DBatLoader Delivers Remcos via .pif Files and UAC Bypass in New Phishing Campaign
A new phishing campaign is spreading the Remcos Remote Access Trojan (RAT) through DBatLoader. It employs User Account Control (UAC) bypass, obfuscated scripts, Living Off the Land Binaries (LOLBAS) abuse, and persistence mechanisms.
Here’s an analysis of the infection chain, key techniques, and detection tips.
How the Attack Works
To see how the attack unfolds, we analyzed the sample inside ANY.RUN’s Interactive Sandbox.
View full execution and analysis
The attack likely starts with a phishing email containing an archive.
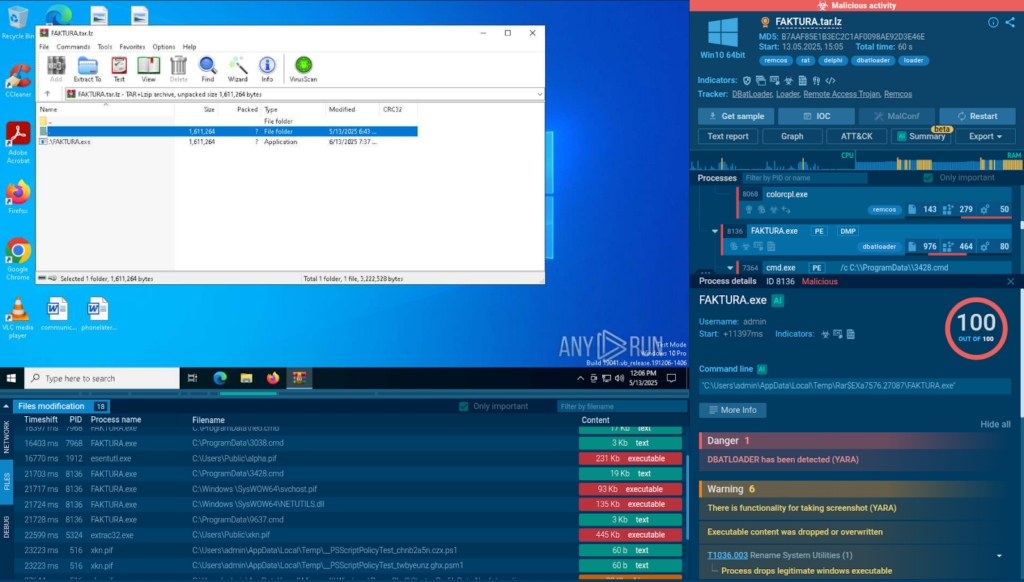
Inside it, there is a malicious executable named “FAKTURA”, which deploys DBatLoader on the system.
Use of .pif Files for Disguise and UAC Bypass
DBatLoader uses .pif (Program Information File) files as a method of disguise and execution.
Originally intended for configuring how DOS-based programs should run in early Windows systems, .pif files have become obsolete for legitimate use. However, they are still executable on modern Windows versions, making them useful for attackers.
Windows treats .pif files similarly to .exe files. When executed, they can run without triggering warning dialogs, depending on system configuration.
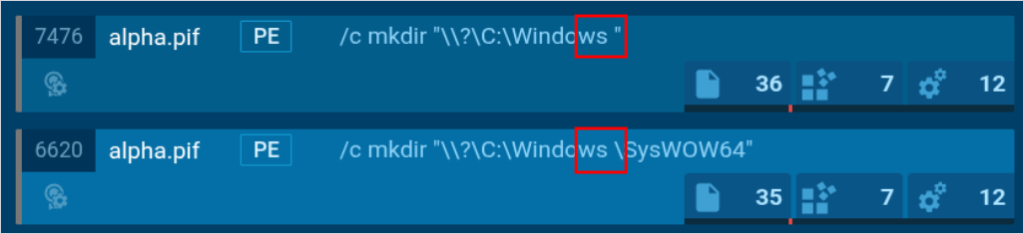
In the analysis, the malicious alpha.pif (a Portable Executable file) bypassed UAC by creating fake directories like “C:Windows “ (note the empty space), exploiting Windows’s folder name handling to gain elevated privileges.
Evasion and Persistence: Ping Command and Scheduled Task
One observed command line uses PING.EXE to ping the local loopback address (127.0.0.1) ten times. While legitimate programs may use this to test network connectivity by sending ICMP echo requests, malware like DBatLoader uses it to introduce artificial delays for time-based evasion.
