Mamona: Technical Analysis of a New Ransomware Strain
Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and threat intelligence analyst. You can find Mauro on X.
These days, it’s easy to come across new ransomware strains without much effort. But the ransomware threat landscape is far broader than it seems, especially when you dive into the commodity ransomware scene. This type of ransomware is developed by a group that sells a builder to third-party operators, with no formal agreement or contract between them, unlike the more organized Ransomware-as-a-Service (RaaS) model.
On this side of the fence, we see countless new products appearing on the cybercrime shelf every day. They’re much harder to track, as victims, strains, infrastructure, and builds often have no direct connection to each other.
Let’s take a look at one of them: Mamona Ransomware. Never heard of it? That’s probably because it’s a new strain but despite its short lifespan, it has already made some noise. It’s been spotted in campaigns run by BlackLock affiliates (who are also linked to Embargo), one of its online builders was exposed and later leaked on the clearnet, and the DragonForce group even stole the main website’s .env file, publishing it on their Dedicated Leak Site on Tor under the headline: “Is this your .env file?”
So, let’s find out what this is all about.
Mamona Ransomware: Key Takeaways
- Emerging threat: Mamona is a newly identified commodity ransomware strain.
- No external communication: The malware operates entirely offline, with no observed Command and Control (C2) channels or data exfiltration.
- Local encryption only: All cryptographic processes are executed locally using custom routines, with no reliance on standard libraries.
- Obfuscated delay technique: A ping to 127[.]0.0[.]7 is used as a timing mechanism, followed by a self-deletion command to minimize forensic traces.
- False extortion claims: The ransom note threatens data leaks, but analysis confirms there is no actual data exfiltration.
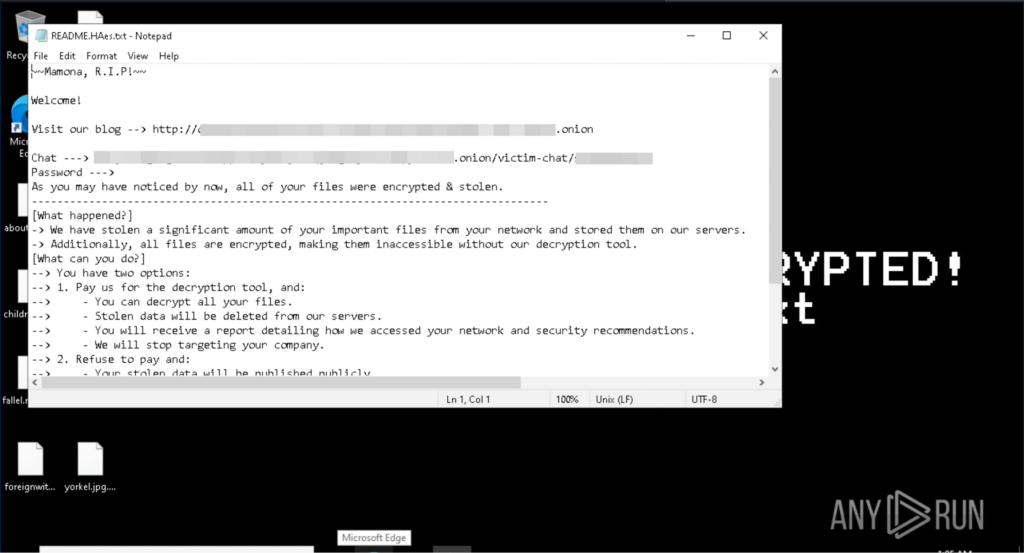
- File encryption behavior: User files are encrypted and renamed with the .HAes extension; ransom notes are dropped in multiple directories.
- Decryption available: A working decryption tool was identified and successfully tested, enabling file recovery.
- Functional, despite poor design: The decrypter features an outdated interface but effectively restores encrypted files.
This emerging ransomware can be clearly observed within ANY.RUN’s cloud-based sandbox environment. You can explore a full analysis session below for a detailed visual breakdown.
View analysis session with Mamona ransomware
Offline and Dangerous: Mamona’s Silent Tactics
When you hear about ransomware, your first educated guess is usually a threat that comes from the outside, exfiltrates sensitive files, encrypts the local versions, and then demands a ransom. Pretty much the full ransomware cycle. But this one is different. it has no network communication at all, acting surprisingly as a mute ransomware. So far, the only connections it attempts are local, plus one to port 80 (HTTP), where no data is actually sent or received.
