could be hiding spyware, screen recorders, or backdoors that give attackers long-term access.
5. Malware Reaching Into Cloud Drives
If a compromised phone is synced with cloud services like Google Drive or OneDrive, attackers may gain access to shared folders filled with contracts, reports, or customer data.
Real-World Android Malware Attacks That Hit Businesses
The risks of Android malware aren’t hypothetical. They are already out there, actively targeting mobile users. Let’s take a closer look at how these threats operate and what they look like when analyzed inside a safe environment of ANY.RUN’s Interactive Sandbox.
Salvador Stealer: Fake Banking App That Collects Sensitive Data in Real Time
Some Android malware doesn’t need advanced tricks to be effective; it just needs to look trustworthy. Salvador Stealer is a perfect example. Masquerading as a legitimate banking app, it lures users into handing over their most sensitive information, then quietly sends it off to the attacker.
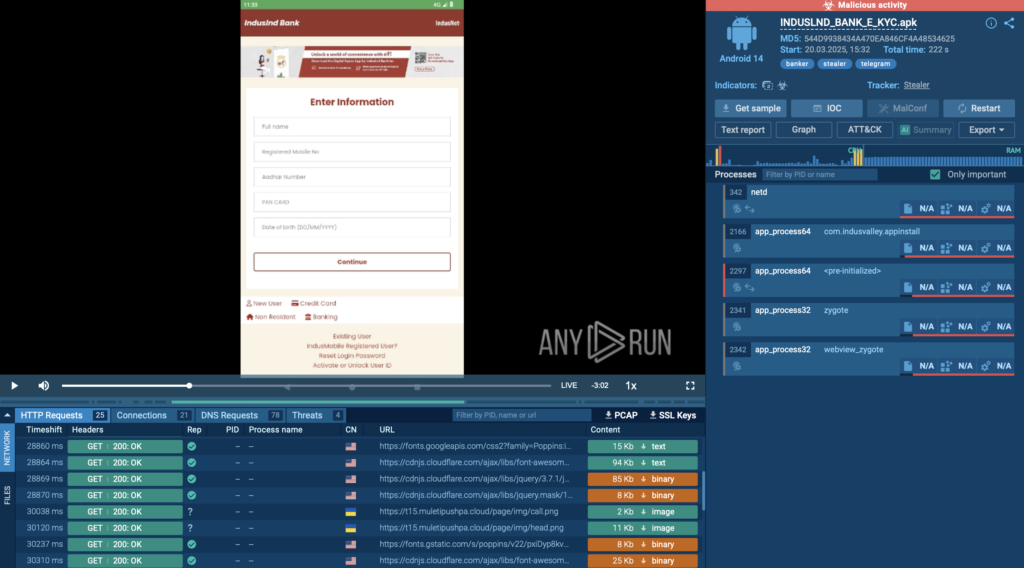
At first glance, it looks like just another banking app. But once launched, Salvador Stealer kicks off a multi-stage attack designed to harvest personal and financial data. Inside the sandbox, the full scope of its behavior becomes immediately clear; everything from fake interfaces to live credential theft is laid bare.
Here’s what we observed inside ANY.RUN’s Android sandbox:
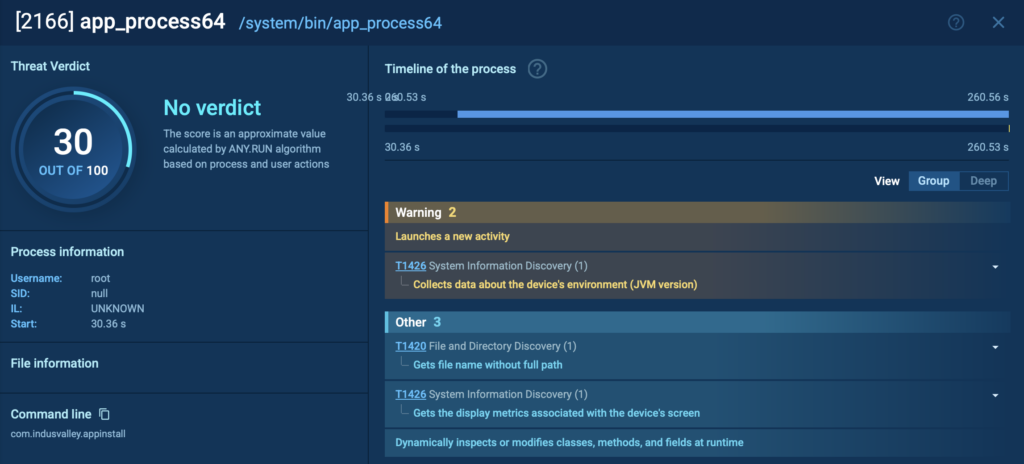
- The APK drops a second payload (base.apk), which acts as the real data stealer.
