YARA Rules: Cyber Threat Detection Tool for Modern Cybersecurity
Every ticking second is a chance for cyber threats to creep in.
For businesses, the stakes couldn’t be higher. One malicious email opened by an employee, and the malware can spread across office computers faster than mushrooms after rain. The consequences? Lost data, financial damage, and a hit to your company’s reputation.
To stop these threats before they cause harm, businesses need to stay prepared.
This is where YARA rules come in. They help cybersecurity teams to detect potential threats, simplify the process, and deliver clear, actionable insights to fight back against potential dangers.
In this article, we’ll dive into the crucial role of YARA rules, how they work, and how their integration into ANY.RUN’s sandbox helps teams to detect and handle cyber threats with confidence and efficiency.
What Are YARA Rules?
Just as a lighthouse guides sailors safely past hidden rocks and treacherous waters, YARA rules guide cybersecurity professionals by identifying malicious patterns and offering a clear signal amidst the noise of potential threats.
YARA, funnily enough, stands for Yet Another Ridiculous Acronym. However, its actions are far more serious than its name suggests. YARA rules play a critical role in cybersecurity, helping professionals identify and classify malware by matching patterns in files, processes, or even memory.
At its core, YARA is a rule-based system that scans for specific characteristics, like unique strings or byte sequences, that are commonly found in malicious software. Think of it as a highly specialized filter that can sift through data to pinpoint potential threats with precision and speed.
How YARA Helps Organizations Detect Cyber Threats
YARA simplifies threat detection by identifying malicious patterns in files, processes, and memory with precision. It automates the scanning process, reducing the need for manual analysis and speeding up response times.
The beauty of YARA lies in its adaptability. Organizations can customize rules to target specific threats or emerging malware families, ensuring their defenses evolve alongside the threat landscape.
Combined with the real-time capabilities of ANY.RUN’s sandbox, this framework not only detects threats but also helps businesses understand their behavior, enabling them to mitigate risks before serious damage occurs.
Main benefits of YARA rules in organizations:
- Quickly identify threats, reducing the time spent on manual analysis.
- Tailored to detect specific malware families or new attack patterns.
- Minimize false positives and improve detection accuracy.
- Streamline the scanning process, saving resources and improving efficiency.
- Reduce the financial impact of cybersecurity breaches by catching threats early.

How does YARA work?
YARA operates as a powerful pattern-matching tool that scans files, processes, or memory dumps for specific characteristics. At its core, it relies on rules, predefined sets of instructions that describe what YARA should look for and under what conditions it should flag something as suspicious.
Here’s how the main process works:
- Creating rules: The first step in using YARA is to create a rule. A rule defines the patterns or conditions YARA will look for in the data.
- Scanning the target: Once the rules are defined, YARA scans the target data, this could be a file, a process, or even a memory dump. During the scan, YARA compares the data against the strings and conditions outlined in the rules.
- Matching patterns: If YARA identifies patterns in the data that match those defined in the rule, it triggers a match. For example, if a rule is designed to detect ransomware, it might flag a file containing encryption-related commands or unique file headers used by ransomware families.
- Flagging threats: When a match occurs, YARA provides a detailed report of the findings. This includes information about the matched rule, the specific patterns detected, and where they were found in the data.
- Providing insights: The output from YARA gives cybersecurity teams actionable insights. These insights help analysts decide whether the flagged file or process is malicious and what steps to take next.
YARA Elements You Should Know
YARA rules are made up of several essential components, each playing a critical role in detecting and classifying malware. To better understand how YARA works, let’s break down its key elements and examine an example.
Meta section
The meta section provides descriptive information about the rule. This includes details like the author, creation date, a brief description of the rule’s purpose, and additional contextual data. While it doesn’t affect the execution of the rule, it helps organize and document it for future use.
Strings section
This section contains the patterns the rule will search for in files or processes. These patterns can include:
- Text strings: Words or phrases often found in malicious code.
- Hexadecimal sequences: Byte-level patterns unique to malware.
