How to Analyze Node.js, Python, Android, and Linux Malware with ANY.RUN
Malware doesn’t stick to one platform or play fair. One day it’s a Python stealer. The next, it’s an Android RAT or a Node.js backdoor quietly pinging its C2. Then it hits Linux, flooding your network with suspicious connections.
Modern threats are unpredictable. They move across systems and languages, often slipping past tools that weren’t built for this level of complexity.
ANY.RUN’s cloud-based sandbox gives companies and SOC teams the flexibility to investigate these threats.
One sandbox where you can analyze, detect, and understand malware and phishing, no matter the OS, architecture, or language. With support for Windows, Linux, and Android, you can choose the environment that fits your sample and see how the same threat behaves across platforms. Just upload, launch, and start investigating.
Let’s see how cybersecurity teams use ANY.RUN to detect and analyze malware written in languages like Python and Node.js, and built to target different systems.
Malware Written in Node.js: Unpacking GootLoader’s Multi-Stage Execution
JavaScript isn’t just for websites anymore, and that’s part of the problem. Threat actors increasingly use JavaScript and Node.js to build droppers, stealers, and loaders that can bypass traditional defenses.
For businesses, these threats often arrive disguised as legitimate files, especially in environments where document sharing and template downloads are common. Once executed, they can trigger multi-stage infections, establish persistence, and pull down additional payloads without leaving obvious traces.
To see how a Node.js-based attack unfolds in the real world, let’s analyze a live GootLoader infection inside the ANY.RUN sandbox.
View analysis of Node.js threat
The attack begins when a user lands on a compromised website while searching for something business-related, like a contract template.
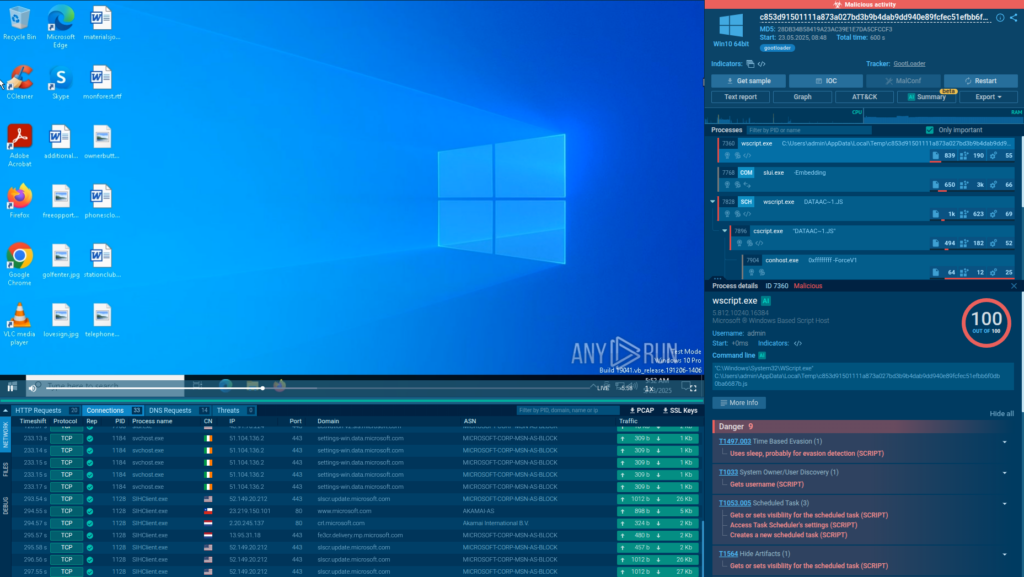
The site delivers a ZIP file containing a trojanized JavaScript file posing as a common library (e.g., jQuery). Once opened, the script runs via wscript.exe, launching a heavily obfuscated payload.
ANY.RUN’s Script Tracer logs and deobfuscates this activity in real time, giving analysts full visibility into each execution step.
