New Pre-Installed Dev Tools for Deep Sandbox Malware Analysis
ANY.RUN sandbox just got even more powerful thanks to a new pre-installed development software set in its virtual machines (VMs).
Building on our existing pre-installed sets, we’re introducing this new option to give researchers even more flexibility and advanced tools for analyzing highly specific and complex malware inside the sandbox.
With this update, before launching an analysis session, users can select the “Development” software set to instantly load a specialized toolkit designed for deep malware investigation. This is especially useful for working with Python-based malware, Node.js-based threats and adding deeper debugging and inspection capabilities.
Let’s take a closer look at this latest addition and discover how you can use it!
Why This Update Matters: Key Benefits
This new software set significantly enhances malware research by providing tools that cater to specific types of malware. Here’s why we’ve added this soft set:
- Analyze new types of malware (Python/Node.js-based threats): Many modern malware samples are written in Python or Node.js, and having the right tools pre-installed makes their analysis more efficient.
- Improved debugging and reverse engineering: The presence of advanced debuggers and analysis tools helps senior analysts dive deeper into malware behavior, extract insights, and develop better detection techniques.
- Faster and more efficient research sessions: No more manual installation, just launch the VM, and all necessary tools are available, saving time and improving workflow.
- Expanding the database of ANY.RUN: By introducing new analysis scenarios, this update broadens the platform’s capabilities, making it more useful for a wide range of malware research and forensic investigations.

What’s Included in the New Software Set?
The pre-installed software set includes essential tools that malware analysts, security researchers, and threat hunters frequently use for analyzing complex threats:
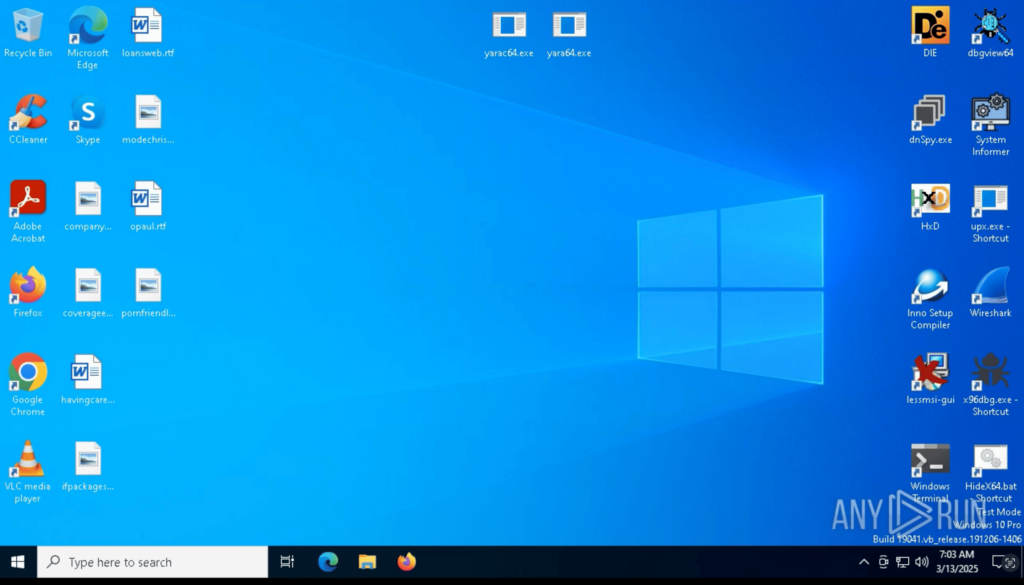
List of Pre-Installed Tools
- Python (latest version) – Important for analyzing Python-based malware, executing scripts, and automating analysis.
- Node.js (latest version) – Helps in investigating Node.js-based malware and executing malicious scripts in a controlled environment.
- DebugView – Captures real-time debug output from Windows applications, useful for identifying malware behavior.
- DIE (Detect It Easy) – A tool for identifying executable file packers, obfuscators, and compilers used by malware authors.
- dnSpy – A powerful .NET debugger and decompiler, ideal for reverse-engineering malware written in C# or VB.NET.
- HxD – A hex editor that allows analysts to inspect and modify binary files, memory, and disk structures.
- Process Hacker – An advanced process monitoring tool for tracking system behavior and detecting malicious activity.
- x64dbg – A dynamic debugger for analyzing malware at the assembly level, often used for unpacking and reverse engineering.
- Wireshark PE – A network protocol analyzer for capturing and inspecting suspicious network traffic during malware execution.
How to Use the New Software Set in ANY.RUN
This pre-installed toolset is now available for ANY.RUN Enterprise users running malware analysis on Windows 10 (64-bit) virtual machine.
Steps to Enable the Pre-Installed Software Set:
- Go to ANY.RUN’s sandbox configuration.