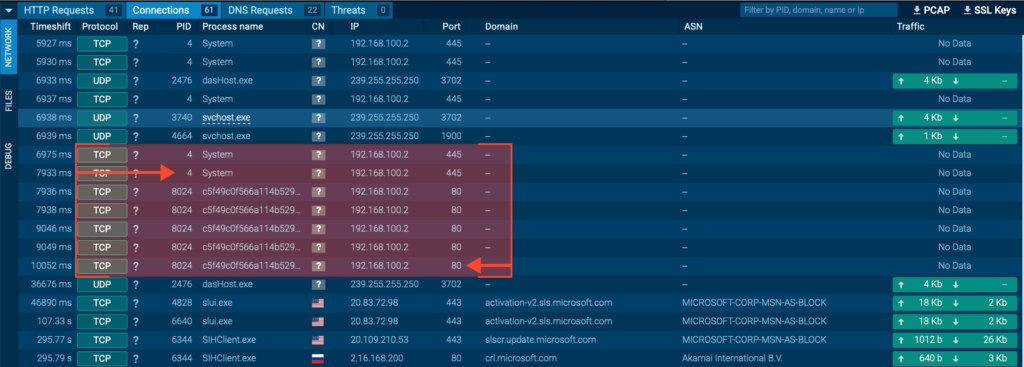
This lack of network communication strongly suggests that the encryption key is either generated locally on the fly or hardcoded within the binary itself. In the medium term, this increases the chances of reverse-engineering a working decrypter which, fortunately, we already have in this case.
A closer look reveals that the encryptor relies entirely on homemade routines. There are no calls to standard cryptographic libraries, no use of the Windows CryptoAPI, and no references to external modules like OpenSSL. Instead, all cryptographic logic is implemented internally using low-level memory manipulation and arithmetic operations.
One key routine is located at internal offsets such as 0x40E100. This function is repeatedly called after pushing registers and buffer pointers to the stack and exhibits patterns typical of custom symmetric logic.
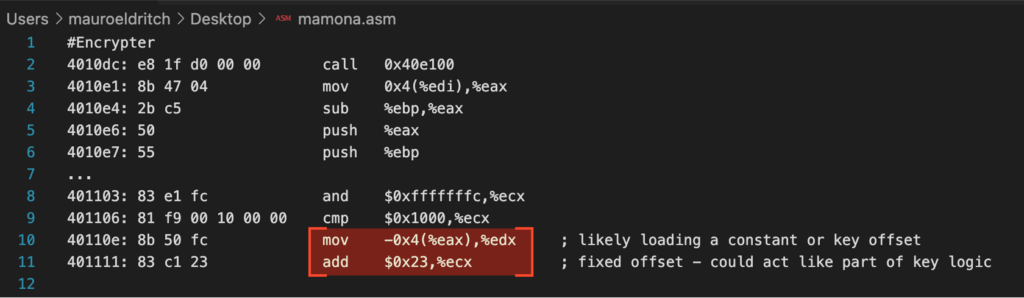
The symmetric structure reinforces the hypothesis of a static or trivially derived key, making Mamona a strong example of commodity ransomware that prioritises simplicity over cryptographic robustness.
Still, just because this malware doesn’t communicate with external hosts doesn’t mean it can’t cause serious local damage. Let’s take a closer look.
