How to Identify and Investigate Phishing Kit Attacks
Phishing kits have invested greatly in the popularity of phishing. They drop the entry threshold for cybercriminals enabling even low-skilled hackers to conduct successful attacks.
In general, a phishing kit is a set of tools for creating convincing fake webpages, sites, or emails that trick users into divulging sensitive information like passwords or credit card credentials. Security specialists should never underestimate this type of malware and fail to be ready to counter its users.
What Phishkits are made of
These ready-to-use packages can be basic, with some pre-written code and website and email templates, and they can be advanced phishing-as-a-service (PHaaS) kits that offer more sophisticated and customizable features. These may even contain automated updates or encryption features.
A typical kit includes:
- Website (email, social network pages) templates mimicking legitimate brands (banks, email providers, cloud services, etc.)
- Data harvesting scripts that capture input in webpage forms
- Automated deployment tools for quick setup
- Bypass techniques such as reverse proxies that intercept multi-factor authentication
- Server-side components that manage the data collected from victims
Some notable Phishkits
- 16Shop: targeted Apple, PayPal, and Amazon users and was distributed as a subscription service.
- Evilginx2: a framework to intercept authentication tokens that helped to bypass MFA.
- BulletProofLink: a PHaaS platform that offered pre-hosted phishing pages and even reused stolen credentials to maximize profit.
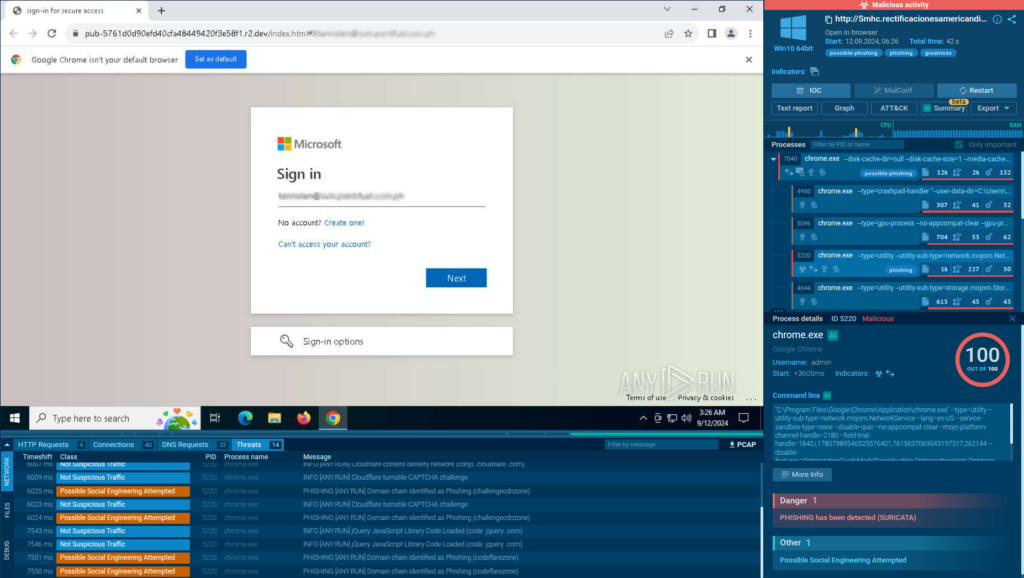
- Greatness: targets Microsoft 365 users and can dynamically generate fake login pages customized for the victim.
- GoPhish: an open-source framework meant for businesses to test their exposure to phishing by imitating attacks but also used maliciously.
- King Phisher: offers advanced features like campaign management and cloning of websites.
- Blitz: known for its simplicity and quick creation of phishing webpages.
Why Phishkits are a serious issue for businesses
Phishing kits are employed to attack both individuals and organizations, but they represent a specific threat to businesses by inviting wider audience of would-be hackers to the industry, multiplying risks and providing an increased workload to security systems.
Besides, phishing kit attacks make it easier to turn any employee into a soft spot of the cyber security perimeter. Even targeted at people, such attacks are a headache for SOC teams.
The features of phishkits that pose increased risks for organizations are:
Scalability: They allow attackers to automate and run phishing campaigns against thousands of employees simultaneously.
