How SOC Teams Save Time and Effort with ANY.RUN: Action Plan
Recently, we hosted a webinar exploring the everyday challenges SOC teams face and how ANY.RUN helps solve them. From low detection rates to alert fatigue, poor coordination, and infrastructure overhead, our team outlined a practical action plan to tackle it all.
Missed the session? Here are the key highlights in this quick recap.
1. Increasing Detection Rate
Challenge: Malware is getting trickier. Fileless techniques, multi-stage payloads, and threats that hide behind user interactions are slipping past traditional tools. This leaves SOC teams blind to critical risks.
Solution: ANY.RUN tackles this head-on by giving analysts a fully interactive sandbox environment. You don’t just watch malware from a distance but also engage with it like a real user. Open files, enter passwords, click suspicious links, whatever it takes to trigger the full execution chain.
One real-world case shows exactly why this is so important.
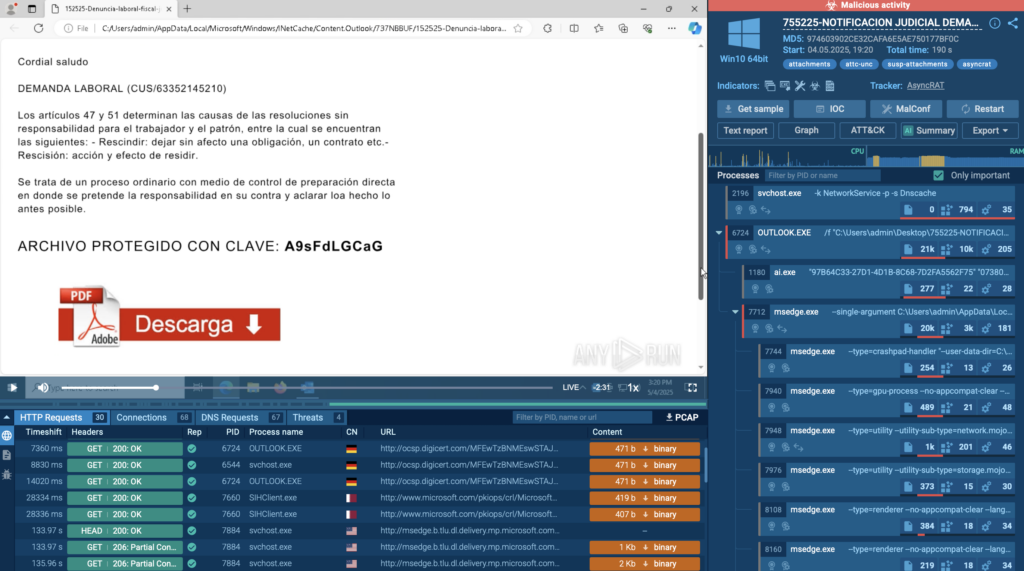
A phishing email came through with an SVG attachment and a password hidden in the message body. Opening the SVG revealed a fake document with a link to download a PDF. That triggered a download of a ZIP archive; one that could only be extracted by manually entering the earlier password.