How Mamona Executes Its Attack
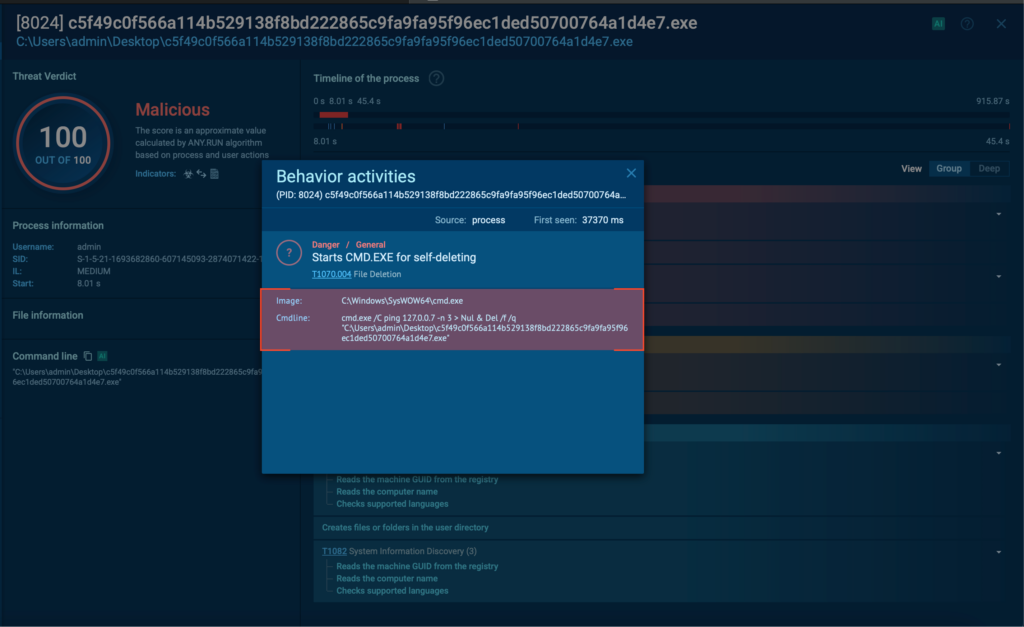
The first thing Mamona does is execute a ping command as a crude time delay mechanism, chaining it with a self-deletion routine via cmd.exe.
The use of ping 127[.]0.0[.]7 is a classic trick in commodity malware: instead of using built-in sleep APIs or timers (which can be flagged by behavioural monitoring), the malware sends ping requests to a loopback IP address, effectively pausing execution.
Interestingly, it uses 127[.]0.0[.]7 instead of the more common 127[.]0.0[.]1, likely as a basic form of obfuscation. It’s still within the reserved localhost block (127[.]0.0[.]0/8) but may bypass simple detection rules that specifically target 127[.]0.0[.]1.
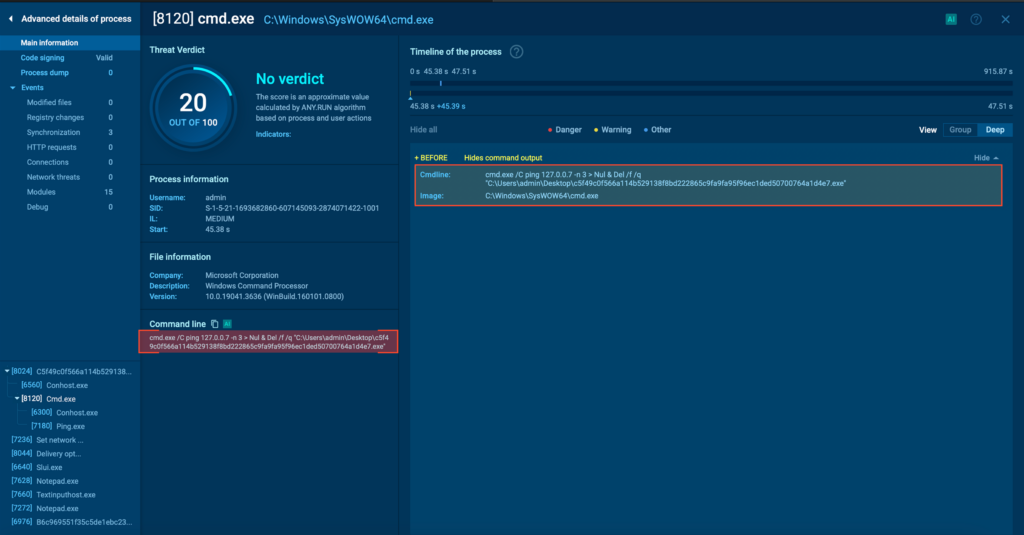
A crude yet useful delay mechanism
Once the short delay is complete, the second part of the command attempts to delete the executable from disk using Del /f /q. Since a process can’t delete itself while it’s still running, this whole sequence is executed in a separate shell process. This is a simple but effective form of self-cleanup, aimed at reducing forensic traces post-infection.
