How MSSPs Can Analyze and Investigate Phishing Attacks with ANY.RUN
Phishing attacks have become a pervasive and escalating threat across various industries, notably in finance, manufacturing, and healthcare. For Managed Security Service Providers (MSSPs), the challenge lies in swiftly identifying and mitigating these threats to safeguard client infrastructures and uphold service integrity.
This case study explores how ANY.RUN’s Threat Intelligence Lookup and Interactive Sandbox can empower MSSPs to detect, investigate, and respond to phishing attacks more effectively.
About the Case Study
As an example, we’ll use a payload from Delivr.to (a platform designed to help organizations assess and enhance their email security by simulating real-world threats). We’ll see how Threat Intelligence Lookup and Interactive Sandbox help with:
- Access to real-world phishing samples: Use our extensive threat database to study current phishing samples, simulate email filter bypasses, and prepare more resilient defenses.
- Deep behavior analysis: Examine samples in the sandbox to uncover IOCs, IOBs, IOAs, TTPs, and link attacks to specific malware families and threat actors.
- Targeted threat discovery: Search phishing samples by country, time period, known artifacts.
- Training and awareness: Use real phishing cases to educate your team and clients, improving detection and response readiness.
Let’s begin.
1. Introducing the payload
We have chosen an HTML file Electronic_Receipt_ATT0001.htm from the payload sample library of Delivr.to.
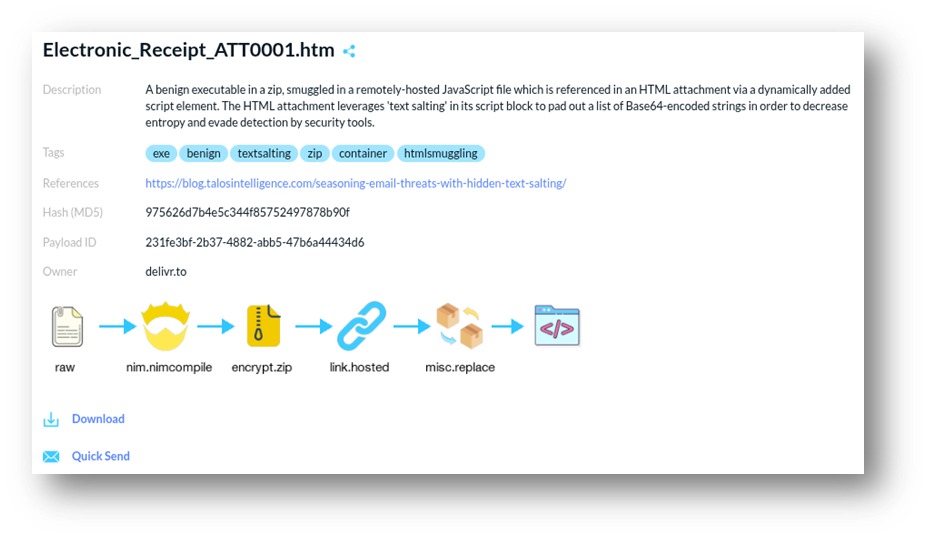
The attachment’s description contains its ID, hash sum, payload chain deployment steps, and the tags describing the attack chain scenario.
Such payloads are meant to be emailed in order to put to test corporate cybersecurity policies. However, a full-fledged understanding of a threat implies not only the detection of email filters bypass, but a full analysis of an activated payload behavior. This is why we shall use ANY.RUN’s TI Lookup to search for this HTML file.
2. Detecting the payload in malware campaigns
Our request to TI Lookup includes the parameter indicating an attached file and the file’s name.
