Release Notes: TAXII Support for TI Feeds, New Sandbox Onboarding, and 900+ Detection Rules
We’ve packed May with updates to make your experience smoother and your threat detection even sharper. Whether you’re just getting started or knee-deep in malware every day, these changes are here to save you time and give you better insights.
In this update:
- A brand-new onboarding tutorial in the sandbox to guide you step by step
- TAXII support for TI Feeds, so you can plug threat intel right into your tools
- A big boost in threat coverage, with new signatures, YARA rules, and standout samples
Take a look below to see how these updates can help you work faster, stay ahead of threats, and get more out of ANY.RUN!
Product Updates
New Sandbox Onboarding Tutorial
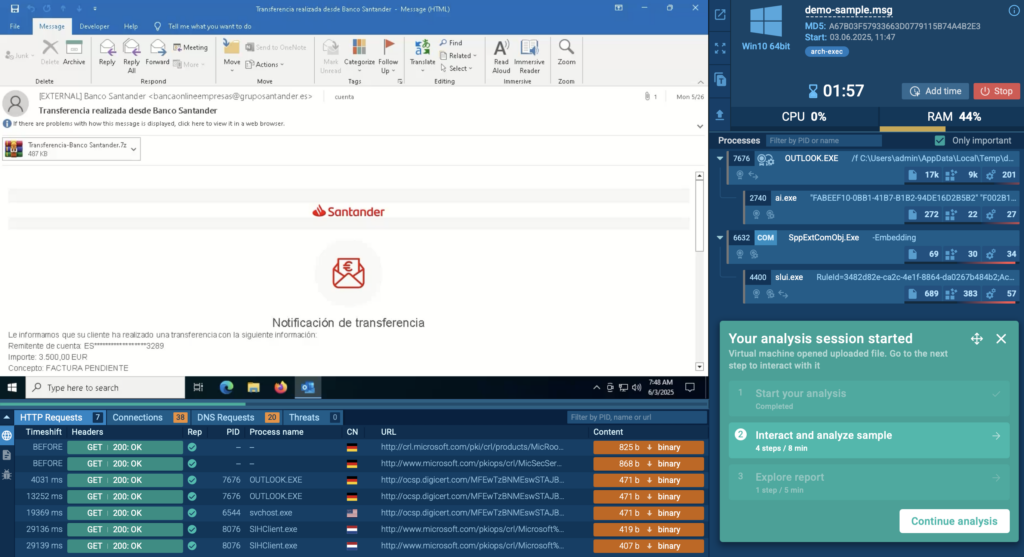
Whether you’re brand new to ANY.RUN or just want a quick refresher, the new onboarding tutorial in the sandbox has you covered. It walks you through each step of the analysis process, from uploading a sample to making sense of the process tree, network activity, and IOCs.
It’s a great starting point for new analysts or anyone looking to get more comfortable with the platform.
You can find it in the FAQ section under the Tutorials tab; just click on Quick Sandbox Tutorial and you’re good to go.
TAXII Protocol Now Supported for TI Feeds
TAXII (Trusted Automated eXchange of Indicator Information) is a widely used protocol for sharing threat intelligence in a fast, secure, and standardized way. It’s designed to make integrating threat data with your existing tools, like SIEMs, EDRs, or TIPs, smooth and efficient.
Now, ANY.RUN’s Threat Intelligence Feeds fully support TAXII, making it even easier to bring high-quality threat data directly into your security stack.
Here’s what you get with ANY.RUN’s TI Feeds + TAXII integration:
- Actionable, real-world threat indicators: The feeds pull data from threats seen across 15,000+ companies worldwide. You’ll get fresh, high-confidence IOCs sourced from dynamic malware analysis and enriched with context from ANY.RUN’s sandbox.
- Minimal false positives: Every indicator is pre-processed and vetted before it reaches your system, so you get clean, reliable data that won’t overload your analysts or flood your alerts.