We can see all the completed processes of the attack from the right side of the screen, where the process tree is. Here is what we discover here:
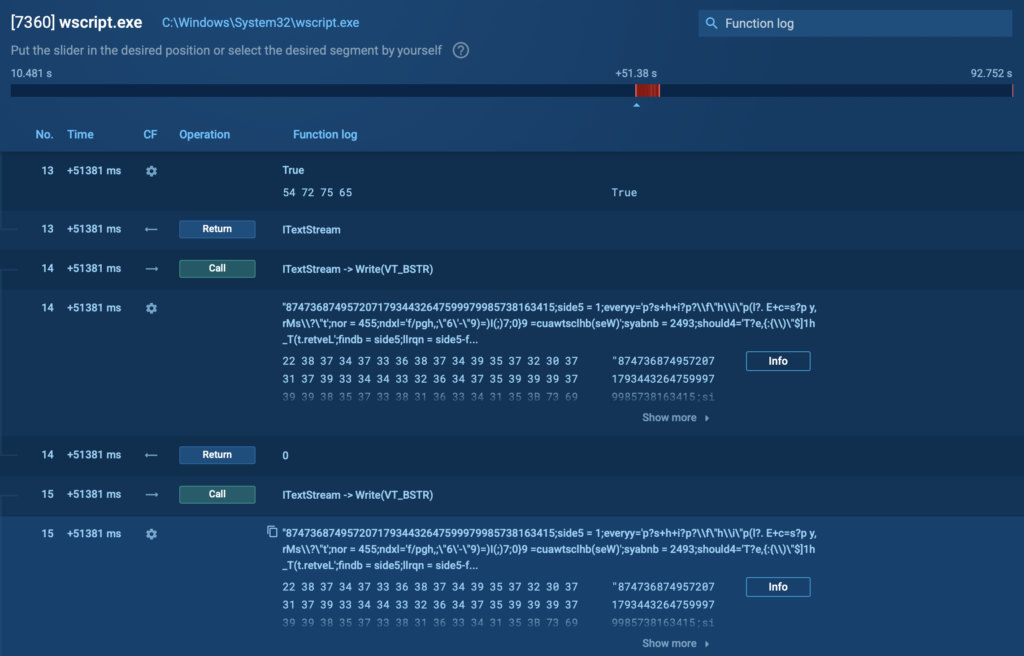
Once executed, the first-stage payload drops a second-stage JavaScript file onto the victim’s system and creates a scheduled task to run it immediately and ensure persistence.
The task launches the second-stage script, initially again through wscript.exe (PID 7828), which then transfers execution to cscript.exe (PID 7896). This script spawns a PowerShell process (PID 8092), which further deobfuscates and runs another PowerShell script.
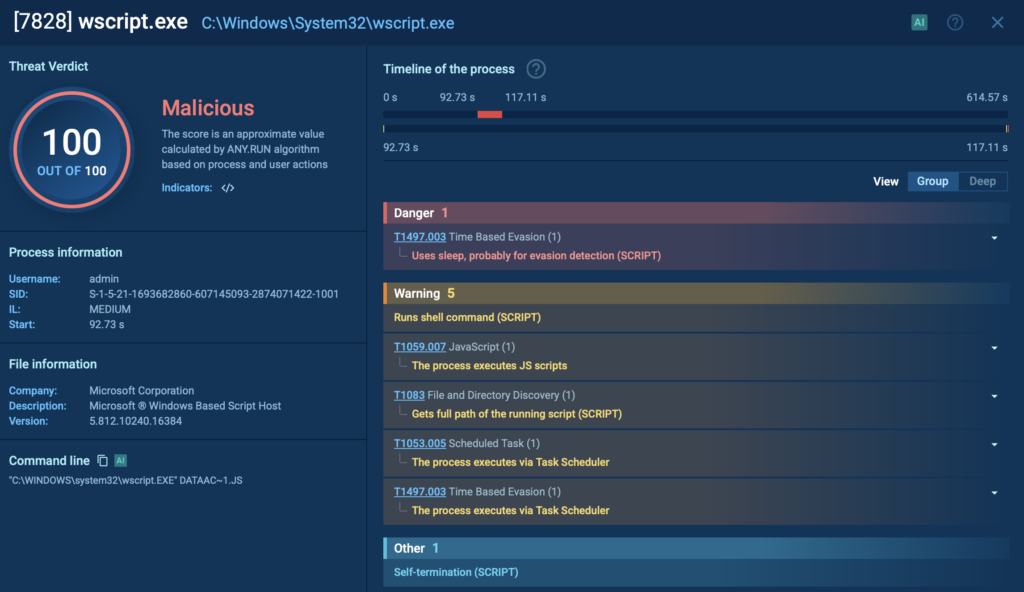
This PowerShell script conducts extensive system reconnaissance, collecting environment variables, OS version, running processes, and more. It communicates with the attacker’s command and control (C2) server by sending compressed and encoded data embedded in HTTP headers, complicating detection.
After establishing communication, the PowerShell script downloads additional payloads, often storing them within the Windows registry to avoid being written to disk. These payloads may include a loader and a secondary component such as a Cobalt Strike Beacon or other post-exploitation tools.
Python-Based Malware: A Stealthy Threat to Business Environments
Python isn’t just a favorite among developers, it’s increasingly used by attackers to create lightweight, modular, and evasive malware. Its readability and cross-platform flexibility make it an ideal choice for building custom stealers, droppers, and loaders that are easy to modify and hard to catch.
For businesses, Python-based malware like Pentagon Stealer poses a real threat. It’s designed to quietly siphon off browser data, crypto wallet credentials, communication tokens, and personal files, often without dropping anything obvious to disk.
To see how it operates in the wild, let’s break down a real sample of the Python variant of Pentagon Stealer in the ANY.RUN sandbox.