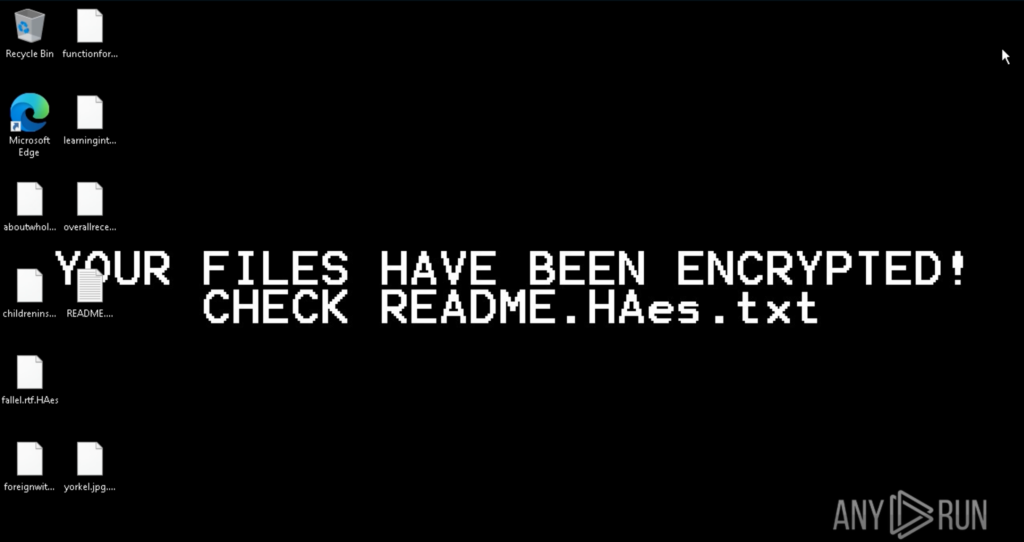
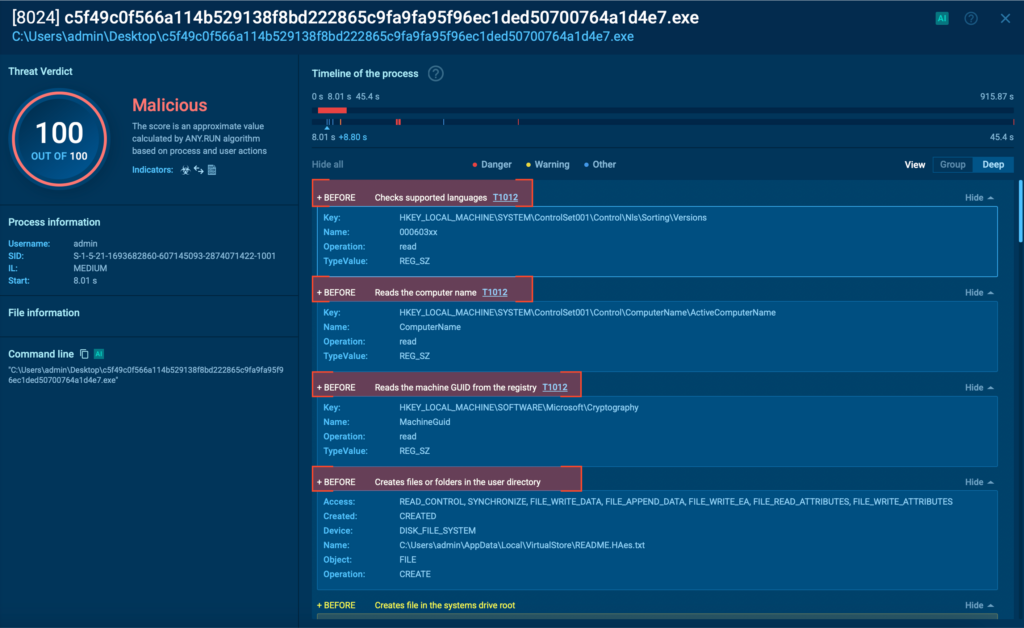
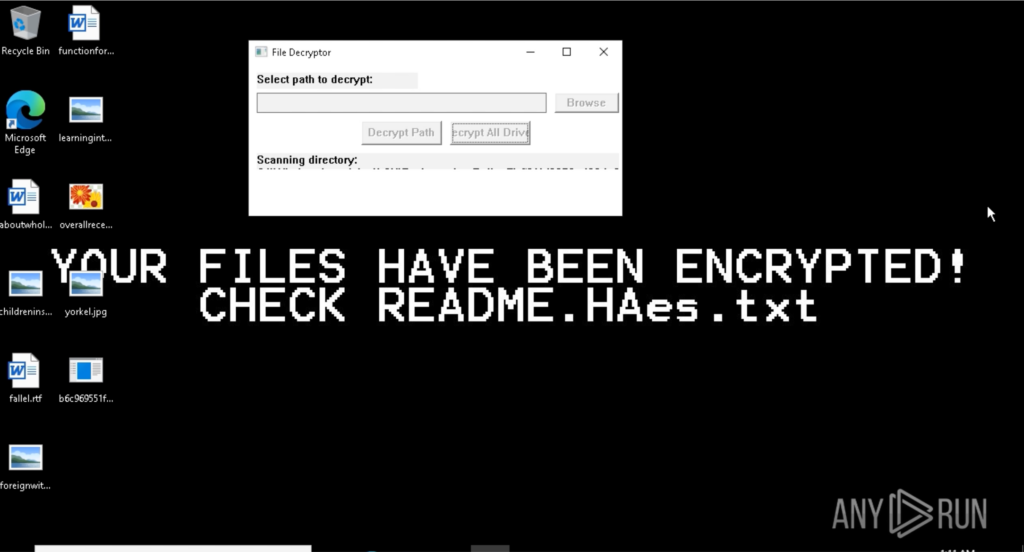
Mamona begins with a straightforward reconnaissance phase, harvesting basic host data like the system’s name and configured language. It then proceeds to drop a ransom note (README.HAes.txt) not only on the Desktop, but recursively inside