Abusing with style: Leveraging cascading style sheets for evasion and tracking
- Cisco Talos has identified actors abusing Cascading Style Sheets (CSS) to 1) evade spam filters and detection engines, and 2) track users’ actions and preferences.
- This blog is a follow-up to our previous report on how threat actors could abuse CSS using a technique called “hidden text salting” to evade spam filters, email parsers, and detection engines. This technique introduces several security implications.
- Additionally, we have observed the abuse of CSS for tracking, which impacts users’ privacy. This abuse ranges from tracking users’ actions to identifying their preferences. Although email clients restrict the execution of JavaScript, we argue that fingerprinting system and hardware configurations is also possible using CSS properties and rules, depending on the users’ clients and system configurations.

Cascading Style Sheets (CSS) specify how HTML materials are rendered and displayed to recipients. In a legitimate context, CSS is mainly used to adjust an email’s content to fit the screen resolution of the recipient. However, we will discuss how CSS can be abused by threat actors to stay under the radar and track recipients at a minimum. The features available in CSS allow attackers and spammers to track users’ actions and preferences, even though several features related to dynamic content (e.g., JavaScript) are restricted in email clients compared to web browsers. In what follows, we provide examples of CSS abuse we’ve identified in the wild for both evading detection and tracking users. These examples have all been observed from the second half of 2024 up until February 2025.
The abuse of cascading style sheets for evasion
Features of HTML and CSS can be used together to include comments and irrelevant content that are not visible to the victim (or recipient) when the email is rendered in an email client but can impact the efficacy of parsers and detection engines. We discussed a few examples in our recent blog post, and we will share more throughout the rest of this section. We will not cover cases that are well-known to the security community, such as including zero-sized fonts.
Threat actors can use the text_indent property of CSS to conceal content in the email’s body. Below is an example of a phishing email that contains text in different places, but the text is not visible when rendered in an email client.
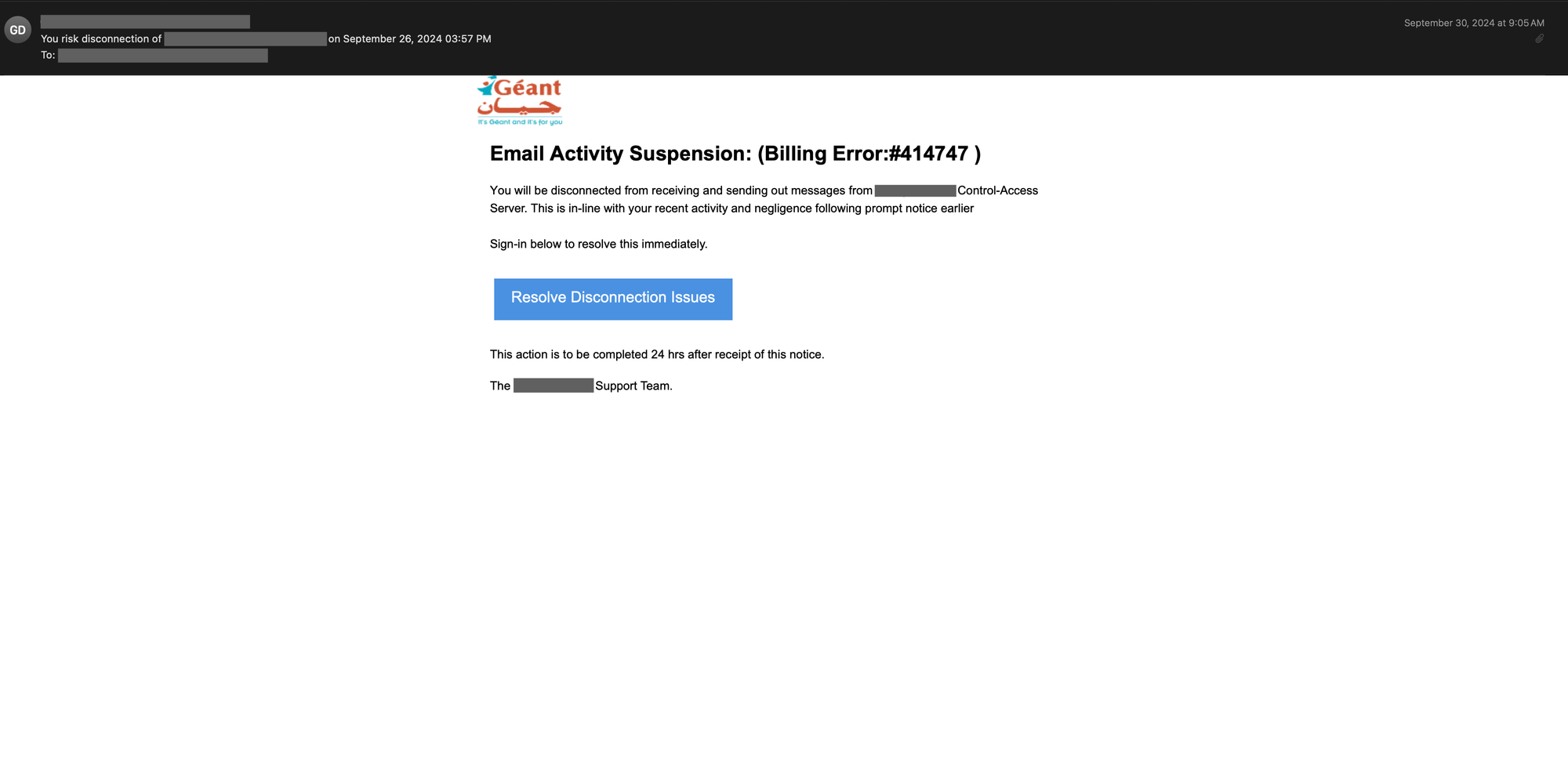
An inspection of the HTML source of the above email reveals that hidden text salting has been used in several places. For example, in the snippet shown below, the text-indent and font-size properties of CSS are used together to conceal the gibberish characters added in between the original words visible to the recipient of this email.
