Release Notes: Android VM, Pre-Installed Dev Tools, TI Reports & Enhanced Detection
March was a productive and exciting month for the ANY.RUN team. We’ve been working hard to improve both our sandbox platform and Threat Intelligence services — all to help you detect threats faster and stay ahead of cybercriminals.
This month, we focused on expanding the environments available for malware analysis and making our threat detection even sharper. We also published fresh TI reports and introduced new signatures and rules to improve detection accuracy.
Let’s take a quick tour of what’s new in ANY.RUN.
Product Updates
Android Environment Now Available for Sandbox Analysis
It’s official! The update many security teams have been waiting for is here: ANY.RUN now offers Android OS in the Interactive Sandbox.
You can now investigate Android malware in a real ARM-based sandbox and see exactly how a suspicious APK file behaves in a mobile environment. This means no more guessing, no more blind spots, and no need for separate mobile analysis tools.
Read technical analysis of Salvador Stealer, a new Android banking malware
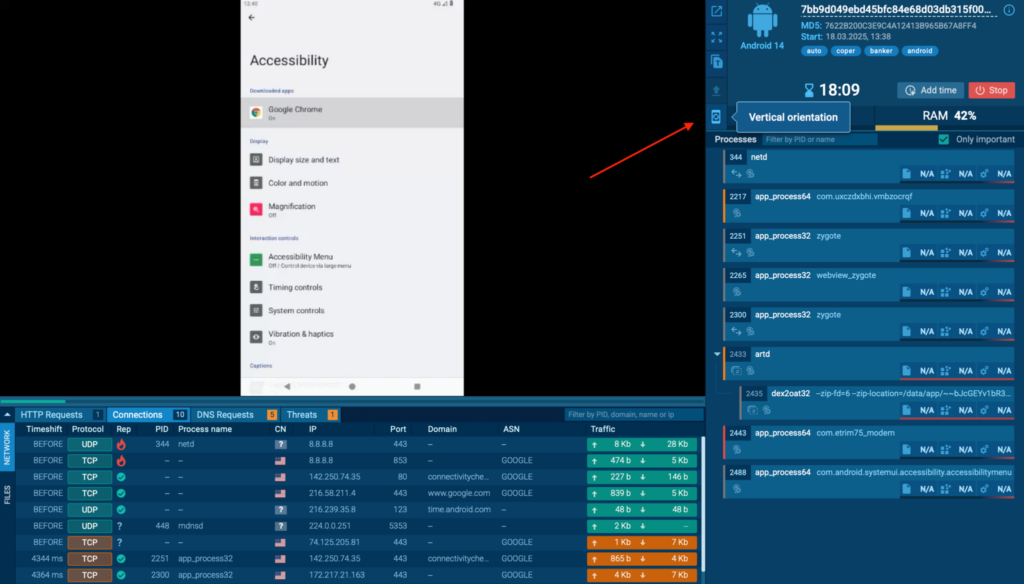
With this release, SOC teams, incident responders, and threat hunters can analyze Android threats faster and with greater accuracy, all within the familiar ANY.RUN interface.
And here’s the best part: Android OS support is available to all users, including Free Plan users.
Why it matters:
- It’s fast: No waiting for static scans or time-consuming reverse engineering.
- It’s interactive: Click, explore, and engage with the malware just like on a real Android device. Grant or deny permissions, trigger actions, and watch how the sample reacts.
- It’s detailed: Track every move the malware makes with process trees, MITRE ATT&CK mapping, and real-time network insights.
- It’s fully cloud-based: No extra setup required. Run Android malware investigations anytime, anywhere, directly in your browser.
- It’s built for teams: Generate structured reports, share findings, and collaborate efficiently across your security team.
This update makes Android malware analysis easier, faster, and more accessible to everyone.

New Pre-Installed Development Tools for Deep Malware Analysis
We’ve introduced a new pre-installed software set in the Windows 10 VMs: the Development Toolkit, designed specifically for advanced malware analysis.
With this update, users can now select the “Development” option when configuring their sandbox environment. This toolkit includes essential software like Python, Node.js, debuggers, decompilers, and reverse engineering tools, pre-installed and ready to use.
