5 Key Ways Threat Intelligence Feeds Drive SOC Performance
Modern Security Operations Centers (SOCs) face an unprecedented challenge: defending against an ever-evolving threat landscape while managing alert fatigue, resource constraints, and the need for rapid response times. The integration of high-quality Threat Intelligence (TI) feeds has proven itself as a force multiplier for SOC teams, transforming reactive security postures into proactive defense strategies.
ANY.RUN’s Threat Intelligence Feeds exemplify how comprehensive, contextual threat data can enhance SOC performance across multiple operational dimensions. By providing real-time indicators of compromise (IOCs), behavioral insights, and detailed malware analysis, these feeds address core challenges of security teams.
Quick Recap: How Threat Intelligence Feeds Help SOCs
| Core SOC Challenges and TI Feeds Solutions | |
|---|---|
| Delayed threat detection |
|
| Slow, manual incident response |
|
| Limited visibility into attack context |
|
| Analyst overload and burnout |
|
| High business risks |
|
Further, we shall elaborate on the role of indicator feeds in optimizing main performance vectors of security teams on the example of ANY.RUN’s Threat Intelligence Feeds.
1. Early Detection of Incidents
Early detection is critical to preventing full-scale breaches. Threats should be identified before they can establish persistence or cause significant damage. Traditional signature-based detection systems often lag behind emerging threats, creating dangerous gaps in coverage during the critical early stages of an attack.
ANY.RUN’s TI Feeds offer real-time access to a continuous stream of fresh Indicators of Compromise (IOCs) gathered from thousands of interactive malware sandbox sessions daily. These indicators include malicious IP addresses, domain names, and URLs that can be quickly integrated into SIEM platforms and security tools.
- Based on sandbox investigations of threats across 15,000 organizations
- Unique indicators from Memory Dumps, Suricata IDS, and internal threat categorization systems
- Verified malicious IPs, domains, and URLs, updated every few hours
Early detection is particularly powerful when combined with automated threat hunting workflows. SOC analysts can configure their systems to automatically query historical logs and network traffic against newly received indicators to uncover ongoing attacks. This retrospective analysis capability means that even if a threat initially bypasses existing controls, it can be identified and contained as soon as relevant intelligence becomes available.
By reducing the Mean Time to Detection (MTTD) organizations can significantly limit the potential impact of security incidents.
2. Faster Threat Mitigation
In cybersecurity, minutes can mean the difference between a contained incident and a major breach. ANY.RUN’s Threat Intelligence Feeds enable automated response mechanisms that dramatically reduce the time between threat identification and mitigation actions.
The feeds’ structured data format allows for seamless integration with Security Orchestration, Automation, and Response (SOAR) platforms and other security tools. When new malicious indicators are received, automated playbooks can immediately trigger protective actions such as blocking malicious IP addresses at firewalls, quarantining suspicious files, or isolating potentially compromised endpoints. The reduction in manual intervention not only accelerates response times but also ensures consistent execution of response procedures regardless of analyst availability or expertise level.
- STIX & MISP formats
- TAXII protocol support
- Connect with any vendor, including OpenCTI, ThreatConnect, QRadar, etc.
The feeds also support threat hunting automation, where new indicators automatically trigger searches across historical data, network logs, and endpoint telemetry. Automatization results in a significant reduction in Mean Time to Response (MTTR), often cutting response times from hours to minutes. This acceleration is particularly critical for threats that exhibit rapid lateral movement or data exfiltration capabilities.
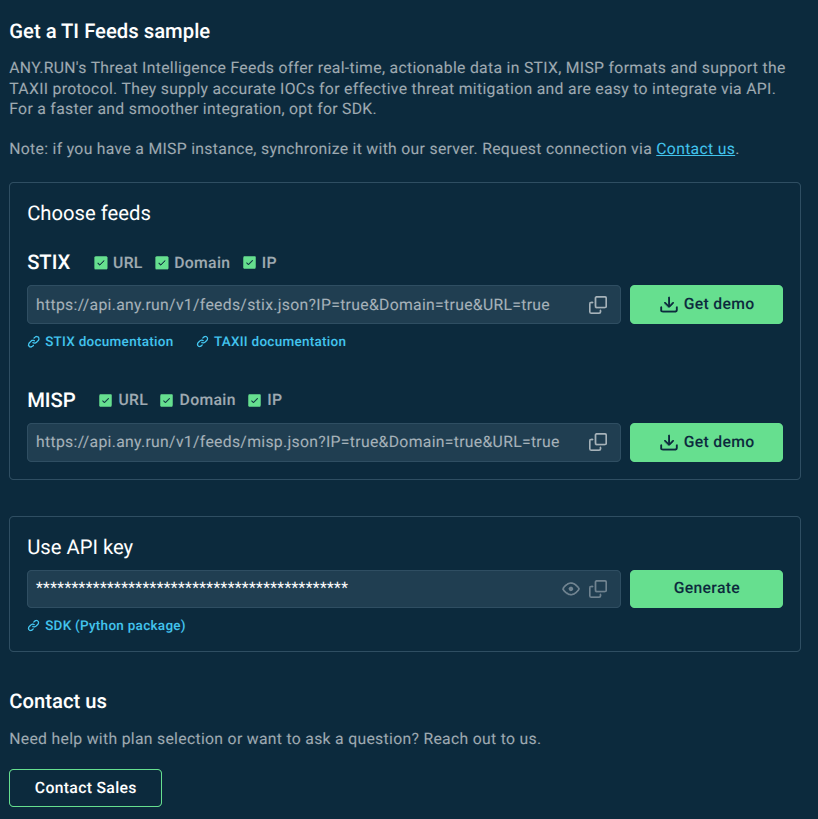
You can request an ANY.RUN’s TI Feeds sample with preferred settings and get assistance with your integration:
3. Better Attack Visibility and Proactive Defense
Understanding the full scope and context of cyber threats is essential for effective defense. ANY.RUN’s Threat Intelligence Feeds provide SOC teams with actionable visibility into campaigns through metadata and direct links to detailed sandbox analysis sessions.
