Malware Trends Overview Report: 2024
2024 has been an eventful year in the world of cybersecurity, with new trends emerging and malware families evolving at an alarming rate. Our analysis highlights the most prevalent malware families, types, and TTPs of the year, giving you a snapshot of the changing threat landscape.

This report is based on the analysis of 4,001,036 public sessions conducted by ANY.RUN’s community inside the Interactive Sandbox over the last 12 months, which is 1 million more than the 2,991,551 sessions in 2023. Of these, 790,549 were tagged as malicious and 211,517 as suspicious, reflecting a rise in suspicious activity compared to the 148,124 suspicious sessions identified in 2023.
ANY.RUN identified an astonishing 1,872,273,168 IOCs in 2024—nearly three times more than the 640,158,713 IOCs uncovered in 2023. This sharp growth highlights not only the expanding use of the platform but also the improved threat coverage and detection capabilities of ANY.RUN.
Top Malware Types in 2024
In 2024, Stealers dominated with 51,291 detections, marking a significant rise compared to 2023, when they were in second place with just 18,290 detections. This highlights their growing popularity among attackers for data theft.
Loaders moved to second place in 2024 with 28,754 detections, a slight increase from their leading position in 2023, where they accounted for 24,136 detections. Despite the shift, Loaders remain a critical component in delivering malware payloads.
RATs (Remote Access Trojans) maintained their third position but saw an increase from 17,431 detections in 2023 to 24,430 detections in 2024, reflecting their continued importance in providing attackers remote control over compromised systems.
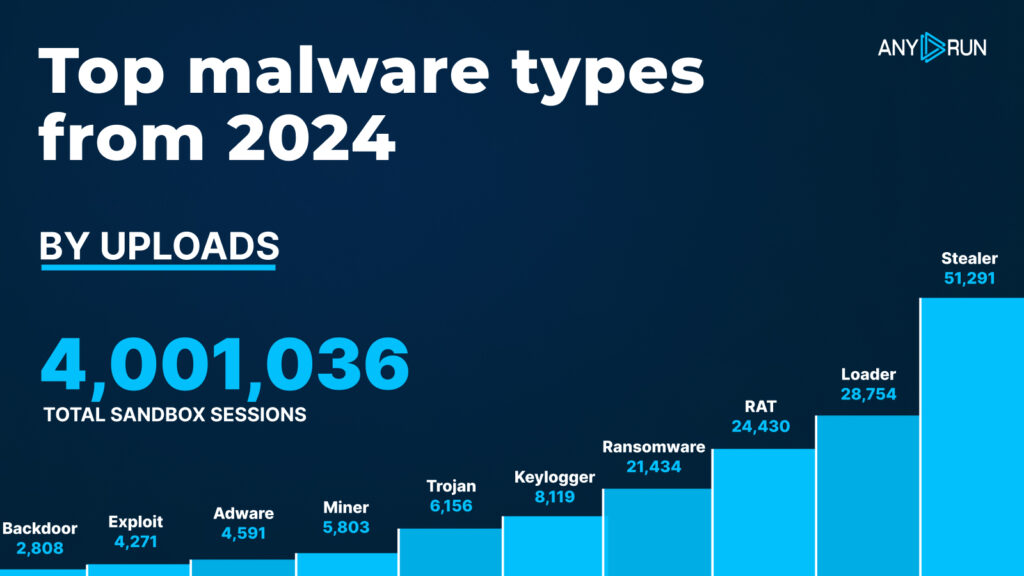
| # | Type | Detections |
|---|---|---|
| 1 | Stealer | 51,291 |
| 2 | Loader | 28,754 |
| 3 | RAT | 24,430 |
| 4 | Ransomware | 21,434 |
| 5 | Keylogger | 8,119 |
| 6 | Trojan | 6,156 |
| 7 | Miner | 5,803 |
| 8 | Adware | 4,591 |
| 9 | Exploit | 4,271 |
| 10 | Backdoor | 2,808 |
To collect fresh threat intelligence on emerging cyber threats, make sure to use TI Lookup, a service that lets you search ANY.RUN’s vast database of the latest threat data.