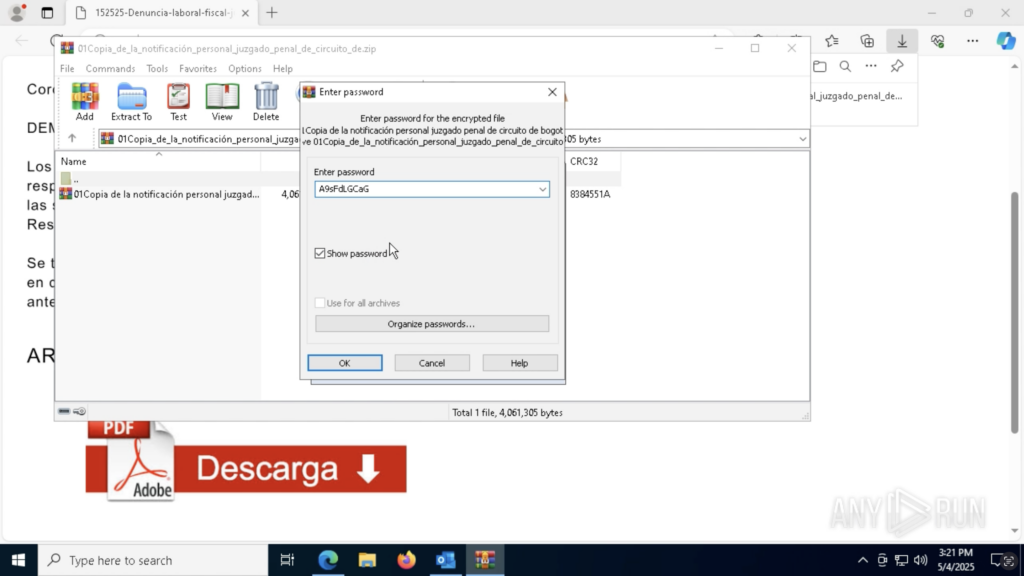
Inside we found an executable file. When run, ANY.RUN flagged it immediately as AsyncRAT, a remote access trojan capable of spying on and controlling infected systems.
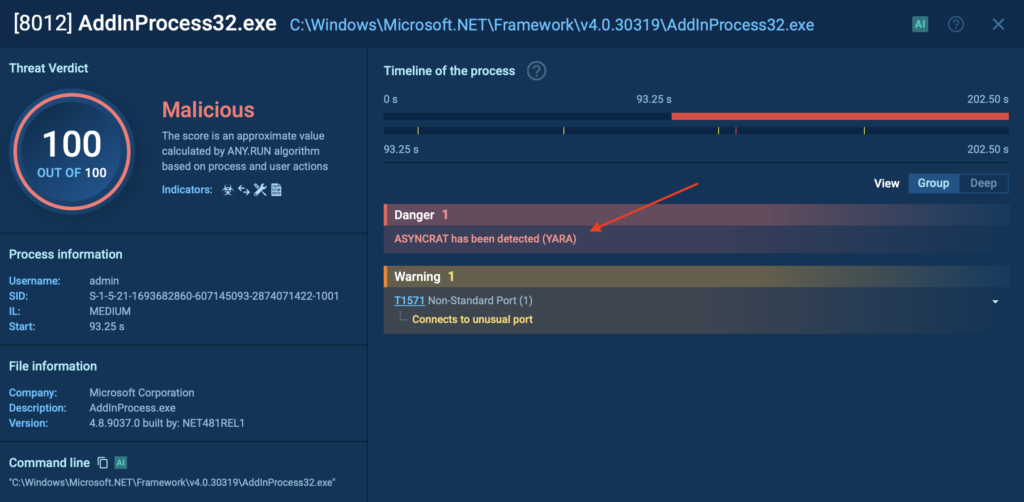
Without interactivity, none of this would have unfolded. A fully automated tool wouldn’t have clicked the link, copied the password, or opened the archive. The attack would’ve gone undetected.
More importantly, the sandbox gave the team:
- A full process breakdown, showing exactly how the malware executed
- Network activity visibility, helping block C2 communication before data exfiltration
- Malware configuration (MalConf), revealing hardcoded domains and other indicators
- Higher detection rates: Fewer blind spots and stronger cyber resilience
- Cost efficiency: Avoiding costly breaches by stopping threats early
- Proactive threat mitigation: Addressing vulnerabilities before attackers exploit them
2. Accelerating Alert Triage and Incident Response
Challenge: When a threat gets past initial defenses, every second counts. The longer it takes to triage an alert or respond to an incident, the higher the risk of malware spreading, systems being compromised, and costly damage being done.
Solution: ANY.RUN provides real-time visibility into malware behavior; no waiting for the sandbox session to end. SOC teams can spot malicious activity the moment it begins, with some malware families being identified even in under 40 seconds.
