How Indicators of Compromise, Attack, and Behavior Help Spot and Stop Cyber Threats
In cybersecurity, the three main types of indicators are a critical concept for threat detection and response. These main types are indicators of compromise, behavior, and attack (IOCs, IOBs, IOAs). Let’s elaborate on their essence, difference, and use.
Distinction in a Nutshell
| IOCs | IOBs | IOAs | |
|---|---|---|---|
| Definition | Artifacts or observables that suggest a system has already been compromised | Patterns or activities that indicate an attack is in progress or imminent | Describes the adversary’s TTPs (Tactics, Techniques, and Procedures), often abstracted from specific tools or campaigns |
| Nature | Reactive | Proactive | Strategic |
| Type | Technical evidence left behind | Behavioral analysis | High-level behavioral models |
| Purpose | Help identify intrusions and data breaches | Detect and block attacks before they succeed | Understand and profile attackers across campaigns or tools |
| Use | Used in threat detection tools like SIEM, IDS/IPS, antivirus, and EDR. Help correlate logs and trace how an attack occurred. Often shared via threat intelligence feeds. | Applied in real-time detection by EDR/XDR platforms. Used in behavioral analytics and heuristics. Focus on what the attacker is trying to do, not just the tools used. | Used in threat modeling, proactive defense, and red teaming. Integrated into MITRE ATT&CK mapping, behavior-based threat hunting. Help anticipate novel attack chains and identify APTs. |
Indicators of Compromise
IOCs are pieces of evidence that suggest that a system, network, or device has been compromised by a cyberattack or malicious activity. They are typically reactive, meaning they are identified after an attack has occurred.
The main purpose of IOCs is to help detect and confirm security incidents with known threats or malware. They serve as forensic evidence in incident investigations and are necessary for adequate incident response and mitigation.
More often than not IOCs are specific — tied to a particular malware or campaign.
IOCs can be classified into:

- File-based: malicious file hashes (e.g., MD5, SHA-1, SHA-256), known malware signatures.
- Network-based: suspicious IP addresses, domains, URLs, or unusual traffic patterns (e.g., connections to a known command-and-control server).
- System-based: registry key changes, unauthorized user accounts, or suspicious processes running.
Being reactive by their nature, IOCs are of immense help in threat prevention. When used smartly, they can be weaponized to block, disrupt, or preempt similar attacks in the future.
This function is provided by threat intelligence: SOC teams collect indicators associated with known malware and incidents (malicious IPs, domains, file hashes, or URLs) and blacklist them in their security systems to prevent future communication or execution associated with those IOCs.
For example, a phishing domain seen in a past attack is added to the block list, preventing any user from accessing it if reused. Potential IOCs can be checked with the help of services like ANY.RUN’s Threat Intelligence Lookup. It searches for information from malware samples added and analyzed in the Interactive Sandbox:
destinationIP:”147.185.221.26″
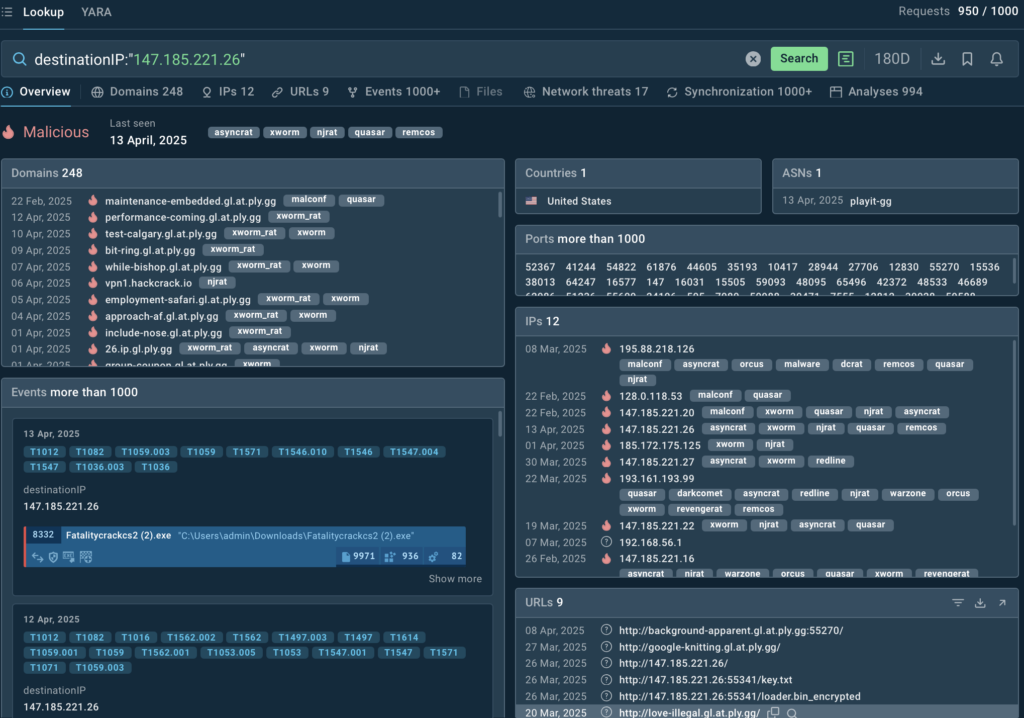
Another way of using IOCs for proactive protection is setting up decoys (honeypots or honeytokens) to monitor access to known indicators or infrastructure that mimics IOC traits.
