Learn to Analyze Real-World Cyber Threats with Security Training Lab
If you are a student, you might be several years away from getting a degree and a profession – and about a month away from becoming a malware analyst. The latter is made possible by ANY.RUN’s Security Training Lab.
There is no point in advertising a career in cybersecurity nowadays. Money talks louder: ransom sums, possible financial costs of operational disruption, and reputational losses hint that investing in cybersecurity teams is a wise solution for any business.
Security Training Lab can be a step towards a specter of career paths that imply cybersecurity literacy and understanding of malware analysis. It also can be a valuable addition to an academic course on threat detection, malware analysis or other cybersecurity subjects.
So, let’s take a closer look at the program.
What is Security Training Lab
It is an interactive digital course on malware analysis produced by ANY.RUN. It comprises 30 hours of academic content on cyber threats, including written materials, video lectures, tasks and tests.
Learn more about Security Training Lab
ANY.RUN is a cybersecurity company with 9 years of experience in providing malware analysis and threat intelligence services to individual security researchers, Managed Security Service Providers (MSSPs), and SOC departments of the largest companies around the world.
Security Training Lab stands out from other courses on malware analysis by focusing on teaching you practical skills with real-world examples of the latest cyber threats.
- Comprehensive Learning: 30 hours of academic content with written materials, video lectures, interactive tasks, and tests.
- Hands-On Experience: Full sandbox access with special plans for teachers and team licenses for students.
- Real-World Practice: Learn through real-world threat samples and labs.
- User-Friendly Platform: Easy-to-use and fast management system.
- Community Support: Private Discord community with tips, lifehacks, and news
What Security Training Lab is Not
Security Training Lab is not just a manual for ANY.RUN’s Interactive Sandbox. As part of the program, a student gets acquainted with a variety of professional tools and more importantly, with the key concepts and methods of cyber threat analysis and research.
Skills You’ll Learn to Analyze Real-World Threats
In the course of Security Training Lab, you’ll acquire several key analytical skills, including, but not limited to, the following.
Conducting Advanced Static Analysis
Static analysis examines a suspicious file without executing it. You will learn to understand the structure and the source code of executable files, the functions of Windows API, use file hashes to identify and track threats, and evaluate files’ entropy.
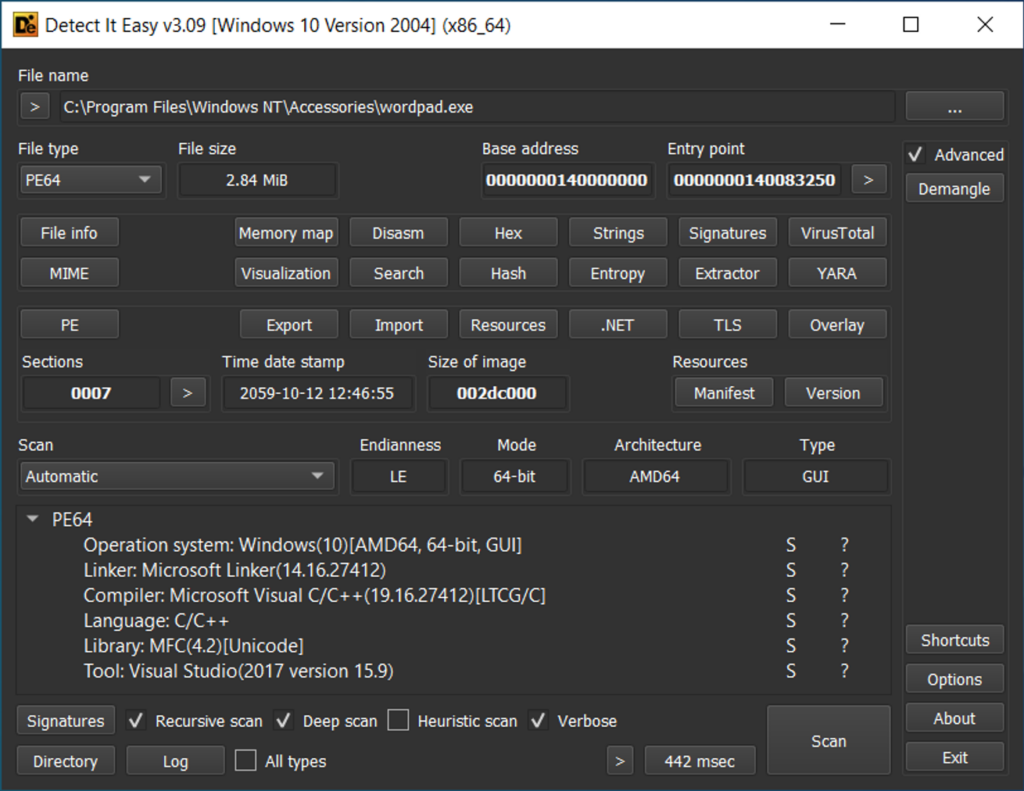
This data defines whether a file is malicious, what its real functions are, how it behaves, and how exactly it threatens the target.
