Expose Android Malware in Seconds: ANY.RUN Sandbox Now Supports Real-Time APK Analysis
It’s here! The news security teams have been waiting for: ANY.RUN now fully supports Android OS in its interactive sandbox!
Now, you can investigate Android malware in a real ARM-based sandbox, exactly as it would behave on an actual mobile device. No more blind spots or unreliable analysis.
With this release, ANY.RUN allows SOC teams, incident responders, and threat hunters to analyze Android threats faster, more efficiently, and with greater accuracy while reducing operational costs.
And the best part? Android OS support is available to everyone, including Free plan users!
Why Your Team Needs Mobile Threat Analysis Inside ANY.RUN’s Android Sandbox
Android malware is a direct risk to businesses, financial institutions, and enterprise security teams. Attackers are targeting mobile devices to steal credentials, infiltrate corporate networks, and compromise financial systems.
Without real-time mobile threat analysis, businesses face delayed detection, higher security costs, and increased exposure to cyber threats.
Now you can interact with APK files in a fully controlled environment, track malicious activity in real time, and generate in-depth reports: all in one convenient place.
By analyzing Android threats inside ANY.RUN’s secure cloud-based environment, businesses can:
- Spot Android malware in seconds: Run suspicious APKs in a real Android environment and catch threats before they spread.
- See exactly what malware is doing: Watch how it abuses permissions, steals data, or makes shady network connections, no more guesswork.
- Make Android threat investigations easier: Quickly analyze mobile malware without slowing down your team or piling on extra work.
- Take full control of your data: Analyze Android threats in a private, secure environment where only your team has access, no third parties involved.
- Improve collaboration: Generate structured reports with detailed APK insights, making escalation and knowledge sharing between your team more effective.
How to Get Started with ANY.RUN’s Android Sandbox
Getting started is quick and easy.
Since ANY.RUN is fully cloud-based, there’s no need to download or install complicated software. Just sign up and follow these simple steps to start analyzing right away:
- Select Android OS – Before launching an analysis, choose Android from the operating system menu.
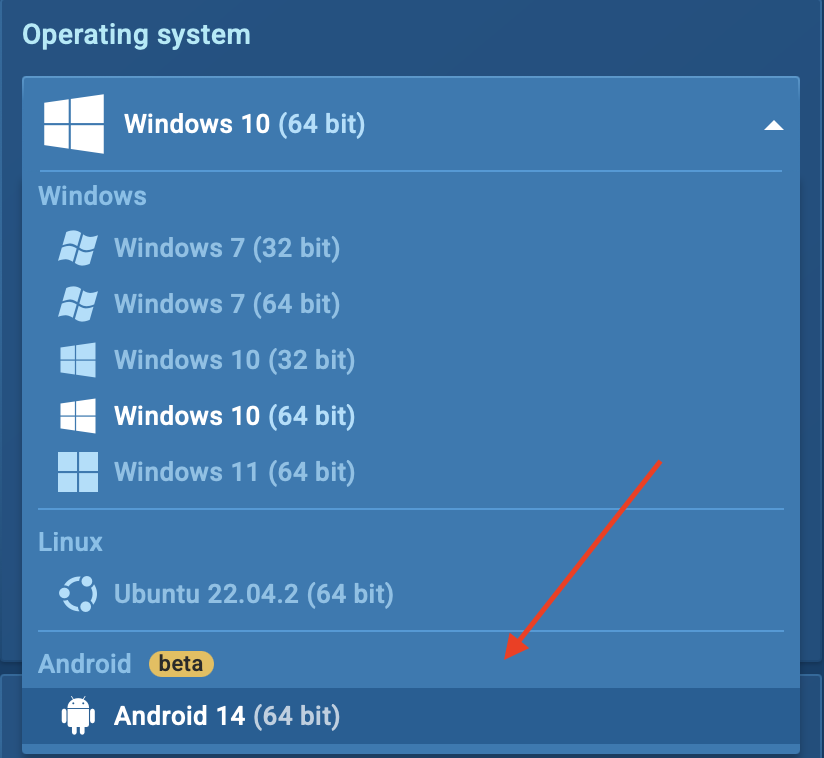
- Upload the APK file – Drag and drop the file into the sandbox.