Finally, IOCs reveal which vulnerabilities are being exploited, so teams can prioritize patching or tighten firewall rules accordingly.
IOCs have their limitations, though. They may not help to detect brand new or advanced threats. It’s important to keep in mind that attackers can easily change IOCs (e.g., domains, hashes), so IOC-based prevention is only as effective as its freshness and context. Context also helps to reduce false positives in detection.
Context can also be provided by TI Lookup: it supports over 40 search parameters and wildcards which allows to combine indicators and parameters in complex search queries:
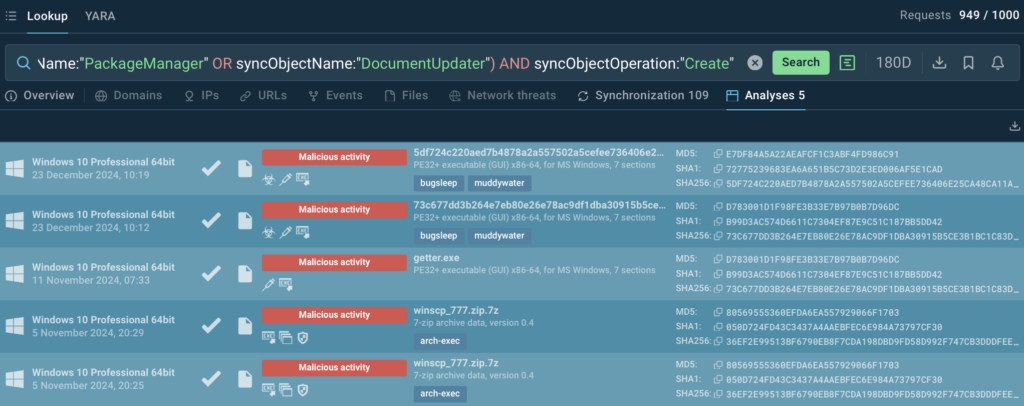
Mutexes often generate false positive alerts in monitoring systems. Malware samples can contain the same objects as legitimate programs, and a lot of mutex names are generic.
Switching to the Analyses tab in the search results, we see, that the combination of mutexes with such innocent general names as PackageManager and DocumentUpdater occurs in malware campaigns of MuddyWater APT group from Iran, which is exactly as dangerous as an APT group from Iran is supposed to be.
On the other hand, this combination of mutexes was last spotted in malware samples about four months ago which allows us to consider this signal obsolete.
Security teams share IOCs via threat intelligence feeds: continuously updated data streams with indicators from fresh malware samples integrated with monitoring and detection systems. ANY.RUN provides Threat Intelligence Feeds in STIX and MISP formats.
Indicators of Behavior
IOBs focus on patterns or behaviors that suggest malicious activity, rather than specific artifacts or static signatures. They describe how an attacker operates, often describing tactics, techniques, and procedures (TTPs). In other words, these indicators focus on what an attacker does rather than specific tools or files.
This enables them to be used for detecting zero-day attacks, unknown or evolving threats that may not have specific IOCs which makes IOBs useful in proactive threat hunting and monitoring. Suspicious behavior can signal an attack in progress, before significant damage occurs.
IOBs may refer to:

- User Behavior: An account logs in from an unusual location or at an odd time.
- System Behavior: A process attempts to access sensitive files repeatedly or executes unauthorized scripts.
- Network Behavior: Encrypted traffic spikes to unknown external servers, resembling data exfiltration.
Thus, typical examples of IOBs are:
- Use of living-off-the-land binaries (e.g., rundll32, certutil);
- Obfuscation techniques;
- Credential dumping after privilege escalation;
- Repeated use of valid accounts for persistence.
IOBs also come with a few shortcomings. It requires advanced analytics, such as behavioral analysis or machine learning, to identify anomalies. Sophisticated monitoring tools (e.g., SIEM, UEBA) should be employed to work with this family of indicators. They can be resource-intensive to analyze and validate. And they may produce false positives if legitimate behaviors mimic malicious ones.