- Regular expressions: For advanced matching of dynamic content.
Condition section
The condition section defines the logic that determines when the rule will trigger. It specifies the criteria for matching patterns, such as requiring a minimum number of matches from the strings section or looking for specific file characteristics.
Real-World Example of YARA Rule
Below is an example of a YARA rule created to detect the Sakula malware family. It shows how each element works together to flag potential threats:
rule Sakula {
meta:
author = "ANY.RUN"
date = "2024-12-11"
description = "Detects Sakula samples"
family = "Sakula"
sample1= "https://app.susp.io/tasks/3c4f4b5e-7254-4fb4-a31e-4617b03110b1"
sample2= "https://app.susp.io/tasks/5722f2e3-64fc-49a4-beac-600c992ab765"
hash1 = "5de4e79682120f5b115eea30ce2da200df380f6256f03e38d3692a785f06fd64"
hash2 = "a9430482e5695c679f391429c7f7a6d773985f388057e856d50a54d1b19f463b"
strings:
$s1 = "%d_of_%d_for_%s_on_%s"
$s2 = "/c ping 127.0.0.1 & del "%s""
$s3 = "/c ping 127.0.0.1 & del /q "%s""
$s4 = "cmd.exe /c rundll32 "%s""
$s5 = "I'm a virus. My name is sola" ascii
$s6 = "Local\SM0:%d:%d:%hs" wide
$s7 = "Vxzruua/5.0" ascii
$s8 = "MicroPlayerUpdate.exe" ascii
$s9 = "CCPUpdate" ascii
$s10 = "Self Process Id:%d" ascii
$op1 = { 81 3E 78 03 00 00 75 57 8D 54 24 14 52 68 0C 05 41 00 68 01 00 00 80 FF 15 00 F0 40 00 85 C0 74 10 8B 44 24 14 68 2C 31 41 00 50 FF 15 10 F0 40 00 8B 4C 24 14 51 FF 15 24 F0 40 00 E8 0F 09 00 }
$op2 = { 50 E8 CD FC FF FF 83 C4 04 68 E8 03 00 00 FF D7 56 E8 54 12 00 00 E9 AE FE FF FF E8 13 F5 FF FF }
condition:
uint16(0) == 0x5a4d and
(4 of ($s*) or
any of ($op*))}Let’s highlight some of the key elements in this rule:
Meta
- author = “ANY.RUN”: Indicates the creator of the rule.
- date = “2024-12-11”: Specifies when the rule was written, useful for tracking its relevance.
- description = “Detects Sakula samples”: Explains the rule’s purpose—targeting Sakula malware.
- family = “Sakula”: Categorizes the malware family the rule focuses on.
- sample1, sample2: Links to Sakula malware samples used for testing and refining the rule.
- hash1, hash2: Cryptographic hashes uniquely identifying the malware samples analyzed.
Strings
- $s6 = “Local\SM0:%d:%d:%hs” wide
This is a wide string (Unicode) that includes placeholders for integers (%d) and a short string (%hs). - $op1 = { 81 3E 78 03 00 00 75 57 8D 54 24 14 52 68 0C 05 41 00 68 01 00 00 80 FF 15 00 F0 40 00 85 C0 74 10 8B 44 24 14 68 2C 31 41 00 50 FF 15 10 F0 40 00 8B 4C 24 14 51 FF 15 24 F0 40 00 E8 0F 09 00 }
This is a hexadecimal byte sequence that represents a specific operation or function in the malware.
Condition
- uint16(0) == 0x5a4d:
This condition checks if the first two bytes of the file are 0x5a4d, which is the signature for a Windows PE (Portable Executable) file. - (4 of ($s) or any of ($op))**:
This condition checks if at least 4 of the strings ($s1 to $s9) are found in the file, or if any of the hexadecimal byte sequences ($op1 or $op2) are found in the file.
See YARA in Action
To better understand how this YARA rule detects Sakula malware, you can observe its behavior in real time using ANY.RUN’s Interactive Sandbox.