Advanced static analysis implies disassembling malware’s code to see its structure, variables, loops, conditional operators, and other elements of the program, which helps to better understand the logic of its operation.
During the course, you will practice using a free tool for advanced static analysis and will become able to navigate through the code, set breakpoints for debugging, change values in memory and registers, gaining full control over the program being analyzed.
 Static Analysis Skills You’ll Learn
Static Analysis Skills You’ll Learn- Dissecting binaries to extract indicators of compromise (IOCs)
- Understanding and modifying assembly code for deeper analysis
- Using disassemblers and decompilers to reconstruct malware logic
Dealing with Encryption in Malware
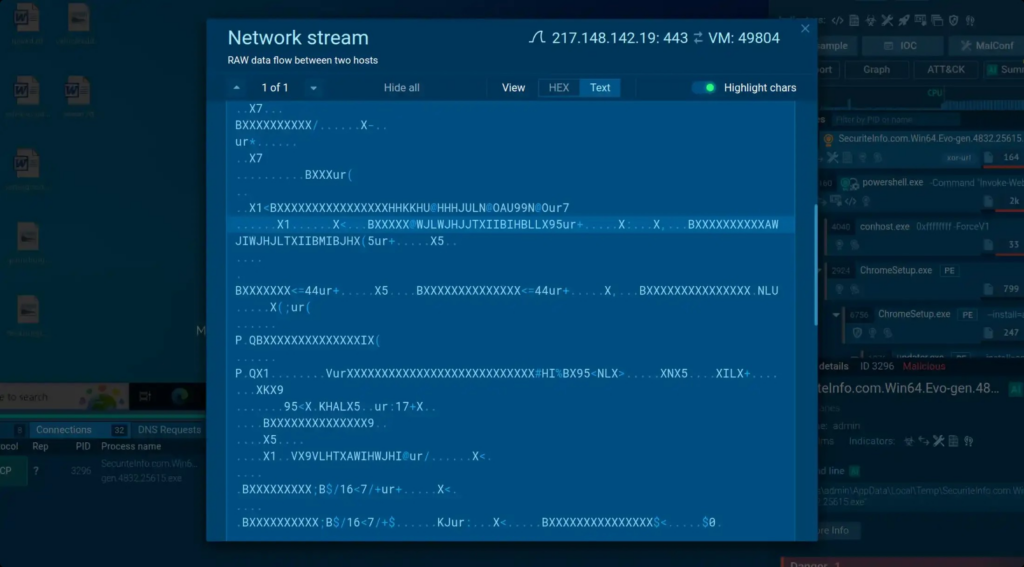
While encryption is a reliable shield to protect confidential data, it is also a tool in hackers’ hands that allows them to hide malicious activity and bypass protective mechanisms.