MFA Bypass: Modern phishkits integrate Adversary-in-the-Middle (AiTM) techniques to steal session cookies, bypassing multi-factor authentication.
Brand Abuse & Reputation Damage: Phishing pages tend to impersonate well-known brands, leading to loss of their customer trust when credentials are stolen.
Supply Chain Attacks: Phishkits can be used to target third-party vendors and gain access to corporate networks via compromised partners.
Defusing Phishkits with Threat Intelligence
Cyber threat intelligence has long proven useful in countering phishkit-based attacks. It involves gathering, analyzing, and acting upon information about current and emerging threats. For countering phishkits, it enforces:
- Early detection: TI helps to collect the indicators of compromise associated with the use of certain phishkits and set up network monitoring for detecting the elements of phishkit infrastructure.
- Behavioral Analys: TI is used to analyze patterns and behaviors of phishing campaigns, to identify new kits or variations of known ones before they cause harm.
- Proactive Blocking: Intelligence feeds are used to update security systems like firewalls, email gateways, or intrusion detection systems to block known malicious domains or IPs.
- Employee Training: By helping to understand phishkits’ anatomy and behavour, TI can facilitate realistic phishing simulations based on actual threats, training staff to recognize and report phishing attempts.
- Vulnerability Management: Seeing what types of phishkits are targeting specific sectors or technologies, organizations prioritize patching vulnerabilities or enhance security measures where they are most needed.
How to Track and Identify Phishing Kit Attacks with TI Lookup
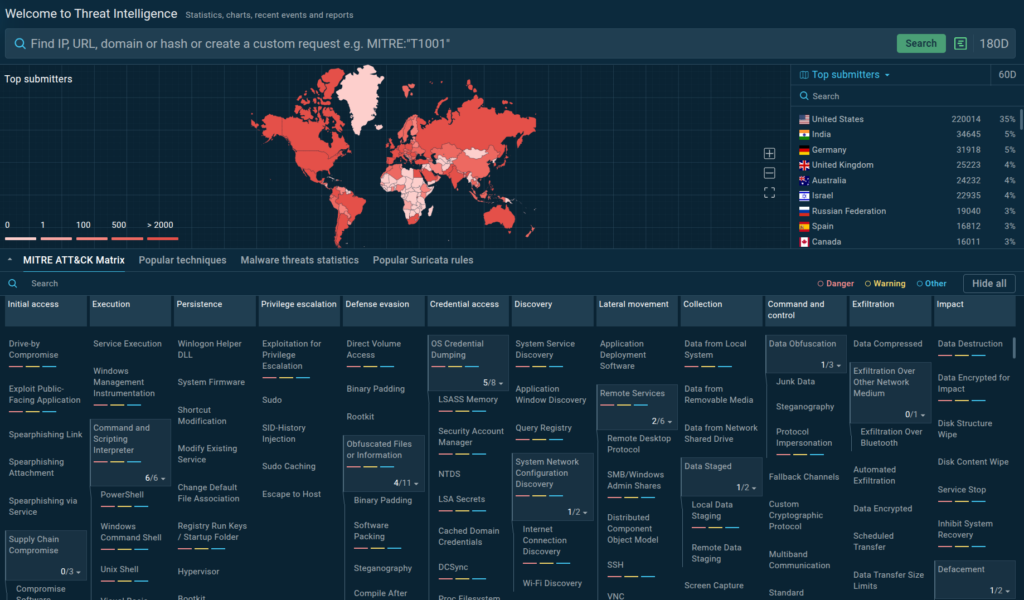
Threat Intelligence Lookup from ANY.RUN provides access to an extensive database of the latest threat data extracted from millions of public sandbox sessions.
It allows analysts to conduct targeted indicator searches with over 40 different parameters, from IPs and hashes to mutexes and registry keys, to enrich their existing intel on malware and phishing attacks.
With TI Lookup, users can collect as well as pin their existing indicators to specific cyber threats. Each indicator in TI Lookup can be observed as part of wider context
Threat Intelligence Lookup empowers organizations with:
- Streamlined Access to Threat Information: Simplifies and speeds up the process of finding threat-related information, making it more convenient and efficient.