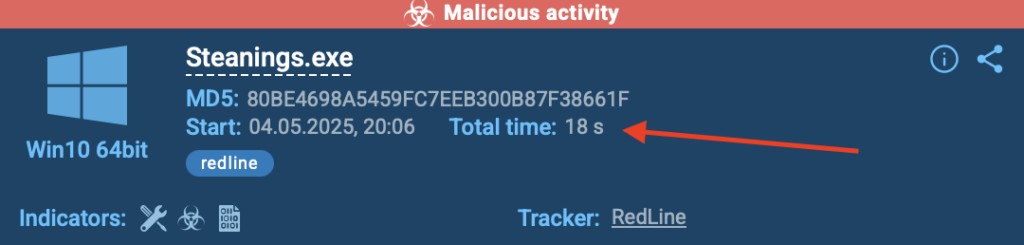
In one case, a suspicious executable was submitted. Within just 18 seconds, ANY.RUN identified it as RedLine Stealer, an infostealer known for targeting credentials and sensitive data.
That rapid detection enabled the security team to take immediate action, cutting off further exposure and containing the threat before it spread.
- Minimized risk exposure: Stop malware early, before it spreads across systems
- Operational efficiency: Reduce alert fatigue and free up analyst resources
- Faster, more reliable incident handling: Protect brand trust and stakeholder confidence
3. Streamlining Training and Onboarding
Challenge: Most security tools come with a steep learning curve. New hires, especially junior analysts, often need months of training before they can contribute meaningfully. That slows down onboarding and increases your team’s dependency on a handful of experts.
Solution: ANY.RUN’s intuitive interface and interactive analysis experience make it a powerful learning environment even for less experienced team members.
New analysts work directly with real threats in a controlled, visual sandbox environment. Features like Script Tracer and AI Summary break down even complex threats into clear, understandable steps.
In one case, a junior analyst explored a sample involving malicious scripting. By opening the Script Tracer, they followed each function call and saw how the attack unfolded line by line. No guesswork. No external tools.
And with the AI Summary, they quickly reviewed the session’s key events, including dropped files, command-line activity, and network behavior, all explained in plain terms.
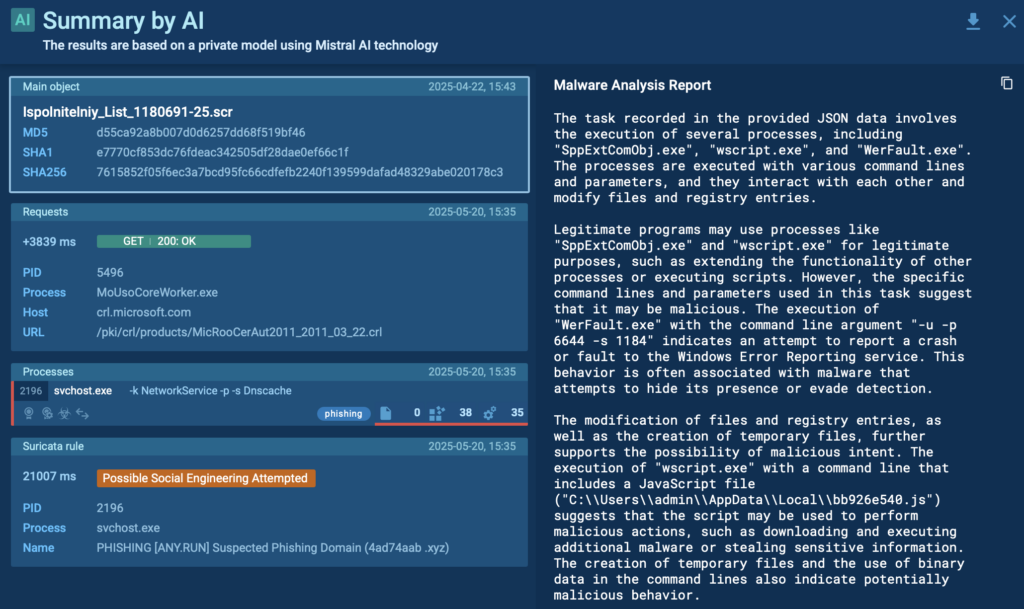
What the sandbox offered for junior specialists:
- Hands-on practice with real malware builds confidence and accelerates learning
- Step-by-step script analysis simplifies complex attacks into teachable moments
- Automated summaries make onboarding easier and less resource-intensive
- Skilled workforce: Accelerate team readiness and reduce reliance on senior staff
- Cost-effective training: No need for expensive onboarding and training
- Faster onboarding: New hires start contributing sooner, without draining resources
4. Addressing Infrastructure Maintenance
Challenge: Maintaining local infrastructure for malware analysis can be a huge drain on time, budget, and IT resources. From server upkeep to licensing and hardware limitations, scaling your operations becomes a logistical challenge, especially across global or hybrid teams.