- Start the investigation – Run the file and observe its behavior in real time.
See It in Action: Analyzing Mobile Malware Inside ANY.RUN’s Android Sandbox
Let’s look at real-world malware cases to see how ANY.RUN’s interactive sandbox makes Android threat analysis easier and more effective.
One notorious Android malware family is Coper, a banking trojan that targets financial apps, steals user credentials, and intercepts SMS messages. Attackers use it to bypass two-factor authentication (2FA) and take full control of compromised devices.
With ANY.RUN’s Android OS sandbox, we can break down exactly how this malware behaves in real time.
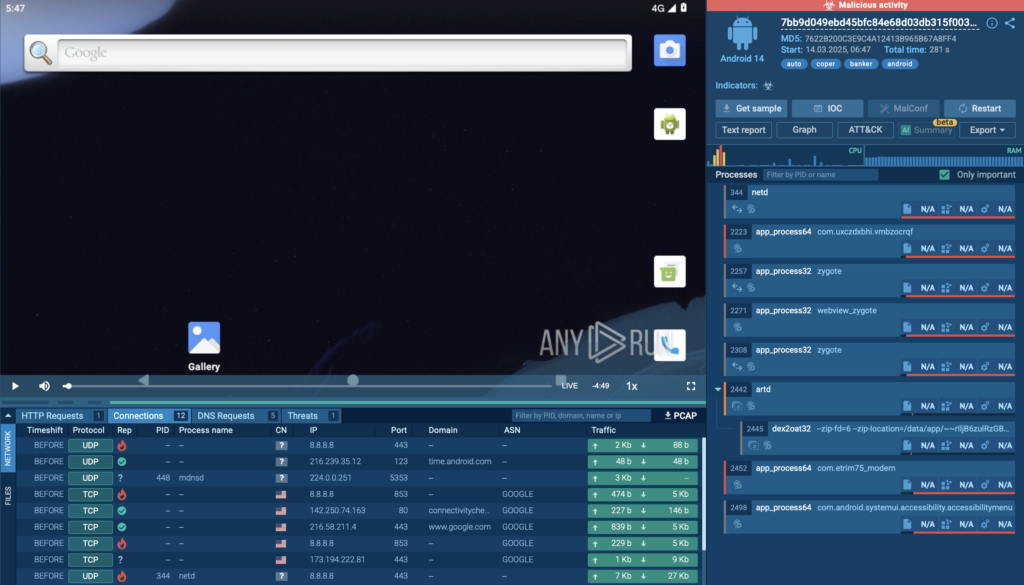
Instant Detection with Interactive Analysis
The first thing you’ll notice after running an analysis is that ANY.RUN immediately flags suspicious activity. In this case, we see a red alert in the top right corner, signaling that the APK file is performing dangerous actions.
Since the sandbox is fully interactive, we can engage with the app just like on a real Android device. This means:
 Opening the malware-infected app and seeing how it behaves
Opening the malware-infected app and seeing how it behaves  Granting or denying permissions to observe how it reacts
Granting or denying permissions to observe how it reacts  Triggering functions like keylogging to uncover hidden actions
Triggering functions like keylogging to uncover hidden actions
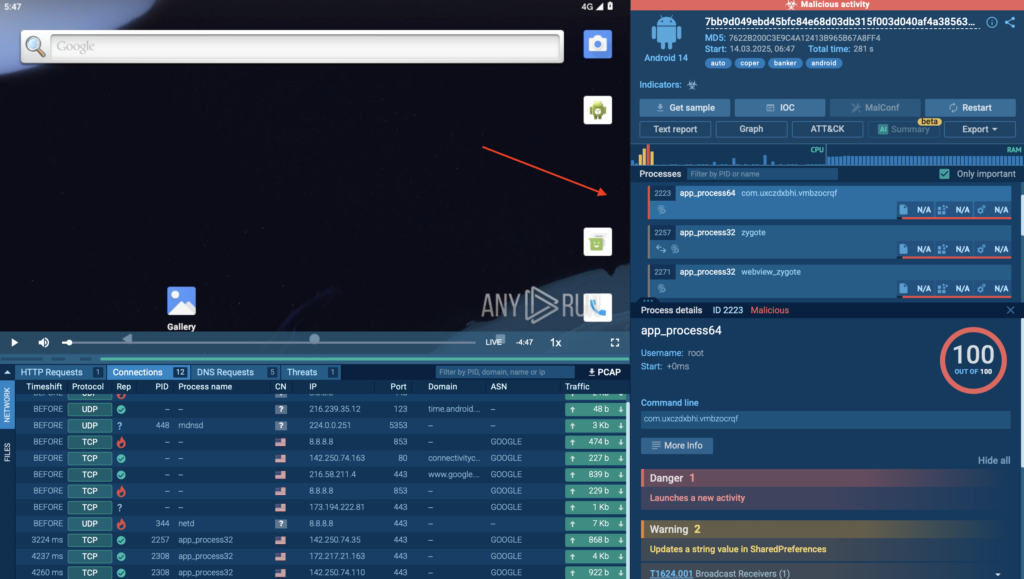
Digging into the Tree of Processes
To understand how Coper operates under the hood, we check the Process Tree section, which provides a structured breakdown of all executed processes.