filePath:”Electronic_Receipt_ATT0001″
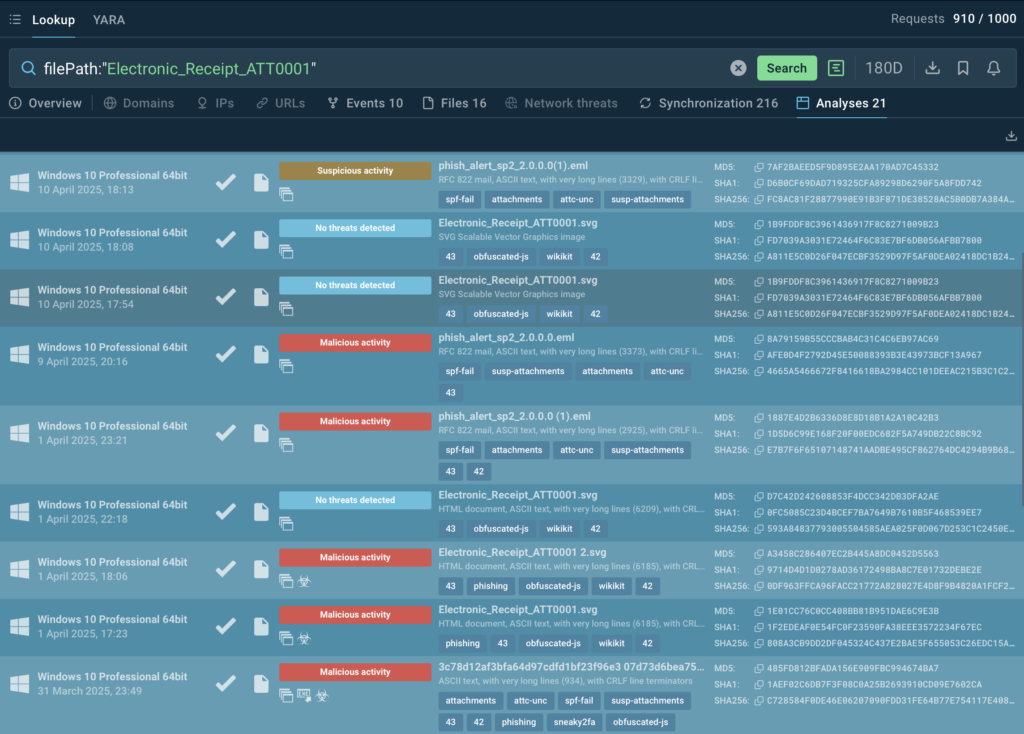
21 malware samples containing this payload have been discovered in TI Lookup at the moment. Besides providing links to the samples and their analyses, TI Lookup highlights the fact that most samples featuring our benign file have been tagged as malicious and attributed to Tycoon phishing kit distributed as Phishing-as-a-Service (PhaaS).
This means that the chosen payload is actually employed in real phishing campaigns.
3. Expanding the malware research
We can also search for other payloads related to Tycoon’s activity. The search query combines the name of the process “outlook.exe” — used when opening emails — and the threat name “tycoon”. As a result, we obtain a broad set of analyses containing various malicious attachment variants associated with Tycoon. This allows us to analyze real-world examples of phishing campaigns and identify recurring delivery patterns.
commandLine:”outlook.exe” and threatName:”tycoon”
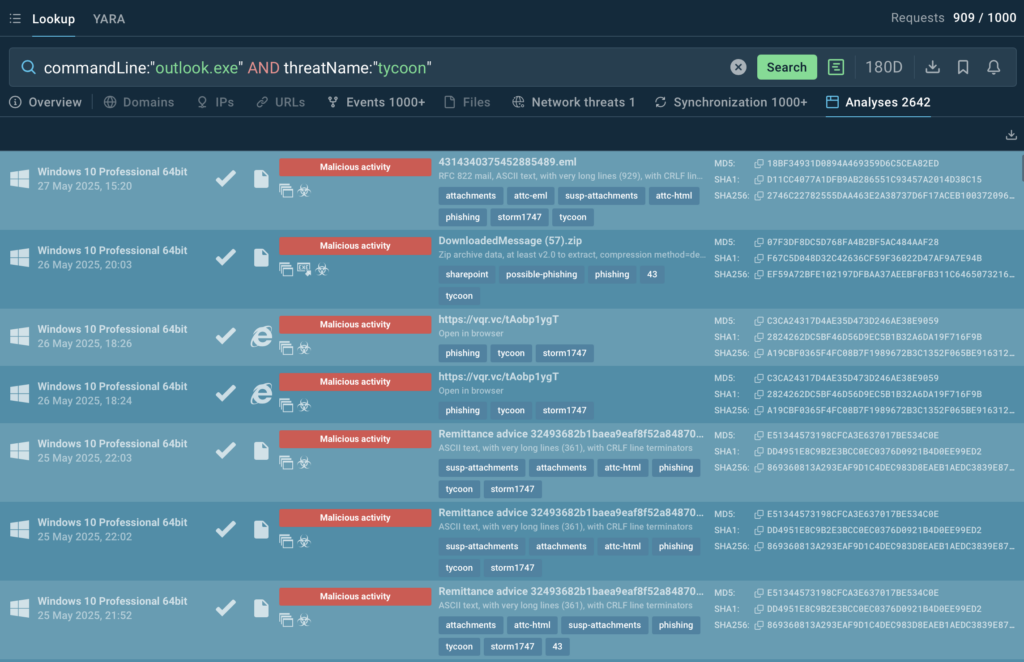
ANY.RUN provides not only attribution to a specific threat but also an overview of the activity landscape — including the number of related samples analyzed by the professional community, the timeframe of the payload’s usage, and the frequency of its appearance. The most recent sample featuring Electronic_Receipt_ATT0001.htm, as of the time of analysis, is dated May 27, 2025, which helps assess the threat’s current relevance.
