How Threat Intelligence Feeds Help During Incident Response
When data meets automation, two pillars of modern tech converge to create something smarter: Threat Intelligence Feeds. Real-time insights, machine-speed decisions, and a global perspective — all working together to outsmart threats before they become incidents.
ANY.RUN’s TI Feeds are structured, continuously updated streams of fresh threat data. They contain network-based IOCs — IP addresses, domain names, and URLs — and are enriched by additional context-providing indicators like file hashes and port indicators.
The Feeds enhance threat detection capabilities of security systems, enable SOC teams to quickly mitigate attacks, including emerging malware and persistent threats.
Source, Structure, Benefits of ANY.RUN’s TI Feeds
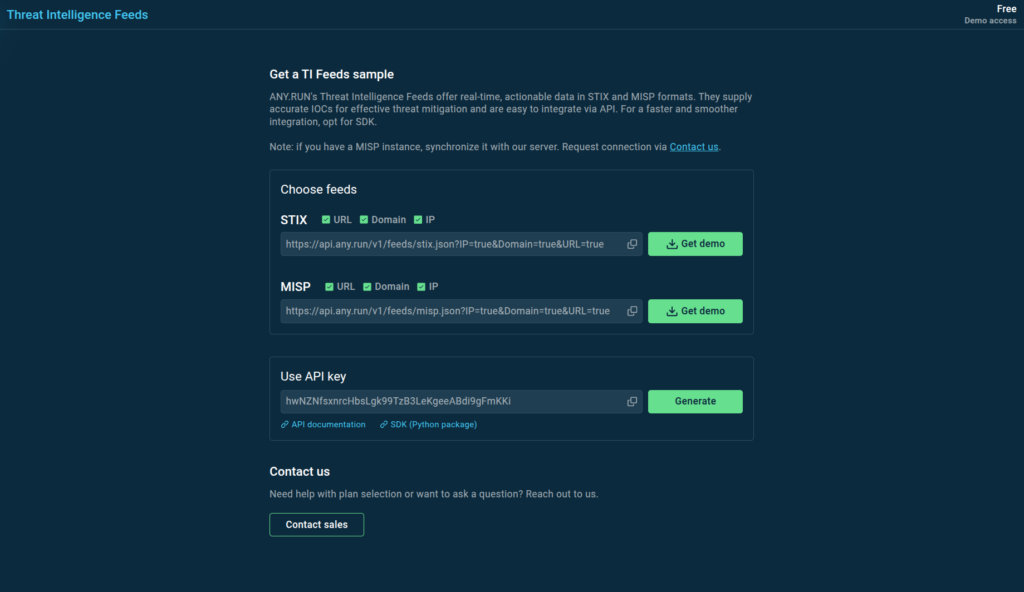
Threat Intelligence Feeds provided by ANY.RUN are sourced from public analysis sessions in our cloud-based sandbox, where users including the SOC teams of 15,000 organizations from a variety of industries detonate and dissect real-world malware samples.
The indicators are pre-processed using proprietary algorithms and whitelists to minimize false positives, ensuring high accuracy and relevance. Each indicator of compromise is enriched with contextual metadata providing deeper insights into the threat.
This means that an IP, URL, or domain in TI Feeds are enriched with:
- External references: Links to relevant sandbox sessions.
- Label: Name of the malware family or campaign.
- Detection timestamps: last/first seen dates provide a timeline to understand if a threat is ongoing or historical.
- Related objects: IDs of files and network indicators related to the IOC.
- Score: Value representing the severity level of the IOC.
ANY.RUN’s TI Feeds come in STIX or MISP format with indicators of your choice. Set up a test sample to start leveraging actionable IOCs data in your security operations. ANY.RUN also runs a dedicated MISP instance that you can synchronize your server with or connect to your security solutions. To get started, contact our team via this page.
By delivering insights into threats and their indicators of compromise (OCs), TI Feeds support organizations across multiple phases of incident response: Incident Triage, Threat Hunting, and Post-Incident Analysis.
Incident Triage
Incident Triage involves assessing and prioritizing security alerts to determine their severity and potential impact. This must be done quickly and yet precisely, saving analysts from wasting time on false positives and highlighting critical true positives.
TI Feeds streamline this process by providing contextual data to validate and enrich alerts, enabling faster and more accurate decision-making.
TI Feeds for Triage:
- Correlation with Known Threats: Feeds supply IOCs (e.g., malicious IPs, domains, file hashes) that can be cross-referenced with incoming alerts to confirm whether an incident is legitimate or a false positive.
- Prioritization: Feeds provide threat severity scores and context (e.g., association with a known ransomware group) to help security teams sort out incidents that pose the greatest risk.
- Automation: Integration with Security Information and Event Management (SIEM) systems or Security Orchestration, Automation, and Response (SOAR) platforms allows TI Feeds to automatically enrich alerts with relevant threat data, reducing manual effort.
Example
A financial institution receives an alert from its intrusion detection system (IDS) about a suspicious outbound connection to an unfamiliar IP address. A TI Feed identifies the IP as part of a command-and-control (C2) server linked to Lynx ransomware. Armed with this information, the team prioritizes the incident as high-severity, immediately isolates the affected endpoint, and escalates it for further investigation, avoiding a potential data breach.
Business Impact