View analysis of Pentagon Stealer
The infection starts with an encrypted dropper, which launches a hidden Python script using AES encryption in CBC mode. Once decrypted, the stealer sets up persistence and scans the system for valuable data.
In ANY.RUN’s sandbox, Pentagon’s behavior is clearly exposed across each stage of the infection chain.
Data theft detection: The stealer harvests browser credentials, cookies, and data from apps like Atomic and Exodus. This activity is automatically flagged by the sandbox, giving analysts immediate insight into what data was accessed and how.
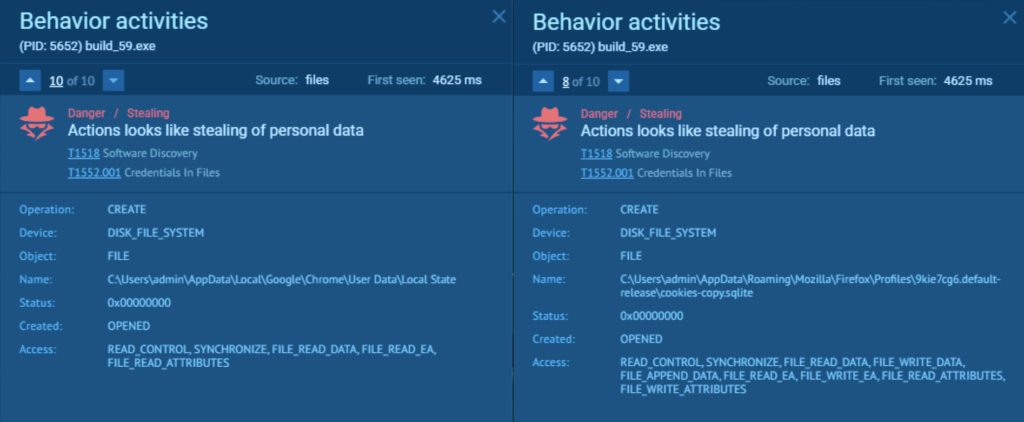
C2 communication: Pentagon communicates with domains like pentagon[.]cy and stealer[.]cy, while variants such as BLX upload stolen data to gofile.io. These indicators are collected and displayed in the IOC section, making it easy to pivot, enrich threat intel, or block infrastructure in other systems.
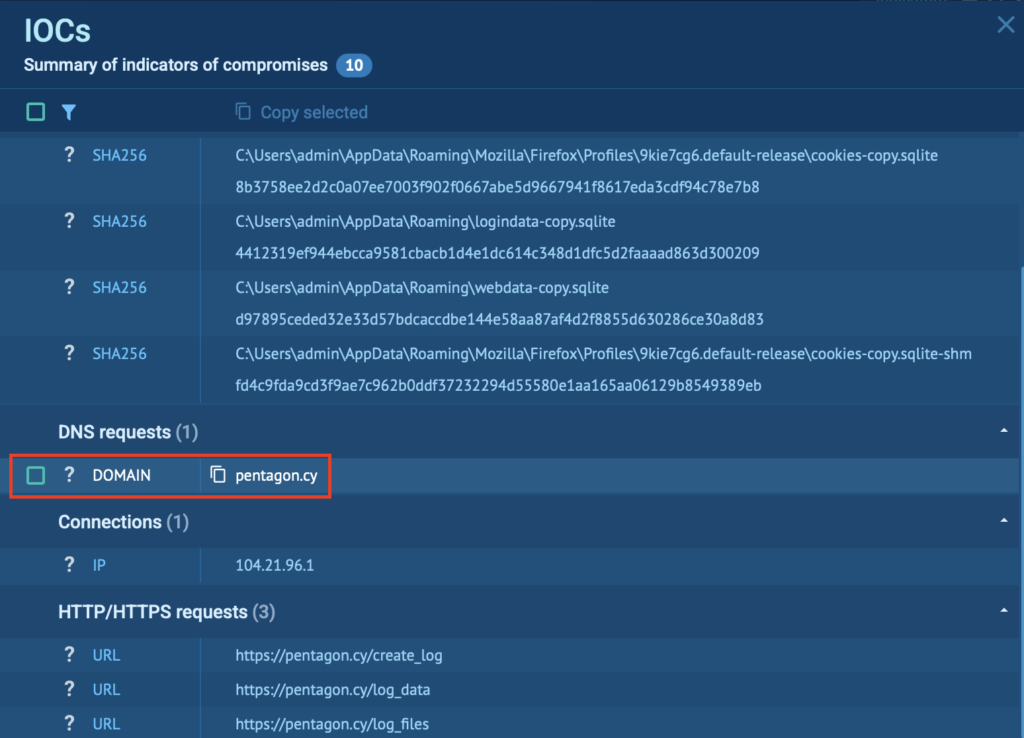
MITRE ATT&CK mapping: The sandbox automatically links observed behavior to ATT&CK tactics and techniques. For Pentagon, this includes:
- Credentials from Web Browsers: The malware extracts saved usernames, passwords, and cookies from Chromium-based browsers, compromising access to email, cloud apps, and internal systems.
