Nitrogen Ransomware Exposed: How ANY.RUN Helps Uncover Threats to Finance
The financial sector is heavily targeted by cybercriminals. Banks, investment firms, and credit unions are prime victims of attacks aimed at stealing sensitive data or holding it hostage for massive ransoms. One emerging threat in this landscape is Nitrogen Ransomware, a malicious group discovered in September 2024.
It has since then been notoriously renowned for several successful attacks like that on SRP Federal Credit Union in South Carolina in December 2024. However, there is still a scarcity of information on the group’s TTPs, and this deficit highlights the value of solutions like ANY.RUN’s threat intelligence and malware analysis suite.
Why Financial Sector Is Vulnerable
The numbers don’t lie: in 2024, 10% of all cyberattacks targeted the financial industry, according to reports.
From ransomware to financial fraud and cloud infrastructure exploits, banks and credit unions face all the kinds of threats that there are. The stakes are high — cyberattacks now cost organizations up to $2.5 billion per incident, with ransomware attacks alone spiking to 20–25 major incidents daily, a fourfold increase in financial losses since 2017.
Why is the financial sector so attractive? It’s simple: money and data. Financial institutions hold sensitive customer information and control vast sums of capital, which makes them tempting targets for ransomware groups like Nitrogen. Early detection and adversary tactics analysis are critical to minimizing damage, and that’s where services like ANY.RUN’s Interactive Sandbox and Threat Intelligence Lookup come in handy.
Meet Nitrogen Ransomware
There are traces of Nitrogen from July 2023, but it’s consensual to track it from September 2024. It was initially observed targeting not only finance but also construction, manufacturing, and tech, primarily in the United States, Canada, and the United Kingdom. The routine was to encrypt critical data and demand a ransom to unlock it. One of their confirmed victims, SRP Federal Credit Union, a South Carolina-based institution serving over 195,000 customers, fell prey on December 5, 2024.
Little is known about Nitrogen’s tactics due to limited public data, but a report by StreamScan provides a starting point.
It offers key indicators of compromise and some insights into the methods. Interestingly, Nitrogen shares similarities with another ransomware strain, LukaLocker, including identical file extensions for encrypted files and similar ransom notes. This overlap raises questions about their origins, but deeper analysis is needed to confirm connections.
The StreamScan report is the primary source of information on Nitrogen, detailing a few critical IOCs:
- Ransomware File: A malicious executable with the SHA-256 hash 55f3725ebe01ea19ca14ab14d747a6975f9a6064ca71345219a14c47c18c88be
- Mutex: A unique identifier, nvxkjcv7yxctvgsdfjhv6esdvsx, created by the ransomware before encryption.
- Vulnerable Driver: truesight.sys, a legitimate but exploitable driver used to disable antivirus and endpoint detection tools.
- System Manipulation: Use of bcdedit.exe to disable Windows Safe Boot, hindering system recovery.
While this report is a good start, it’s light on details. This is where ANY.RUN steps in, offering deeper insights through dynamic analysis and threat intelligence enrichment.
ANY.RUN’s Threat Intelligence Versus Nitrogen
Let’s research some of the above-mentioned indicators via Threat Intelligence Lookup to find more IOCs, behavioral data, and technical details on Nitrogen attacks.
1. Tracking the Mutex
Before encrypting files, Nitrogen creates a unique mutex (nvxkjcv7yxctvgsdfjhv6esdvsx) to ensure only one instance of the ransomware runs at a time. Using ANY.RUN’s Threat Intelligence Lookup, analysts can search for this mutex and uncover over 20 related samples, with the earliest dating back to September 2, 2024.