4. Watching the malware in action
Let’s conduct a more detailed analysis of the payload in the ANY.RUN Sandbox. We’ll view one of the malware analyses.
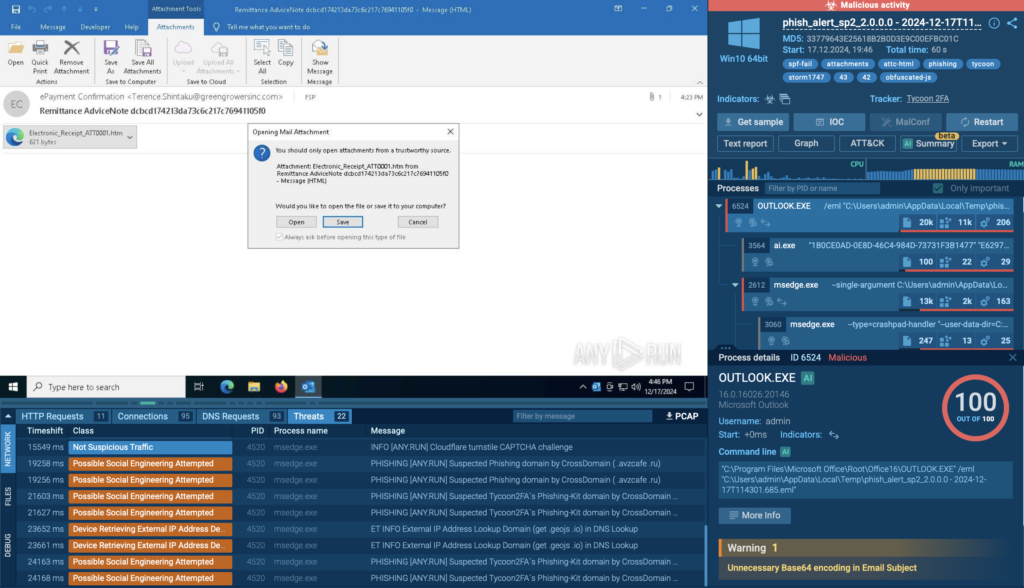
First of all, we can explore malicious email information. The recipient’s address helps identify the likely aim of the attack and the organization it may have been directed against. The email subject is also available, and in some cases, its context—allowing us to assess the social engineering tactics used by the attacker to persuade the recipient to open up the malicious attachment.
