What is ClickFix and how to protect your company | Kaspersky official blog
Attackers are increasingly using the ClickFix technique to infect Windows computers to force users to run malicious scripts manually. The use of this tactic was first seen in the spring of 2024. Since then, attackers have come up with a number of scenarios for its use.
What is ClickFix?
The ClickFix technique is essentially an attempt to execute a malicious command on the victim’s computer relying solely on social engineering techniques. Under one pretext or another, attackers convince the user to copy a long command line (in the vast majority of cases — a PowerShell script), paste it into the system’s Run window, and press Enter, which should ultimately lead to compromising the system.
The attack normally begins with a pop-up window simulating a notification about a technical problem. To fix this problem, the user needs to perform a few simple steps, which boil down to copying some object and executing it through the Run application. However, in Windows 11, PowerShell can also be executed from the search bar for applications, settings, and documents, which opens when you click on the icon with the system’s logo, so sometimes the victim is asked to copy something there.
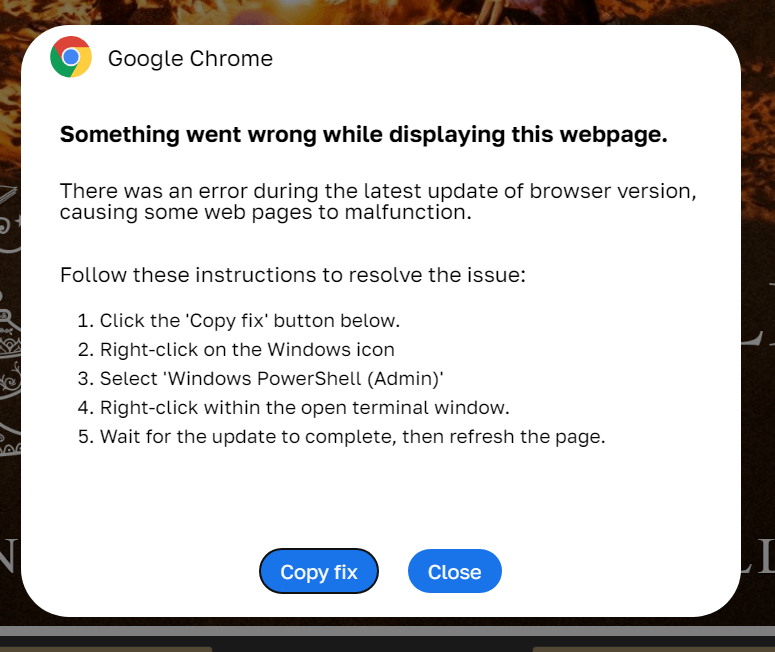
ClickFix attack – how to infect your own computer with malware in three easy steps. Source
This technique earned itself the name ClickFix because usually the notification contains a button, the name of which is somehow related to the verb “to fix” (Fix, How to fix, Fix it…), which the user needs to click to solve the alleged problem or see instructions for solving it. However, this isn’t a mandatory element — the need to launch some code can be justified by the requirement to check the computer’s security, or, for example, to confirm that the user is not a robot. In this case, the Fix button can be omitted.
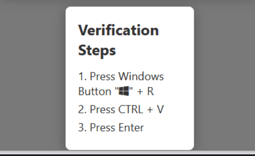
An example of instructions for confirming that you’re not a robot. Source
The scheme may differ slightly from case to case, but attackers typically give the victim the following instructions:
- click the button to copy the code that solves the problem;
- press the key combination [Win] + [R];
- press the combination [Ctrl] + [V];
- press [Enter].
So what actually happens? The first action (clicking the button to copy the code that solves the problem) copies some script invisible to the user to the clipboard. The second (pressing the key combination [Win] + [R]) opens the Run window, which in Windows is designed to quickly launch programs, open files and folders, and enter commands. In the third (pressing the combination [Ctrl] + [V]), the PowerShell script is pasted into Run window from the clipboard. And finally, with the fourth action (pressing [Enter]), the code is launched with the current user privileges.
As a result of executing the script, malware is downloaded and installed onto the computer — with the specific malicious payload varying from campaign to campaign. Thus, what we get is the user running a malicious script on their own system thereby infecting his own computer.