Here, you can:
- See which processes are spawned by the malware
- Identify connections to suspicious services or commands
- Detect any attempts to gain persistence or execute additional payloads
The Process Tree is located in the right part of the analysis screen, giving a clear and organized view of how the APK interacts with the system.
Instead of manually tracking logs, security teams get a clear breakdown of malicious actions in a simple, visual format.
Understanding the Attack Tactics with MITRE ATT&CK Mapping
Next, we head to the MITRE ATT&CK Matrix section, which helps map out exactly what techniques and tactics Coper is using.
Inside ANY.RUN, this can be found under the MITRE ATT&CK tab, where you get a structured breakdown of:
- The specific attack techniques used (e.g., credential theft, keylogging, SMS interception)
- The broader tactics the malware follows (e.g., persistence, privilege escalation)
- Links to detailed explanations for deeper research
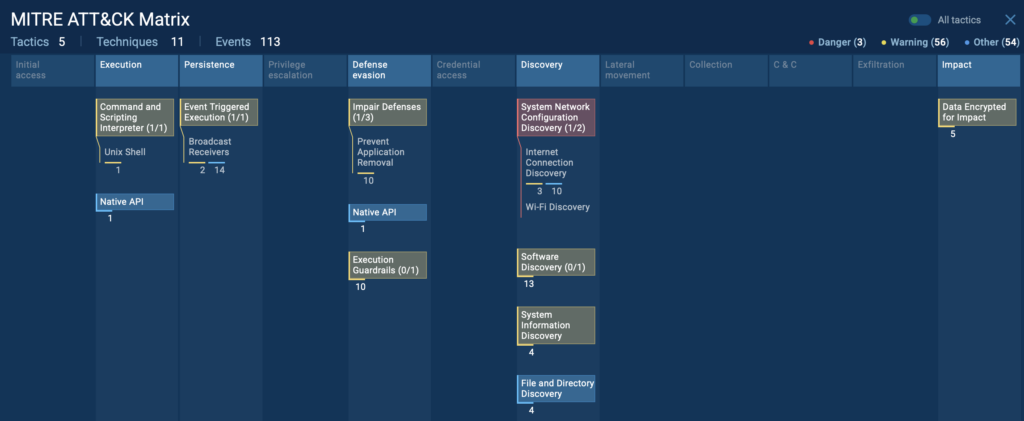
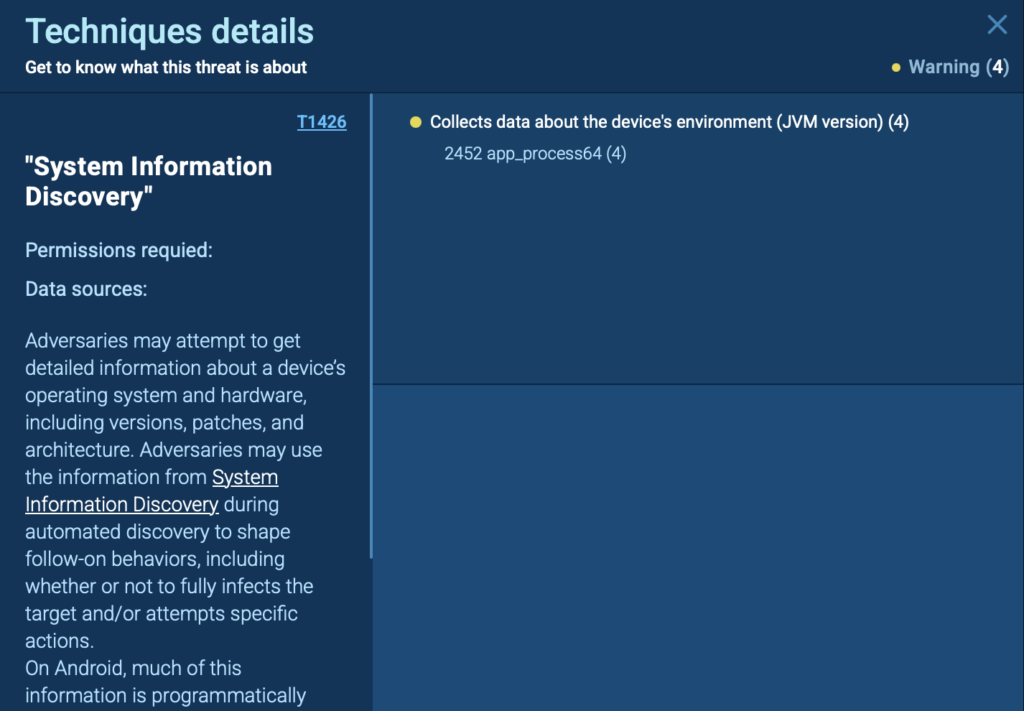
By clicking on any technique, you get a detailed description of how the attack works, making it easier to correlate threats and improve security defenses.
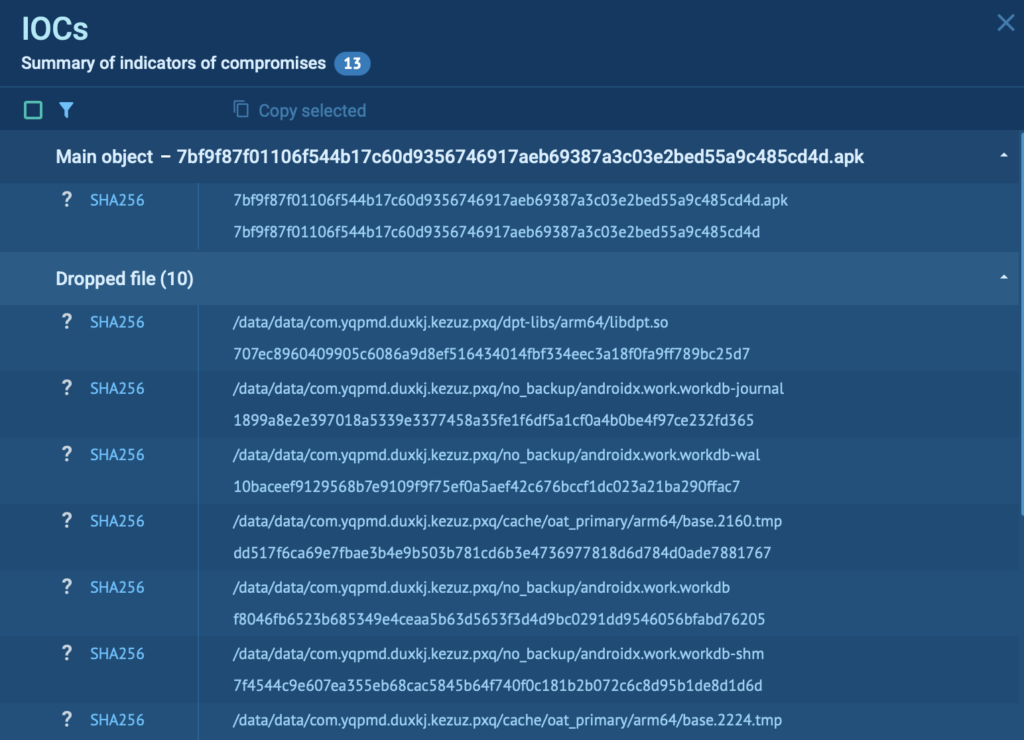
Collecting IOCs for Threat Intelligence
Once the analysis is complete, ANY.RUN generates structured, in-depth reports, allowing SOC teams to get:
- Malicious URLs and IP addresses
- Dropped or modified files
- Registry changes and system modifications
These IOCs can be exported and shared for further action, helping organizations update security rules, improve detection, and prevent future infections.