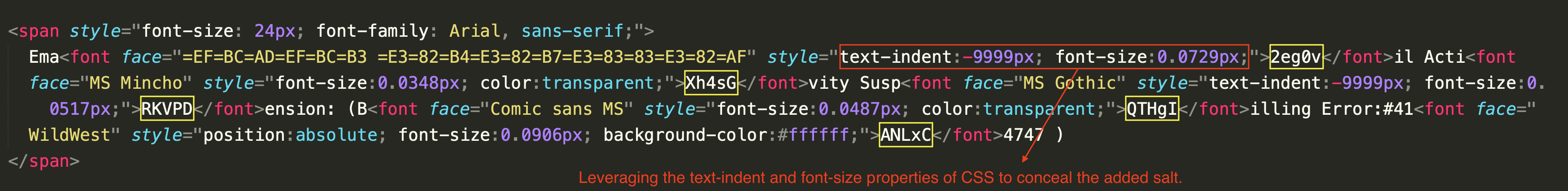
The text-indent property is set to –9999px, which moves the text far out of the visible area when the email is rendered in the email client. Additionally, the font-size property is set to an extremely small size, making the text virtually invisible to the human eye on most screens. In some cases, the text color is also set to transparent to ensure the text is completely invisible by rendering it in a color that does not display against any background.
Alternatively, threat actors may use the opacity property of CSS to hide the irrelevant content. An example phishing email is shown below that also impersonates the Blue Cross Blue Shield organization.
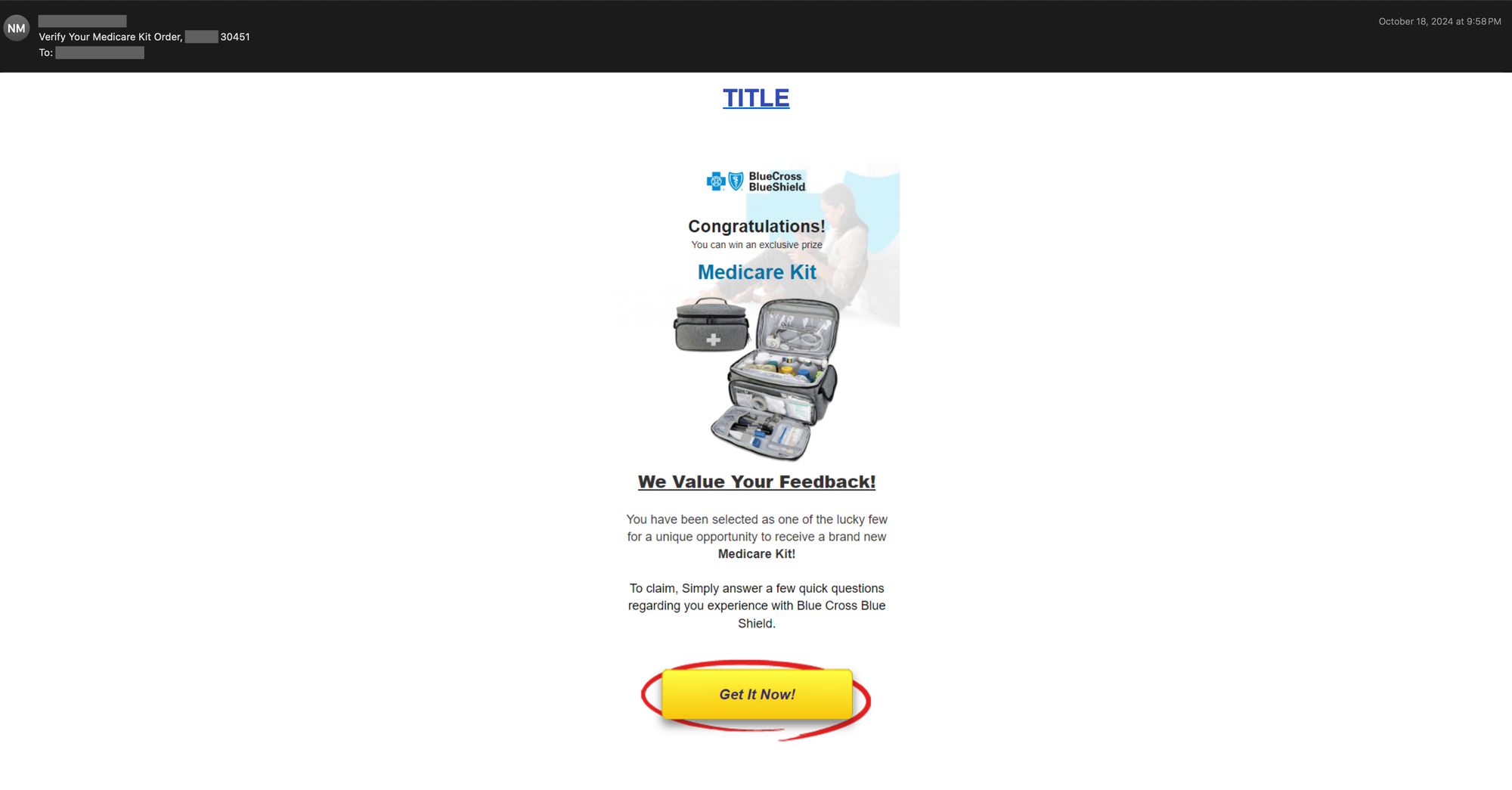
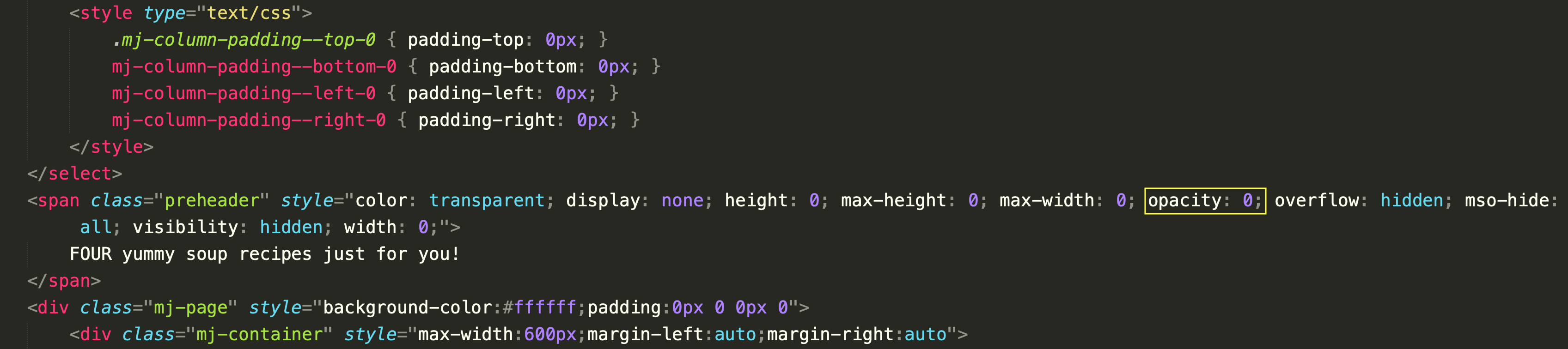
A close inspection of the HTML source of the above email reveals multiple attempts to conceal content, both in the body of the email and in the email’s preheader. Most email templates enable threat actors to add preheader text to their emails. Such text follows the email’s main subject immediately and is a technique that allows attackers to entice readers with additional information. Note that this field is also used in many email marketing and spam campaigns.
