Release Notes: SDK Integration, Notifications, 1000+ Detection Rules, and APT Reports
April was another busy month for the ANY.RUN team!
We continued improving our malware detection capabilities, expanded our behavior signatures, and sharpened threat intelligence, all to make your investigations faster, deeper, and even more precise.
From adding fresh Suricata rules and YARA signatures to detecting new malware behaviors, here’s what’s new at ANY.RUN this month.
Let’s dive in!
Product Updates
Integration of ANY.RUN Services with Your Security Systems via SDK
In April, we’ve announced the release of the ANY.RUN SDK, making it easier than ever to integrate our products directly into your infrastructure.
Security teams can now automate submissions, accelerate workflows, and tailor ANY.RUN’s solutions to fit their existing systems like SIEM, SOAR, or XDR.
This gives them faster investigations, fewer manual tasks, and more resources freed up for critical analysis.
By integrating ANY.RUN’s products into the security infrastructure via SDK, you can:
- Automatically submit files and URLs to the Interactive Sandbox
- Search IOCs, IOBs, and IOAs across our threat database via TI Lookup
- Receive and process network-based IOCs with TI Feeds
The SDK is available for users with the Hunter and Enterprise plans.
With the help of this simple integration, we want to make sure that organizations reduce incident response time, improve detection rates, and build a stronger, more resilient security posture.
How to get started: The SDK is Python-based and includes documentation, libraries, and ready-to-use code samples. Find full instructions on GitHub and PyPI.
Contributions and suggestions from other developers are also welcome! For more info on how to contribute, see our guide.
Stay Informed with the New Notifications Window
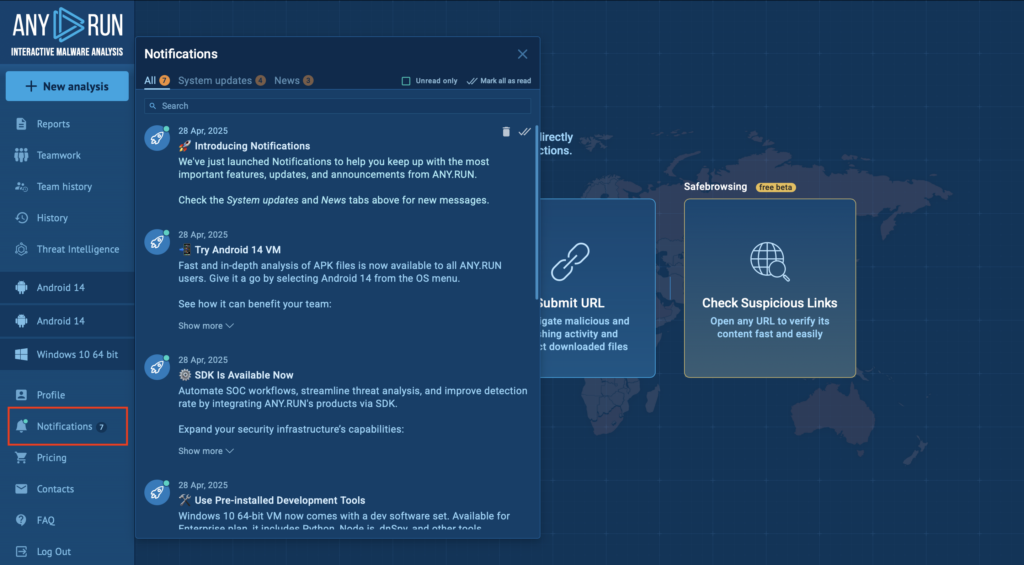
ANY.RUN users will now have access to Notifications directly from the platform interface.
This section is built to keep you informed about the most important updates without cluttering your workflow.
With quick access to key information, your security team can easily stay on top of new capabilities, detection improvements, and emerging threats.
Notifications are short, clear, and actionable, so you can stay focused on your investigations while staying in the loop.
Inside the Notifications section, you’ll find:
- Key product updates and new feature announcements
- Alerts about critical service improvements
- Links to major research reports and threat analyses
- Important security advisories from our team
Threat Coverage Updates
In April, we expanded our detection coverage across Android, Windows, and Linux environments with updated rules, behavior signatures, and threat intelligence to support more precise, faster investigations.
Here’s a quick look at what’s been updated:
New Suricata Rules
We added 902 new Suricata rules in April to improve visibility into network-based threats, including malicious domains, phishing infrastructure, and C2 traffic.
These updates enhance detection coverage for various malware families, including miners, stealers, and ransomware.