It’s ideal for analyzing complex threats like Python-based malware, Node.js-based samples, or malware that requires deeper debugging and inspection.
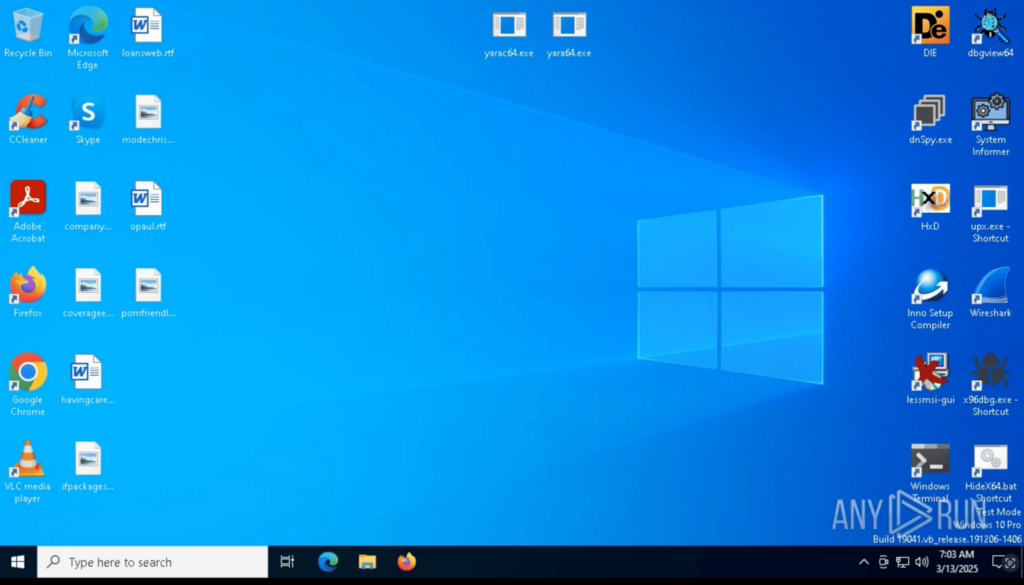
What’s inside the Development Toolkit?
- Python (latest version)
- Node.js (latest version)
- DebugView
- Detect It Easy (DiE)
- dnSpy
- HxD Hex Editor
- Process Hacker
- x64dbg Debugger
- Wireshark PE
This set removes the need to manually install research tools, making your analysis sessions faster, smoother, and more efficient.
Threat Coverage Updates
We’ve also boosted our threat detection and intelligence capabilities for more precise analysis.
Suricata Rules
In March, we expanded our network-based threat detection by adding 1,654 new Suricata rules. These rules enhance visibility over malicious domains, C2 infrastructure, and phishing campaigns.
Key updates include:
- Detection of 25 domains linked to Lumma Stealer activity.
- Identification of 2 domains associated with Pentagon-related infrastructure.
New Behavior Signatures
In March, we added a total of 64 new behavior-based detection signatures to improve malware visibility and detection accuracy. These signatures cover mutex findings, suspicious activity patterns, C2 communications, and detections for popular malware families.
Highlights from this update include:
- VANHELSING malware
- Wormlocker
- ScreenConnect abuse
- Advanced Installer misuse
- HatVibe malware
- VANHELSING detection (additional session)
- GRANDOREIRO banking trojan
- SVCSTEALER mutex detection
- DINODASRAT detection
- MINSTLOADER detection (script-based)
Additionally, behavior signatures were introduced to detect:
- C2 communications related to Pentagon infrastructure (requires MITM analysis)
- Grandoreiro C2 IP address
- HTTP requests linked to Sneaky2FA phishing activity
- domains spoofing e-zpass
- suspicious activity and evasion techniques
New YARA Rule Updates
To further strengthen static detection and classification, we added 5 new YARA rules in March. These rules improve the identification of emerging malware families and suspicious behavior patterns.