- Credentials in Files: It scans user directories for sensitive files, like password.txt or wallet backups, that may contain unprotected login credentials.
- System Information Discovery: Pentagon gathers OS details, hardware info, and environment variables to tailor its behavior or decide whether to proceed with the attack.
- Query Registry: The stealer accesses Windows Registry keys to detect installed software, security tools, and persistence mechanisms.
- Service Stop: It disables security-related services like Windows Defender to avoid detection and ensure uninterrupted operation of follow-up payloads.
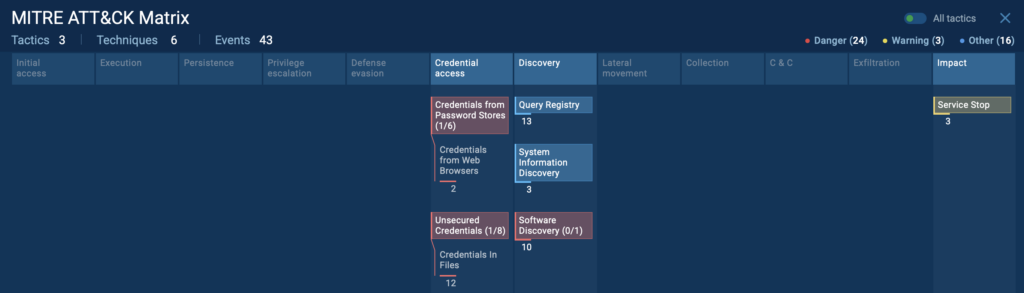
With this mapping, teams get a full picture of the attack’s intent and progression without manually stitching logs together.
Android Malware: How Salvador Stealer Hijacks Banking Credentials
Salvador Stealer is a highly deceptive Android malware disguised as a legitimate banking app. Behind its clean interface lies a full-fledged phishing and data exfiltration machine, designed to steal everything from government ID numbers and personal information to net banking credentials and one-time passwords.
For both individuals and financial institutions, Salvador poses a serious threat, combining technical sophistication with aggressive credential harvesting and real-time data leaks via Telegram and phishing servers.
To uncover the full behavior of Salvador Stealer and observe its actions in real time, we executed the sample inside ANY.RUN’s Android environment.
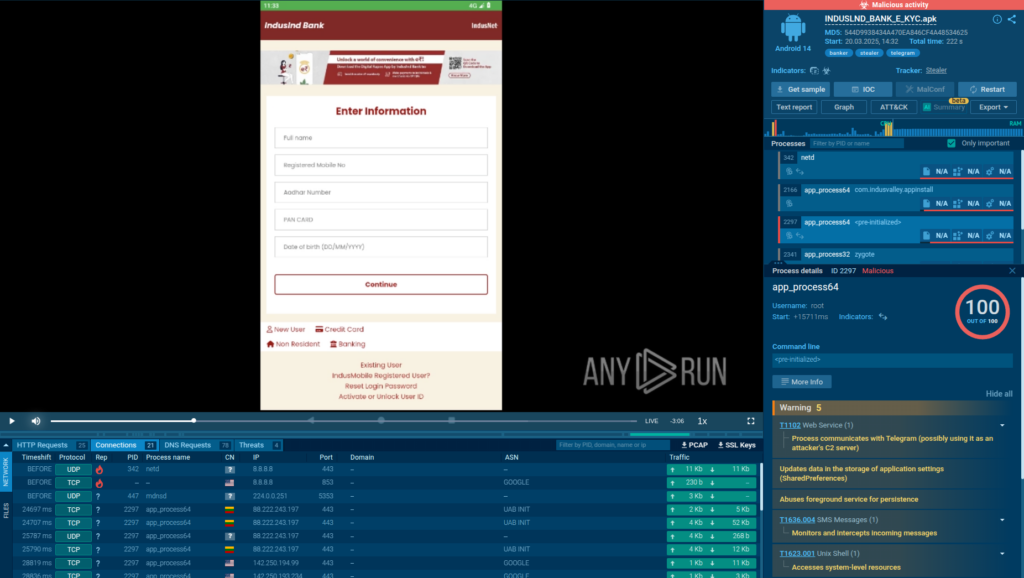
Inside the interactive Android VM, we could clearly observe each stage of the infection, uncovering its tactics, visualizing the phishing interface, and tracing data exfiltration with minimal manual effort.
We see that Salvador Stealer operates in two stages:
- Dropper APK – Silently installs and triggers the second-stage payload.
- Base.apk (Payload) – The actual credential-stealing component.
Dropper APK Behavior
The dropper APK is engineered to install the second-stage malware without the user’s knowledge. It uses specific permissions and intent filters in its AndroidManifest.xml.
