57 suspicious Chrome extensions with millions of installs | Kaspersky official blog
Cybersecurity researchers have discovered 57 suspicious extensions in the official Chrome Web Store with more than six million users. The plugins caught their attention because the permissions they request don’t match their descriptions.
What’s more, these extensions are “hidden” — meaning they don’t show up in Chrome Web Store searches, and search engines don’t index them. Installing such a plugin requires a direct link to it in the Chrome Web Store. This post details why extensions can be a dangerous tool in cybercriminal hands, explains the direct threat posed by these recently discovered plugins, and gives tips on how not to fall victim.
Why extensions are dangerous, and how convenience undermines security
We’ve posted many times about why browser extensions shouldn’t be installed thoughtlessly. Browser plugins often help users speed up routine tasks, such as translating information on websites or checking spelling; however, the minutes you save often come at the cost of privacy and security.
This is because, in order to work effectively, extensions typically need access to everything you do in the browser. Even Google Translate asks for permission to “Read and change all your data on all websites” you visit — that is, not only can it monitor what you do online, but also alter any information on a page. For example, it might display a translation instead of the original text. If that’s what an online translator can do, just imagine what a malicious extension with the same access can get up to!
The problem is that most users are unaware of the risks posed by plugins. Whereas executable files from untrusted sources have come to be viewed as potentially dangerous, browser extensions enjoy a broad level of trust — especially if downloaded from an official store.
Too many unnecessary permissions
In the case of the 57 suspicious extensions found in the Chrome Web Store, the main sign of malicious intent was the broad sweep of permissions requested, such as access to cookies — including authentication ones.
In practice, this allows attackers to steal session cookies from victims’ devices, and those session cookies are used to avoid entering a password each time they visit a website. Such cookies also enable scammers to sign in to victims’ personal accounts on social networks or online stores.