syncObjectName:”nvxkjcv7yxctvgsdfjhv6esdvsx”
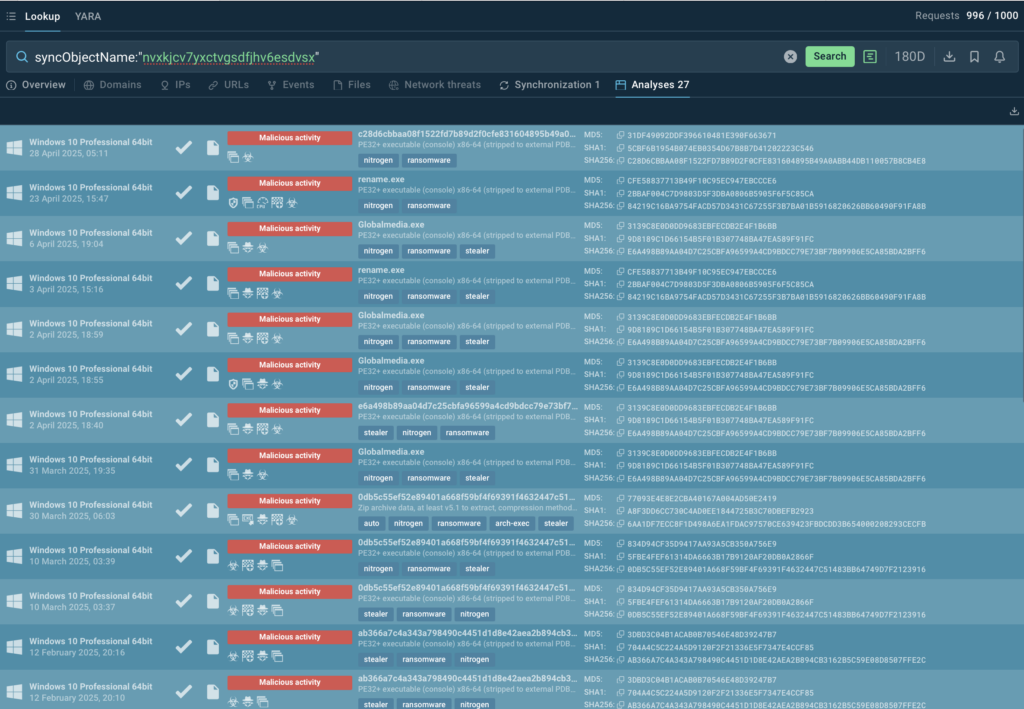
For each sample, an analysis session can be explored to enrich the understanding of the threat and gather additional indicators not featured in public research.
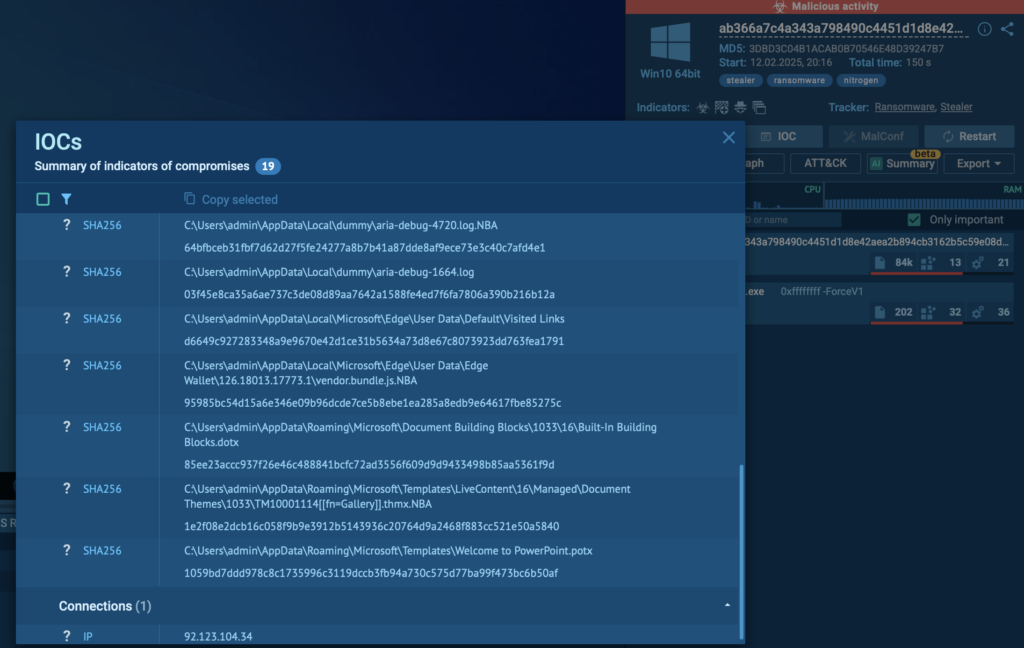
ANY.RUN’s analyses also link Nitrogen to LukaLocker, as both share similar code structures and behaviors. By identifying additional IOCs from related tasks, ANY.RUN helps organizations update their detection systems to block Nitrogen before it strikes.