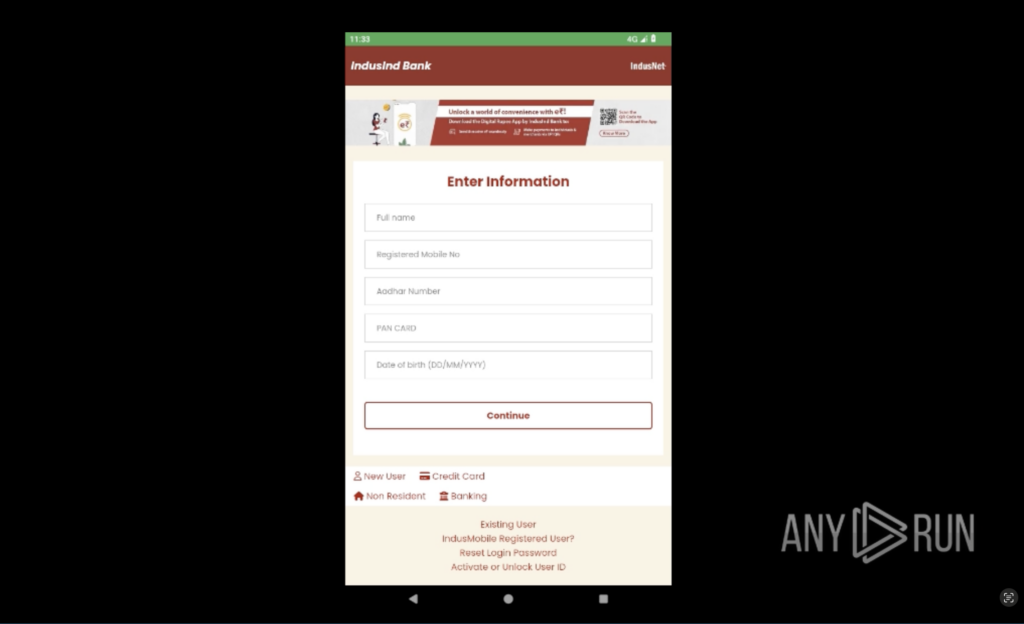
- A phishing-style login page embedded in the app tricks users into entering Aadhaar numbers, PAN cards, banking credentials, and more.
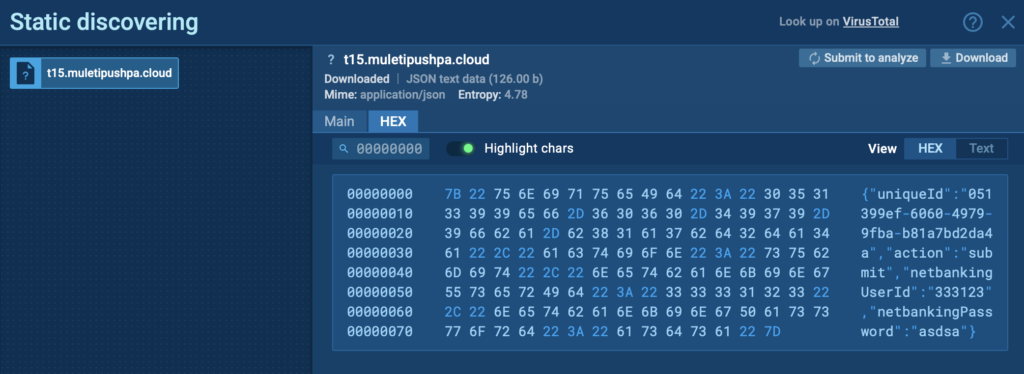
- As soon as data is entered, it’s exfiltrated in real time, sent simultaneously to a phishing site and a Telegram bot.
- SMS access is abused to intercept OTPs, allowing the attacker to bypass MFA protections.