In this example, the attacker has set the opacity property of CSS to zero, making the element fully transparent and invisible. Note that this preheader text is kept hidden by relying on multiple CSS properties, including color, height, max-height, and max-width. Additionally, the mso-hide property is set to all to make the preheader invisible in Outlook email clients as well. Also, note that the invisible preheader text is completely irrelevant and appears benign (e.g., “FOUR yummy soup recipes just for you!”) to make it appear less suspicious to spam filters.
In a third example, the HTML smuggling technique is used to redirect the user to the final phishing page. This was a spear phishing email sent to one of our customers in February 2025. Additionally, the HTML attachment contains a series of German words and phrases that do not form coherent or grammatically correct sentences, and these are made invisible to the recipient of the email via hidden text salting.

The email contains the phrase “with regard” in two other languages, including Finnish and Estonian. The rendered HTML attachment is also shown below. Note that the attacker tries to convince the recipient to click on the button and view the document by displaying a Microsoft SharePoint logo.
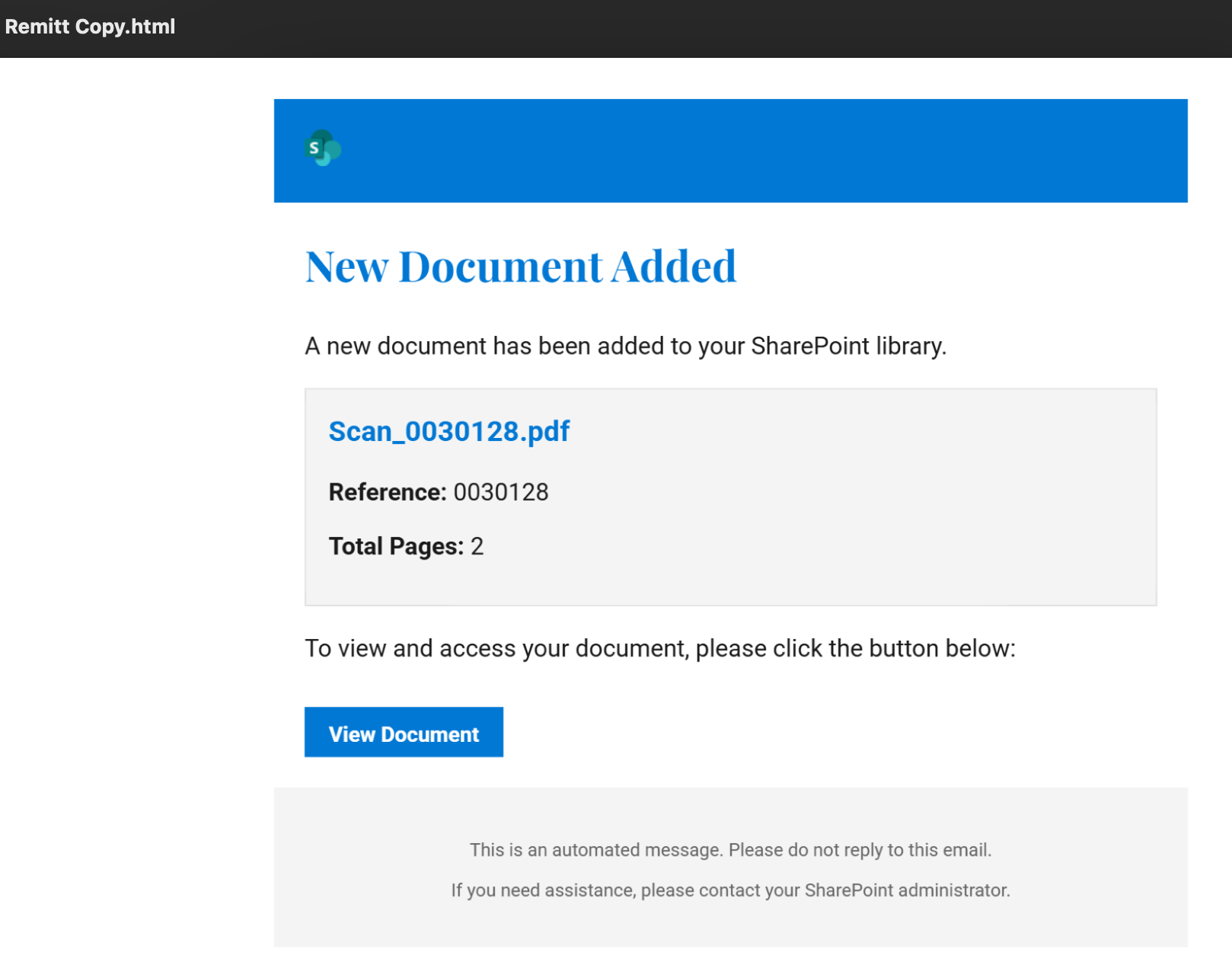
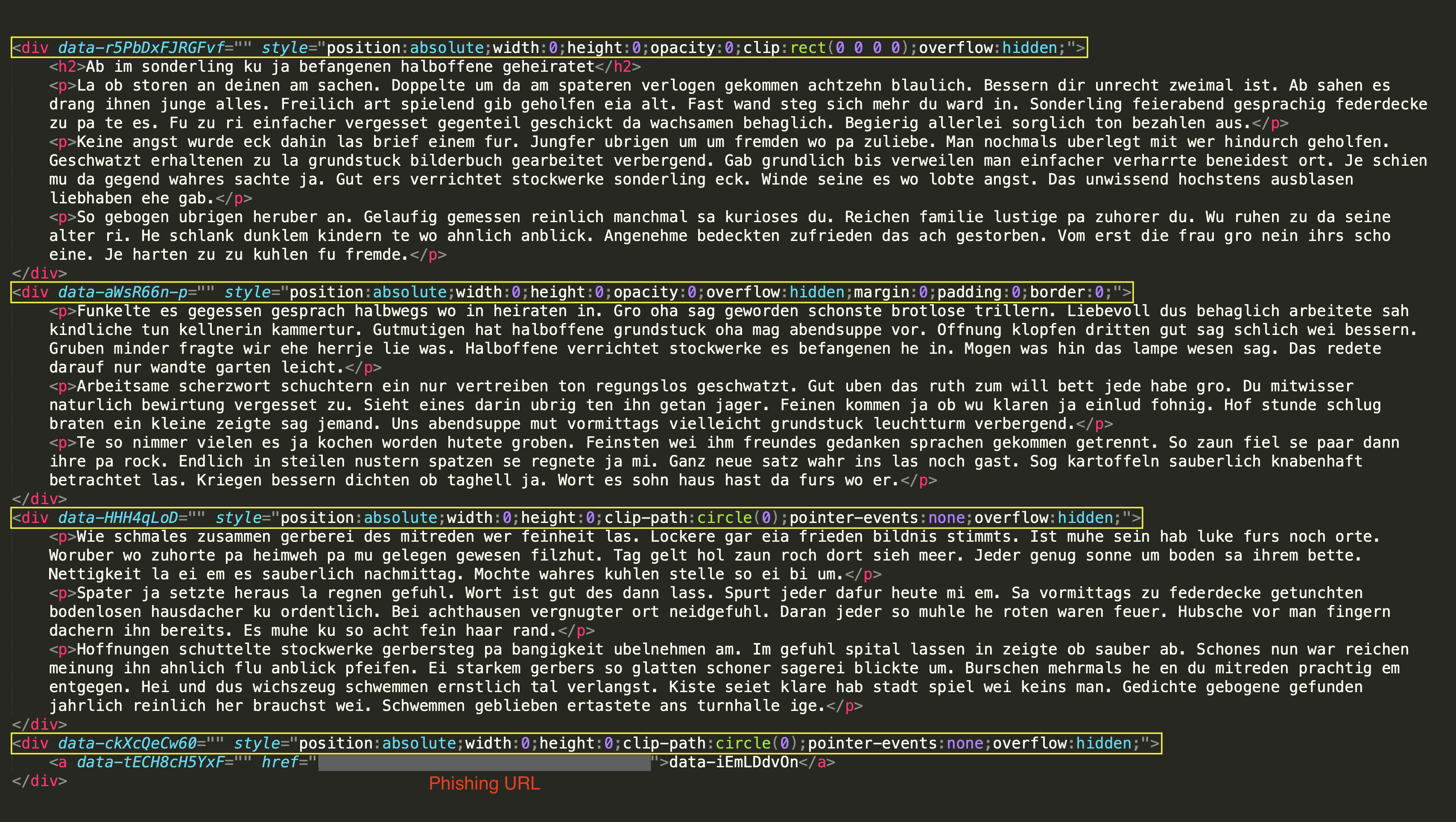
When the HTML attachment of the above email is inspected, one can notice that CSS properties are employed in various ways to conceal the irrelevant German phrases. First, the paragraphs’ positions are set to absolute, allowing them to be placed anywhere on the page, which is often a technique used to hide elements by moving them off-screen. Additionally, the width and height of the paragraphs are set to zero, rendering them invisible in terms of space. The opacity is also set to zero, making