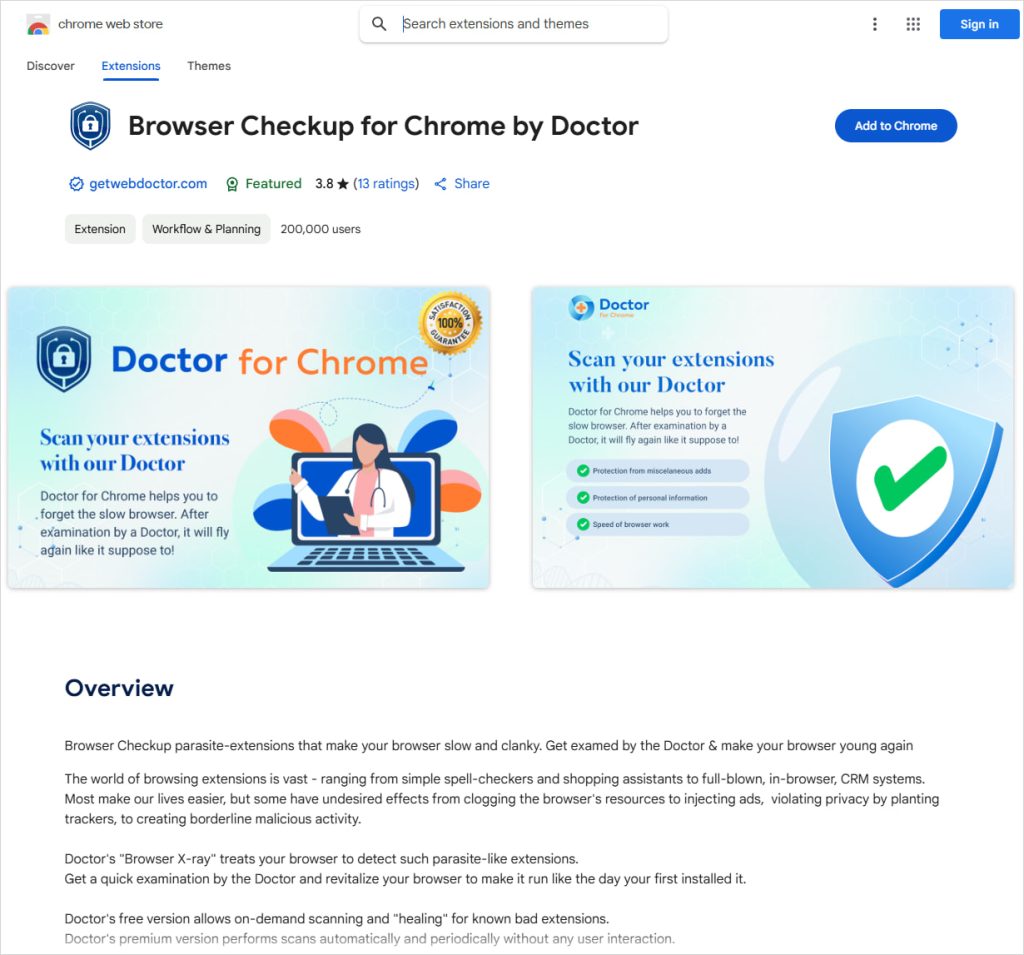
Browser Checkup for Chrome by Doctor is one of the suspicious extensions masquerading as an “antivirus” for the browser. Source
In addition, the permissions requested grant the malicious extensions a host of interesting capabilities, including:
- Tracking user actions in Chrome
- Changing the default search engine and modifying search results
- Injecting and executing scripts on pages visited by users
- Remotely activating advanced tracking of user actions
How the investigation began
Cybersecurity researcher John Tuckner got on the trail of the suspicious extensions after examining the code of one of them: Fire Shield Extension Protection. Tuckner initially spotted this extension because it was published in the official Chrome store as hidden — it didn’t show up in search results and was accessible only via a direct link to the page in the Chrome Web Store.
Note that hidden extensions and apps in official stores are not unheard-of. The big platforms allow developers to hide them from the eyes of ordinary users. Such a practice tends to be the preserve of owners of private corporate software, and intended for use only by employees of a particular company. Another valid reason for hiding a product is when it’s still in the development stage.
However, both these explanations could be ruled out in the case of Fire Shield Extension Protection, boasting 300 000-plus users: a private corporate tool in the development stage with such a user base? Not likely.
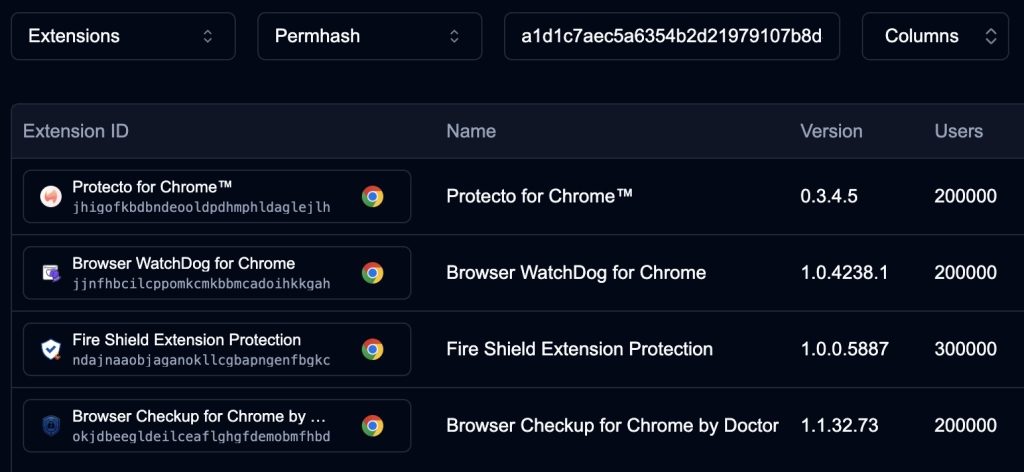
Suspicious extensions with 200–300 thousand users each. Source
What’s more, the plugin features didn’t fit the profile of a highly specialized corporate solution: the description said that Fire Shield checks permissions requested by other extensions installed by the user, and warns about unsafe plugins.
To perform such tasks, it only needed permission to use the chrome.management API, which would allow it to get information about, and manage other installed plugins. But Fire Shield wanted much broader rights, which we’ve listed above with a description of the threats associated with this level of access.