Solution: ANY.RUN eliminates that overhead with a fully cloud-based sandbox platform. There’s no setup, no hardware dependency, and no waiting around for installations or updates. Everything runs in the browser.
Your team can launch pre-configured virtual machines (Windows, Linux, or Android) in seconds, whether they’re in the office or halfway across the world. There’s no cap on the number of analyses, and you can scale instantly by adding users without touching infrastructure.
In fact, one of our enterprise clients, Expertware, reduced their IOC extraction and investigation turnaround time by over 50% after switching to ANY.RUN, all without deploying a single server.

Read interview details here: How MSSP Expertware Uses ANY.RUN’s Interactive Sandbox for Faster Threat Analysis
Key benefits of the sandbox:
- Zero setup required: Fully browser-based, ready to go from day one
- Unlimited analysis: No hardware limits, no bottlenecks
- Pre-configured VMs: Supports cross-platform investigations (Windows, Linux, Android)
- Cost savings: No on-prem infrastructure or licensing overhead
- Scalability: Add new users instantly without extra drag
- Faster time to value: Onboard, analyze, and act faster than traditional setups
5. Improving Team Coordination
Challenge: Even the best tools fall short when teams can’t work together efficiently. In many SOCs, communication gaps between analysts, team leads, and managers lead to duplicated work, missed alerts, and delays in decision-making.
Solution: ANY.RUN’s built-in Teamwork Mode is designed to make collaboration effortless no matter if your team works in the same office or across time zones. You can create different teams, assign roles, manage access, and track progress, all from a single interface.
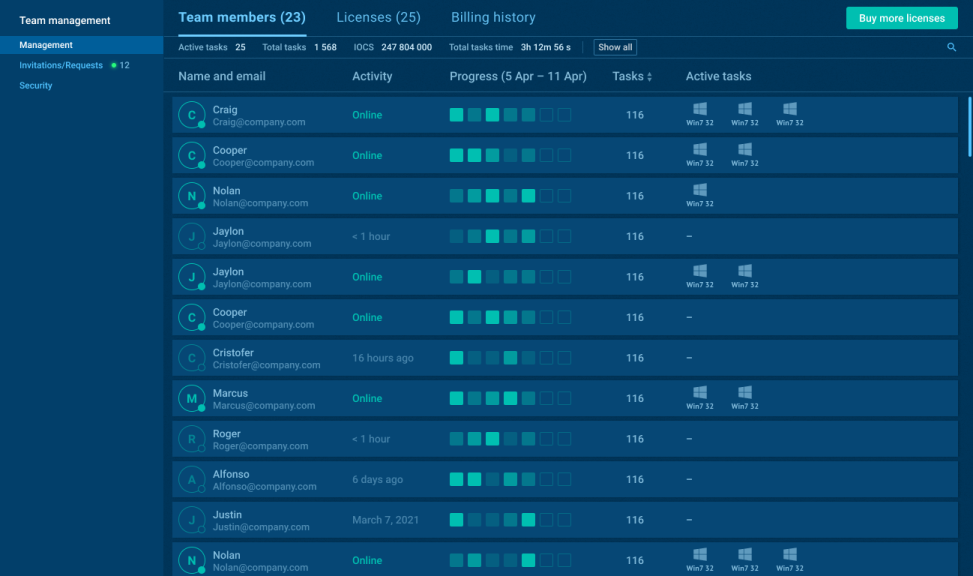
You also get full control over privacy settings. Make all submissions private by default or customize access levels for each user based on their role. That means sensitive data stays protected without compromising collaboration.