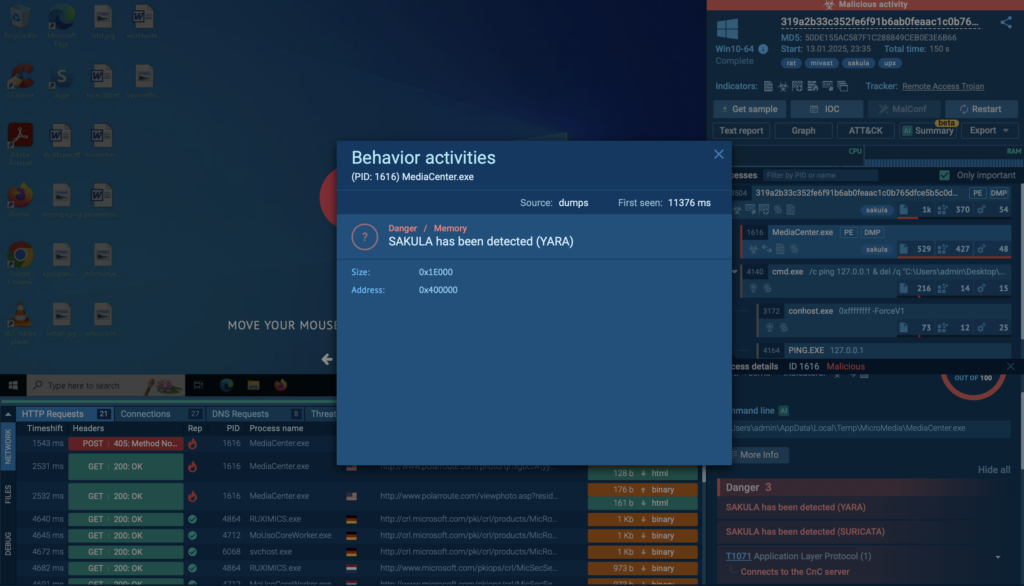
This analysis session showcases the malware’s activity and how the rule effectively identifies its patterns.
ANY.RUN’s interactive sandbox is a dynamic environment where cybersecurity teams can analyze files and observe their behavior in real time. Unlike traditional sandboxes, ANY.RUN lets users interact with the malware, providing deeper insights and faster results.
YARA is an inseparable part of this process. By integrating YARA rules into the sandbox, ANY.RUN identifies malicious patterns in files and processes with precision and speed.
ANY.RUN experts are constantly adding new YARA rules to the core of our malware sandbox, making the analysis process faster and saving security teams loads of time.
You can easily upload any suspicious file or link into the sandbox, and during the analysis, YARA rules will kick in. If there’s malware hiding in your file or link, the sandbox will spot it for you.
For example, after analyzing the following sample in the ANY.RUN sandbox, the process fgfkjsh.exe was flagged as malicious with the “MassLogger” tag.