Inside ANY.RUN, we observed the dropper launching a new activity immediately after execution, behavior consistent with silent installations.
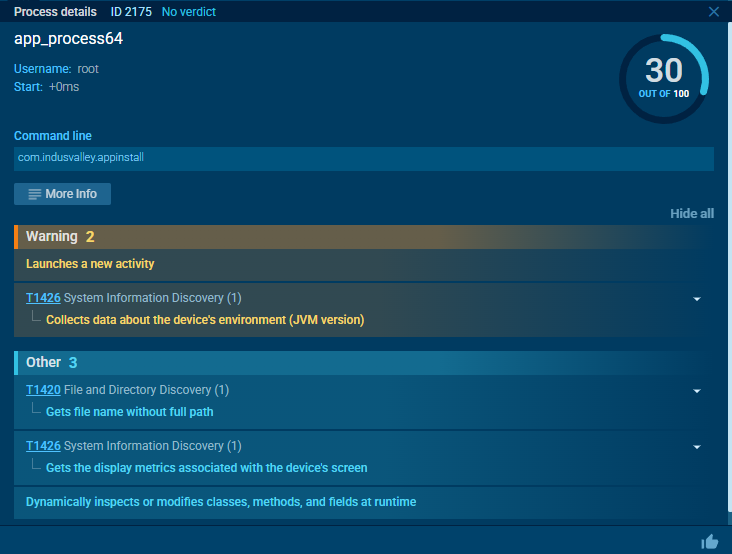
Payload Behavior & Phishing Interface
Once executed, the payload connects to Telegram, used as a Command and Control (C2) channel and triggers the “starts itself from another location” signature, confirming it was deployed via dropper.
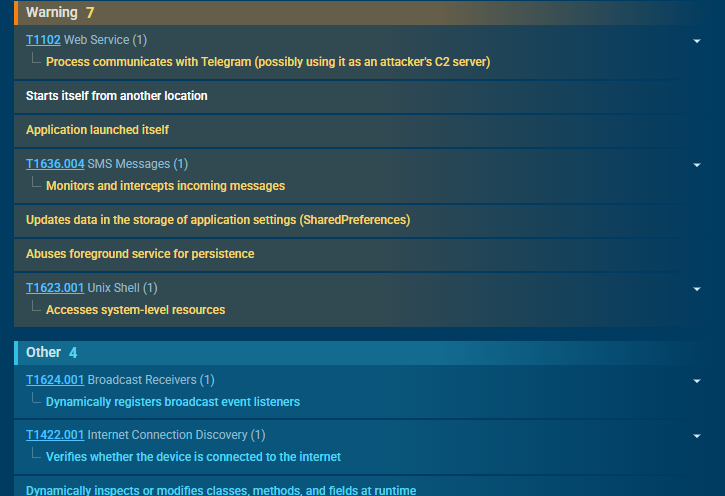
Real-Time Credential Exfiltration
After submission, all user data is immediately exfiltrated to:
- A phishing website controlled by the attacker
- A Telegram bot used as a backup C2 channel
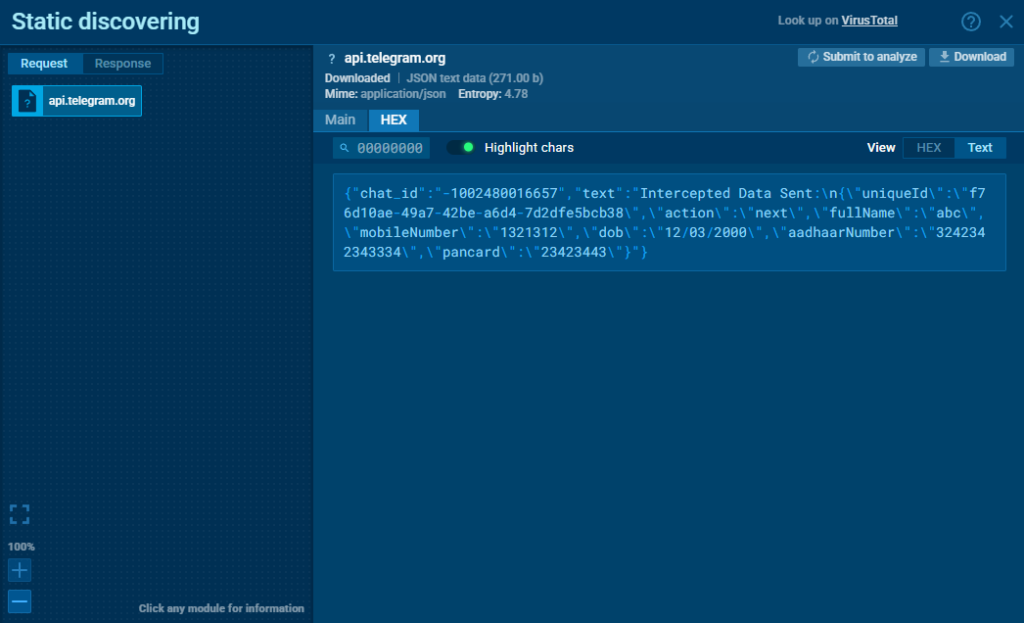
ANY.RUN’s HTTPS MITM Proxy mode captured this behavior clearly, allowing us to inspect the exact HTTP requests, destination URLs, and the contents of the exfiltrated data in plaintext.