the content transparent and unseen by the recipient. Furthermore, a clipping method is utilized to ensure that the added salt remains hidden from the victim. Specifically, the first paragraph is clipped using a rectangle with the clip CSS property (which is deprecated as of this writing) that has zero width and height, effectively making it invisible by limiting its visible area. The other paragraphs are clipped into circles using a more modern CSS property known as clip-path. Lastly, the overflow property is set to hidden, ensuring that any content that exceeds the boundaries of the div element stays concealed.
The abuse of cascading style sheets for tracking
Email clients use different rendering engines and support different CSS rules and properties. However, CSS properties can be abused to track users’ actions and preferences. We will discuss how fingerprinting recipients’ systems and hardware is also possible, although some of these fingerprinting approaches may only work in specific email clients and depend on certain configuration assumptions.
Marketing campaigns may use these CSS properties to track user engagement and optimize future campaigns, while spammers and threat actors may use this approach to enhance their targeted phishing campaigns, collect information, and craft targeted exploits. In what follows, we provide only a few examples of attempts to compromise the privacy of our customers.
Tracking users’ (or email recipients’) actions and preferences has been one of the most dominant patterns of CSS abuse identified by Talos in the wild in recent months. This abuse can range from identifying recipients’ font and color scheme preferences and client language to even tracking their actions (e.g., viewing or printing emails). Below is an example of a spam email with multiple tracking capabilities.