- Boosted detection and response automation: Use TI Feeds to automatically block malicious IPs, flag risky logs, enrich alerts, or trigger playbooks, saving your team time and cutting response delays.
How It Works
If you’re on a paid plan, you can now set up ANY.RUN’s TI Feeds as a TAXII endpoint in your existing system, whether it’s a SIEM, EDR/XDR, NGFW, or TIP platform.
Once connected to our TAXII server, your tools will start receiving fresh threat intel automatically. Want to see what the feeds look like? You can preview a sample in STIX or MISP format.
For full access to the latest indicators, reach out to us for 14-day trial of TI Feeds.
Threat Coverage Updates
In May, we expanded our detection coverage across Windows, Linux, and Android environments with 900+ new behavior signatures, YARA rules, Suricata rules, and attribution-based detections. These updates help defenders spot emerging malware families and reduce analysis time with better context and accuracy.
New Behavior Signatures
162 new behavior-based signatures were added to improve detection across commodity malware, ransomware, loaders, and remote tools.
Highlighted additions include:
- BPFDoor – A stealthy Linux backdoor that receives TCP/UDP/ICMP packets directly via BPF filters. Linked to the Red Menshen group, this malware hides without opening network ports and persists on servers for months.
- Sakura RAT – A rare APT-26 (Deep Panda) tool used in major data breaches. It hides C2 traffic in normal HTTP requests and uses stolen certificates to avoid detection.
- RoamingMOUSE – An Excel dropper used by MirrorFace (APT10) to side-load the Anel backdoor. Targets Japanese and Taiwanese government entities.
- FinalDraft – A cross-platform backdoor that uses Microsoft Graph API and Outlook drafts as C2 channels. It can proxy traffic and inject malicious code.
- PayDay Loader – Delivered via fake VPN/AI websites, this tool silently downloads stealers like Lumma and Poseidon across Windows, macOS, and Android.
- TerraStealer v2 – A stealer from the Golden Chickens toolkit. It grabs browser credentials and crypto wallets and exfiltrates data via Telegram or cloud services. Often paired with TerraLogger.
Other behavior-based detections added for the following threats:
New Tool and Utility Detections
We also added detections for commonly abused remote access tools and packers:
YARA Rule Updates
In May, we released 19 new and updated YARA rules to strengthen static detection and improve malware classification during analysis. These rules help identify emerging threats, improve attribution, and support faster triage, especially when working with evasive samples or reviewing files pre-execution.
Here are the latest additions:
- Packit Stealer – Rule added to detect this custom packer-based stealer known for targeting credentials and crypto assets.
- Lobshot – Detection rule to catch a Windows-based stealer that uses legitimate processes for stealth.
- GoFing – Rule added for this lesser-known info-stealer that focuses on browser and session data.
- Anel Backdoor – Part of the RoamingMOUSE dropper chain; used in targeted attacks.
- Teapot Stealer – New rule to detect this Python-based stealer active in commodity malware campaigns.
- Ralord Ransomware – Detection rule for this rapidly spreading ransomware targeting personal files and enterprise systems.
We also added YARA rules tied to the following threats:
Suricata Rule Updates
To improve detection of network-based threats, we added 756 new Suricata rules in May. These updates expand visibility into malicious domains, phishing infrastructure, and command-and-control traffic seen across live malware samples.
Some highlights include new detections for infrastructure observed in:
- WikiKit Campaign – Detects domain chains used in phishing and payload delivery.
- EvilProxy Campaign – Tracks malicious proxies abusing login flows and multi-factor authentication bypasses.
These rules are automatically applied during analysis and contribute to network-layer IOCs in your reports, making it easier to detect lateral movement, data exfiltration, and malware beaconing early in the infection chain.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with TI Lookup, YARA Search, and Feeds, we equip businesses to speed up investigations, reduce security risks, and improve team’s efficiency.
The post Release Notes: TAXII Support for TI Feeds, New Sandbox Onboarding, and 900+ Detection Rules appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