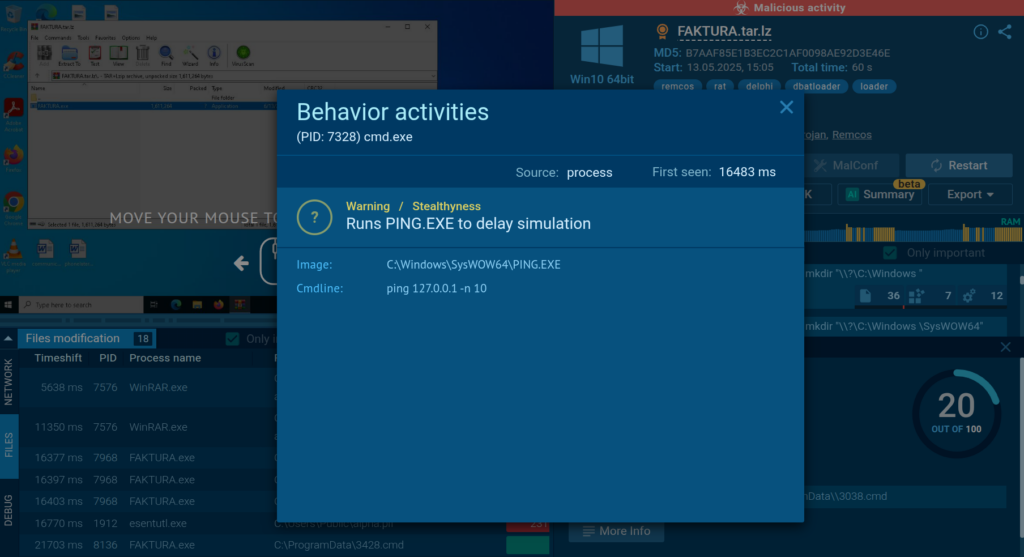
In some cases, this technique can also be repurposed for remote system discovery.
The malicious svchost.pif file launched NEO.cmd through CMD, which then executed extrac32.exe to add a specific path to Windows Defender’s exclusion list, allowing it to evade further detection.
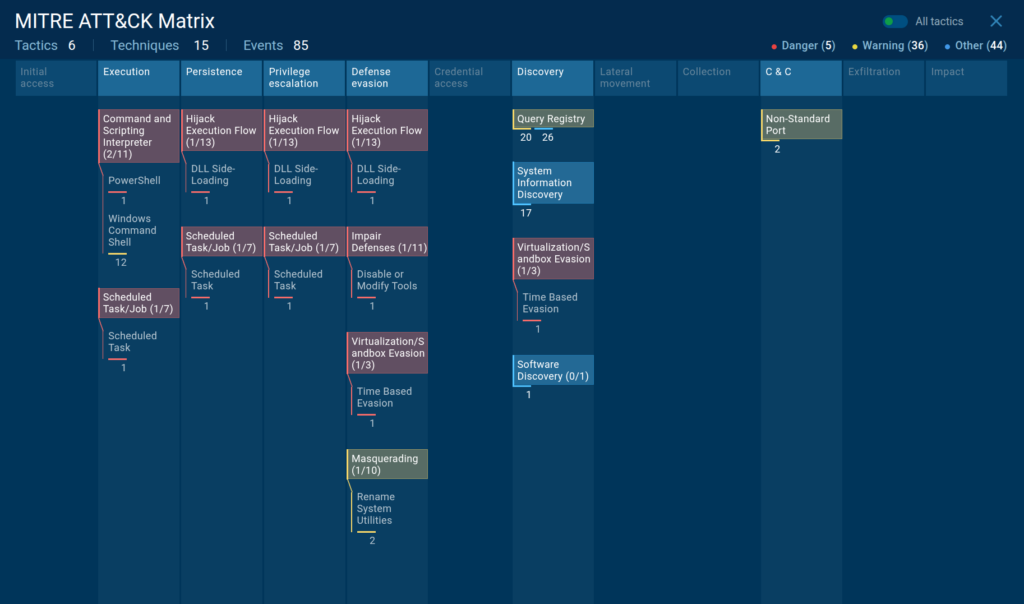
To maintain persistence and survive following reboots, DBatLoader abuses a scheduled task to trigger a Cmwdnsyn.url file, which launches a .pif dropper.