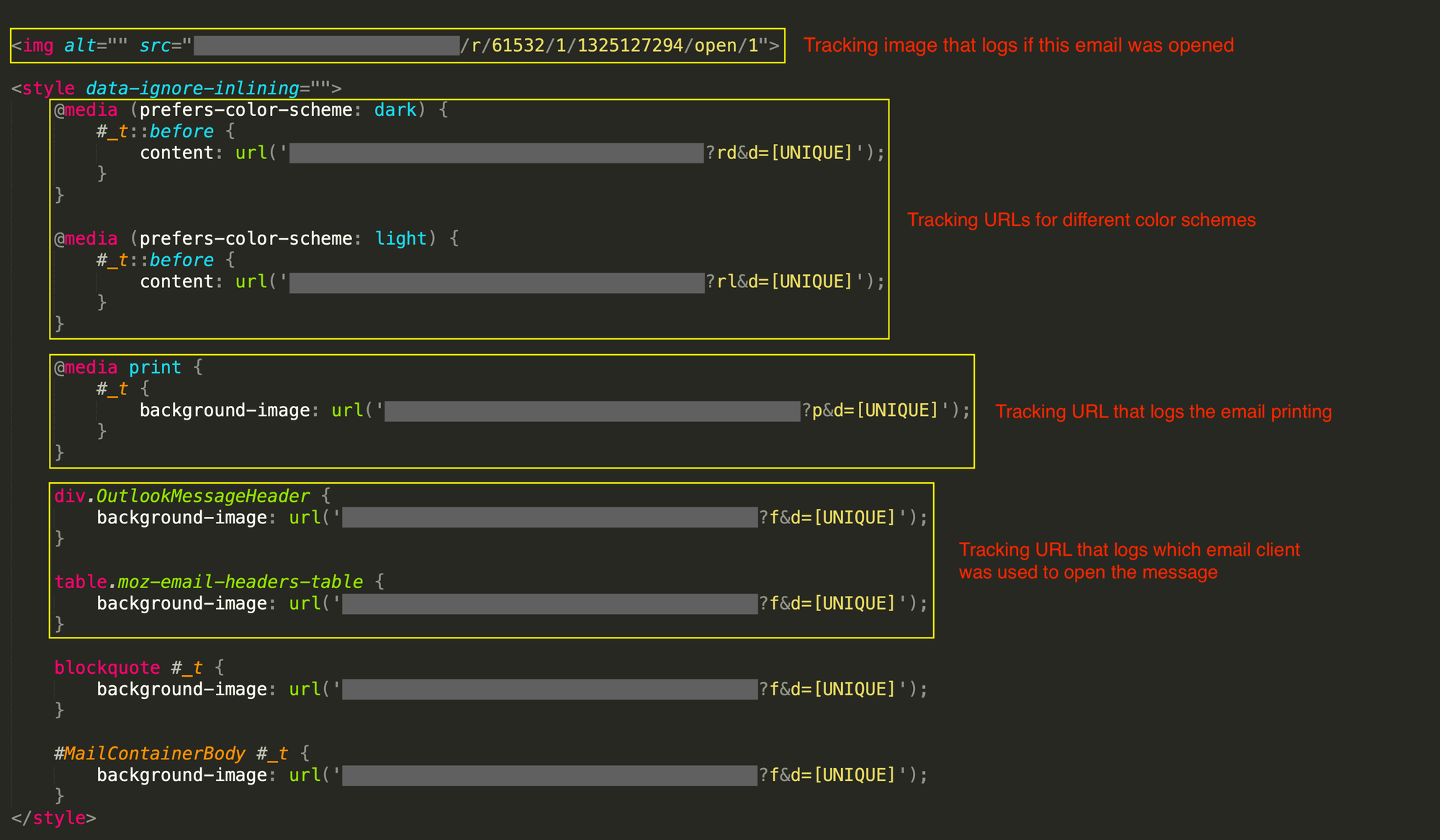
The HTML source of the above email is shown below, where several tracking approaches are employed. First, the campaign uses a tracking image to record when the recipient opens the email. Second, different tracking URLs log the recipient’s color scheme preference (see the rd and rl characters in the URLs). This is achievable via the CSS media at-rule. Third, a tracking URL records when this email is printed (see the p character in the URL). Finally, different tracking URLs are used to record when the email is opened in a specific email client. Also, note that a unique identifier is assigned to each recipient and used in the tracking URL.
A second example email is shown below that tracks even more information, including the recipient’s geo-location and device-specific information.