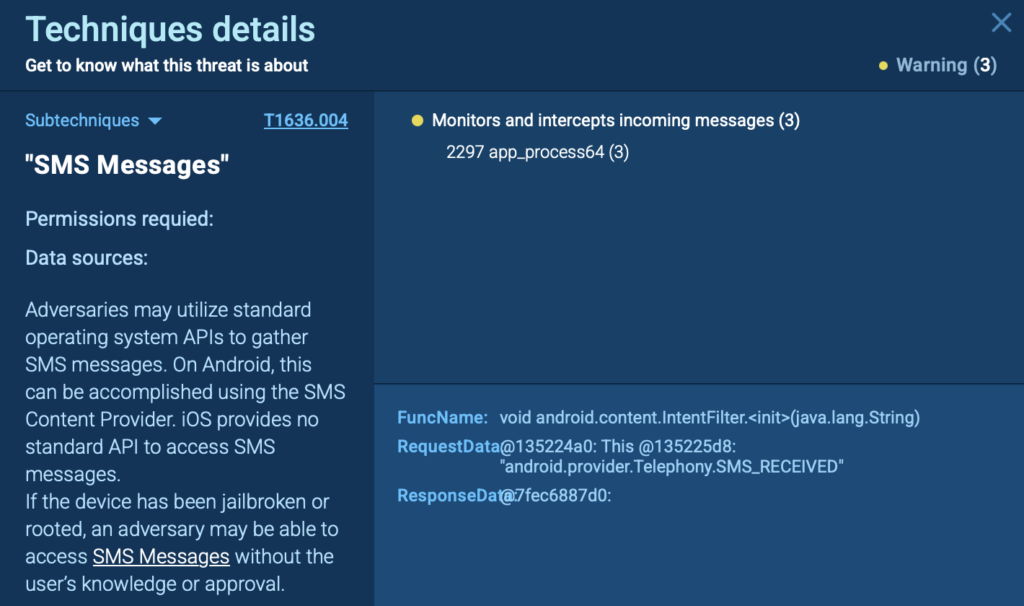
- If the app is stopped or the device is rebooted, it restarts automatically, making removal difficult without deeper system access.
Business Impact: How This Threat Could Compromise Financial Operations
When malware like Salvador Stealer slips onto an employee’s phone, it doesn’t only steal personal information but can also open the door to your company’s financial systems.
If that employee has access to payroll platforms, vendor payment portals, or internal banking credentials, the attacker could:
- Extract login tokens or session cookies from financial apps
- Capture 2FA codes via SMS interception to bypass login security
- Impersonate the employee and initiate unauthorized transactions
- Use stolen identity data (like PAN or Aadhaar) to access linked accounts
- Exfiltrate sensitive data synced with corporate drives or mobile finance apps
Even worse, because Salvador uses multiple exfiltration channels and persistence mechanisms, it can continue collecting and forwarding data long after the initial infection without triggering most mobile security alerts.
SpyNote: Remote Access Malware That Turns Phones into Listening Devices
SpyNote is a remote access trojan (RAT) designed to turn infected phones into full-on surveillance tools. Disguised as a legitimate app, it silently gains deep access to the device and starts recording, tracking, and exfiltrating everything in the background.
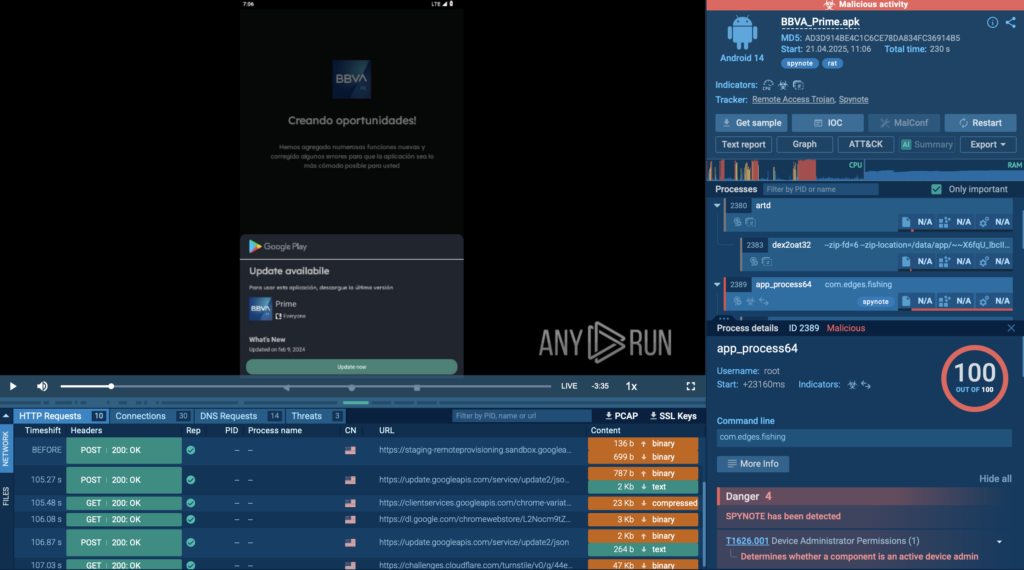
Once installed, SpyNote immediately requests Accessibility Service permissions, a common trick to quietly escalate privileges. That one tap is all it needs. From there, it clicks through remaining prompts on its own, granting itself dangerous capabilities without alerting the user.
