How scammers exploit genuine Microsoft business notifications
For an email attack to succeed, the first thing cybercriminals need to do is get their messages in front of potential victims. In a recent post, we covered how scammers leveraged notifications from GetShared — a fully legitimate service for sharing large files. Today, we examine another method for delivering malicious emails. The operators behind this scam have learned to insert custom text into genuine thank-you messages sent by Microsoft 365 to its new business subscribers.
A genuine Microsoft email with a nasty surprise inside
The attack kicks off with a legitimate email in which Microsoft thanks the recipient for purchasing a Microsoft 365 Apps for Business subscription. The email does, in fact, arrive from the Redmond tech giant’s legitimate address: microsoft-noreply@microsoft.com. One would be hard-pressed to imagine an email address with a more trusted reputation, so the message easily gets past any email server filters.
One more time, just so we’re clear: this is an honest-to-goodness email from Microsoft. The contents match a typical purchase confirmation. In the screenshot below, the company thanks the recipient for buying 55 Microsoft 365 Apps for Business subscriptions worth a total of $587.95.
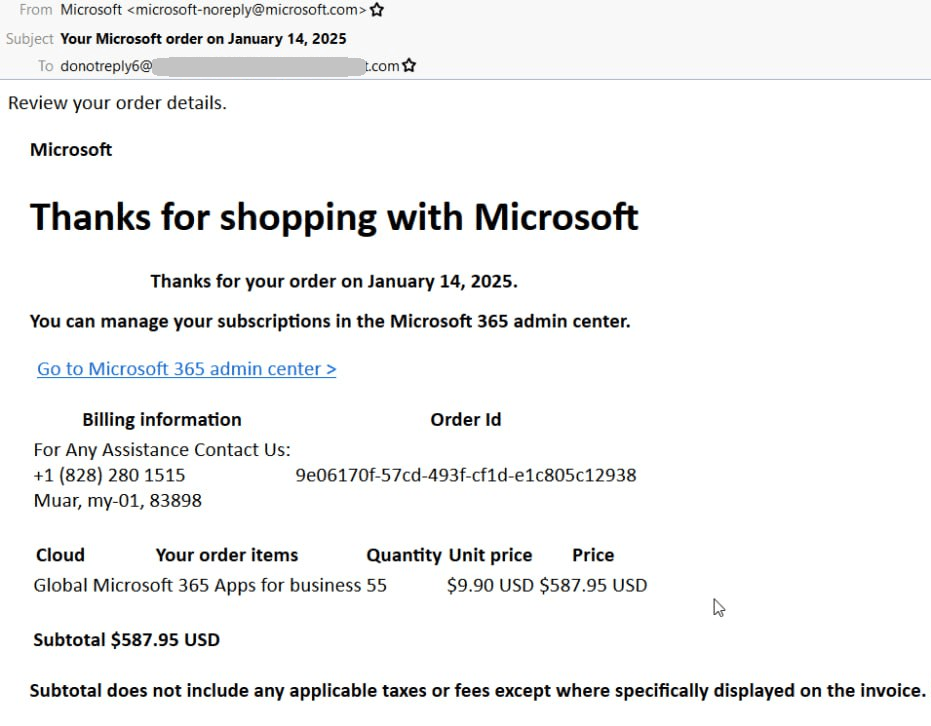
Example of a Microsoft business notification where attackers inserted their message in the Billing information section
The crux of the scam lies in the text attackers add to the Billing information section. Typically, this section contains the subscriber company’s name and the billing address. However, the scammers swap out that information for their own phone number, plus a note encouraging the recipient to call “Microsoft” if they need any assistance. The types of “purchased” subscriptions suggest that the scammers are targeting company employees.
They prey on a common employee fear: making an expensive, unnecessary purchase could cause trouble at work. And since resolving the issue by email isn’t an option (the message comes from a no-reply address), the victim is left with little choice but to call the phone number provided.
Who answers the calls, and what happens next?
If the victim takes the bait and decides to call to inquire about the subscriptions they’ve supposedly purchased, the scammers deploy social engineering tricks.
A Reddit user, who’d received a similar email and called the number, shared their experience. According to the victim, the person who answered the call insisted on installing some support software, and sent an EXE file. The subsequent conversation suggests that the file contained a RAT of some kind.
The victim didn’t suspect anything was amiss until the scammer promised to refund money to their bank account. That was a red flag, as they shouldn’t have had access to the victim’s banking details. The scammer went on to ask the victim to sign in to their online banking to check if the transaction had gone through.
The victim believes that the software installed on their computer was malware that would have allowed the attackers to intercept their login credentials. Fortunately, they recognized the danger early enough and hung up. Within the same thread, other Reddit users reported similar emails containing various contact details.
How scammers send phishing emails from a genuine Microsoft address
How, exactly, the attackers manage to send Microsoft notifications to their victims is still something of a mystery. The most plausible explanation came from another Reddit user, who suggested that the scam operators were using stolen credentials or trial versions to access Microsoft 365. By using BCC or simply entering the victim’s email address when purchasing a subscription, they can send messages like the one shown in the screenshot above.
An alternative theory is that the scammers gain access to an account with an active Microsoft 365 subscription and then use the billing-information resend feature — specifying the target user as the recipient.
Whichever is true, the attackers’ goal is to replace the billing information — the only part of the Microsoft notification they can alter — with their own phone number.
How to protect yourself against such attacks
Malicious actors keep finding new loopholes in well-known, perfectly legitimate services to use for phishing campaigns and scams. That’s why, to keep an organization secure, you need not only technical protections but also administrative controls. Here’s what we recommend:
- Train your employees to spot potential threats early. This process can be automated with an e-learning tool like Kaspersky Automated Security Awareness Platform.
- Install a robust security solution on every corporate device to fend off spyware, remote access Trojans, and other malware.
Kaspersky official blog – Read More