Learn more about the Teamwork Mode here: ANY.RUN Teamwork Mode Updates
- Better visibility for managers: Monitor investigations without slowing the team down
- More structure across teams: Define roles and workflows clearly
- Improved security posture: Ensure sensitive data is only seen by the right people
6. Freeing up Analysts for More Important Tasks
Challenge: Manual analysis takes time, and relying on human input for every alert doesn’t scale. But the alternative, fully automated tools, often miss threats that require user interaction to activate, like phishing pages behind CAPTCHAs or payloads inside password-protected files.
Solution: ANY.RUN bridges that gap with Automated Interactivity, a unique feature that emulates real user behavior inside the sandbox. It clicks, types, solves CAPTCHAs, and opens files, just like a real analyst would, ensuring full detonation of the threat and speeds up investigations.
That means even in automated mode, your team doesn’t miss threats that rely on tricking the user into doing something first.
View automated interactivity session here
In this session, the sandbox was given a phishing URL. It required a CAPTCHA check to reach the final malicious page; something most tools would skip. But with Automated Interactivity, ANY.RUN solved the CAPTCHA, reached the phishing content, and flagged the threat immediately.
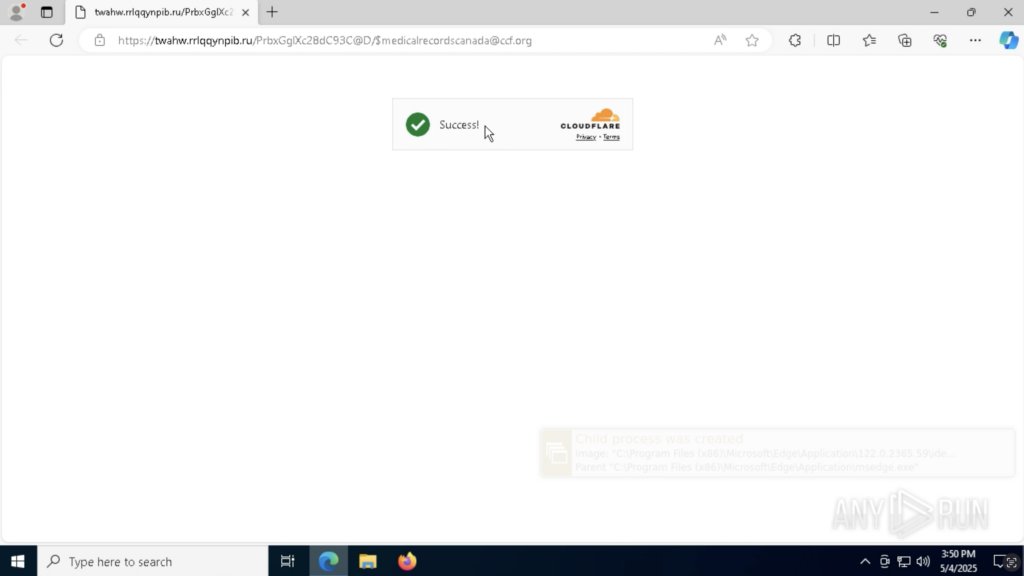
- Scalable analysis workflows: Handle more alerts without expanding your team
- Lower operational costs: Less time per case, more automation without blind spots
- Consistent detection quality: Get the same deep results whether done manually or programmatically
7. Gaining Better Visibility into Emerging Threats
Challenge: One of the biggest challenges for SOCs today is staying ahead of threats. When you don’t have enough intel, or worse, outdated intel, you’re forced to react instead of prepare. That slows down your defenses and increases your exposure.