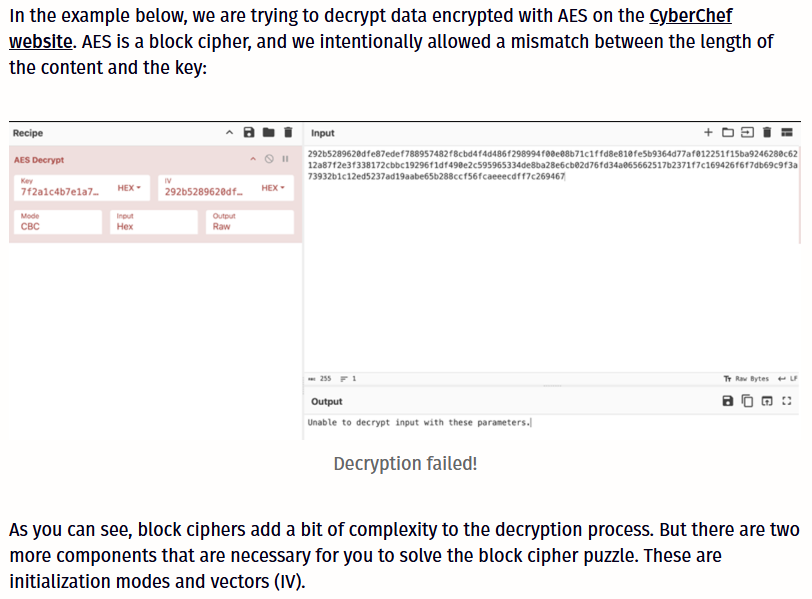
You’ll discover the principles of encryption, different approaches to its implementation, the most popular encryption algorithms from XOR to RSA and RC4 with their strengths and weaknesses, and the basics of decryption.
The acquaintance with encryption algorithms helps to detect the signs of software’s malicious nature: code obfuscation, encrypting network traffic for hiding activity or data for extortion. Knowing how data is decrypted allows one to bypass malware’s protection against analysis.
 Malware Decryption Skills You’ll Learn
Malware Decryption Skills You’ll Learn- Identifying and analyzing obfuscated and encrypted payloads
- Extracting encryption keys and decrypting malicious payloads
- Bypassing malware encryption techniques to reveal hidden threats
Identifying Malicious Behavior
Understanding and predicting malware behavior is the main task of malware analysis. The more we know about the stack of current malicious capabilities, the easier it is to deal with future threats.
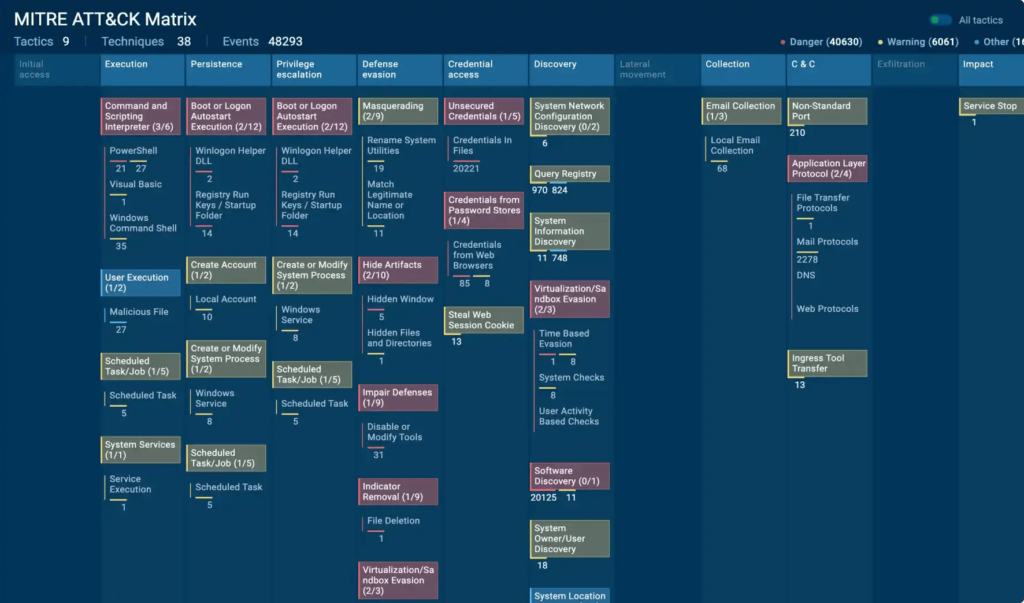
When executed, the malware generates files, establishes connections, and modifies processes. It also takes measures to avoid detection and analysis, maintain persistence, to hide its launch, and enhance its privileges.