- Reduces Mean Time to Detect (MTTD) by quickly validating alerts.
- Minimizes resource waste on false positives, allowing focus on critical incidents.
- Enhances compliance by ensuring timely response to high-risk threats.
ANY.RUN’s TI Feeds are updated every few hours, pulling fresh IOCs from over 16,000 daily public tasks submitted by its community. This near real-time delivery ensures organizations can respond to emerging threats almost immediately after they are detected in the wild.
Threat Hunting
- Enriching Network Data: Feeds supply IOCs that can be correlated with network logs, endpoint data, or user activity to uncover anomalies.
- Guiding Hypothesis Development: TI Feeds enriched with contextual data provide the basis for further malware, attack, or actor investigation. Enabled to proceed from IOCs to TTPs, hunters can craft targeted hypotheses about potential threats.
- Proactive Defense: By highlighting emerging threats (e.g., new exploit kits or phishing campaigns), TI Feeds allow hunters to search for related activity before an attack fully unfolds.
Example
A retail company’s threat-hunting team learns from their TI Feed about a new phishing campaign targeting e-commerce platforms with a specific malicious domain and a unique file hash for a ransomware payload. The team uses this intelligence to search their network logs for any connections to the domain or instances of the file hash.
They discover a single endpoint that attempted to access the domain but was blocked by the firewall. Further investigation reveals a phishing email that evaded initial detection. The team neutralizes the threat by quarantining the endpoint and updating email filters, preventing a potential ransomware outbreak.
Business Impact

- Prevents incidents by identifying threats before they cause harm.
- Strengthens proactive security posture, reducing the likelihood of successful attacks.
- Protects brand reputation by avoiding customer data exposure.
Post-Incident Analysis
Post-Incident Analysis focuses on understanding the root cause of an incident, assessing its impact, and improving future defenses. TI Feeds provide critical context to reconstruct the attack, identify gaps in security, and build remediation strategies.
ANY.RUN’s TI Feeds draw from a vast dataset generated by a diverse community of 500,000 analysts and teams of 15,000 enterprises. This scale ensures broad coverage of threats, including zero-day exploits and emerging malware, tailored to various industries. It helps teams map incidents to global trends.
TI Feeds in Post-Incident Analysis
- Attack Reconstruction: Feeds supply detailed intelligence on threat actors and associated IOCs, helping teams trace the attack’s origin and progression.
- Gap Identification: By comparing the incident to known threat patterns, TI Feeds reveal weaknesses in defenses (e.g., unpatched vulnerabilities or misconfigured systems).
- Retrospective Analysis: Newly published threat intel can be used to re-analyze old data. This helps identify if earlier, undetected activity was related to a known campaign.
Example
After a manufacturing company suffers a data breach involving stolen intellectual property, the incident response team uses their TI Feed to analyze the attack. The feed reveals that the breach was caused by a spear-phishing campaign linked to a nation-state actor known for targeting industrial sectors.
Since ANY.RUN’s Feeds provide links to sandbox analyses of the phishing samples, the team can extract the attacker’s TTPs, including the use of a specific exploit in an unpatched software version and a custom PowerShell script for data exfiltration.
The team can now patch the vulnerability, deploy new endpoint detection rules to flag similar scripts, and conduct employee training on recognizing spear-phishing emails. Additionally, the feed’s geopolitical context prompts the company to enhance monitoring of critical R&D systems.
Business Impact

- Reduces Mean Time to Recover (MTTR) by guiding effective remediation
- Strengthens long-term resilience by addressing root causes and vulnerabilities
- Supports compliance by documenting lessons learned and mitigation steps for audits
Ways TI Feeds Support Organizational Efficiency
ANY.RUN’s TI Feeds are designed for easy integration with SIEM, SOAR, firewalls, and other security platforms, supporting formats like STIX and MISP. This ensures automated ingestion of IOCs, streamlining workflows and enhancing existing tools’ effectiveness.
By integrating real-time, high-quality threat data with automation, TI Feeds enhance organizational resilience, reduce risks, and support informed decision-making. Their most important benefits that align with business objectives and KPIs are:
1. Early Detection Capabilities
TI Feeds enable identification of potential risks before they escalate into costly incidents. By identifying malware or phishing campaigns at their inception, TI Feeds help businesses avoid disruptions, protect customer trust, and safeguard revenue streams.

2. Faster Response Times
TI Feeds significantly shorten the time to identify and mitigate threats by correlating threat data with ongoing incidents. Faster response times contribute to KPIs like Mean Time to Detect (MTTD) and Mean Time to Respond (MTTR), which are critical for minimizing the impact of security breaches.
Addressing breaches promptly reduces financial losses, protects brand reputation, and ensures compliance with regulatory requirements (e.g., GDPR, CCPA).
3. Informed Decision-Making
TI Feeds give organizations actionable intelligence, enabling data-driven decisions that align cybersecurity strategies with business goals. A clear picture of the threat landscape helps business leaders prioritize investments in security controls, employee training, or third-party partnerships, driving long-term resilience and competitive advantage.
4. Proactive Defense
TI Feeds shift organizations from reactive to proactive cybersecurity, anticipating threats and preventing incidents before they occur. It improves KPIs like the percentage of prevented incidents, reduction in remediation costs, and increased system uptime
Conclusion
ANY.RUN’s Threat Intelligence Feeds deliver significant value by combining high-quality, low-noise data, near real-time updates, a massive community-driven dataset, seamless integration, and unique sandbox-driven insights.
These benefits directly enhance Incident Triage by speeding up alert validation, Threat Hunting by enabling proactive threat discovery, and Post-Incident Analysis by providing detailed context for remediation.
By integrating TI Feeds into incident response workflows, organizations can minimize damage, enhance security posture, and align cybersecurity efforts with business objectives.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request trial of ANY.RUN’s services to test them in your organization →
The post How Threat Intelligence Feeds Help During Incident Response appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