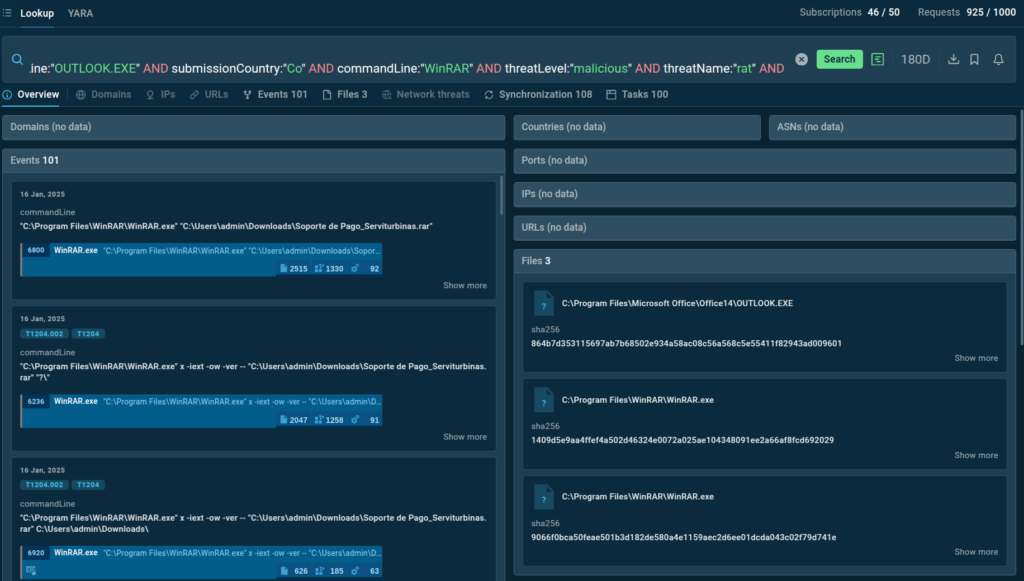
It features over 40 search parameters, including IPs, mutexes, and even YARA rules, allowing you to pin the tiniest artifacts to specific malware and phishing attacks and enrich your TI with additional context and actionable indicators.
Learn more about Threat Intelligence Lookup →

Top Malware Families in 2024
In 2024, Lumma Stealer jumped straight to the top with 12,655 detections, taking over the ranking from nowhere as it wasn’t seen in the 2023 report. Its rapid rise shows how quickly cybercriminals have adopted it.
Agent Tesla moved up to second place in 2024 with 8,443 detections, compared to 4,215 detections in 2023 when it was in third place. Its continued presence shows it remains a go-to choice for attackers.
AsyncRAT claimed third place in 2024 with 8,257 detections, while in 2023, Redline was the most popular malware family with 9,205 detections, and Remcos followed with 4,407 detections.