Solution: ANY.RUN’s Threat Intelligence Lookup (TI Lookup) gives your team access to a constantly updated database of real-world Indicators of Compromise (IOCs), Action (IOAs), and Behavior (IOBs), collected from hundreds of thousands of sandbox analyses performed by SOC teams across 15,000 businesses.
With over 40 filterable parameters, your team can create advanced queries to uncover patterns, spot repeat offenders, and enrich investigations with up-to-date threat data.
Let’s have a look at the following TI Lookup query:
This query helps to collect intel on phishing threats that host malicious pages on the glitch.me domain and use Telegram for exfiltration.
After hitting enter and see fresh threat samples and indicators that match our request. This includes IPs, URLs, domains, and links to sandbox analyses of actual phishing attacks.
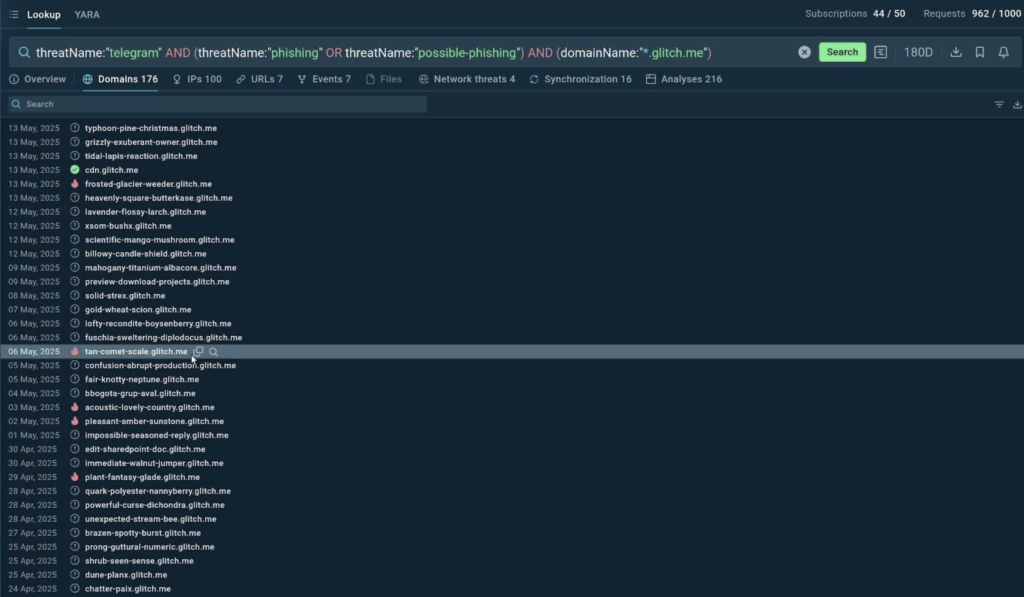
That’s how in seconds we gained over a hundred new indicators that can enrich our defense infrastructure.
By having just one or two artifacts, you can quickly connect them to the threats, attacks, and campaigns behind them.
Our database is constantly updated with unique indicators because the data comes from the latest sandbox analyses globally.
As a result, your team gains:
- Fast, flexible search to find IOCs by threat name, behavior, domain, file type, and more
- Fresh, actionable data sourced from real sandbox detonations globally
- Subscription-based monitoring to stay informed on new threats matching saved queries
ANY.RUN’s TI Lookup turns passive intel into an active advantage, giving your team the context they need to protect your business from evolving threats.
- Proactive defense: Equip your team with the intel they need to strengthen defenses before an attack happens, not after
- Continuous monitoring: Subscribe to threat patterns and stay informed about evolving risks specific to your environment
- Faster triage and response: Quickly link isolated indicators to known threats and campaigns, helping your team respond with precision and speed
8. Expanding Threat Monitoring and Detection Capabilities
Challenge: Many detection systems rely on outdated or generic threat feeds. The result is missed attacks, wasted time chasing false positives, and a growing gap between what your team sees and what attackers are actually doing in the wild.
