Enriching ANY.RUN’s TI Feeds with Unique IOCs: How It Works
Threat Intelligence Feeds from ANY.RUN provide a continuously-updated stream of the latest indicators of compromise. They enable SOC teams to quickly detect and mitigate attacks, including the emerging malware and persistent threats.
But how do ANY.RUN’s feeds get enriched with fresh and, most importantly, unique indicators that cannot be found elsewhere?
Let’s find out.
About ANY.RUN’s Threat Intelligence Feeds
ANY.RUN’s Threat Intelligence (TI) Feeds offer an extensive collection of Indicators of Compromise (IOCs) designed to enhance the threat detection capabilities of security systems. These feeds provide detailed information beyond the basics, including malicious IPs, URLs, domains, file hashes, and links to actual analysis sessions. This comprehensive data helps you understand how threats operate and behave in real-world scenarios.
Where does this data come from?
An international community of over 500,000 researchers and cybersecurity pros who upload and analyze real-world malware and phishing samples every day to ANY.RUN’s Public submissions repository.
With TI Feeds from ANY.RUN, organizations can:
- Expand and speed up threat hunting with enriched up-to-date data
- Enhance alert triage and prioritize most urgent issues.
- Improve incident response thanks to better understanding threats and their behaviors.
- Proactively defend against new and evolving threats.
IOCs Provided by ANY.RUN TI Feeds
TI Feeds contain indicators along with additional info like the threat score, which signals the reliability:
- 100: Highly reliable
- 50: Suspicious
- 75: Trustworthy
Here are the indicators you can find in ANY.RUN’s TI Feeds.
IP addresses
Compromised IPs instantly signal of cybercriminal operations, they are often linked to Command-and-Control (C2) servers or phishing campaigns. By analyzing IP addresses, cybersecurity teams can proactively block suspicious traffic and analyze attack patterns and tactics.
Domains
They provide a higher-level view of malicious activity, often connecting multiple IPs or malware instances within a single campaign.
ANY.RUN’s TI feeds provide comprehensive information about domains, including all the details available for IP addresses, such as threat names, types, detection timestamps, and related file hashes.
URLs
URL addresses serve as gateways to distribute malware, execute phishing campaigns, or redirect users to malicious content.
By analyzing URLs, cybersecurity teams can uncover attack patterns, block harmful traffic, and prevent unauthorized access to systems and data.
How ANY.RUN’s TI Feeds Are Enriched with Unique IOCs
There are several features of Threat Intelligence Feeds stand out, but the one of the key factors is the way we collect indicators. Here are the two methods we use to get the latest and the most accurate indicators.
IOCs Extracted from Malware Configurations
TI Feeds are fueled by the data from ANY.RUN’s Interactive Sandbox. Which provides, among others, the option to extract malware configurations from memory dumps.
Configurations are crucial for understanding malware’s behavior and functions, tying it to a family and an adversary, and identifying all types of Indicators of Compromise (IOCs), which are then used for detection purposes. Such IOCs are particularly valuable as they contain hardcoded details such as command and control (C2) server addresses, encryption keys, and specific attack parameters.
Take a look at this sandbox session.
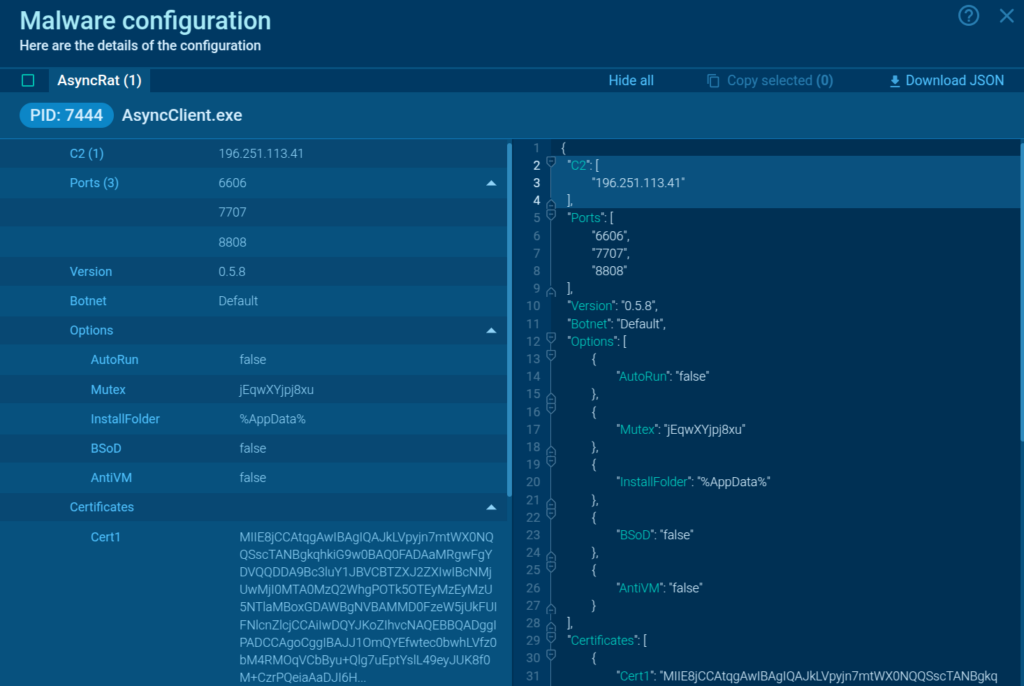
By opening the MalConf tab we can observe the extracted configuration of an AsyncRAT sample. One of the pieces of data found here is the malicious IP address used by the malware for communication with its C2 server.
ANY.RUN automatically extracts this crucial indicator and sends it to TI Feeds, which then get fed into the clients’ detection systems. This helps them identify the threat early and minimize its potential impact.