| # | Name | Detections |
|---|---|---|
| 1 | Lumma | 12,655 |
| 2 | Agent Tesla | 8,443 |
| 3 | AsyncRAT | 8,257 |
| 4 | Remcos | 8,004 |
| 5 | Stealc | 7,653 |
| 6 | Xworm | 7,237 |
| 7 | Redline | 7,189 |
| 8 | Amadey | 5,902 |
| 9 | Snake | 4,304 |
| 10 | njRAT | 3,522 |
With TI Lookup, you can track all of these and other malware families and stay updated on their evolving infrastructure. Here is an example of a request to TI Lookup to find Lumma domains:
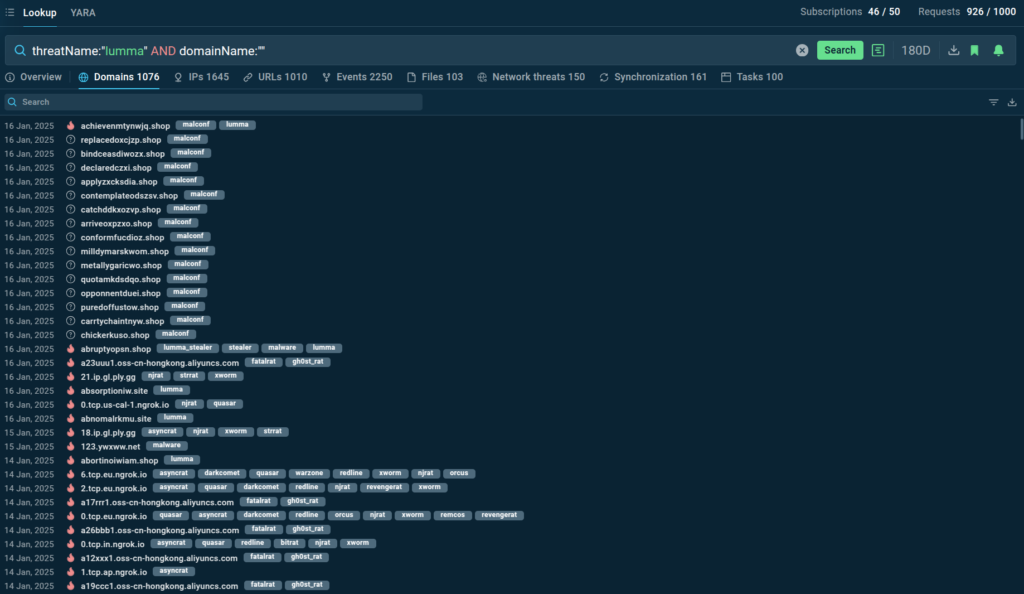
The service provides a list of relevant domain names used by the malware. Many of them are marked with the malconf tag, indicating that these domains were extracted from Lumma samples’ configurations.
Top MITRE ATT&CK Techniques in 2024
The MITRE ATT&CK framework is a globally recognized resource that breaks down how attackers operate, mapping their tactics and techniques into clear categories. It’s an invaluable tool for cybersecurity professionals to understand and respond to threats effectively.
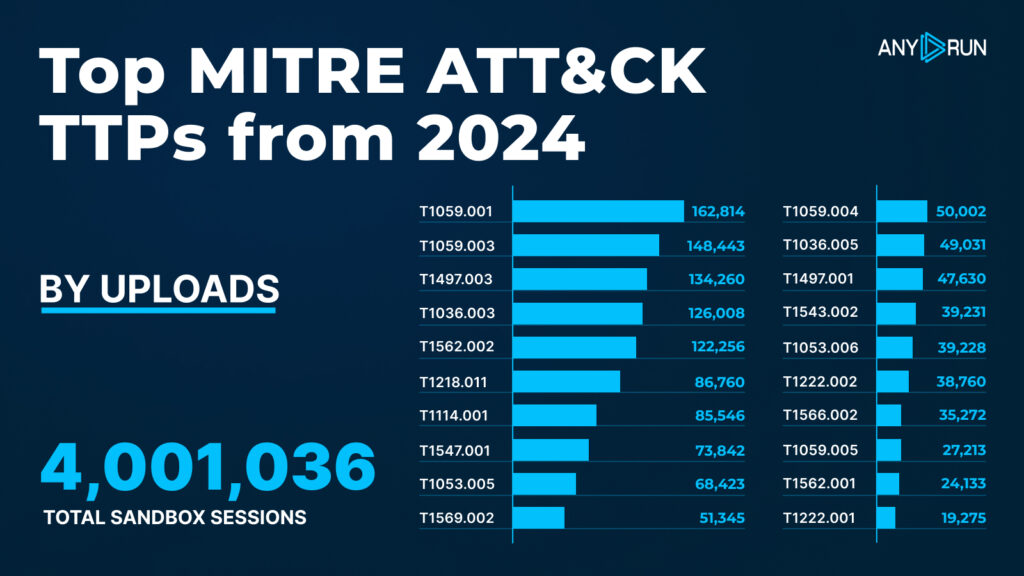
In 2024, ANY.RUN recorded over 1.4 million matches to ATT&CK techniques, a noticeable increase from 1.2 million matches in 2023.