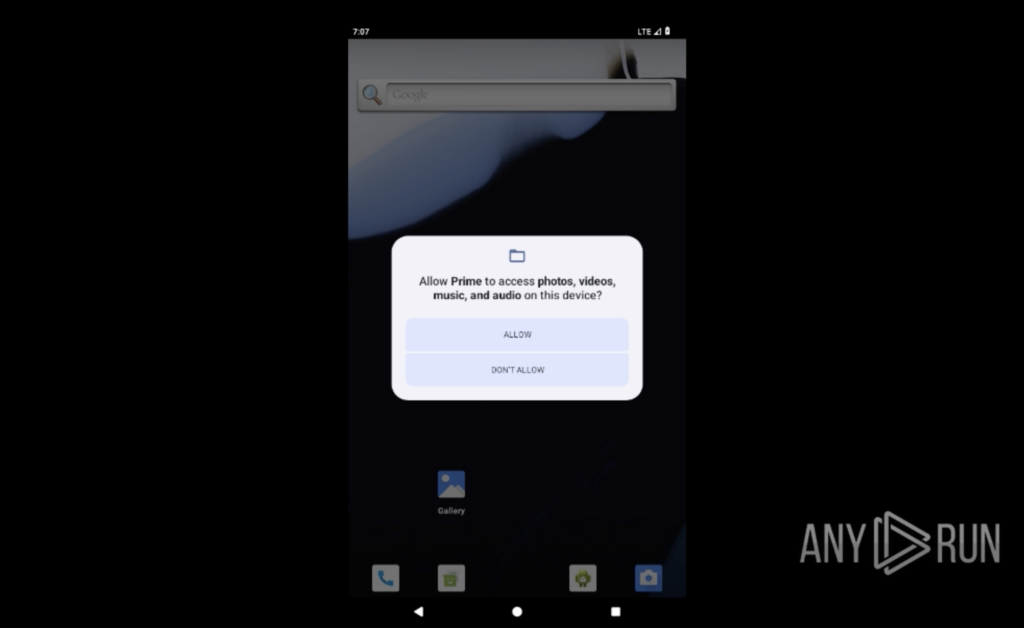
Now the attacker can activate the microphone and cameras, record calls, track GPS location, and access contacts, files, and SMS, all silently.
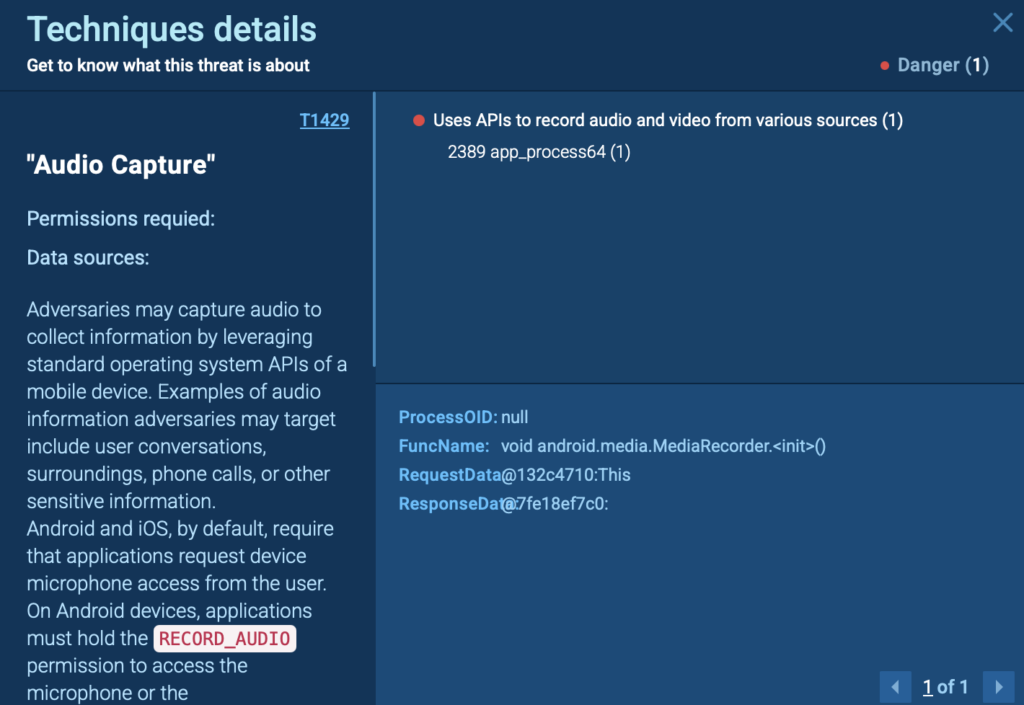
To see all the tactics and techniques used in this attack, you can click the “ATT&CK” button in the top-right corner of the ANY.RUN sandbox session. This instantly maps every malicious action to the MITRE ATT&CK framework, giving your team a clear breakdown of the attacker’s behavior, connected directly to the processes that triggered them.