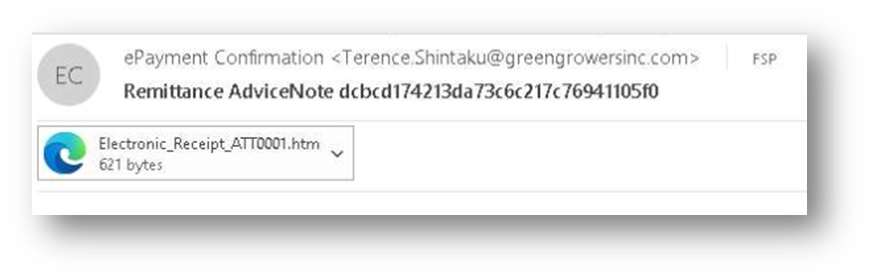
Detailed email header information can be retrieved from the Static Discovering tab:
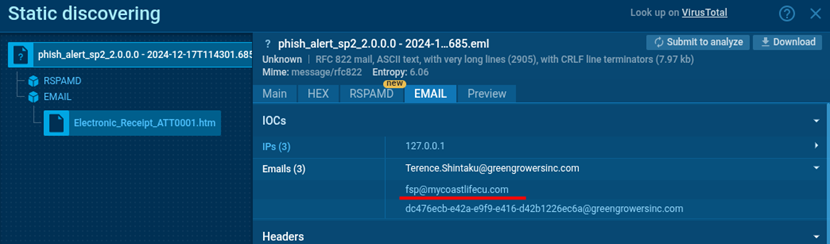
The email recipient’s address — fsp@mycoastlifecu.com — belongs to CoastLife Credit Union, a U.S.-based financial institution, which is confirmed by its presence on the company’s official website.
The use of a legitimate corporate email as the recipient suggests that this attachment was part of an actual phishing campaign targeting employees of financial organizations. This, in turn, indicates the attackers’ likely focus — U.S.-based companies providing banking or financial services.
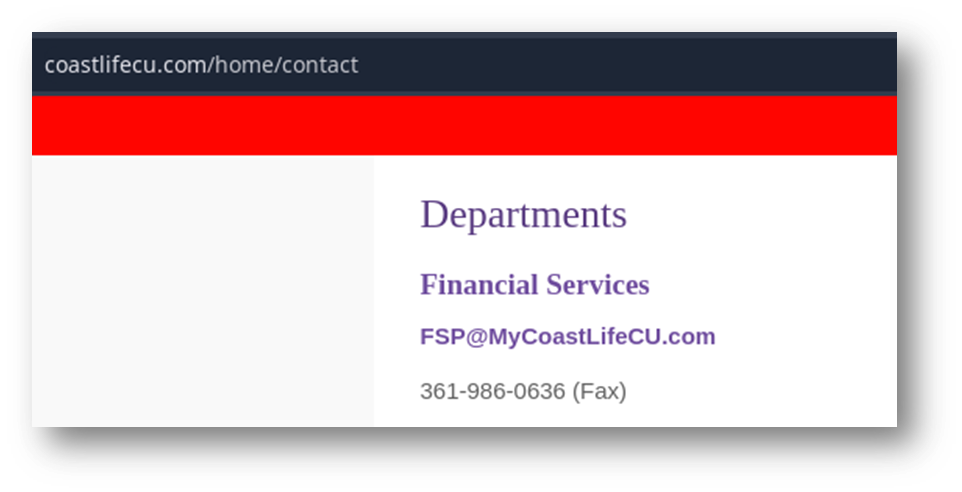
“Authentication-Results” indicates that the email failed SPF verification. Specifically, it shows that the sender’s IP address 141.95.114.239 was not authorized to send emails on behalf of the domain greengrowersinc.com. This data confirms sender spoofing and identifies the specific IP address involved in the email campaign.
5. Performing interactive analysis
On executing the malicious HTML attachment in the ANY.RUN environment, we can observe the phishing page that loads upon its activation. The execution triggers the download of a webpage hosted on the domain nq.jrerqaoiha.ru which looks like a typical part of malicious infrastructure. Besides, a Microsoft authentication page appearing on a .ru domain is highly unusual and suggests a fraudulent scheme.