Obfuscation and Remcos Deployment
The loader used .cmd files obfuscated with BatCloak to download and run Remcos.
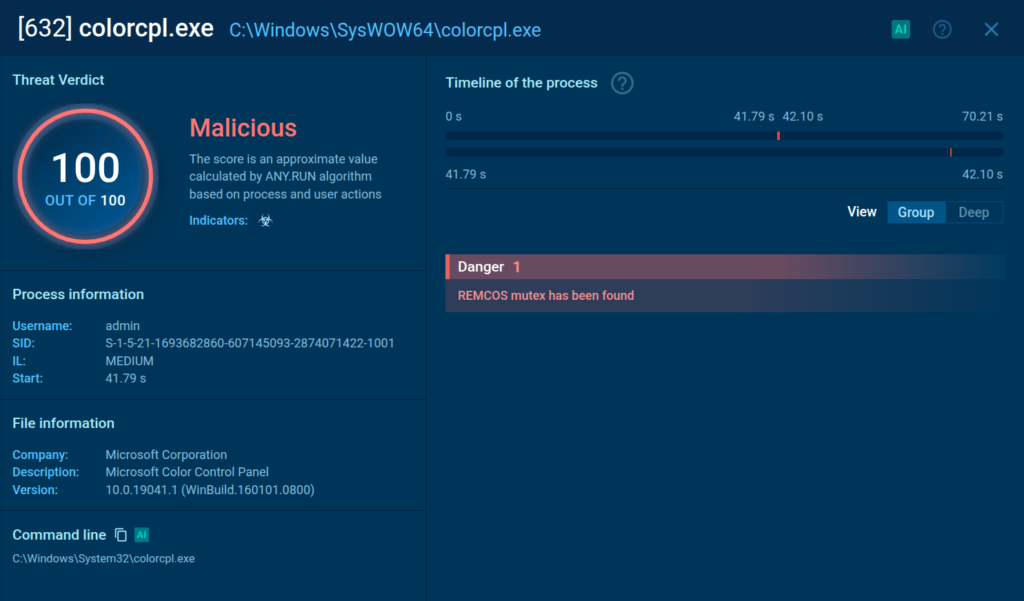
Remcos injects into trusted system processes SndVol.exe, colorcpl.exe or others, varying on each new instance, blending in with the rest of the processes.
Spot Similar Attacks with Proactive Sandbox Analysis
Multi-stage attacks that utilize different means of staying hidden on the system are hard to identify with standard signature-based solutions. The most effective way to ensure detection is to proactively detonate the suspicious files inside the safe, virtual environment of a malware sandbox.
ANY.RUN’s Interactive Sandbox allows security teams to conduct fast and in-depth analysis of malware and phishing attacks to maximize the detection rate. The service offers fully interactive cloud-based VMs supporting Windows, Android, and Linux systems.
- Accelerate Threat Analysis: The sandbox detects malware strains in under 40 seconds, reducing incident investigation time and boosting SOC productivity.
- Keep Your Infrastructure Safe: Analyze suspicious files and URLs in a cloud-based, isolated environment to eliminate the risk of compromising corporate infrastructure.
- Boost Team Collaboration: Configure access levels, track productivity, and coordinate the team’s work on threat analysis.
- Improve Cost-Effectiveness: Minimize financial losses with faster threat analysis and detection that supercharges response and containment.
Analysts can monitor unusual file paths, track processes for unexpected activity, analyze network connections, and, most importantly, manually engage with the system and threats.
The sandbox flags all the malicious behaviors and generates a detailed report with IOCs that can be adapted for detection rules and endpoint security improvement.
About ANY.RUN
Over 500,000 cybersecurity professionals and 15,000+ companies in finance, manufacturing, healthcare, and other sectors rely on ANY.RUN. Our services streamline malware and phishing investigations for organizations worldwide.
- Speed up triage and response: Detonate suspicious files using ANY.RUN’s Interactive Sandbox to observe malicious behavior in real time and collect insights for faster and more confident security decisions.
- Improve threat detection: ANY.RUN’s Threat Intelligence Lookup and TI Feeds provide actionable insights into cyber attacks, improving detection and deepening understanding of evolving threats.
Give ANY.RUN’s services a try in your company with a 14-day trial →
The post DBatLoader Delivers Remcos via .pif Files and UAC Bypass in New Phishing Campaign appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