- Detailed Insights into Attacks: Provides detailed information on attacker methods, helping to determine the most effective response measures. Deep analysis makes the actions of analysts more precise and effective.
- Reduced Mean Time to Respond (MTTR): Offers quick access to key threat information, enabling analysts to make swift decisions.
- Increased Detection and Response Speed: Ensures data is up-to-date, helping businesses improve the speed of detecting and responding to new threats.
1. Collecting Intel on Tycoon2FA Phishkit Abusing Cloudflare Workers
Tycoon2FA is a phishkit that has been offered as a service to cyber criminals since 2023. This threat’s specialty is adversary-in-the-middle attacks that make it possible to not only steal victims’ login credentials but also bypass two-factor authentication (2FA).
Tycon2FA operators make extensive use of Cloudflare Workers and Cloudflare Pages for hosting fake login forms that are abused for stealing personal data.
With TI Lookup, we can collect the latest example of domains utilized for Tycoon2FA attacks using the following query:
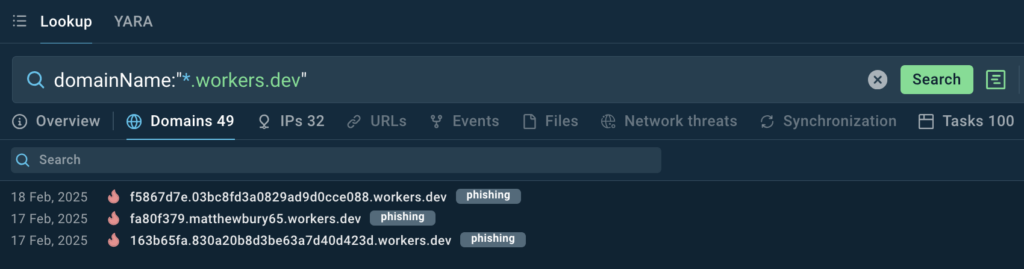
TI Lookup provides 49 domains, with some of them being labeled with the “phishing” tag. At this point, users can collect these indicators to enrich their defense.
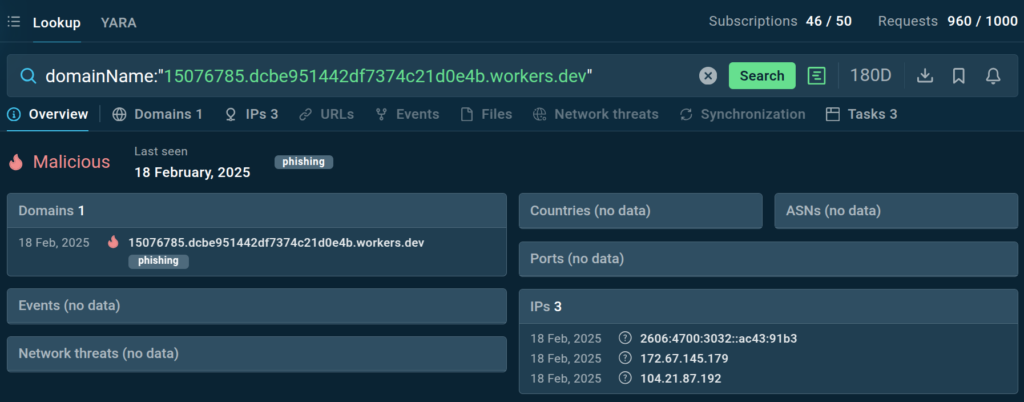
Using TI Lookup can be also helpful during triage, when you need to check if a certain Cloudflare Workers domain is malicious. As you can see in the image above, the service instantly informs you about the threat level of the queried domain.
The Tasks tab in TI Lookup provides a list of the latest analysis reports performed in ANY.RUN’s Interactive Sandbox featuring the requested domains.