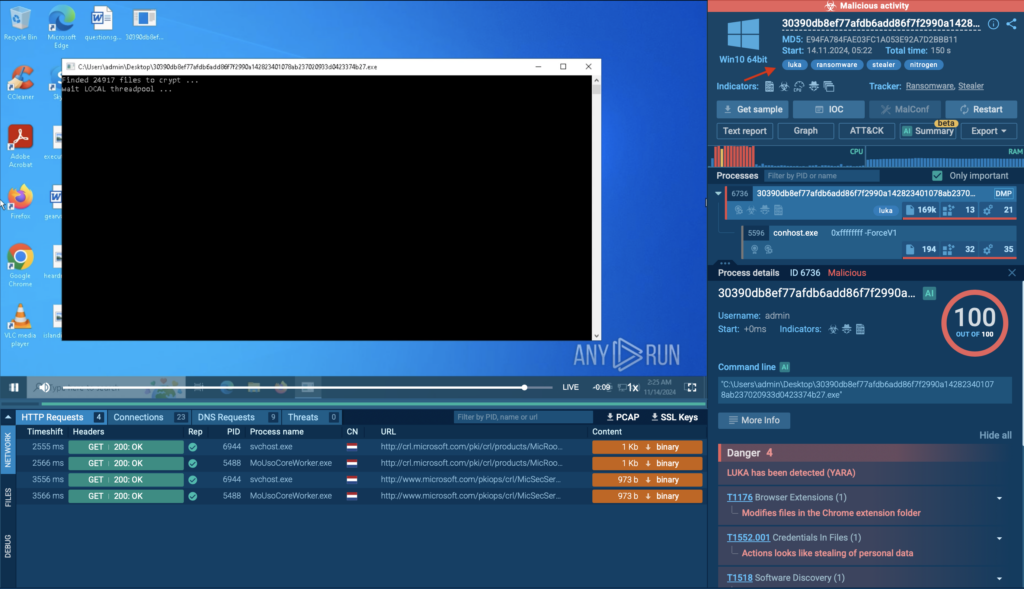
2. Exposing the Vulnerable Driver
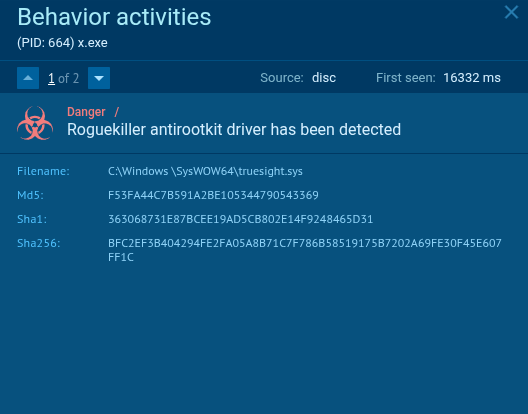
Nitrogen exploits truesight.sys, a legitimate driver from RogueKiller AntiRootkit, to kill AV/EDR processes and thus disable antivirus and endpoint detection tools. This driver, listed in the LOLDrivers catalog, is used by threat actors because it’s not inherently malicious, so it does not trigger standard defenses.
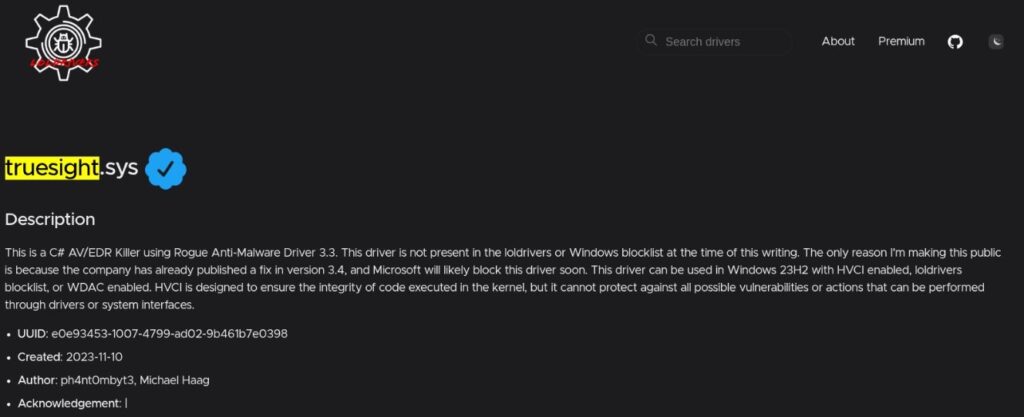
ANY.RUN’s TI Lookup reveals over 50 analyses linked to truesight.sys:
sha256:”Bfc2ef3b404294fe2fa05a8b71c7f786b58519175b7202a69fe30f45e607ff1c”
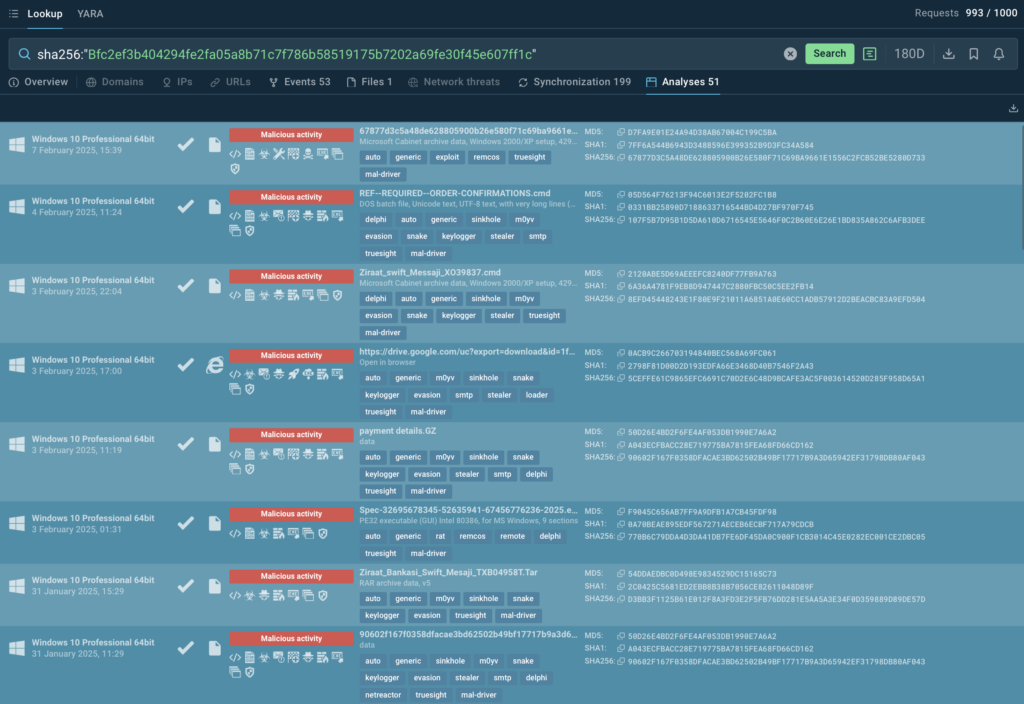
By parsing these analyses, teams see how the driver can be abused, from terminating security processes to evading detection.