This level of visibility is critical when dealing with mobile malware that uses encrypted channels. Teams can immediately verify whether sensitive information was stolen, where it was sent, and how it was packaged, all without reverse-engineering the app or relying on guesswork. It shortens investigation time, boosts detection accuracy, and helps teams extract actionable IOCs in minutes.
Linux Malware: Uncovering Mirai’s Network Flood Inside the Sandbox
While Linux systems are often seen as more secure, they’re far from immune, especially when it comes to IoT-targeting malware like Mirai. Built to infect vulnerable devices with weak or default credentials, Mirai turns compromised routers, IP cameras, and other Linux-based systems into part of a massive botnet used for coordinated DDoS attacks.
In our sandbox session, we ran a Mirai sample inside a Linux virtual environment, revealing exactly how this malware behaves post-infection.
View the full analysis session
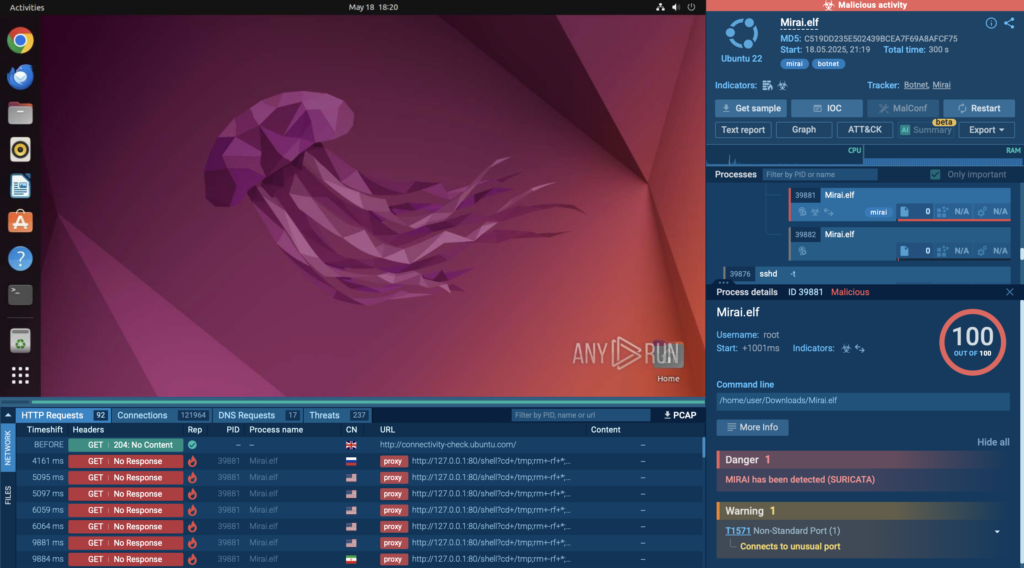
After running the analysis, the malware began scanning the internet for additional targets, sending out a flood of connection attempts to IP addresses across various ports. The spike in outbound activity was visible in the sandbox’s network traffic tab, highlighting Mirai’s worm-like behavior as it looked to propagate further.