These actions are traceable and can help to identify an ongoing attack, assist in the analysis process, or develop a cybersecurity strategy to protect against known malware strains.
You will explore MITRE ATT&CK — a constantly updated database of attacker tactics and techniques — and practice using it in malware behavior analysis.
 Malware Behavior Analysis Skills You’ll Learn
Malware Behavior Analysis Skills You’ll Learn- Mapping malware actions to MITRE ATT&CK techniques
- Detecting persistence mechanisms and evasion tactics
- Using sandbox environments to log and analyze malware activity
Performing In-depth Dynamic Analysis
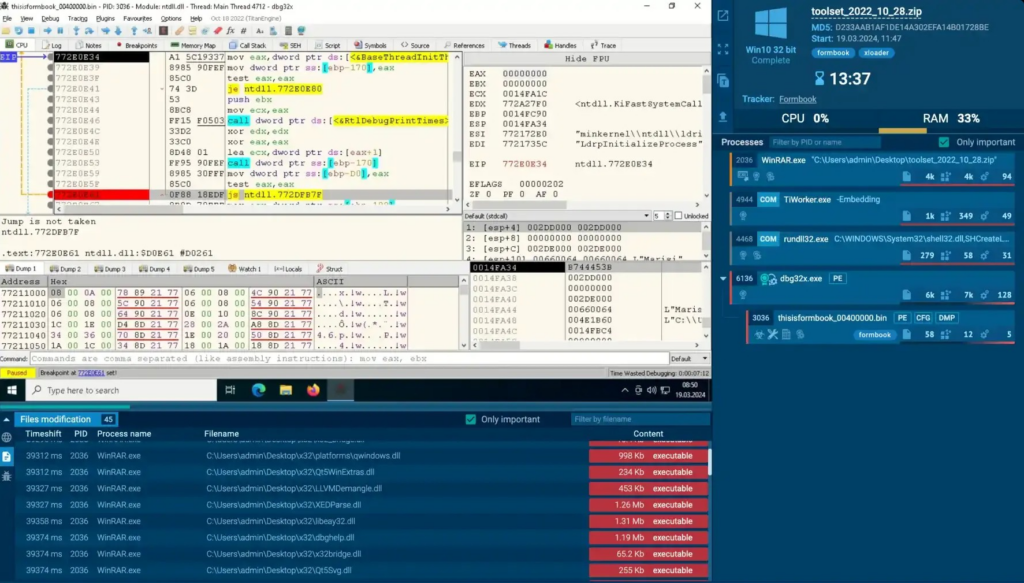
For dynamic analysis we need to watch malware in action, so we let it loose within a safe virtual machine environment. Basic dynamic analysis gives us a first glimpse of how the malware interacts with the system. Advanced dynamic analysis is like examining the behavior of a malware under a microscope: we get into the intricacies of the malicious code to understand its algorithms and find weaknesses.
Security Training Lab will equip you with powerful tools for advanced dynamic analysis (API Monitor and x64dbg) and guide you through debugging and anti-debugging techniques. You will learn to combine debugging with static analysis to maximize its efficiency.