- Select Windows 10-64 as the operating system.
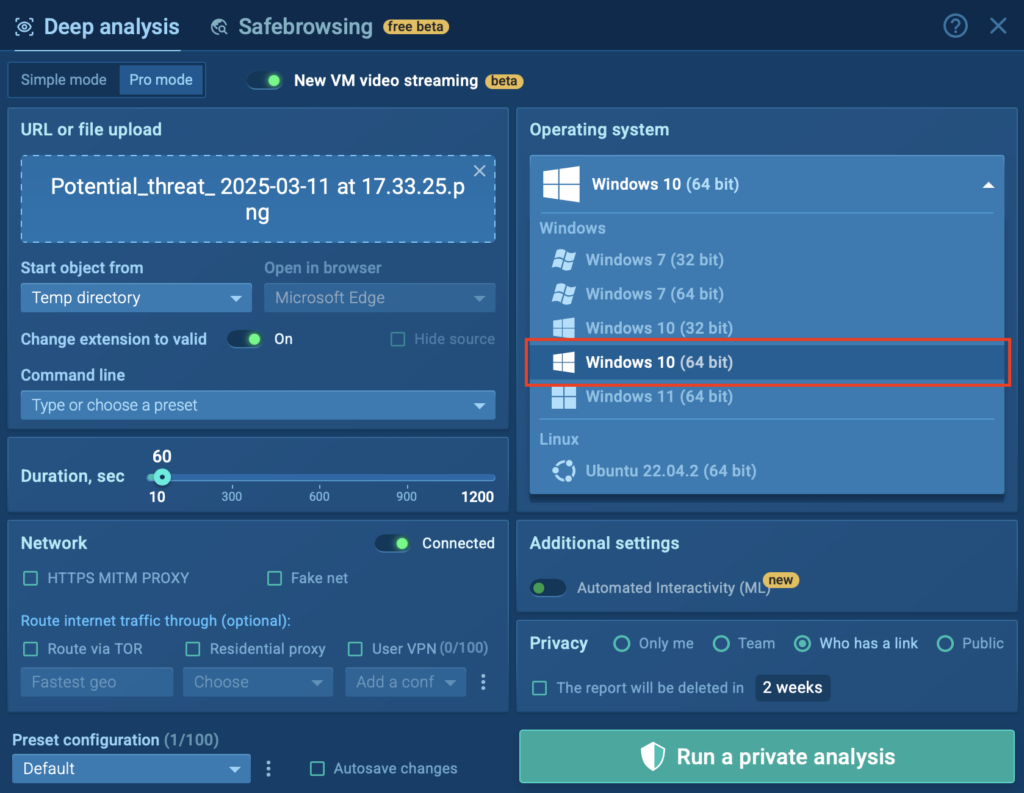
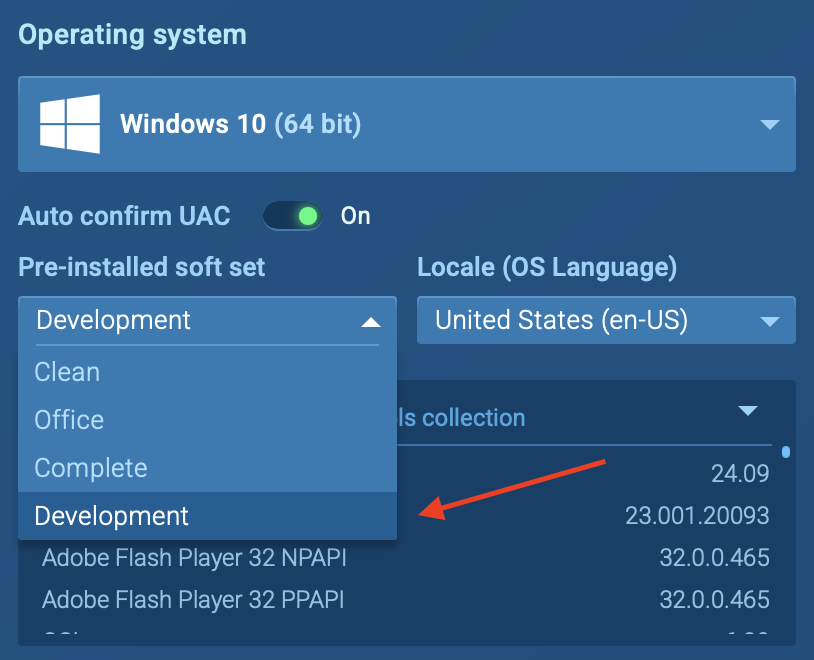
- In the “Pre-installed Soft Set” option, choose “Development”.
- Start the analysis session, and the selected tools will be automatically available inside the VM.
Let’s look at a couple of practical examples of how this update improves research workflows.