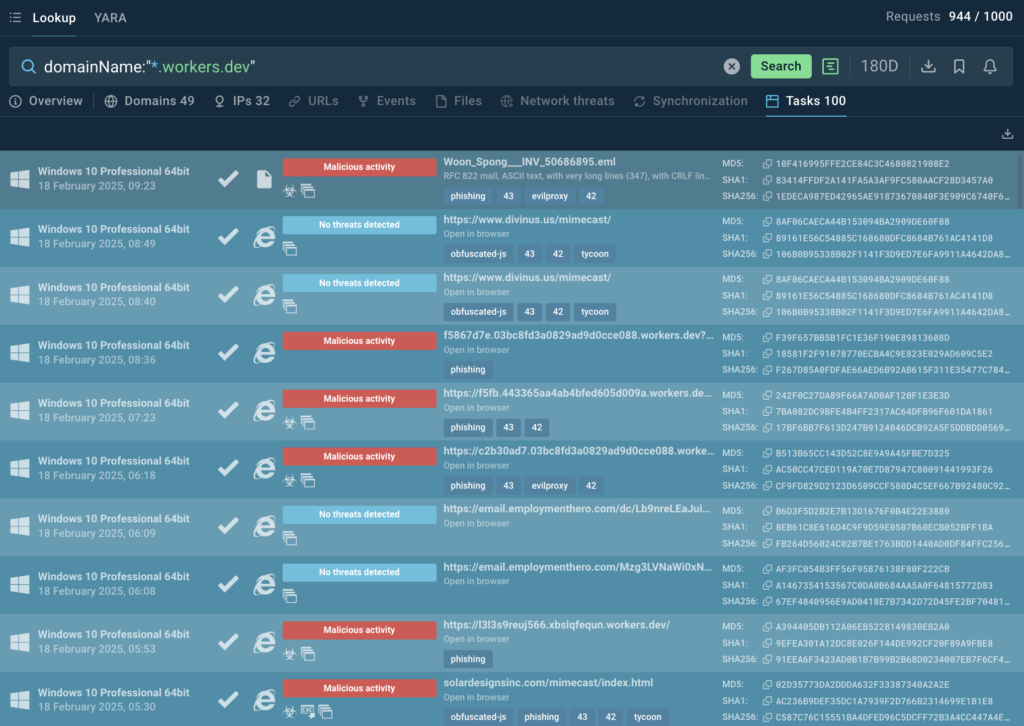
Here, we can discover that Cloudflare’s domain is also used by another phishing-as-a-service tool, EvilProxy.
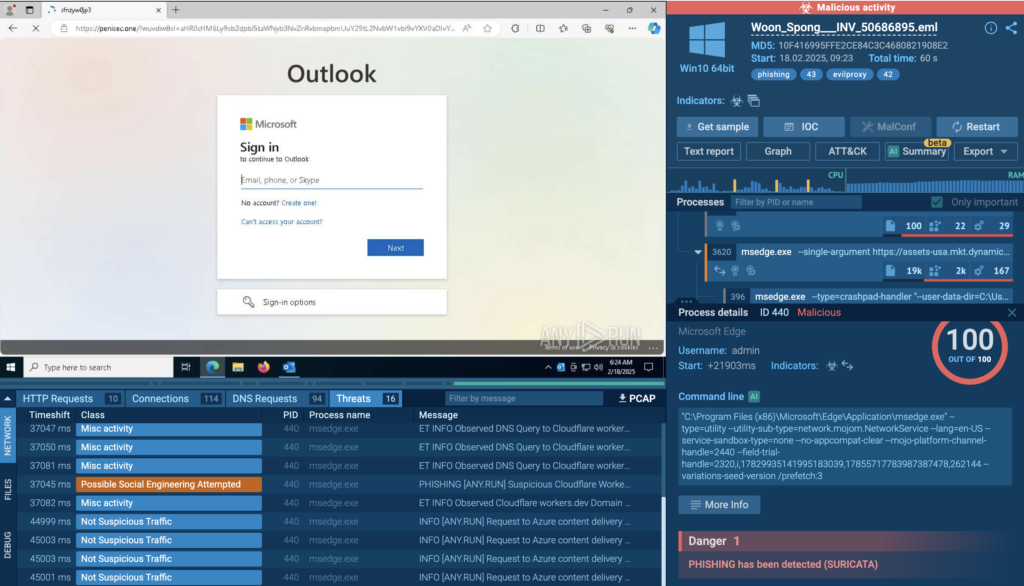
If you want to dig deeper, you can open any of these reports inside the sandbox and observe real-world attacks as they unfolded and rerun analysis of these URLs yourself.