The driver’s name as a search query with the “CommandLine” parameter gives a selection of system events involving the driver:
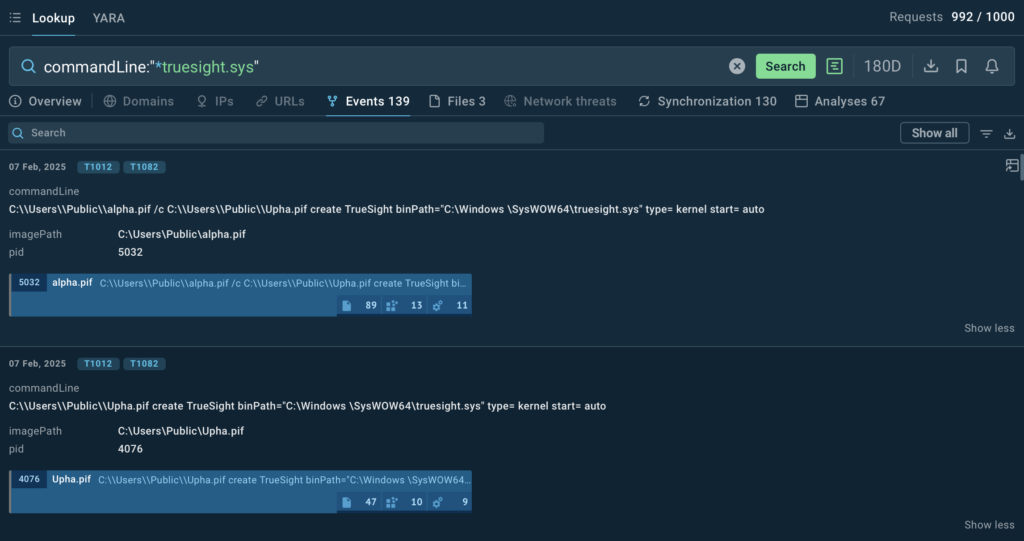
ANY.RUN’s Interactive Sandbox’s ability to detect and flag this activity ensures organizations can block such exploits early.

3. Catching System Manipulation
Nitrogen uses the Windows utility bcdedit.exe to disable Safe Boot, a recovery mechanism that could otherwise help restore an infected system. As the StreamScan report says:
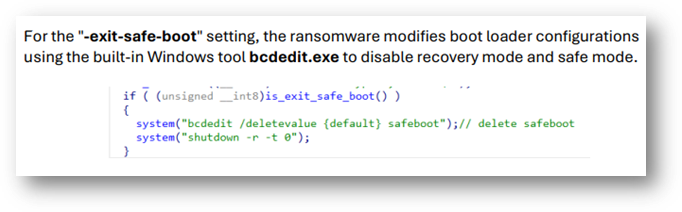
ANY.RUN allows analysts to use YARA rules to search for this behavior, identifying samples that tamper with system settings.