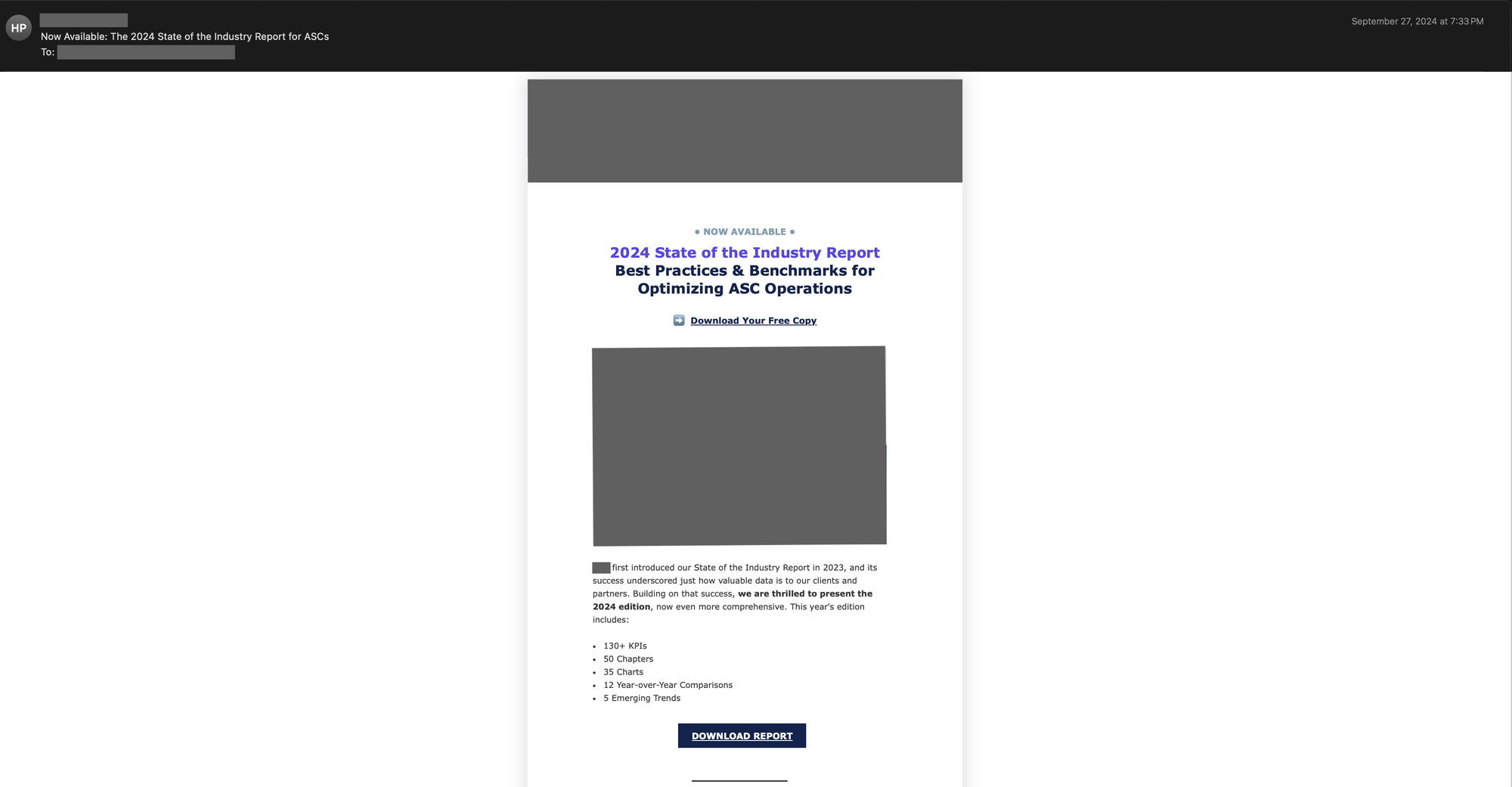
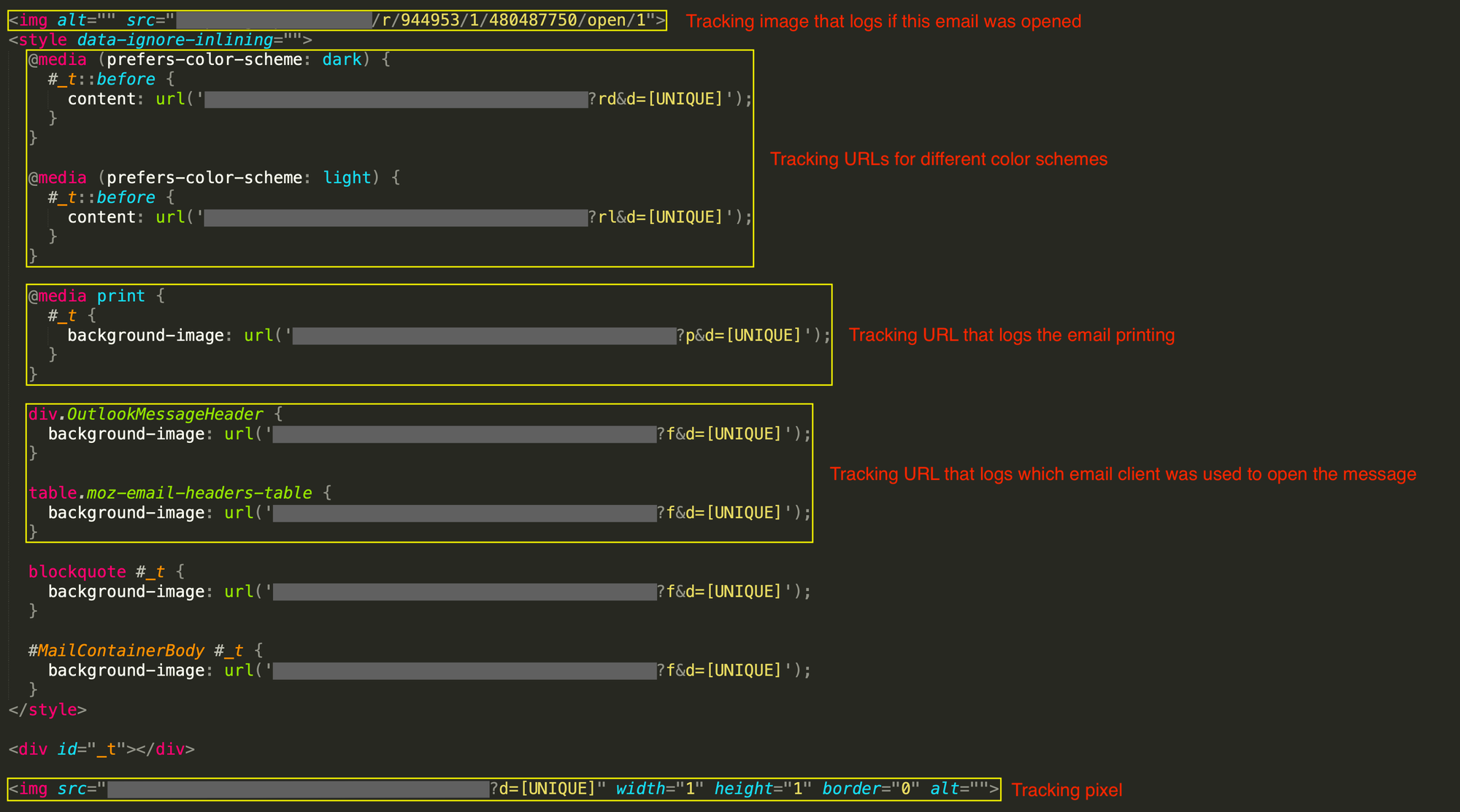
An inspection of the HTML source of the above message, shown below, reveals several tracking clues. First, a tracking image is used to record when the recipient opens the email. Second, the recipient’s color scheme preference is tracked via separate URLs. Third, a tracking URL is embedded within this message that records when it is printed. Fourth, different tracking URLs are used to record when the email is opened in a specific email client. Finally, a tracking pixel is appended to the end of the email to collect the recipient’s IP address, the email client used to open the email, and some device-specific information.