multiple folders, increasing the chances the victim will see it.
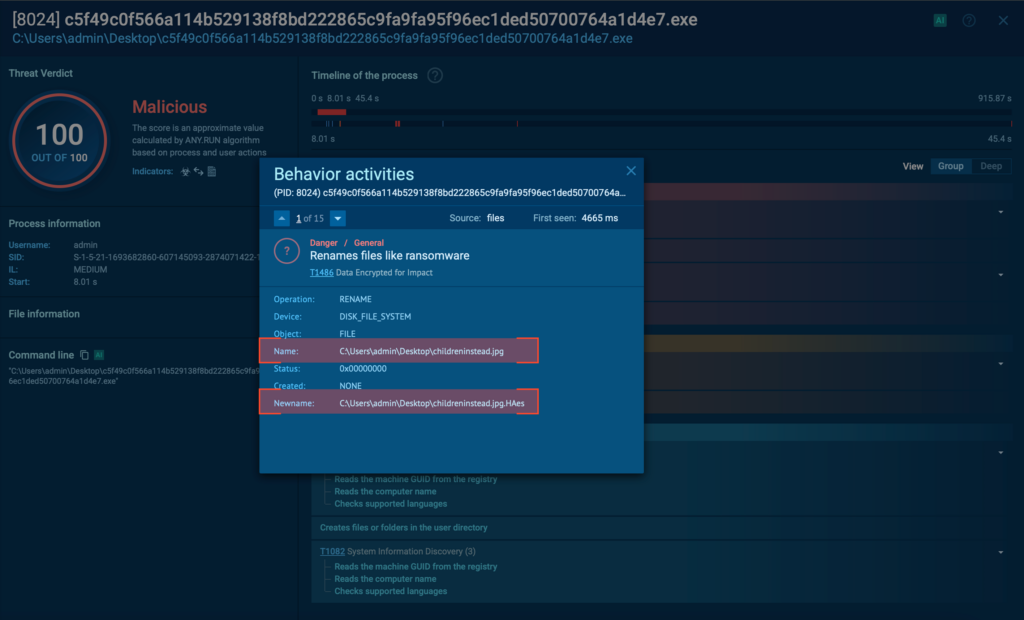
Following the ransom note deployment, Mamona begins encrypting user files, renaming them with the .HAes extension and making them inaccessible. To reinforce the impact, it changes the system wallpaper to a stark warning: “Your files have been encrypted!”
