Threat Intelligence Pivoting: Actionable Insights Behind Indicators
Pivoting in cyber threat intelligence refers to using one piece of data to find and explore related information and expand your understanding of a threat. It lets discover hidden connections between indicators of compromise and find potential vulnerabilities before they are exploited.
Why pivoting matters
Cyber threat intelligence concentrates on indicators of compromise, IOCs. These are data points or artifacts (like IP addresses, domain names, file hashes, email addresses, etc.) that indicate a potential or actual malicious activity. Pivoting is researching links and correlations between IOCs and thus discovering new IOCs relevant to the same attack, malware, or threat agent.
Pivoting helps make CTI proactive, helps predict and prevent the unfolding of an attack or the emergence of new threats.
Threat intelligence and pivoting are critical for businesses and corporate security because they enhance an organization’s ability to anticipate, detect, and respond to cyber threats. By leveraging actionable insights from threat intelligence and pivoting to discover deeper connections, businesses can protect their assets, reduce risk, and strengthen overall cybersecurity posture.
Note that the definition of pivoting in threat intelligence is different to that in cyber security. Generally, it’s a popular term used in many other fields.
In CS the term is usually used by pen testers and hackers. Here pivoting is the act of an attacker moving from one compromised system to one or more other systems within the same or other organizations. Pivoting is fundamental to the success of advanced persistent threat (APT) attacks.
How it works
Pivoting for CTI shows its potential when IOCs are viewed not as “atomic” but rather as complex objects. Taken by themselves, they are, so to say, “backward-looking”, they lack context. IOCs are good forensic material, but not enough for predictive, proactive security effort.
Pivoting focuses on behaviors. Indicators are linked through their behavioral commonalities. This approach grasps IOC relationships, helps discover new ones, predict their behavior, generalize tendencies, and eventually build strong and adaptive defense based on the understanding of adversaries.
Pivoting routine
Pivoting is not just about techniques and tools; it is rather about a certain approach or dare say a certain mindset. Once adopted, it’ll give your threat intelligence a new depth and perspective.
The most basic algorithm is:
- Select an initial indicator. For example, a suspicious IP. Or a domain name associated with a known threat or attack.
- Analyze the indicator with a tool of your choice.
- Decompose the indicator. Understand its parameters. Define which of them could signal malicious behavior or be linked to other artifacts.
- Find and analyze linked artifacts. Pay attention to those that haven’t been yet connected with a threat or an attack.
- Research the discovered data.
- Draw actionable insights.
Where to start
You can start with network indicators pivoting. Basic network IOCs are IPs, domains, SSL/TSL certificates. They all have certain parameters: for example, registrar and registrant for domains, hosting provider or server type for an IP address, issue date or issuer for a certificate.
One of the most powerful tools for IOC research is ANY.RUN’s Thread Intelligence Lookup. It lets you search threat artifacts by about 40 search parameters, including YARA and Suricata rules, combine them and get real-time updates of search results.
TI lookup is integrated with the Interactive Sandbox used for researching malware in action within a safe virtual environment.
For example, let us try using ASN to identify network infrastructure.
1. Find IPs assigned to the “Autonomous System of Iranian Research Organization for Science and Technology” using TI Lookup. The search query is:
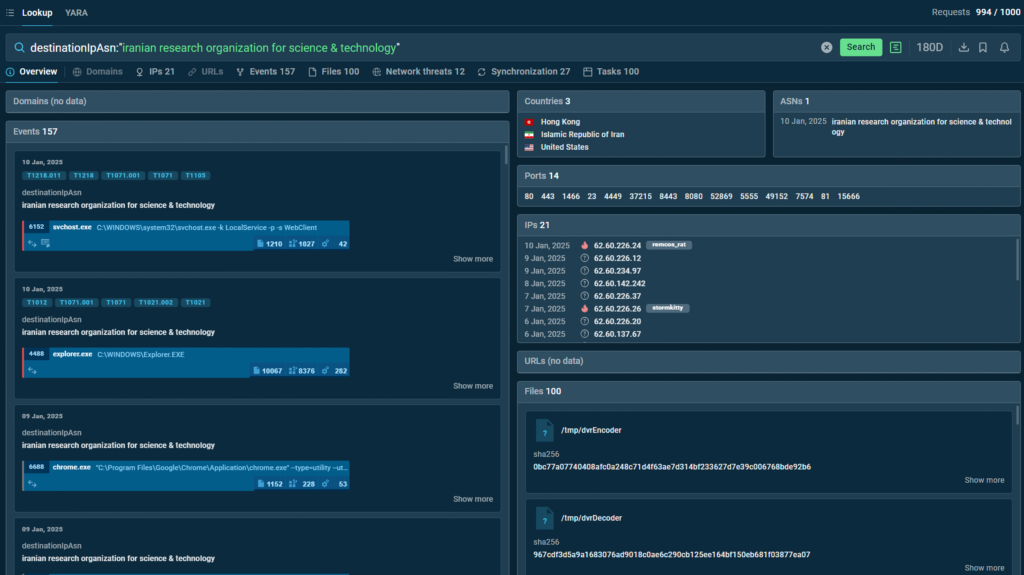
2. Look at the list of IP addresses in the search results. Some of them have tags assigned to them. The tag “Stormkitty” refers to the eponymous stealer — StormKitty.
ANY.RUN’s Cybersecurity Blog – Read More