 Dynamic Malware Analysis Skills You’ll Learn
Dynamic Malware Analysis Skills You’ll Learn- Utilizing debugging tools to trace malware execution
- Bypassing anti-analysis techniques used by advanced threats
- Extracting runtime indicators and identifying malicious system modifications
Analyzing Script- and Macro-Based Attacks
Malicious scripts require our close attention: they have become incredibly popular with attackers in recent years, mainly because they effectively bypass traditional endpoint defenses and are easy to obfuscate.
Macros are small programs written in scripting languages and embedded in other applications. They get direct access to the Windows API, making them incredibly powerful both for legitimate use and for hackers.
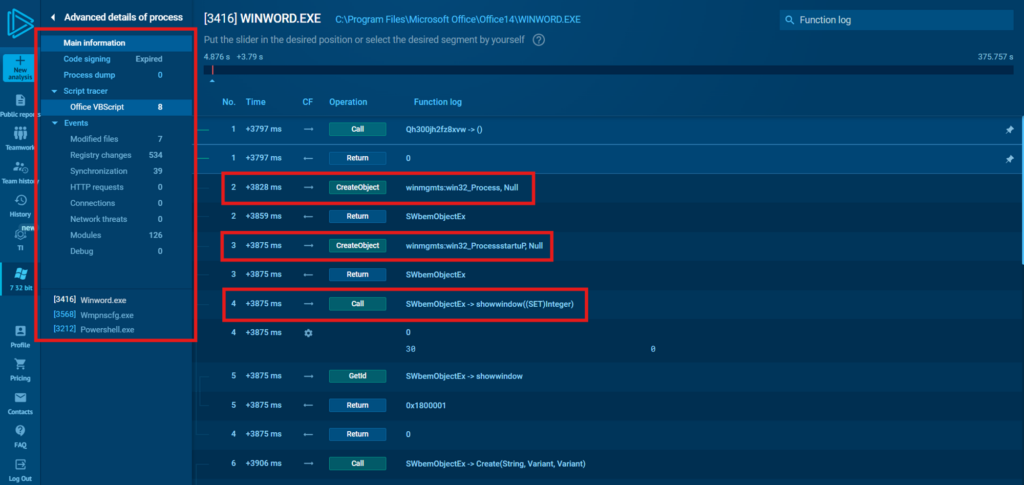
You will get to know the two main approaches to dissecting scripts — viewing the source code or dynamically executing it and observing it — and master ANY.RUN’s built-in tools for analyzing script-based malware and compiled malware that uses scripts.
Malicious macros are given special attention since they are used in a number of real-world attack scenarios, and their code usually is heavily obfuscated which complicates analysis. You will learn to use tools like ANY.RUN can help you identify their behavior without resorting to tedious deobfuscation.
 Scripts and Macros Analysis Skills You’ll Learn
Scripts and Macros Analysis Skills You’ll Learn- De-obfuscating malicious scripts to extract payloads
- Analyzing PowerShell and JavaScript-based malware
- Detecting macro-based threats in Office documents and emails
Get Access to Security Training Lab
Interested in trying Security Training Lab yourself or bringing it to your educational institution?
Send us a message and our team will get in touch to discuss your specific needs and provide a customized quote.
Conclusion
Security Training Lab provides a comprehensive and hands-on learning experience for mastering malware analysis. Completing this course will equip you with essential skills to detect, analyze, and mitigate real-world cyber threats.
With in-depth knowledge and practical exercises, you will gain the confidence to navigate the ever-evolving landscape of cybersecurity threats and contribute effectively to digital defense strategies.
For students looking to begin a career in cybersecurity, this course serves as a solid foundation. The skills you acquire will prepare you for roles such as malware analyst, security researcher, or SOC analyst, helping you take the first step toward a successful and impactful career in the field.
By mastering real-world threat analysis techniques, you will stand out in the job market and be ready to face the challenges of modern cybersecurity.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post Learn to Analyze Real-World Cyber Threats with Security Training Lab appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More