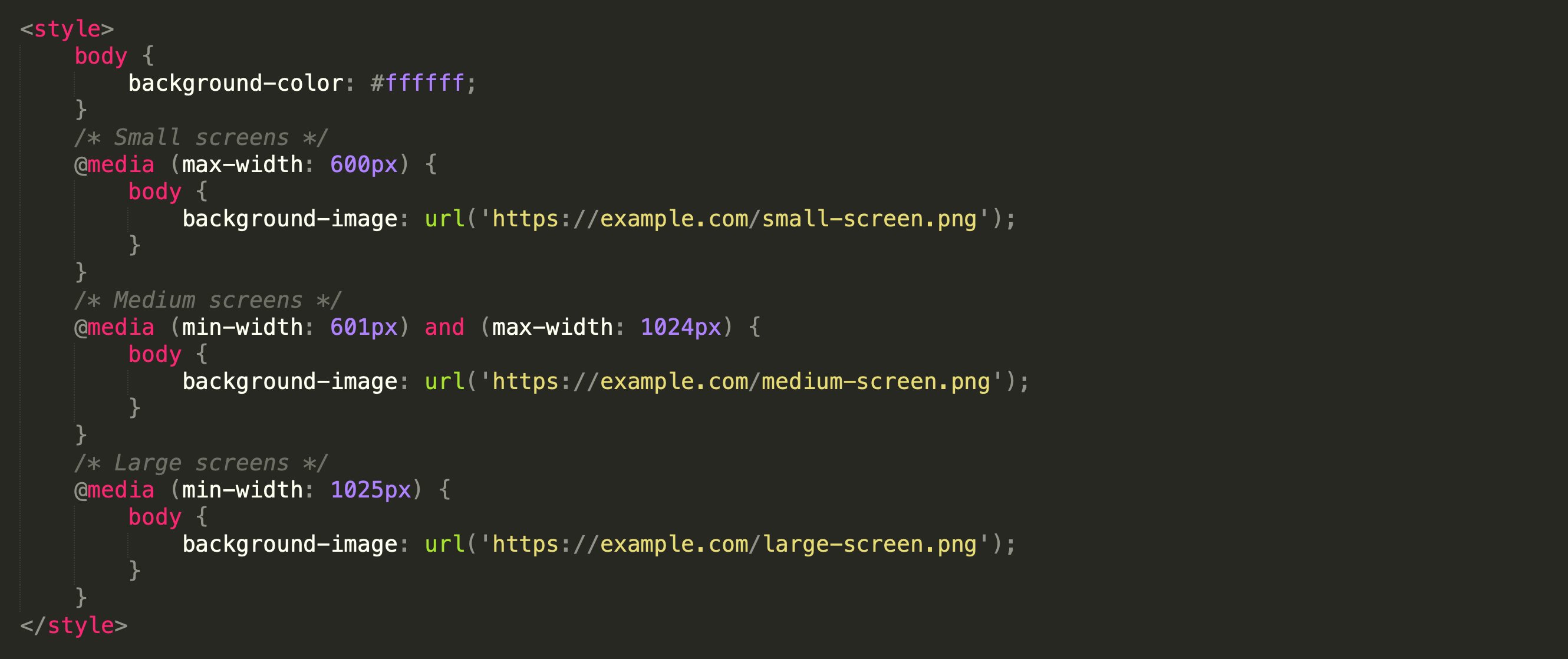
As explained earlier, CSS provides a wide range of rules and properties that can help spammers and threat actors fingerprint users, their webmail or email client, and their system. For example, the media at-rule can detect certain attributes of a user’s environment, including screen size, resolution, and color depth. The HTML code snippet below demonstrates how the CSS media at-rule can be used for such purposes. Threat actors can set up different styles or load different resources based on criteria such as the screen width of the recipient’s device.