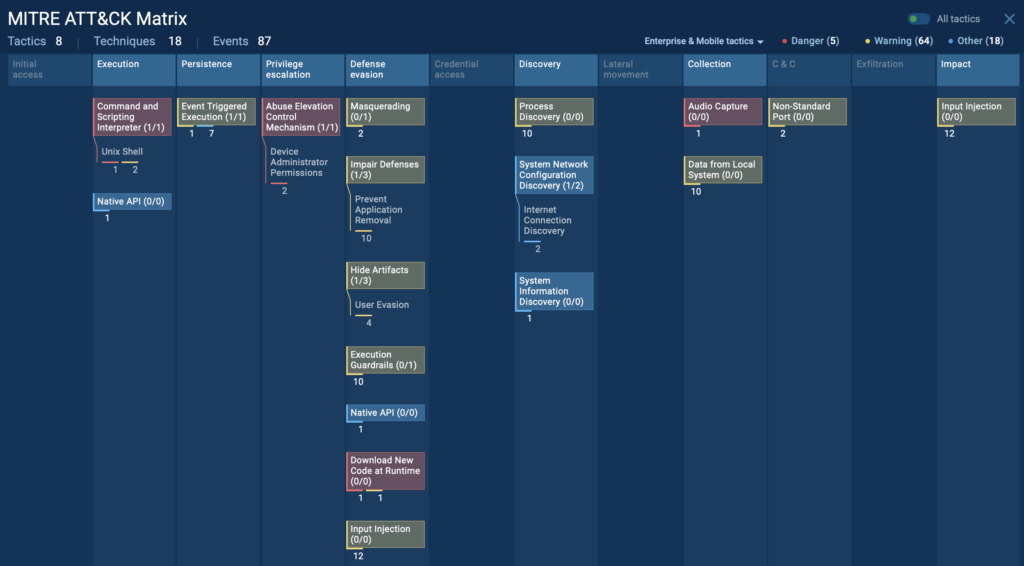
Business Risk: Surveillance on Corporate Phones
SpyNote’s goal isn’t only to steal but also to observe. When installed on a phone used for work, the risks escalate fast.
Think of what could be exposed:
- Internal meetings recorded via microphone
- Conversations in HR or legal teams captured via keylogs or screenshots
- GPS-tracked business travel or client visits
- Shared files, documents, and client data pulled from storage
- 2FA codes intercepted and forwarded to attackers
The stealthy nature of SpyNote means an infected phone might remain under attacker control for weeks, gathering intelligence, watching operations, and quietly spreading further into your network.
How ANY.RUN Helps You Detect and Respond Faster
As you’ve seen with Salvador Stealer and SpyNote, Android malware can be stealthy, persistent, and devastating. These two samples used different methods, phishing, privilege escalation, surveillance, but both were fully exposed inside ANY.RUN’s interactive sandbox.
By analyzing malware in a real Android environment, ANY.RUN helps security teams see the full picture quickly and clearly. Instead of sifting through logs or relying on static reports, you can observe how threats behave in real time and understand their true intent in minutes.
Here’s what that means for your business:
- Faster incident response: Spot and contain threats before they escalate into breaches or downtime
- Smarter decision-making: Understand the risk level and prioritize based on actual behavior, not guesses
- Clear communication: Visual reports and mapped behavior make it easier to explain threats to leadership or compliance teams
- Reduced investigation time: Automatically extract IOCs and behavioral data that would take hours to collect manually
- Stronger mobile security posture: Detect threats that specifically target mobile workflows, BYOD environments, and remote access apps
ANY.RUN shows you what malware does and helps you act on it faster, defend your organization more effectively, and avoid costly consequences.
Final Thoughts: Mobile Threats Need Real-Time Visibility
Android malware is a growing threat to business continuity, security, and trust. From stolen credentials to full-device surveillance, these attacks demand more than traditional defenses.
With ANY.RUN, your team can uncover malicious behavior in real time, trace how it works, and act before it spreads.
Start your 14-day trial with a business email
The post Why Businesses Are at Risk of Android Malware Attacks and How to Detect Them Early appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