ANY.RUN’s Interactive Sandbox allows analysts to observe how malware or suspicious files behave in a controlled environment and detect anomalous behaviors that may indicate a potential threat. For example, in this analysis session we see remote code execution via mshta.exe triggered by a command entered manually by a user and mentioning a (misspelled) CAPTCHA:
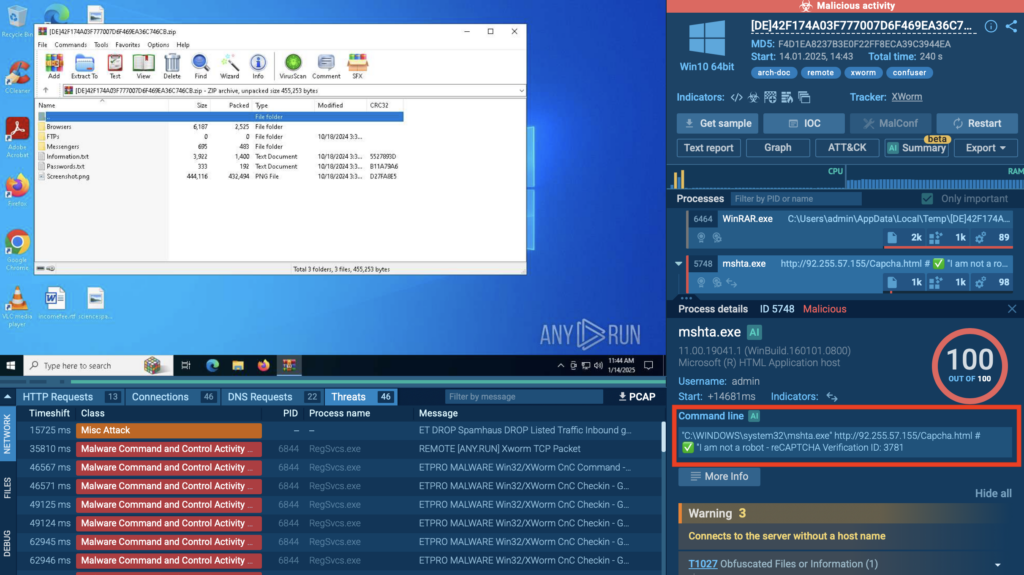
What does this activity indicate? In their latest campaign, Storm-1865 distributed phishing emails impersonating Booking.com. The emails contained links leading to fake CAPTCHA pages designed to build trust and lure users into interaction. The threat actor leveraged the ClickFix technique, instructing victims to paste a malicious command into the Windows command prompt.

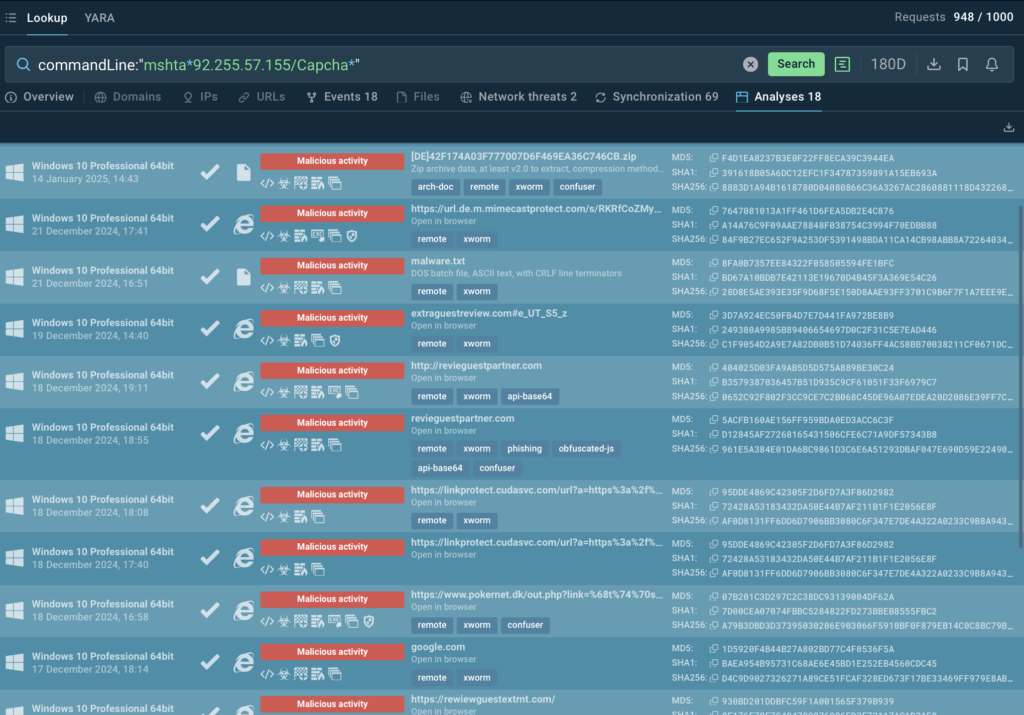
The campaign has been observed delivering several commodity malware families, including XWorm, Lumma Stealer, VenomRAT, AsyncRAT, DanaBot, and NetSupport RAT. With the following TI lookup query, we can search through recent public sandbox analyses and find samples with the same malicious activity for further research:
commandLine:”mshta92.255.57.155/Capcha“
Indicators of Attack
IOAs are proactive indicators that focus on the intent and actions of an adversary during an attack, emphasizing the “how” and “why” of malicious activity. They aim to detect attacks in real time, and to catch it in its early stages (e.g., during reconnaissance, exploitation, or lateral movement). This allows cybersecurity teams to prevent attacks by interrupting the kill chain.