The ransom note shares links to a dedicated leak site (DLS) and a victim’s chat support, both on Tor. Also, it states that “we have stolen a significant amount of your important files from your network” and “Refuse to pay: your stolen data will be published publicly” but that actually does not happen, as we discussed earlier. There’s literally no network activity so this seems to be a threat to coerce the victim into paying the ransom.
But we have an ace up our sleeve. For this engagement, alongside the malware sample, we also managed to obtain a decrypter thanks to Merlax, a friend and fellow malware researcher. Let’s take a look at how it works.
Undoing Mamona’s Damage
We’re dealing with a Ctrl-Z in .exe form, so let’s give it a chance and see how it performs. Visually, it’s a mess: the interface looks like a homemade project built with an older version of Visual Studio. UI elements are poorly rendered, often misaligned or clipping outside window boundaries.
But the backend does its job far better than the frontend, and the files are back to normal.
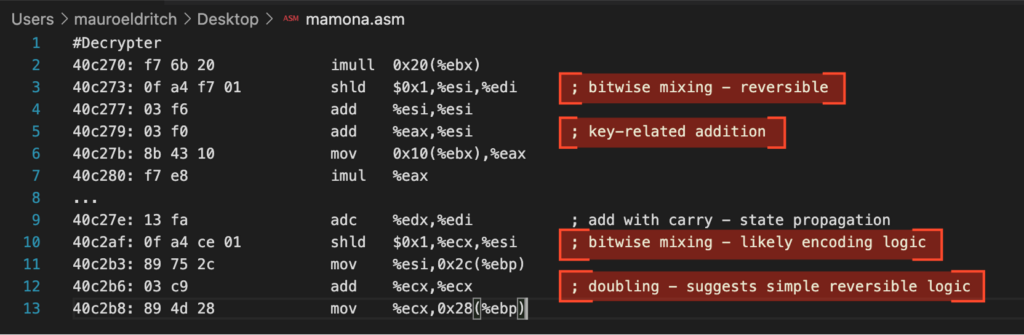
By analysing the decrypter, we find an interesting internal function at offset 0x40C270. Much like in the ransomware sample, we observe a series of low-level operations: alignment to 4-byte boundaries (and $0xfffffffc, %ecx), fixed memory offsets (add $0x23), and repeated use of instructions such as mov, lea, and arithmetic operations, all indicative of a custom-built symmetric routine.
Despite the absence of a traditional XOR operation, the logic appears reversible and consistent with homemade encryption mechanisms.
We have already infected our test machine and vaccinated it, and we are ready for the next stop on our journey: the ATT&CK Matrix. As usual, ANY.RUN takes care of that automagically.

Mapping the Threat: Mamona via MITRE ATT&CK
ANY.RUN’s ATT&CK integration makes it easy to understand and track malware behaviour by profiling its events, tactics, and techniques.
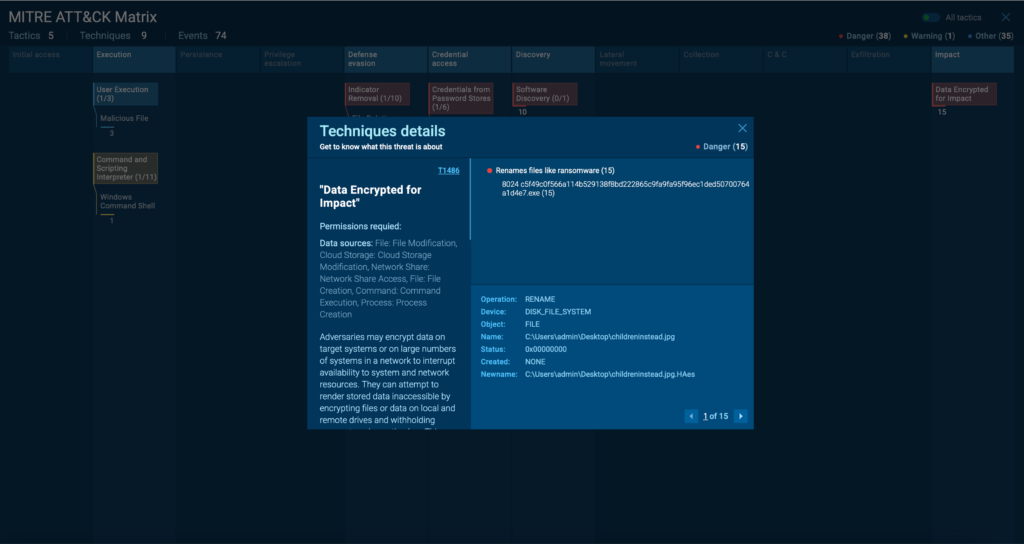
Let’s take a look at how Mamona’s behaviour fits into this framework:
- Discovery: T1012: Query Registry + T1082: System Information Discovery. The reconnaissance routine where the malware queries different local registries like hostname and language.