In this analysis of GoldDigger malware, we can see a collection of useful IOCs by clicking the “IOC” button in the top right corner of the screen.
Generating a Structured Report for Easy Sharing
Once the analysis is complete, it’s time to generate a detailed report. In ANY.RUN, this can be done in the Reports section, allowing SOC teams to:
 Quickly escalate cases with clear, organized evidence.
Quickly escalate cases with clear, organized evidence.  Share findings across teams for improved collaboration.
Share findings across teams for improved collaboration.  Enhance future detection strategies using real-world behavioral data.
Enhance future detection strategies using real-world behavioral data.
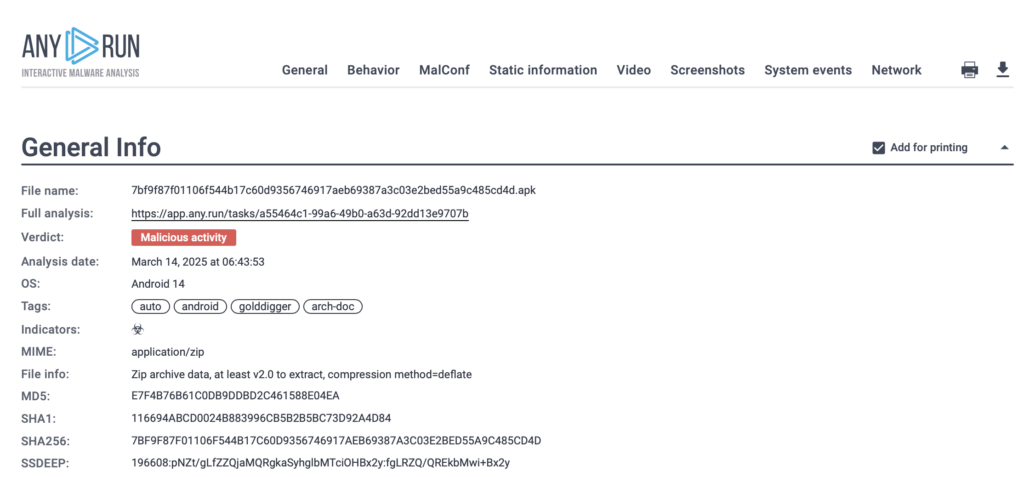
Having a clear, documented report helps SOC teams, threat hunters, and incident responders work more efficiently, ensuring that findings are communicated effectively across teams.

Turn Your Team’s Hours of Android Malware Investigation into Minutes
ANY.RUN’s Android OS support is a whole new way to investigate mobile threats with speed and precision.
Whether your security team is tackling incident response, malware research, or threat hunting, this release helps businesses detect Android threats easier, cut investigation time, and strengthen security operations.
- It’s fast – No waiting for static scans or manual reverse engineering. See how an APK behaves in seconds
- It’s interactive – Click, explore, and engage with malware just like you would on a real Android device.
- It’s detailed – Track every action with process trees, MITRE ATT&CK mapping, and real-time network insights.
- It’s fully cloud-based – Run Android malware investigations anytime, anywhere, without worrying about infrastructure.
- It’s built for teams – Generate structured reports, share findings, and collaborate on investigations seamlessly.
Start your first Android analysis today and experience the precision of mobile malware analysis inside a real ARM-based sandbox.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post Expose Android Malware in Seconds: ANY.RUN Sandbox Now Supports Real-Time APK Analysis appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