Examples of IOAs:

- Reconnaissance: Unusual port scanning or enumeration of network resources.
- Exploitation: Attempts to exploit a known vulnerability (e.g., SQL injection or buffer overflow).
- Persistence: Installation of backdoors or scheduled tasks to maintain access.
- Lateral Movement: Abnormal internal network traffic, such as attempts to access multiple systems with stolen credentials.
- C2 Communication: Process beaconing to rare external IP at intervals.
- Credential Theft: LSASS memory access by a non-standard process.
- Data Exfiltration: Sensitive files zipped and sent via Dropbox or OneDrive.
What typical indicators of attack might look like:
- Word document spawns PowerShell;
- Process injection detected;
- A user logs in from two geographies within minutes;
- Suspicious lateral movement.
Since IOAs are specific signs of an active or imminent attack, often tied to known TTPs or malicious artifacts, it is possible to research these indicators with the aid of ANY.RUN’s Threat Intelligence Lookup through the Interactive MITRE ATT&CK Matrix.
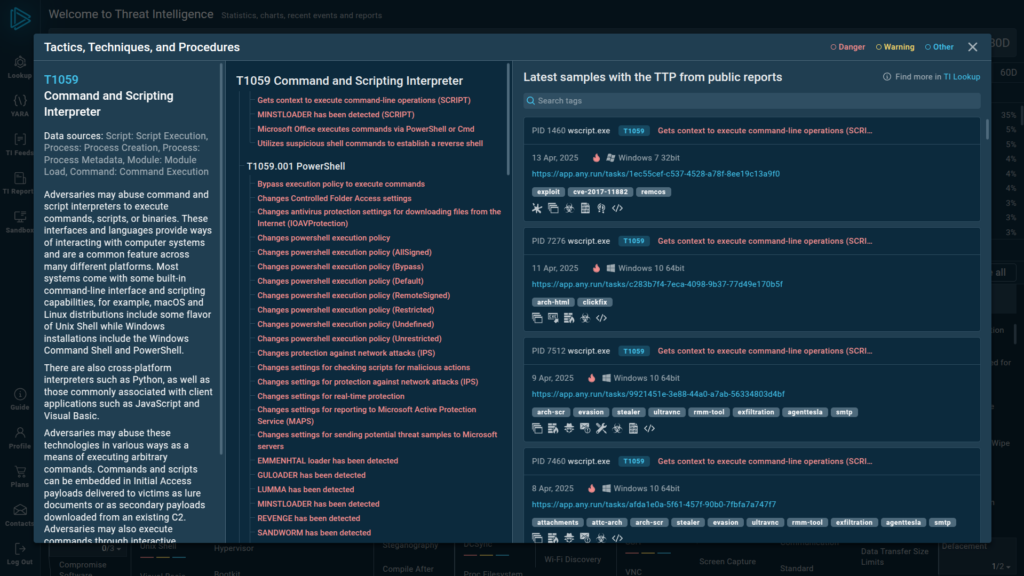
The Matrix lets you map TTPs to actual samples of malware and phishing threats and view their entire execution chain inside the Interactive Sandbox, as well as collect additional indicators.
Conclusion
The most valuable aspect of indicators in institutional cybersecurity is of course their potential to help prevent threats and incidents, stop attacks from succeeding, and thus avoiding financial loss, operational disruption, and reputation damage. Regularly collecting and using IOCs, IOAs, and IOBs, including with the services like ANY.RUN’s TI Lookup and TI Feeds, can help your SOC team fight off threats and keep your infrastructure safe.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals and 15,000 organizations worldwide. The Interactive Sandbox simplifies malware analysis of threats that target both Windows and Linux systems. The threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Integrate ANY.RUN’s Threat Intelligence suite in your organization →
The post How Indicators of Compromise, Attack, and Behavior Help Spot and Stop Cyber Threats appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