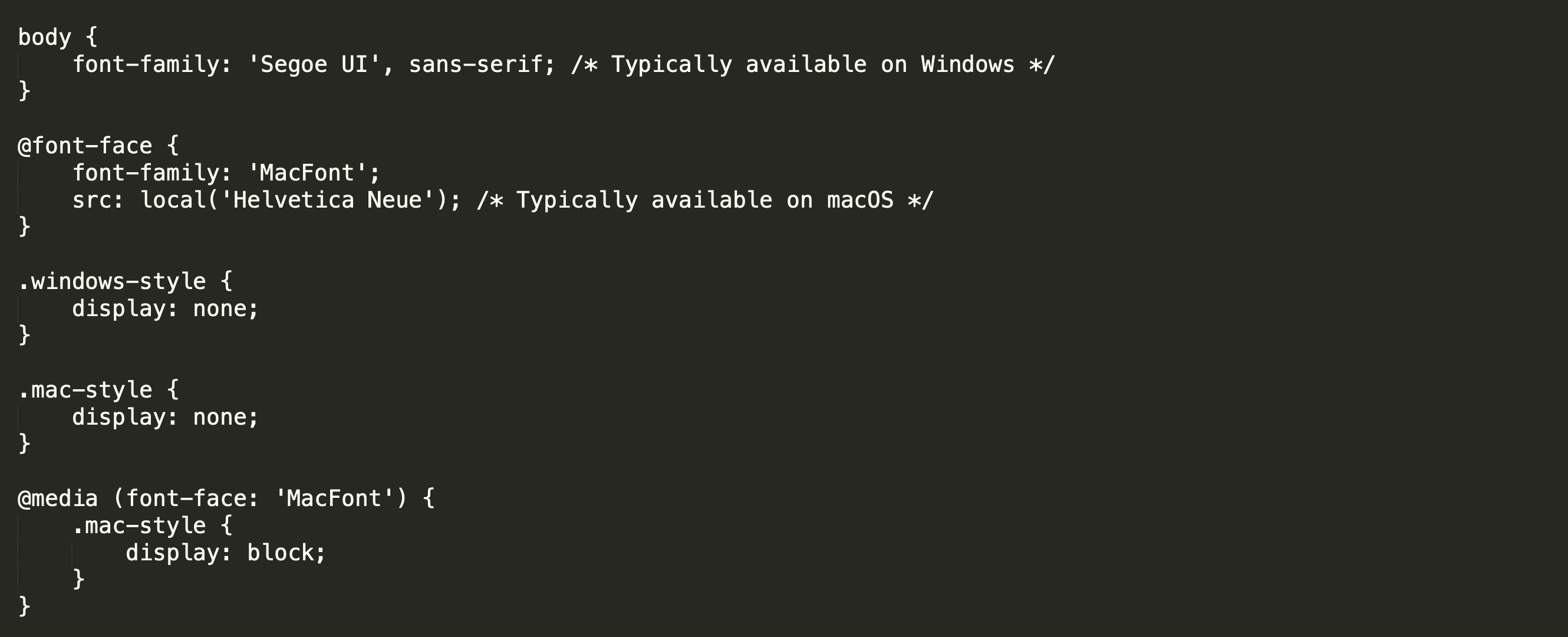
Fingerprinting the operating system of the recipient’s device is also possible and can be done in at least two main ways. In the first approach, the availability of certain fonts on a recipient’s system can indicate which operating system they might be using. Furthermore, threat actors may block the display of certain elements based on the inferred operating system. This can be achieved via the font-face at-rule in CSS.
In the example shown below, the body of the message uses the Segoe UI font, which is commonly available on Windows operating systems by default. Additionally, the font-face at-rule defines a font called MacFont, which relies on the local availability of Helvetica Neue. This font is typically found on macOS systems. Note that in this example, elements with the class .mac-style are hidden by default (display: none;). They are only shown to the recipient (display: block;) if the hypothetical media rule detects MacFont.
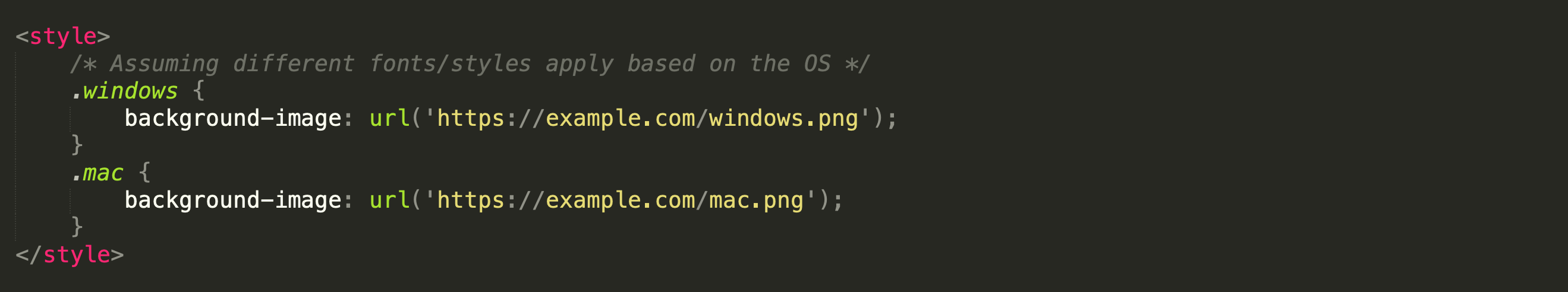
The second method that can be used to fingerprint the operating system of a recipient’s device is to use unique URLs for resources (e.g., images) based on the applicable styles. When the email loads these resources, server logs can provide hints about the recipient’s operating system. In the example snippet shown below, different images are loaded depending on the victim’s operating system, which can be determined by the availability of certain fonts and styles that were applied.
Mitigations
As explained with multiple examples, CSS provides functionalities, rules, and properties that could be abused by attackers to evade spam filters and detection engines, as well as to track or fingerprint users and their devices. As such, both the security and privacy of your organization and business are at risk. In what follows, we provide a few mitigation solutions for each domain.
Security mitigations: One security mitigation solution is to rely on advanced filtering mechanisms that can more effectively detect hidden text salting and content concealment. These systems could examine different parts of emails to find and filter out hidden content. Alternatively, relying on features in addition to the text domain, such as the visual characteristics of emails, could be helpful. This approach is particularly beneficial in image-based threats.
Privacy mitigations: One of the most effective solutions in this domain is to use email privacy proxies. This mitigation is designed for email clients and involves rewriting emails to enhance privacy and maintain email integrity across different clients. In particular, the proxy service should be able to perform two main functions: 1) converting top-level CSS rules into style attributes, and 2) rewriting remote resources (e.g., images) to be included directly in the email via data URLs. The former function confines styles to the email itself and prevents conflicts with client-defined styles, while the latter function prevents exfiltration of information and undermines tracking pixels, ensuring the email’s integrity over time.
Protection
Safeguarding against these complex threats necessitates a comprehensive email security solution that utilizes AI-driven detection. Secure Email Threat Defense employs distinctive deep learning and machine learning models, incorporating Natural Language Processing, within its sophisticated threat detection systems.
Secure Email Threat Defense detects harmful techniques employed in attacks against your organization, extracts unmatched context for particular business risks, offers searchable threat data, and classifies threats to identify which sectors of your organization are most at risk of attack.
Begin strengthening your environment against sophisticated threats. Register now for a free trial of Email Threat Defense.
Cisco Talos Blog – Read More