2. Researching Phishkit Campaigns via Suricata rules
Threat Intelligence Lookup supports search by Suricata IDS rules. Add a rule ID (SID) and see an assortment of incidents where the same rule was triggered.
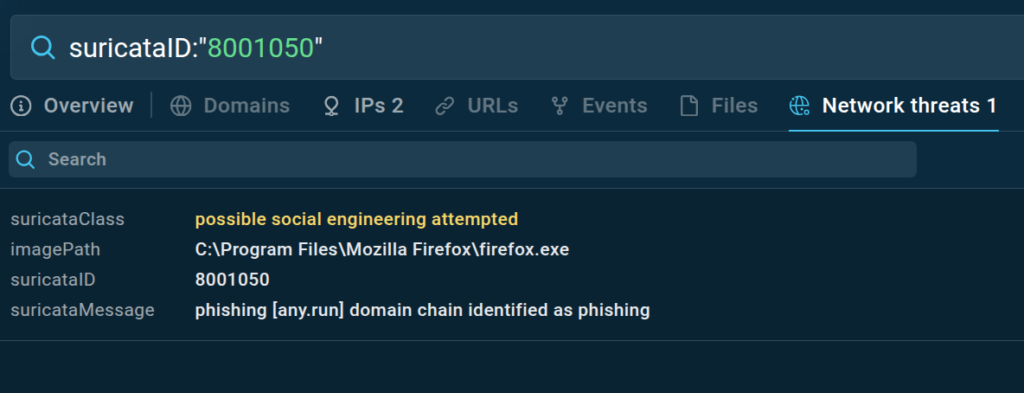
Let’s use the rule with the class “Possible social engineering attempted” via the following query:
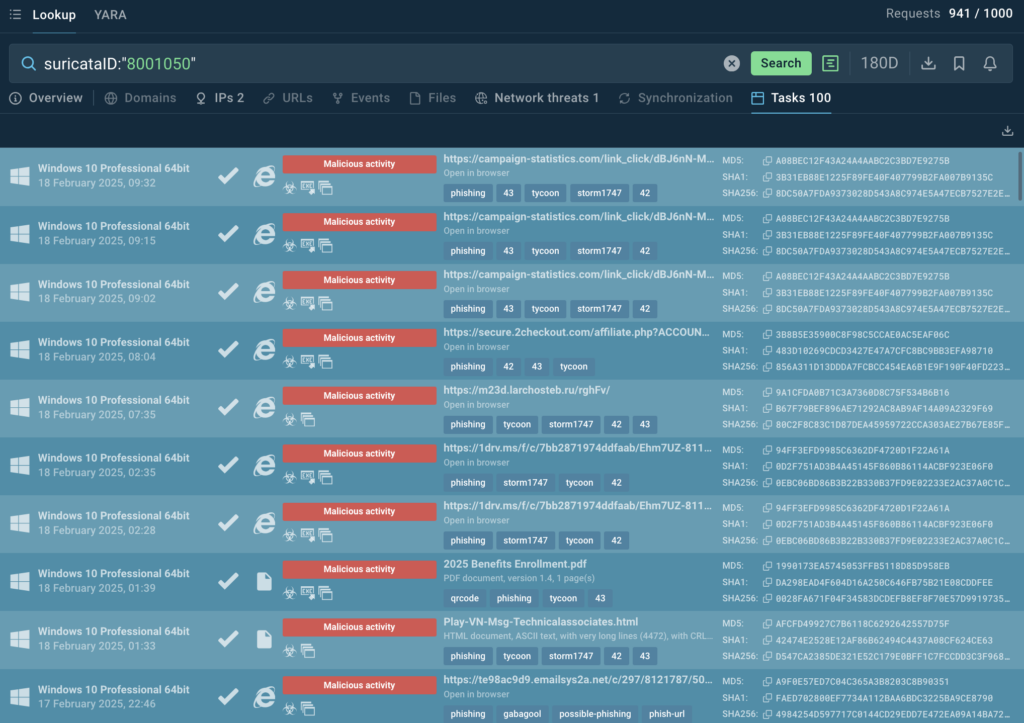
Among the results, we can see examples of Gabagool and Sneaky2FA phishing kit attacks, as well as Tycoon2FA’s which are linked to the Storm1747 APT.