Solution: ANY.RUN’s Threat Intelligence Feeds (TI Feeds) deliver fresh, high-confidence IOCs straight from live sandbox investigations submitted by over 15,000 companies around the world. These feeds include metadata-rich indicators linked to real execution behavior and attack chains.
Test and integrate TI Feeds from ANY.RUN
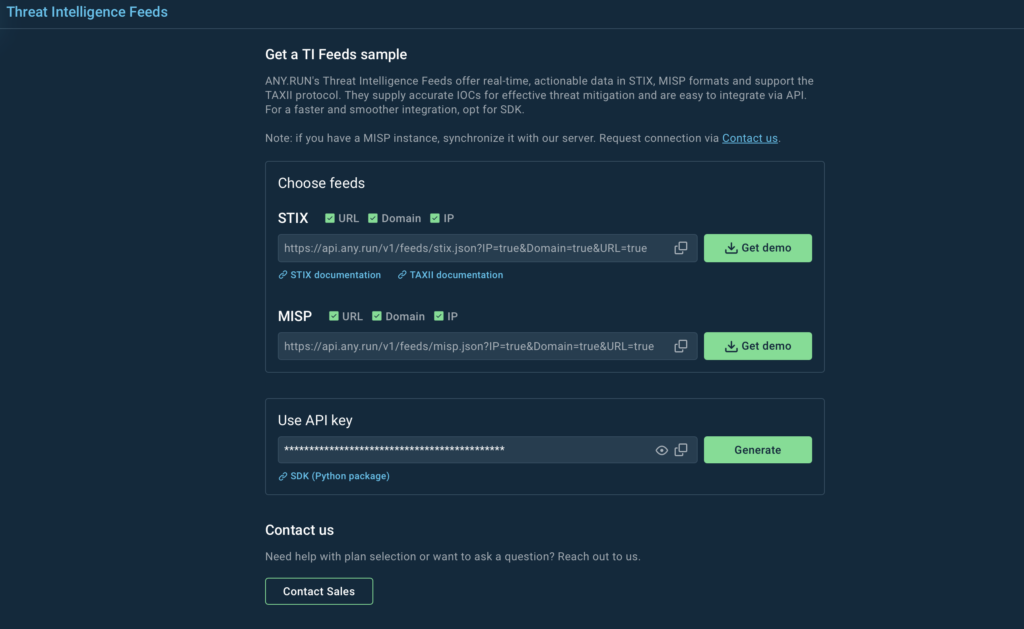
The feeds are available in widely supported formats (STIX, MISP) and integrate via the TAXII protocol, making it easy to plug directly into your SIEM, SOAR, or XDR platform.
What your team gains:
- Enriched detection systems supplemented with data from active malware campaigns
- Unique indicators for identifying emerging malware pulled from memory dumps, Suricata alerts, and internal categorization
- Context-aware intel with IOCs tied to sandbox sessions, giving full visibility into how the threat behaves, which is essential for timely and effective incident response
- Improved detection rates: Expand your visibility with threat data that reflects what attackers are doing right now, not last quarter
- Competitive advantage: Stay ahead of emerging threats, build resilience, and position your organization as security-forward
- Proactive security: Fresh, actionable feeds allow your team to take preventive measures, reducing the chances of successful attacks before they even begin
Solve Your SOC Challenges with ANY.RUN
Security teams today are under constant pressure to detect more, react faster, and do it all with limited resources. ANY.RUN is built to help modern SOCs meet those demands with speed, precision, and clarity.

ANY.RUN helps your team reduce effort, increase impact, and stay ahead of evolving threats with the tools they actually need.
Ready to see the difference for yourself?
Start your ANY.RUN trial to see how our services can contribute to your security→
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with TI Lookup, YARA Search, and Feeds, we equip businesses to speed up investigations, reduce security risks, and improve team’s efficiency.
The post How SOC Teams Save Time and Effort with ANY.RUN: Action Plan appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

 Quick reminder
Quick reminder