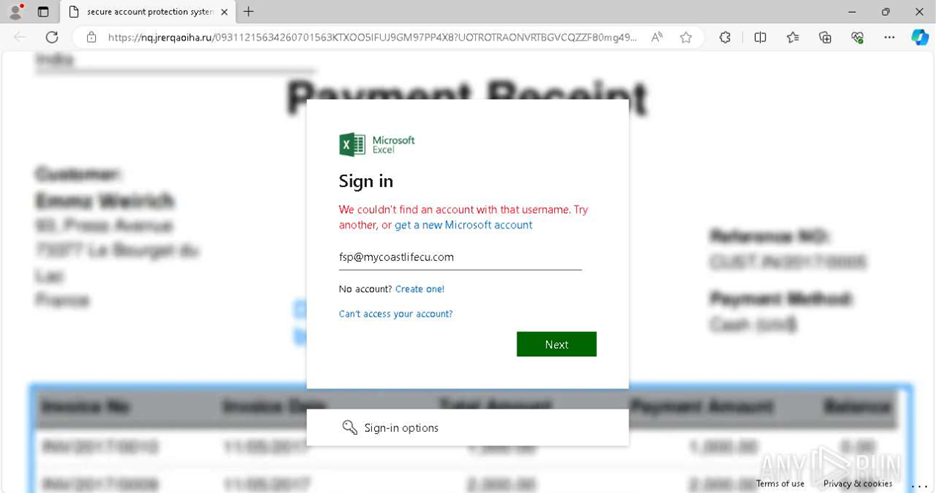
The page mimics a Microsoft Excel login form with official Microsoft branding. The interface prompts the user to enter their credentials, suggesting an attempt at credential harvesting.
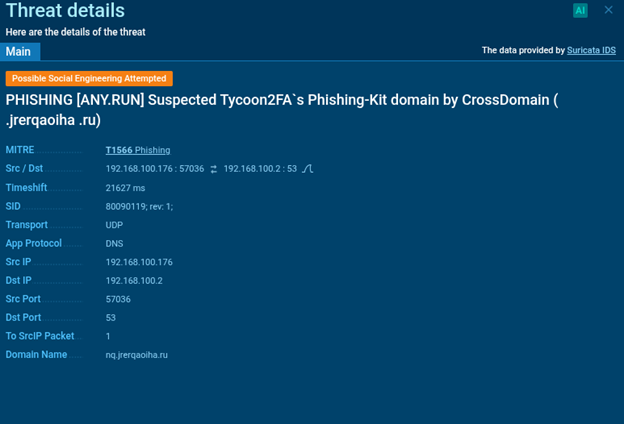
“Network → Threats” tab shows detected network threats. For each recorded activity, you can view detailed detection results based on Suricata IDS, including:
- Signature description
- Protocol used
- Relevant IP addresses and ports
- MITRE ATT&CK technique mapping. In this case, a connection to the domain nq.jrerqaoiha.ru classified as part of the Tycoon2FA phishing kit was linked to T1566 (Phishing) technique and tagged as Potential Social Engineering.
These steps, which cover several analytical aspects critical for cybersecurity professionals, demonstrate how ANY.RUN enables in-depth research of phishing attacks, which is highly relevant for most MSSP companies.
Integrate ANY.RUN’s Solutions in Your MSSP
Integrating ANY.RUN’s Threat Intelligence Lookup and Interactive Sandbox into your MSSP operations equips you with advanced tools to combat phishing and other cyber threats efficiently.
These solutions deliver precise, actionable intelligence to ensure:
- Stronger Client Protection: Proactively investigate and identify malware and phishing attacks using ANY.RUN’s services to take faster actions for safeguarding clients’ infrastructure.
- Accelerated Research: Uncover extensive context on any threat, slashing threat investigation time and enabling faster analyst response.
- Maximized ROI: Speed up triage and response with TI Lookup and the Interactive Sandbox to prevent incidents faster and avoid financial and reputational losses.
- In-depth Threat Analysis: Leverage ANY.RUN’s Interactive Sandbox for real-time detonation and analysis of malicious files and URLs missed by automated systems.
- Streamlined SOC Processes: Take advantage of 2-second searches to reduce triage, investigation, and response times, enhancing team productivity.
Get a 14-day trial of ANY.RUN’s solutions and see how much faster and deeper your threat investigations can be.
Conclusion
ANY.RUN’s Threat Intelligence Lookup and Interactive Sandbox offer robust solutions for analyzing and preventing phishing attacks. The services enable MSSPs to conduct in-depth behavioral analyses of suspicious emails and attachments, identify indicators of compromise, and attribute threats to specific malicious actors. By integrating these capabilities into their security operations, MSSPs can enhance their threat detection and response times, providing clients with proactive defense mechanisms against phishing threats.
The post How MSSPs Can Analyze and Investigate Phishing Attacks with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