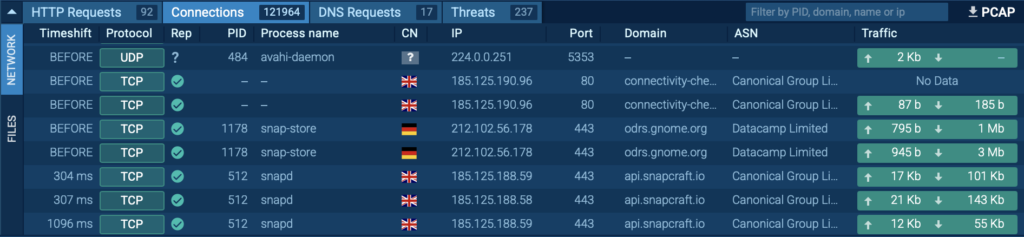
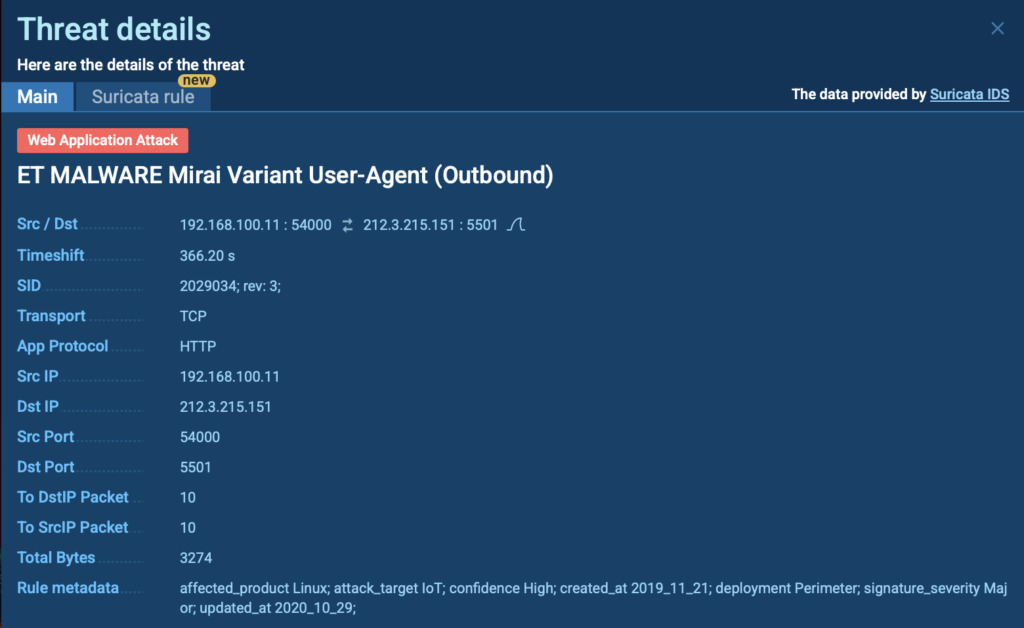
To add another layer of detection, Suricata rules were triggered during the session, automatically flagging the traffic as malicious and confirming the presence of a Mirai variant. This kind of signature-based alert is crucial for quickly validating what you’re looking at without needing to manually inspect every packet.
By analyzing Mirai in ANY.RUN, cyber security teams gain:
- A real-time view of malicious scanning and propagation behavior
- Easy access to network IOCs, including contacted IPs, ports, and protocols
- Automated rule-based detection (Suricata) to validate threats instantly
- A safe environment to test Linux-specific malware, which is often harder to analyze in traditional sandboxes
Whether you’re defending enterprise infrastructure or monitoring connected devices, ANY.RUN’s support for Linux malware analysis makes it easier to uncover threats that operate below the radar of Windows-based defenses.
Going Deeper with Pre-Installed Developer Tools
Not every sample can be cracked with just behavioral analysis, some require deeper inspection, debugging, or code-level investigation. ANY.RUN’s pre-installed development software set is perfect for these purposes.
Available for Windows 10 (64-bit) VMs, this configuration equips analysts with a curated toolkit tailored for reverse engineering, unpacking, and scripting, all without needing to set anything up manually.
By selecting the “Development” software set before starting a session, users instantly gain access to tools like Python, Node.js, x64dbg, Detect It Easy, dnSpy, HxD, DebugView, Process Hacker, and more to investigate complex malware like custom loaders, obfuscated stealers, or scripts in Node.js or Python.
Let’s look at two real-world use cases where this set has been used:
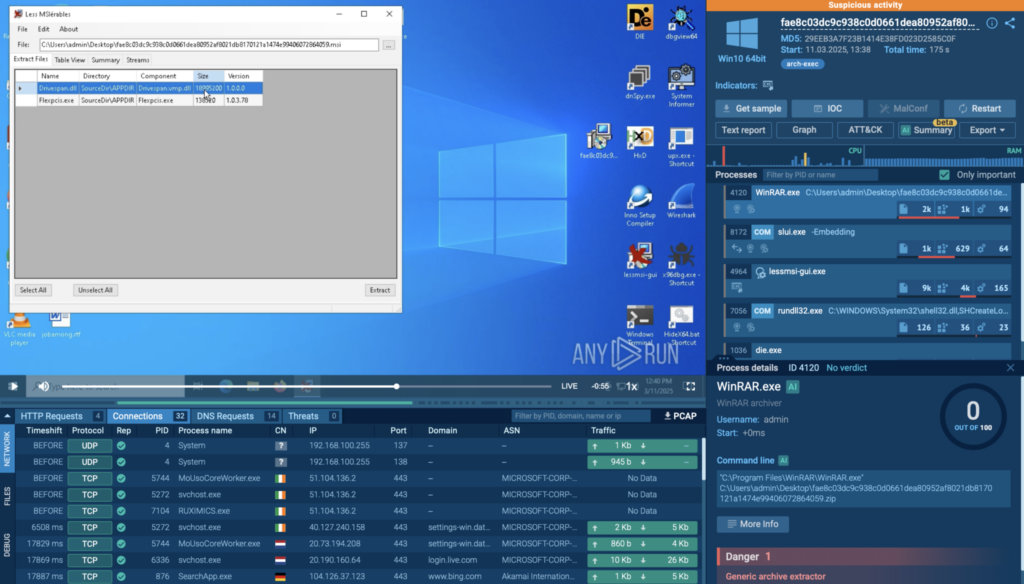
Example 1: Extracting MSI Files Without Execution
Using Lessmsi, analysts can safely unpack .msi files and inspect their contents without running them, critical for avoiding accidental payload execution. In one session, this was combined with Detect It Easy (DiE) to analyze extracted binaries and flag suspicious file signatures or packers.