The rankings saw some significant changes: Masquerading (T1036.005), the top technique in 2023 with 486,058 matches, was overtaken in 2024 by PowerShell (T1059.001) and CMD (T1059.003), which led the list with 162,814 and 148,443 matches, respectively.
In 2024, new techniques appeared that were absent in 2023, including Python scripting (T1059.004) with 50,002 matches, System Checks for Sandbox Evasion (T1497.001) with 47,630 matches, and Linux Permissions Modification (T1222.002) with 38,760 matches.
| Rank | Technique ID | Technique Name | Detections |
|---|---|---|---|
| 1 | T1059.001 | Command and Scripting Interpreter: PowerShell | 162,814 |
| 2 | T1059.003 | Command and Scripting Interpreter: Windows CMD | 148,443 |
| 3 | T1497.003 | Virtualization/Sandbox Evasion: Time-Based | 134,260 |
| 4 | T1036.003 | Masquerading: Rename System Utilities | 126,008 |
| 5 | T1562.002 | Impair Defenses: Disable Antivirus Tools | 122,256 |
| 6 | T1218.011 | System Binary Proxy Execution: Rundll32 | 86,760 |
| 7 | T1114.001 | Email Collection: Local Email Collection | 85,546 |
| 8 | T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys | 73,842 |
| 9 | T1053.005 | Scheduled Task/Job: Scheduled Task | 68,423 |
| 10 | T1569.002 | System Services: Service Execution | 51,345 |
| 11 | T1059.004 | Command and Scripting Interpreter: Python | 50,002 |
| 12 | T1036.005 | Masquerading: Match Legitimate Name or Location | 49,031 |
| 13 | T1497.001 | Virtualization/Sandbox Evasion: System Checks | 47,630 |
| 14 | T1543.002 | Create or Modify System Process: Windows Service | 39,231 |
| 15 | T1053.006 | Scheduled Task/Job: Cron | 39,228 |
| 16 | T1222.002 | File and Directory Permissions Modification: Linux | 38,760 |
| 17 | T1566.002 | Phishing: Spearphishing Link | 35,272 |
| 18 | T1059.005 | Command and Scripting Interpreter: Visual Basic | 27,213 |
| 19 | T1562.001 | Impair Defenses: Disable or Modify Tools | 24,133 |
| 20 | T1222.001 | File and Directory Permissions Modification: Windows | 19,275 |
Top TTPs highlights:
- Scripting Dominance (T1059.001 & T1059.003):
PowerShell and Windows CMD remain the top tools for attackers, with over 310,000 detections combined. Their flexibility and integration with systems make them ideal for executing malicious commands. Monitoring script activity and implementing strict execution policies are critical defenses.
- Evasion Tactics on the Rise (T1497.003 & T1036.003):
Sandbox evasion through time-based delays (134,260 detections) and masquerading via renamed system utilities (126,008 detections) highlight attackers’ focus on stealth. Behavioral analysis and anomaly detection can help counter these techniques.
- Targeting Defenses (T1562.002):
Disabling antivirus tools was detected 122,256 times in 2024, showcasing its effectiveness for attackers. Organizations must invest in layered defenses that can identify and respond to tampering attempts in real-time.
- Exploiting System Services (T1569.002 & T1218.011):
Adversaries frequently used system services like Rundll32 (86,760 detections) and service execution (51,345 detections) to execute malicious code while blending into normal operations.
- Phishing and Email Collection (T1114.001 & T1566.002):
Techniques like local email collection (85,546 detections) and spearphishing links (35,272 detections) remained effective, especially in targeted attacks. Robust email filtering and user training remain vital for reducing these risks.
Report Methodology
This report is built on insights from 4,001,036 tasks submitted to our public threat database in 2024. Each task represents the hard work and curiosity of our community of researchers, who used ANY.RUN to uncover threats and analyze malware.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Get a 14-day free trial of ANY.RUN’s products →
The post Malware Trends Overview Report: 2024 appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