- Execution: T1059.003: Command and Scripting Interpreter. Since Mamona spawns CMD to invoke ping as a cheap delay mechanism and then moves on to its self-deletion.
- Defense Evasion: T1070.004: Indicator Removal. The self deletion routine attached to the previous ping command.
- Impact: T1486: Data Encrypted for Impact. The encryption process where all our files end up having the “.HAes” extension.
This sums up Mamona’s behavior, which deviates from the usual pattern seen in commodity ransomware. It shows no network activity, no Command and Control channels over Telegram, Discord, or similar platforms. Instead, it relies on a weak, locally executed key generation routine and doesn’t include any form of double extortion, making its threats of data theft and publication purely coercive.
What it does have is a retro-styled decrypter that, despite its clunky and outdated interface, simply works.
Mamona Threat Impact
The Mamona ransomware campaign presents significant risks despite its offline, minimalistic design:
For end users: Victims face immediate file encryption, system disruption, and psychological pressure through false claims of data theft. The ransom note’s threatening tone adds urgency, even though there’s no actual data exfiltration.
For organizations: Mamona can interrupt workflows, encrypt shared drives, and complicate incident response, especially in environments lacking offline backups or real-time monitoring. Its simplicity also makes it harder to detect through conventional network-based defenses.
For security teams: The absence of C2 traffic and use of locally executed logic reduce visibility in traditional detection systems. Its use of basic commands like ping and cmd.exe mimics legitimate activity, requiring deeper behavioral analysis to flag accurately.
For the broader threat landscape: Mamona exemplifies the rise of easy-to-use, builder-based ransomware that favors simplicity over sophistication. Its leaked builder lowers the entry barrier for attackers, raising concerns about wider adoption by low-skilled threat actors.
Conclusion
The analysis of Mamona Ransomware shows how even a quiet, offline threat can cause disruptions.
This strain highlights a rising trend: ransomware that trades complexity for accessibility. It’s easy to deploy, harder to detect with traditional tools, and still effective enough to encrypt systems and pressure victims into paying. Its leaked builder and low barrier to entry only raise the risk of widespread abuse by less sophisticated attackers.
By analyzing Mamona in real time using ANY.RUN’s Interactive Sandbox, we were able to capture the full attack chain, from initial execution and system changes to ransom note deployment and encryption logic, all without needing external network traces.
Here’s how this type of dynamic analysis helps defenders stay ahead:
- Detect threats faster: Spot unusual behavior, even in offline-only attacks.
- See everything in motion: Monitor local activity, file operations, and persistence techniques as they happen.
- Speed up investigations: Gather and interpret IOCs without jumping from one tool to another.
- Respond more effectively: Share artifacts and tactics across security teams.
Experience real-time visibility with ANY.RUN and catch threats others might miss.
Try ANY.RUN’s Interactive Sandbox today
IOCs
SHA256:b6c969551f35c5de1ebc234fd688d7aa11eac01008013914dbc53f3e811c7c77
SHA256:c5f49c0f566a114b529138f8bd222865c9fa9fa95f96ec1ded50700764a1d4e7
Ext:.HAes
File:README.HAes.txt
References
https://bazaar.abuse.ch/sample/c5f49c0f566a114b529138f8bd222865c9fa9fa95f96ec1ded50700764a1d4e7
https://bazaar.abuse.ch/sample/b6c969551f35c5de1ebc234fd688d7aa11eac01008013914dbc53f3e811c7c77
https://app.any.run/tasks/cdcc75cd-d1f0-4fae-8924-d1aa44525e7e
The post Mamona: Technical Analysis of a New Ransomware Strain appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