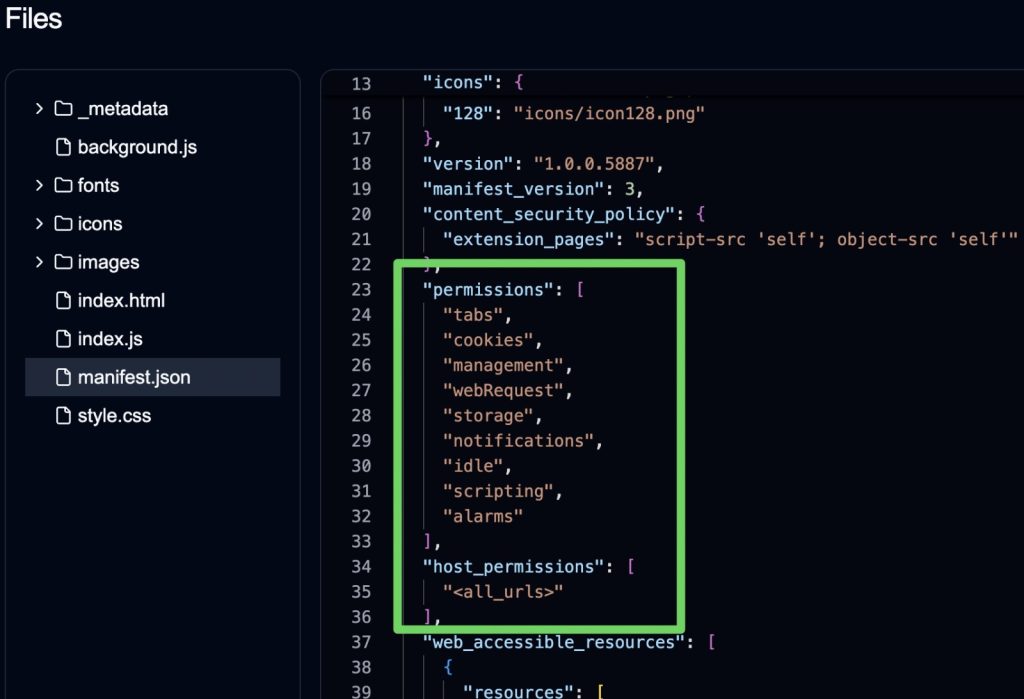
Suspicious plugin wants too many permissions — including access to all sites, cookies, and user activity. Source
57 plugins disguised as legitimate tools
While analyzing Fire Shield Extension Protection, Tuckner found a clue that led to 35 more suspicious plugins. Among the links extracted from the extension code, he noticed a domain called unknow[.]com (seemingly a misspelling of “unknown”). A typo in a domain is a red flag to any cybersecurity expert, since it’s a common trick used by scammers, who hope the victim won’t notice.
Using a special tool, Tuckner found 35 more extensions associated with the same suspicious domain. The names of the extensions also had a lot in common, which confirmed their being connected. And they all requested broad access rights that didn’t match their stated description.
![Extensions associated with the suspicious domain unknow[.]com](https://media.kasperskydaily.com/wp-content/uploads/sites/92/2025/05/29111227/suspicious-chrome-extensions-with-6-million-installs-4-1024x637.jpg)
Extensions associated with the domain unknow[.]com, which kickstarted John Tuckner’s investigation. Source
Most of the suspicious extensions Tuckner found had a fairly standard set of described features: blocking ads, improving search results, and protecting user privacy. In reality, however, many lacked the code to perform these tasks. Some of the extensions all came from the same companies.
Further research led Tuckner to unearth 22 more suspicious plugins, some of which were publicly available (not hidden). Here’s the full list of them — below we give only hidden extensions with the most downloads:
- Fire Shield Extension Protection (300 000 users)
- Total Safety for Chrome (300 000 users)
- Protecto for Chrome (200 000 users)
- Securify for Chrome (200 000 users)
- Choose Your Chrome Tools (200 000 users)
Bottom line
All the evidence points to attackers hiding their malicious plugins to avoid detection by official store moderators. At the same time, such extensions are often distributed through search ads or malicious sites.
The researchers found no instances of detected suspicious extensions stealing user passwords or cookies. After a detailed study of the code, plus a series of experiments, they concluded that extended tracking of user activity doesn’t start immediately but some time after installation of the extension, and can be launched by a command from a remote server.
The nature of their code, the option of remote control, their repeating behavior patterns, and embedded functionality lead us to conclude that the extensions all belong to the same family of spyware or data-stealing programs. As such, we advise that you:
- Check your device for suspicious extensions (see the full list).
- Download only those extensions that you really need; periodically check the list in your browser, and delete any unused or suspicious ones immediately.
- Install a reliable security solution on all your devices to warn you of any danger in good time.
Browser plugins are more dangerous than they look. Read also:
Kaspersky official blog – Read More