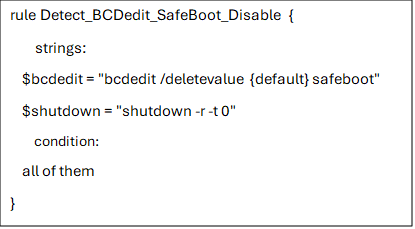
A simple YARA search in ANY.RUN’s TI Lookup returned several files linked to this tactic, each with associated analysis sessions that reveal additional IOCs.
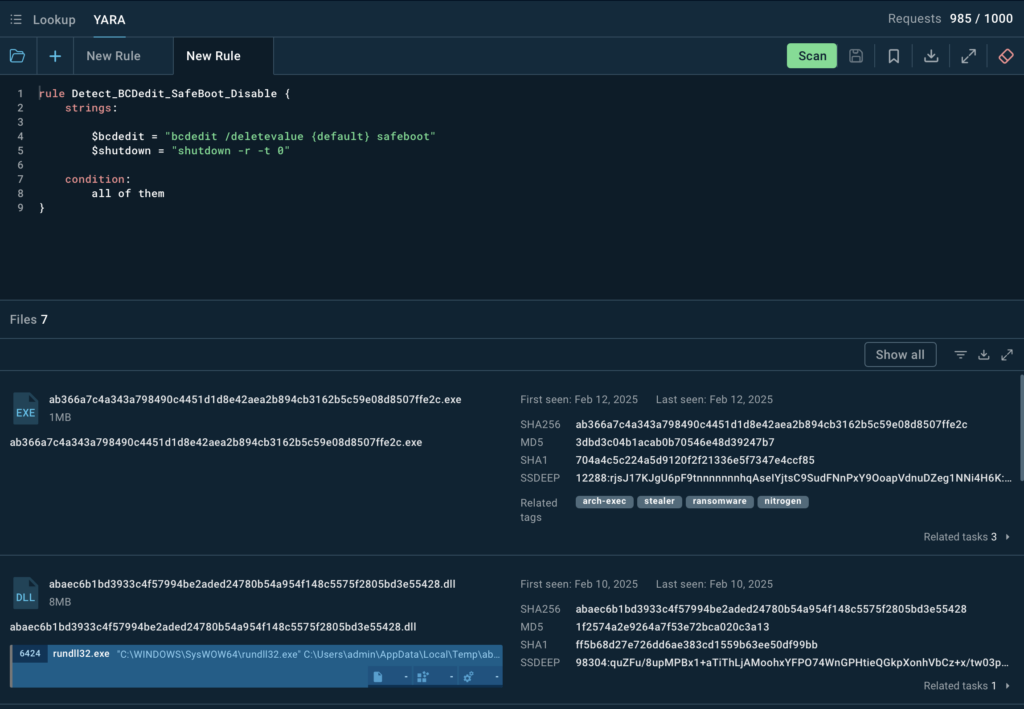
By integrating these IOCs into SIEM or EDR systems, organizations can detect and block attempts to modify Windows boot settings before encryption begins, stopping Nitrogen in its tracks. To defend against threats like Nitrogen, security teams should:
- Monitor for unusual use of PowerShell, WMI, and DLL sideloading.
- Block known malicious infrastructure and domains.
- Educate employees about phishing and social engineering tactics.
- Use threat intelligence services to proactively hunt for related IOCs and TTPs.
Conclusion
The financial sector’s battle against ransomware is far from over, but solutions like ANY.RUN are leveling the playing field. By dissecting Nitrogen Ransomware’s tactics —system manipulation, driver exploitation, and mutex creation — ANY.RUN empowers cybersecurity teams to detect, analyze, and respond to the threat faster. Its dynamic analysis capabilities let analysts observe malware in action, from file encryption to system components abuse, in a safe sandbox environment. Meanwhile, its TI Lookup enriches threat data by providing additional indicators, uncovering connections to other attacks, campaigns, and techniques.
Nitrogen is a reminder that today’s cyberattacks are not only persistent — they’re precise. As Nitrogen and similar groups continue to evolve, staying proactive with dynamic analysis and enriched threat intelligence is the key to keeping financial institutions safe, to avoid direct capital losses, reputation damage.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post Nitrogen Ransomware Exposed: How ANY.RUN Helps Uncover Threats to Finance appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