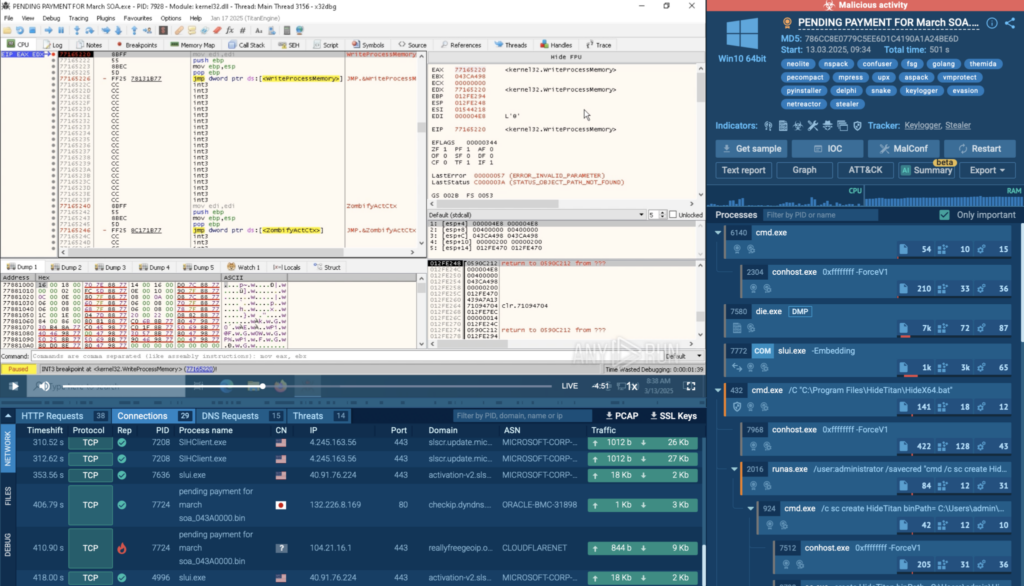
Example 2: Debugging Obfuscated Malware with x64dbg
In another session, x64dbg was used to step through malware execution line by line, helping analysts understand how the sample unpacked itself and interacted with system components; insights that static analysis alone couldn’t reveal.
Having these tools built into the sandbox means your team can dig deeper without wasting time setting things up. It speeds up investigations, helps catch more sophisticated threats, and gets you closer to answers when every minute counts.
A Smarter Way to Investigate Multi-Platform Threats
Modern malware doesn’t limit itself to one environment, and neither should your analysis. From Windows loaders and Python stealers to Android banking malware and Linux-based botnets, today’s threats are built to adapt. The same sample can behave differently depending on where it runs, dropping different payloads, using OS-specific evasion techniques, or communicating with separate C2 infrastructure.
Using a different tool for each platform only slows your team down and increases the risk of missing critical behavior.
ANY.RUN brings everything together in one place. One sandbox where you can detect, investigate, and understand threats, no matter the OS, architecture, or language. Launch analysis sessions across Windows, Linux, and even real Android environments to see how malware acts in each context.
- Faster Investigations Across Platforms: Skip the tool-switching and analyze samples across operating systems, Windows, Linux, and Android, from one streamlined interface.
- Deeper Insight into Complex Samples: Whether it’s a Node.js loader or a Python stealer, trace execution, follow obfuscated logic, and unpack evasive behavior with ANY.RUN’s Script Tracer, Pre-Installed Dev toolkit.
- Clear View of Network Behavior: See how malware communicates, even over encrypted channels or uncommon protocols using HTTPS MITM Proxy and Suricata rule integration.
- Complete Context Behind Every Attack: Understand the full attack chain, from persistence to exfiltration, through mapped behavior, process trees, ATT&CK matrix, and comprehensive logs.
- Cloud-Based, Ready-to-Go Malware Analysis: Skip complex setups. Launch your session in seconds with debuggers, interpreters, and network tools already built in.
- Built for Teamwork and Collaboration: ANY.RUN makes it easy for teams to work together. Share live sessions, tag behaviors, and keep everyone, from analysts to managers, on the same page.
Join ANY.RUN with your business email to get a 14-day trial of advanced features and see how much faster and deeper your malware investigations can be.
The post How to Analyze Node.js, Python, Android, and Linux Malware with ANY.RUN appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More