Example 1: Extracting MSI Package Files with Lessmsi
In the following analysis session, we can see how the Lessmsi tool helps extract files from MSI packages without executing them.
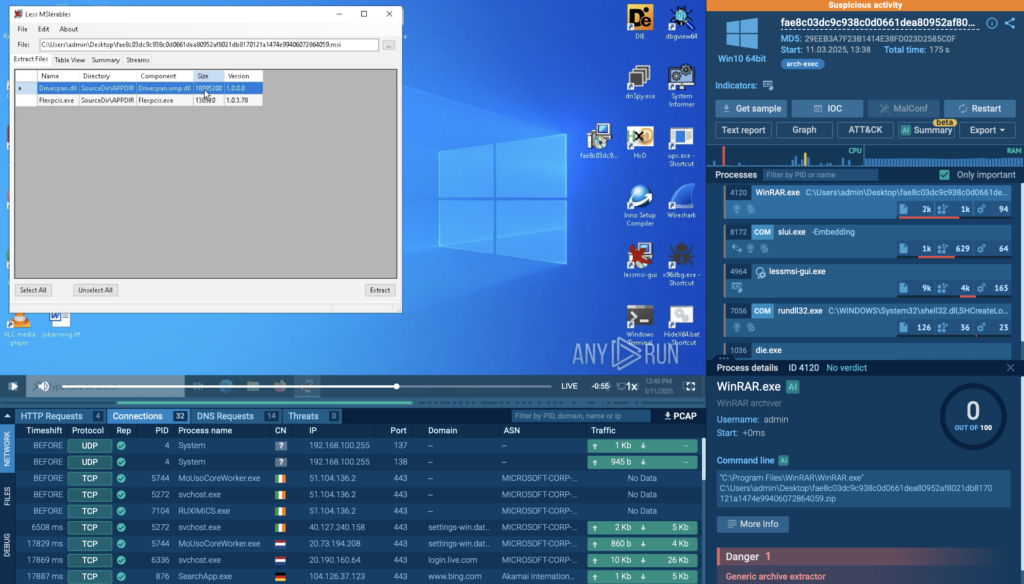
This is particularly useful for researchers who want to inspect the contents of an installer safely and identify any suspicious files or embedded scripts.
During this process, the Detect It Easy (DiE) tool is also used, helping analysts gather more details about the extracted binaries, such as file signatures, packers, and obfuscation methods.
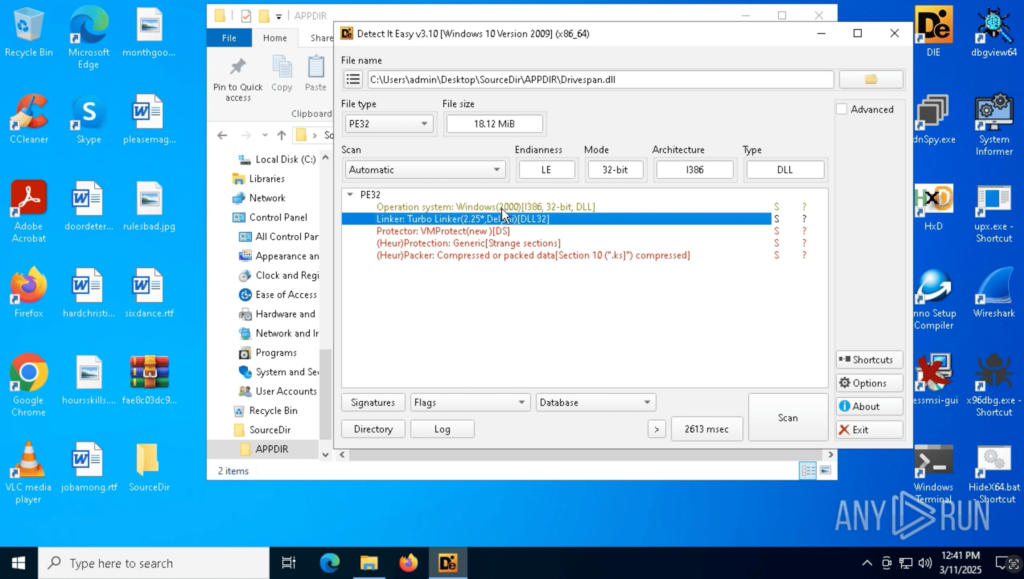
By combining these tools, users can uncover hidden threats inside MSI packages without the risks associated with running them.
Example 2: Debugging Malware with x64dbg
In this analysis session, x64dbg is used, a powerful debugger that allows users to step through malware execution, analyze code behavior, and identify hidden functionality.