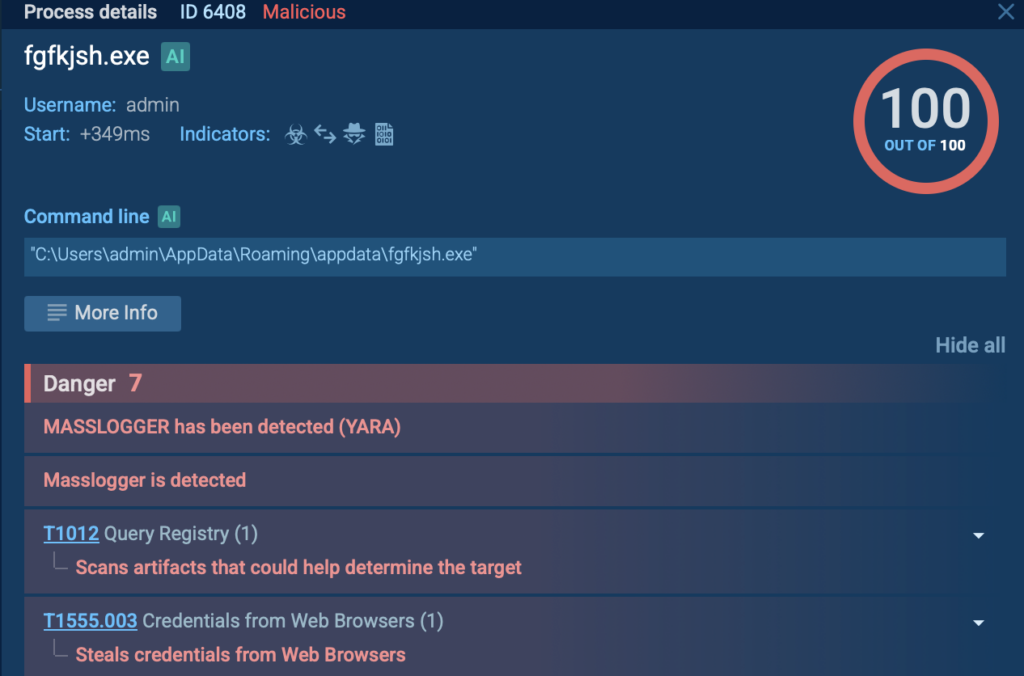
By clicking on the process located on the right side of the screen, the sandbox displays the message “MASSLOGGER has been detected (YARA).”
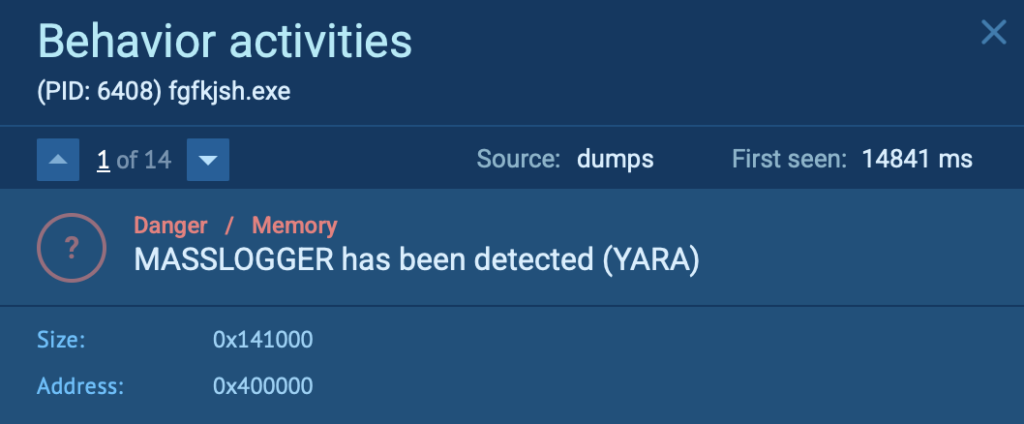
But note that YARA isn’t working alone: ANY.RUN’s sandbox also uses Suricata rules to make detections even sharper.
Discover more about Suricata rules and how they complement YARA in this detailed article: Detection with Suricata IDS
YARA Search in TI Lookup
YARA rules aren’t just limited to the sandbox: they’re also available in ANY.RUN’s Threat Intelligence (TI) Lookup. This tool lets you search a massive database of malware artifacts using YARA rules, helping you find connections between known threats and your own files.
It’s perfect for teams handling big datasets or looking to spot trends in cyber threats. By combining YARA’s precision with the power of the sandbox and TI Lookup, ANY.RUN gives businesses a complete solution to fight back the evolving threats.
Check out this video on YARA Search in TI Lookup.
About ANY.RUN
ANY.RUN helps more than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target both Windows and Linux systems. Our threat intelligence products, TI Lookup, YARA Search, and Feeds, help you find IOCs or files to learn more about the threats and respond to incidents faster.
Request free trial of ANY.RUN’s services →
The post YARA Rules: Cyber Threat Detection Tool for Modern Cybersecurity appeared first on ANY.RUN’s Cybersecurity Blog.
ANY.RUN’s Cybersecurity Blog – Read More