Learn more on how to track APTs
You can download data on all of these samples, which includes hashes, and use it to further enrich your security systems. As always, you can also explore each report in detail to collect even more insights into these attacks.
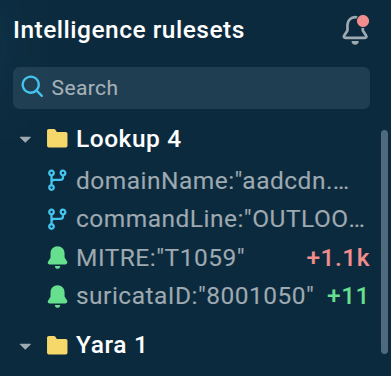
TI Lookup also lets you automatically receive notifications about the new results available for specific search queries. All you need to do is click the bell icon, and all of the updates will be displayed in the left side menu.
3. Tracking new samples of Mamba2FA Phishkit
If your organization has been previously attacked with a certain phishing kit, then you can easily stay updated on the newest indicators related to it.
Let’s take Mamba2FA as an example. It is a widely utilized phishkit that has been used in numerous attacks against businesses in the financial and manufacturing sectors.
With a simple query that combines the name of the phishkit with an empty domain name field, we can quickly discover both new attacks, as well as network indicators like domains and URLs recorded during sandbox analysis:
threatName:”mamba” AND domainName:””
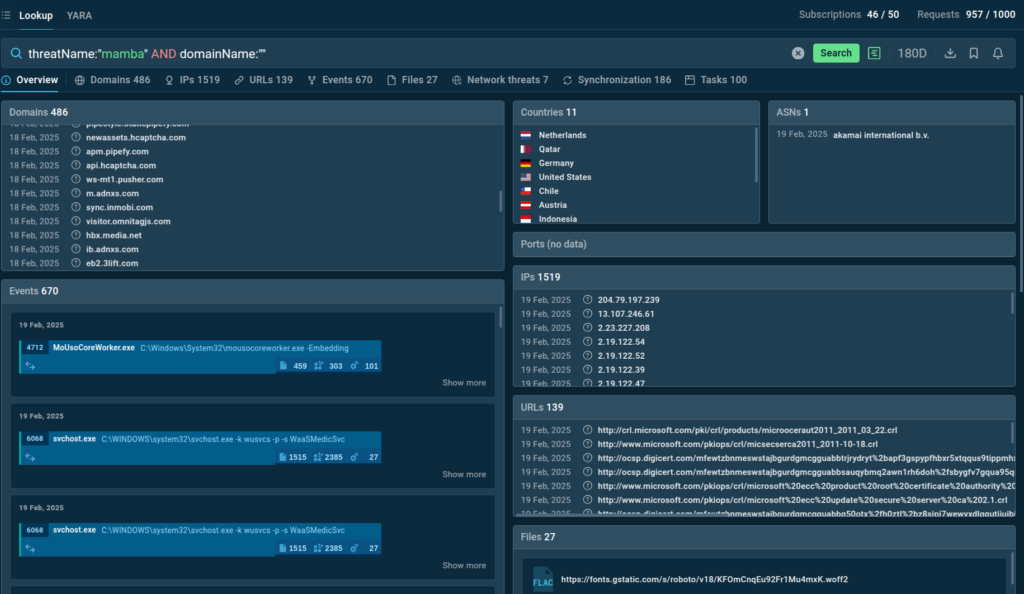
Learn more about proactively identifying Mamba2FA attacks in the article by a phishing analyst.

Conclusion
Security experts are far from underestimating the risks behind phishing kits. They don’t just open gates to a mass of low-skilled beginners to the cybercrime market. They abuse known brands and trademarks by impersonating their resources, employ sophisticated infiltration and anti-evasion techniques, and are constantly evolving.
To avoid financial and reputational loss, organizations should consider investing in high-end threat intelligence solutions as well as emphasize employee educating and training.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post How to Identify and Investigate Phishing Kit Attacks appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