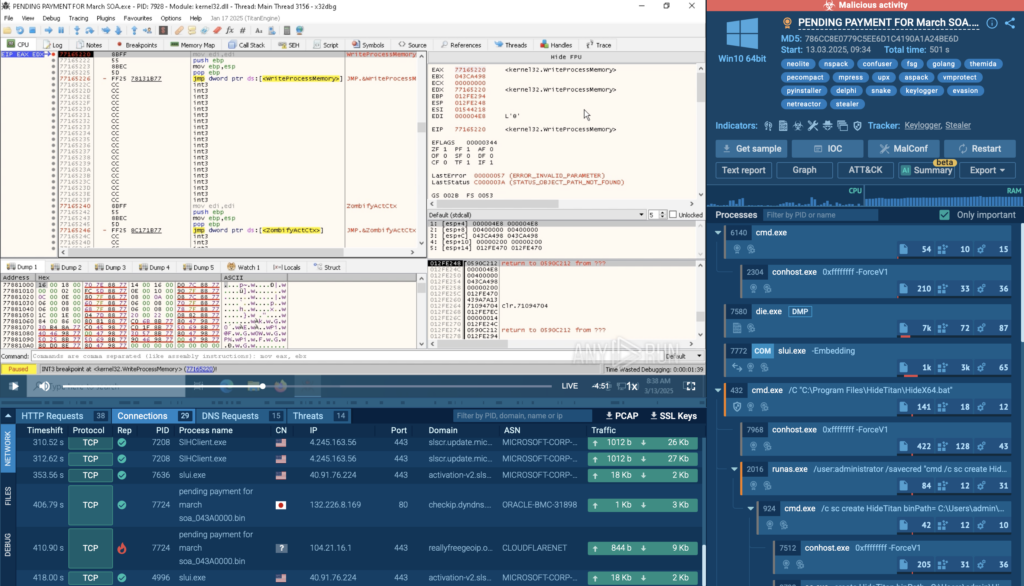
This is particularly useful for unpacking malware, bypassing obfuscation techniques, and understanding how the sample interacts with the system.
Example 3: Searching Inside Unpacked Binaries with HxD
In this analysis session, HxD is used, a hex editor that allows users to search within all types of files for specific strings, patterns, or hidden data. This is useful when working with unpacked binaries, encrypted payloads, or malware that tries to conceal its real purpose within other formats.
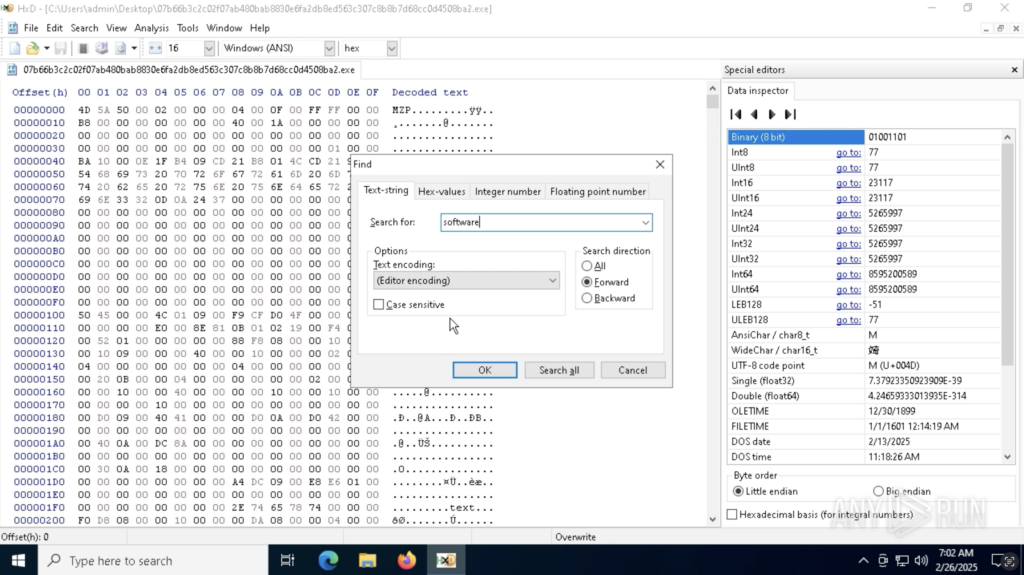
By using HxD inside ANY.RUN’s sandbox, analysts can quickly locate critical data inside malware samples without needing to transfer files externally, making the analysis process safer and more efficient.
In this case, the word “software” was searched with the help of HxD inside our secure environment to look for relevant information.
Conclusion
With the new pre-installed development software set, malware analysis in ANY.RUN just got a whole lot easier. Instead of jumping between different tools and setups, everything you need is already there inside the sandbox, ready to go.
For businesses, this means faster threat detection and a more seamless workflow, all in a secure, controlled environment.
Give it a try and see how much easier malware detection and analysis can be!
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post New Pre-Installed Dev Tools for Deep Sandbox Malware Analysis appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