New TI Reports Published
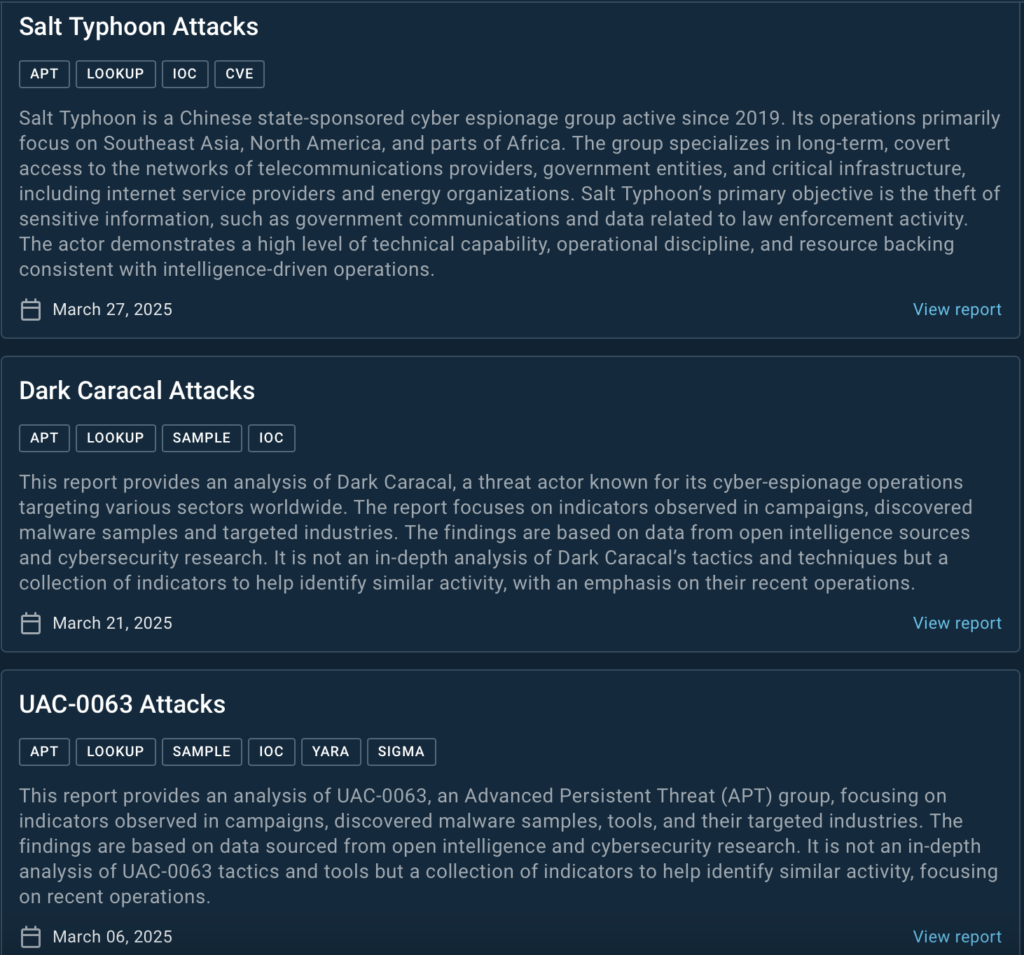
In March, we expanded our Threat Intelligence library with three new reports covering the latest activity of active APT groups. These reports provide valuable insights into real-world attacks, tools, and indicators to help security teams detect and respond to emerging threats.
Here’s what’s new:
- Salt Typhoon Attacks: An in-depth report on a Chinese state-sponsored cyber espionage group active since 2019. The report highlights the group’s long-term, covert operations targeting government entities, critical infrastructure, and telecommunications providers across Southeast Asia, North America, and Africa.
- Dark Caracal Attacks: A collection of IOCs and malware samples linked to Dark Caracal, a threat actor known for global cyber-espionage campaigns. The report focuses on recent activities, targeted sectors, and indicators to help identify similar threats.
- UAC-0063 Attacks: A detailed analysis of UAC-0063, an APT group known for persistent and targeted attacks. The report includes IOCs, malware samples, YARA, and SIGMA rules to help defenders spot related malicious activity.

About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
The post Release Notes: Android VM, Pre-Installed Dev Tools, TI Reports & Enhanced Detection appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