IOCs Detected with Suricata IDS Rules
Indicators detected with Suricata rules are valuable because they focus on identifying patterns in network traffic rather than specific details like IP addresses or domains. This means Suricata can recognize threats even when attackers change their infrastructure.
Thanks to ANY.RUN’s extensive integration of Suricata rules for traffic analysis, we can consistently extract fresh network indicators of numerous malware families and cyber threats.
Check out this report, which shows analysis of a FormBook sample.
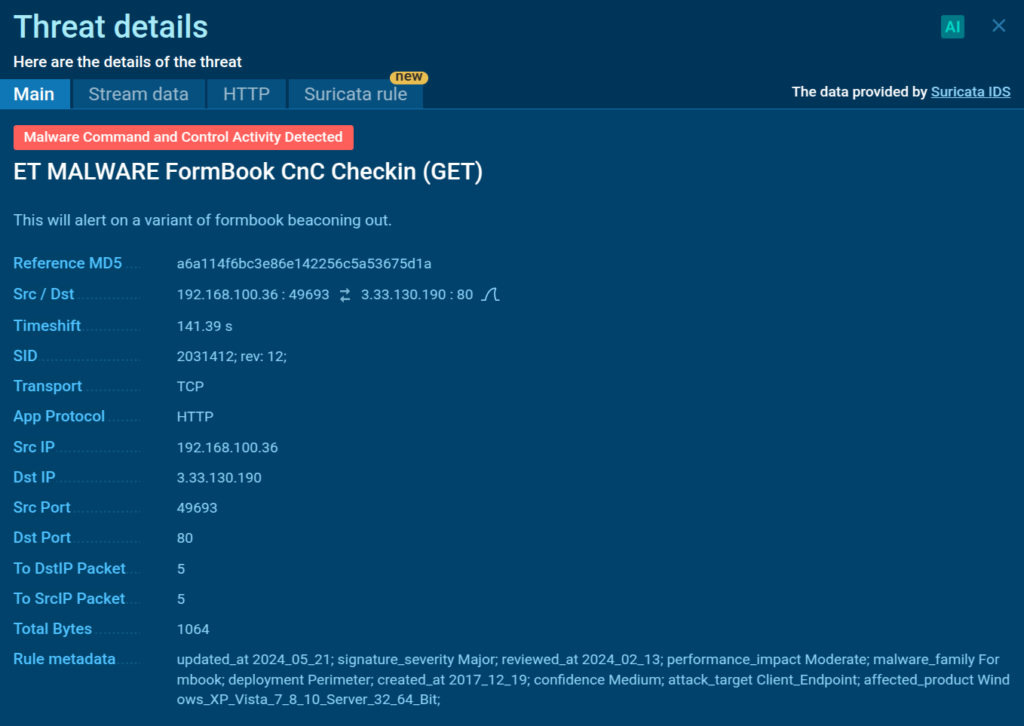
When we navigate to the Threats tab and then click on one of the triggered Suricata rules, we can see that the system has detected connection to domain controlled by the attackers.
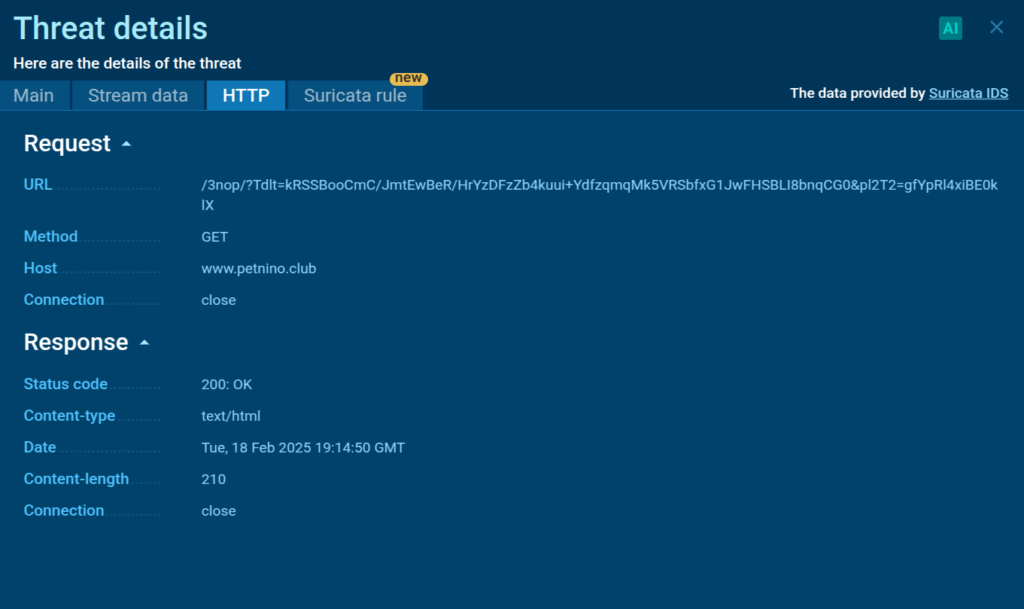
As you expect, this domain is sent directly to TI Feeds, strengthening our clients’ defense capabilities.
Integrate ANY.RUN’s TI Feeds
You can test ANY.RUN’s Threat Intelligence Feeds in STIX and MISP formats completely for free by getting a free demo sample here.
ANY.RUN also runs a dedicated MISP instance that you can syncronize your server with or connect to your security solutions. To get started, contact our team via this page.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Get a 14-day free trial of ANY.RUN’s Threat Intelligence service →
The post Enriching ANY.RUN’s TI Feeds with Unique IOCs: How It Works appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More