Each indicator of compromise comes enriched with contextual information, including malware family classification, detection timestamps, related artifacts, and campaign attribution data. This metadata enables analysts to know not just what to block, but why the threat is significant, and how it fits into broader attack patterns.
- Indicators come with extensive metadata
- Related sandbox sessions show threats’ execution and TTPs
- IOCs are linked to specific threats
The integration with ANY.RUN’s Interactive Sandbox provides an additional layer of research depth. When investigating an alert triggered by a threat intelligence indicator, analysts can access the complete sandbox session that generated the IOC, observing the malware’s behavior in real-time.
For example, let’s view Virlock ransomware detonated in the Sandbox:
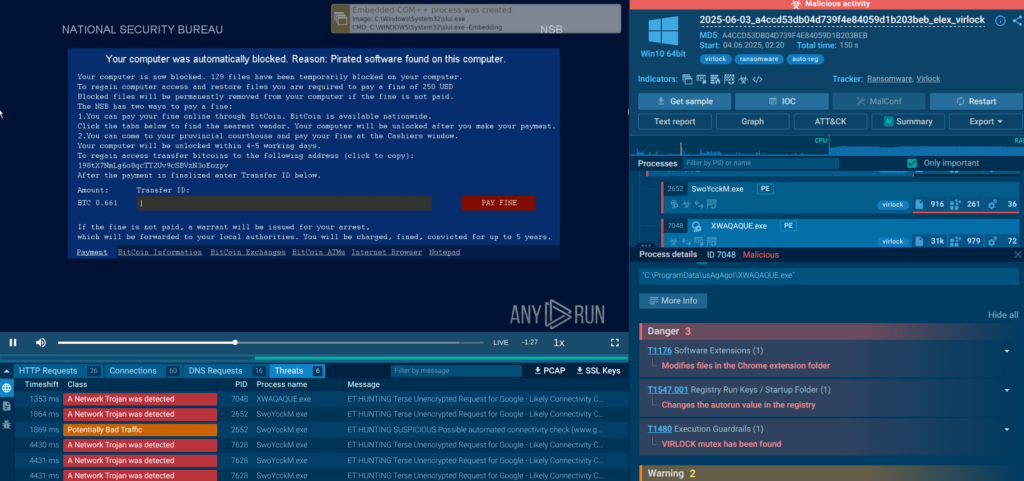
By understanding the tactics, techniques, and procedures (TTPs) associated with specific threat actors, SOC teams can implement preventive measures and monitoring strategies tailored to anticipated attack vectors.
4. Reduced Analyst Fatigue
An average SOC handles 11,000 alerts daily, with only 19% worth investigating, per the 2024 SANS SOC Survey. Analysts get routinely overwhelmed by high volumes of security alerts, many of which prove to be false positives. ANY.RUN’s Threat Intelligence Feeds address this challenge by improving alert quality and providing the context necessary for rapid triage and decision-making.
The contextual metadata and sandbox links accompanying each indicator further reduce investigation time by providing analysts with immediate answers to common questions. The sandbox integration is particularly helpful for junior analysts who may lack the skills and experience required for advanced malware analysis.
The effect is a more sustainable SOC workflow where analysts can focus on high-value activities such as threat hunting, incident response, and security architecture improvements rather than being overwhelmed by alert triage and manual investigation tasks.
5. Risk Reduction
The ultimate goal of any security operation is risk reduction, and ANY.RUN’s Threat Intelligence Feeds contribute to this objective through mechanisms that address both immediate tactical threats and overall security posture.
At the tactical level, the feeds enable rapid identification and mitigation of active threats, directly reducing the organization’s exposure to compromise and impact from successful attacks. The automated response mechanisms fueled by TI Feeds ensure that threats are contained before they can achieve their objectives, whether those involve data theft, system disruption, or lateral movement.
The proactive defense capabilities enabled by ANY.RUN’s Threat Intelligence Feeds also contribute to long-term risk reduction by helping organizations stay ahead of emerging threats. Rather than simply responding to attacks after they occur, SOC teams can implement preventive measures based on observed attack trends and threat actor innovations.
How to Integrate Threat Intelligence Feeds from ANY.RUN
You can test ANY.RUN’s Threat Intelligence Feeds in STIX, MISP, and TAXII formats by requesting a trial on this page.
- Spot and block attacks quickly to prevent disruptions and damage.
- Keep your detection systems updated with fresh data to proactively detect emerging threats.
- Handle incidents faster to lower financial and brand damage.
ANY.RUN also runs a dedicated MISP instance that you can synchronize your server with or connect to your security solutions.
Conclusion
ANY.RUN’s Threat Intelligence Feeds help SOCs transform into proactive, intelligence-driven operations. The combination of real-time IOCs, rich metadata, and sandbox integration provides SOC analysts with the framework they need to protect their organizations effectively.
Businesses implementing TI feeds can expect measurable improvements in key performance indicators including Mean Time to Detection, Mean Time to Response, false positive rates, and analyst retention. More importantly, they can expect a fundamental shift from reactive to proactive security operations, with improved resilience against both current and emerging threats.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request trial of ANY.RUN’s services to test them in your organization →
The post 5 Key Ways Threat Intelligence Feeds Drive SOC Performance appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