Behavior Signatures
We introduced 91 new behavior-based signatures to improve detection for malware samples across platforms. These updates include:
Android:
Windows:
Linux:
Vulnerability Exploits Tracked:
In April, we observed active exploitation attempts involving two newly disclosed vulnerabilities:
These exploits were identified during real-world malware analysis sessions and are now reflected in our detection logic. ANY.RUN continues to monitor and analyze new CVEs to provide fast, actionable insights for defenders.
New YARA Rule Updates
We released 13 new and updated YARA rules to improve static detection and classification, covering both new malware strains and updates to existing detections.
New or updated rules include:
Additionally, we added and updated detectors and extractors for:
- Grandoreiro banking malware
New TI Reports Published
In April, we added two new reports to our Threat Intelligence library, focused on advanced persistent threats (APTs) and coordinated cybercriminal activity. These reports provide fresh insights into recent campaigns, along with actionable tools to support threat hunting, attribution, and detection.
Please note that the reports are available to TI Lookup’s paid users. Contact us to try TI Lookup for your SOC team.
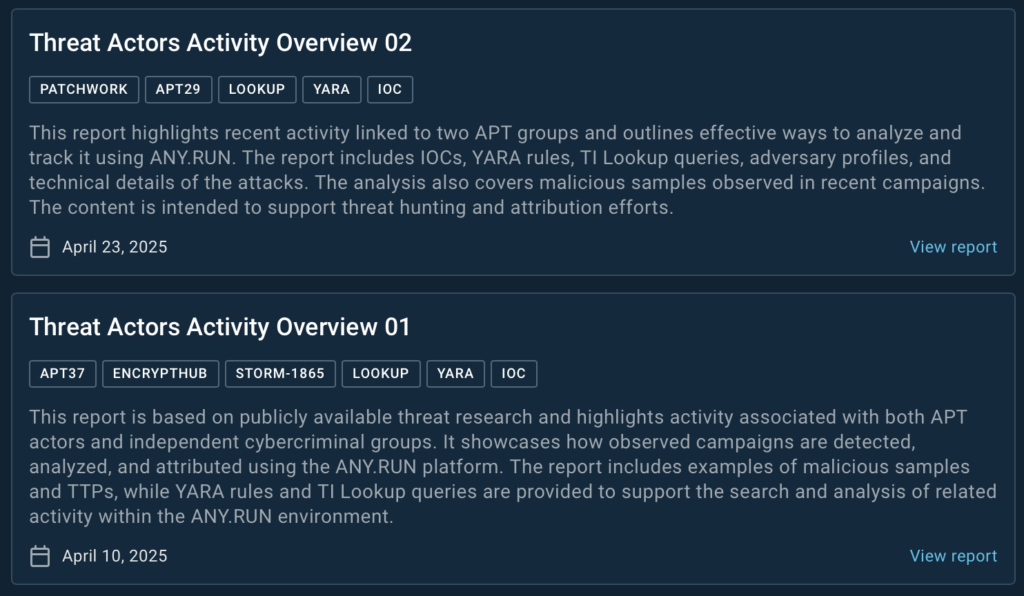
Threat Actors Activity Overview 01
This report analyzes campaigns linked to APT37, EncryptHub, and STORM-1865, combining info from public research and ANY.RUN’s own findings. It includes:
- IOC lists and observed TTPs
- Related malware samples
- TI Lookup queries and YARA rules
- Guidance for detecting similar threats in your environment
This overview shows how threat actor activity is identified, analyzed, and traced using ANY.RUN’s tools.

Threat Actors Activity Overview 02
This report focuses on recent campaigns associated with PATCHWORK and APT29. It provides:
- YARA rules and TI Lookup queries to support detection
- IOC collections and sample analysis
- Adversary profiles and campaign behavior
- Technical breakdowns of malicious files
The report is built to support threat hunters and analysts in tracking high-impact adversaries with greater precision.
About ANY.RUN
ANY.RUN supports over 15,000 organizations across industries such as banking, manufacturing, telecommunications, healthcare, retail, and technology, helping them build stronger and more resilient cybersecurity operations.
With our cloud-based Interactive Sandbox, security teams can safely analyze and understand threats targeting Windows, Linux, and Android environments in less than 40 seconds and without the need for complex on-premise systems. Combined with TI Lookup, YARA Search, and Feeds, we equip businesses to speed up investigations, reduce security risks, and improve team’s efficiency.
The post Release Notes: SDK Integration, Notifications, 1000+ Detection Rules, and APT Reports appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