Typical attacks using the ClickFix technique
Sometimes attackers create their own websites and lure users to them using various tricks. Or they hack existing websites and force them to display a pop-up window with instructions. In other cases similar instructions are delivered under various pretexts via email, social networks, or even through instant-messengers. Here are some typical scenarios of using this technique in attacks:
1. Unable to display the page, need to refresh the browser
A classic scenario in which the visitor doesn’t see the page they expected to and is told they need to install a browser update to display it.
2. Error loading a document on a website
Another standard tactic: the user isn’t allowed to view a certain document in Microsoft Word or PDF format. Instead, they’re shown a notification asking to install a plugin for viewing the PDF or “Word online”.
3. Error opening a document from email
In this case attackers substitute the file format. The victim sees a .pdf or .docx icon, but in reality clicks on the HTML file that opens in the browser. Then everything is similar to the previous case — what are needed are: a plugin, malicious instructions, and the familiar “How to fix” button.
4. Problems with the microphone and camera in Google Meet or Zoom
A more unusual variation of the ClickFix tactic is used on fake Google Meet or Zoom websites. The user receives a link for a video call, but “is not allowed to join” it, because there are problems with their microphone and camera. The message “explains” how to fix it.
5. Prove that you’re not a robot – fake CAPTCHA
Finally, the most curious version of the attack using ClickFix: the site visitor is asked to complete a fake CAPTCHA to prove they’re not a robot. But the required proof is, of course, is to follow the instructions written in the pop-up window.
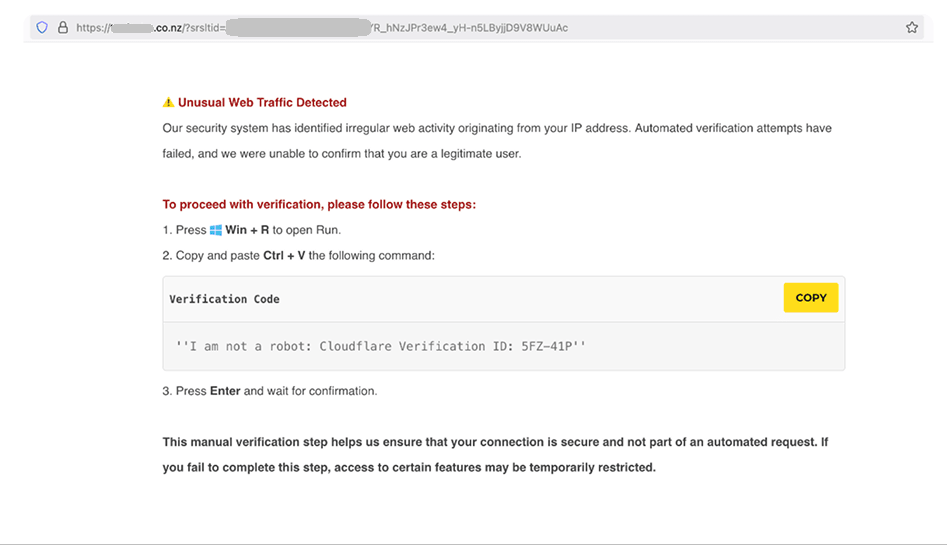
Prove you’re not a robot – to do this, run a malicious script on your computer. Source
How to protect yourself from ClickFix attacks?
The simplest mechanism for protecting your company from attacks using the ClickFix technique involves blocking the [Win] + [R] key combination in the system — it’s hardly needed at all in the day-to-day work of the typical employee. However, this isn’t a panacea — as we already wrote above, in Windows 11 the script can be launched from the search bar, and some variations of this attack use more detailed instructions in which the user is told how to manually open the Run window.
Therefore, protective measures, of course, should be comprehensive and primarily aimed at training employees. It’s worth conveying to them that if someone seeks any manual manipulations with the system — it’s an extremely alarming sign.
Here are some tips on how to protect your organization’s employees from attacks using ClickFix tactics:
- Be sure to use a reliable security solution on all corporate devices, and also install protection at the mail gateway level.
- Raise employee awareness of cyberthreats, including new tactics, with specialized training. Organizing such training is easy – just use our automated educational Kaspersky Automated Security Awareness Platform .
Kaspersky official blog – Read More



